Microsoft MD-101 Exam Practice Questions (P. 4)
- Full Access (417 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #31
Note: The question is included in a number of questions that depicts the identical set-up. However, every question has a distinctive result. Establish if the solution satisfies the requirements.
Your company has a number of Windows 10 Microsoft Azure Active Directory (Azure AD) joined workstations. These workstations have been enrolled in Microsoft
Intune.
You have been tasked with making sure that the workstations are only able to run applications that you have explicitly permitted.
Solution: You make use of Windows Defender Application Guard.
Does the solution meet the goal?
Your company has a number of Windows 10 Microsoft Azure Active Directory (Azure AD) joined workstations. These workstations have been enrolled in Microsoft
Intune.
You have been tasked with making sure that the workstations are only able to run applications that you have explicitly permitted.
Solution: You make use of Windows Defender Application Guard.
Does the solution meet the goal?
- AYes
- BNoMost Voted
Correct Answer:
B
Instead use Windows Defender Application Control (WDAC).
Windows Defender Application Control and virtualization-based protection of code integrity.
Using WDAC to restrict devices to only authorized apps has these advantages over other solutions:
1. WDAC lets you set application control policy for code that runs in user mode, kernel mode hardware and software drivers, and even code that runs as part of
Windows.
2. WDAC policy is enforced by the Windows kernel itself, and the policy takes effect early in the boot sequence before nearly all other OS code and before traditional antivirus solutions run.
3. Etc.
Note: Application Guard helps to isolate enterprise-defined untrusted sites, protecting your company while your employees browse the Internet. As an enterprise administrator, you define what is among trusted web sites, cloud resources, and internal networks. Everything not on your list is considered untrusted. If an employee goes to an untrusted site through either Microsoft Edge or Internet Explorer, Microsoft Edge opens the site in an isolated Hyper-V-enabled container.
For Microsoft Office, Application Guard helps prevents untrusted Word, PowerPoint and Excel files from accessing trusted resources.
Reference:
https://docs.microsoft.com/en-us/windows/security/threat-protection/device-guard/introduction-to-device-guard-virtualization-based-security-and-windows- defender-application-control https://docs.microsoft.com/en-us/windows/security/threat-protection/device-guard/introduction-to-device-guard-virtualization-based-security-and-windows- defender-application-control
B
Instead use Windows Defender Application Control (WDAC).
Windows Defender Application Control and virtualization-based protection of code integrity.
Using WDAC to restrict devices to only authorized apps has these advantages over other solutions:
1. WDAC lets you set application control policy for code that runs in user mode, kernel mode hardware and software drivers, and even code that runs as part of
Windows.
2. WDAC policy is enforced by the Windows kernel itself, and the policy takes effect early in the boot sequence before nearly all other OS code and before traditional antivirus solutions run.
3. Etc.
Note: Application Guard helps to isolate enterprise-defined untrusted sites, protecting your company while your employees browse the Internet. As an enterprise administrator, you define what is among trusted web sites, cloud resources, and internal networks. Everything not on your list is considered untrusted. If an employee goes to an untrusted site through either Microsoft Edge or Internet Explorer, Microsoft Edge opens the site in an isolated Hyper-V-enabled container.
For Microsoft Office, Application Guard helps prevents untrusted Word, PowerPoint and Excel files from accessing trusted resources.
Reference:
https://docs.microsoft.com/en-us/windows/security/threat-protection/device-guard/introduction-to-device-guard-virtualization-based-security-and-windows- defender-application-control https://docs.microsoft.com/en-us/windows/security/threat-protection/device-guard/introduction-to-device-guard-virtualization-based-security-and-windows- defender-application-control
send
light_mode
delete
Question #32
You are currently making use of the Antimalware Assessment solution in Microsoft Azure Log Analytics.
You have accessed the Protection Status dashboard and find that there is a device that has no real time protection.
Which of the following could be a reason for this occurring?
You have accessed the Protection Status dashboard and find that there is a device that has no real time protection.
Which of the following could be a reason for this occurring?
- AWindows Defender has been disabled.Most Voted
- BYou need to install the Azure Diagnostic extension.
- CWindows Defender Credential Guard is incorrectly configured.
- DWindows Defender System Guard is incorrectly configured.
Correct Answer:
A
Microsoft Defender Antivirus is usually the primary antivirus/antimalware product on your device.
To review protection status -
1. On the Antimalware dashboard, you will review the Protection Status blade and click no real time protection.
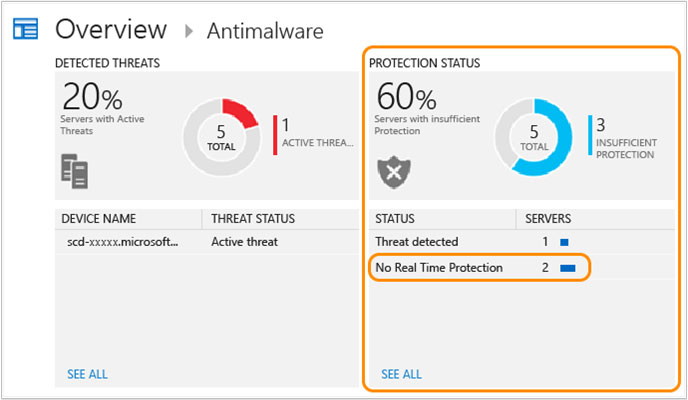
2. Search shows a list of servers without protection.
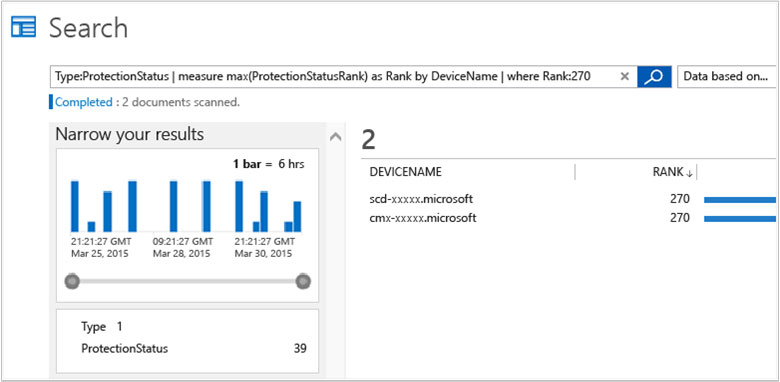
3. At this point you now know what servers do not have realtime protection.
Computers that do not have System Center Endpoint Protection installed (or if SCEP is not detected) will be reported as no real time protection.
Reference:
https://docs.microsoft.com/ga-ie/azure/security-center/security-center-install-endpoint-protection
A
Microsoft Defender Antivirus is usually the primary antivirus/antimalware product on your device.
To review protection status -
1. On the Antimalware dashboard, you will review the Protection Status blade and click no real time protection.

2. Search shows a list of servers without protection.

3. At this point you now know what servers do not have realtime protection.
Computers that do not have System Center Endpoint Protection installed (or if SCEP is not detected) will be reported as no real time protection.
Reference:
https://docs.microsoft.com/ga-ie/azure/security-center/security-center-install-endpoint-protection
send
light_mode
delete
Question #33
You are currently making use of the Antimalware Assessment solution in Microsoft Azure Log Analytics.
You have accessed the Protection Status dashboard and find that there is a device that is not reporting.
Which of the following could be a reason for this occurring?
You have accessed the Protection Status dashboard and find that there is a device that is not reporting.
Which of the following could be a reason for this occurring?
- AWindows Defender System Guard is incorrectly configured.
- BYou need to install the Azure Diagnostic extension.Most Voted
- CWindows Defender Application Guard is incorrectly configured.
- DThe Microsoft Malicious Software Removal tool is installed.
Correct Answer:
B
Azure Diagnostics extension is an agent in Azure Monitor that collects monitoring data from the guest operating system of Azure compute resources including virtual machines.
Note: As the Azure Diagnostic extension can only be used for Virtual Machines a better answer would be that the Microsoft Monitoring Agent (MMA) is missing.
Incorrect:
Not A: Windows Defender System Guard reorganizes the existing Windows 10 system integrity features under one roof and sets up the next set of investments in
Windows security. It's designed to make these security guarantees:
Protect and maintain the integrity of the system as it starts up
Validate that system integrity has truly been maintained through local and remote attestation
Not C: For Microsoft Edge, Application Guard helps to isolate enterprise-defined untrusted sites, protecting your company while your employees browse the
Internet. As an enterprise administrator, you define what is among trusted web sites, cloud resources, and internal networks. Everything not on your list is considered untrusted. If an employee goes to an untrusted site through either Microsoft Edge or Internet Explorer, Microsoft Edge opens the site in an isolated
Hyper-V-enabled container.
Reference:
https://docs.microsoft.com/en-us/azure/azure-monitor/agents/diagnostics-extension-overview https://docs.microsoft.com/en-us/azure/azure-monitor/visualize/tutorial-logs-dashboards
B
Azure Diagnostics extension is an agent in Azure Monitor that collects monitoring data from the guest operating system of Azure compute resources including virtual machines.
Note: As the Azure Diagnostic extension can only be used for Virtual Machines a better answer would be that the Microsoft Monitoring Agent (MMA) is missing.
Incorrect:
Not A: Windows Defender System Guard reorganizes the existing Windows 10 system integrity features under one roof and sets up the next set of investments in
Windows security. It's designed to make these security guarantees:
Protect and maintain the integrity of the system as it starts up
Validate that system integrity has truly been maintained through local and remote attestation
Not C: For Microsoft Edge, Application Guard helps to isolate enterprise-defined untrusted sites, protecting your company while your employees browse the
Internet. As an enterprise administrator, you define what is among trusted web sites, cloud resources, and internal networks. Everything not on your list is considered untrusted. If an employee goes to an untrusted site through either Microsoft Edge or Internet Explorer, Microsoft Edge opens the site in an isolated
Hyper-V-enabled container.
Reference:
https://docs.microsoft.com/en-us/azure/azure-monitor/agents/diagnostics-extension-overview https://docs.microsoft.com/en-us/azure/azure-monitor/visualize/tutorial-logs-dashboards
send
light_mode
delete
Question #34
You need to consider the underlined segment to establish whether it is accurate.
To enable Windows Defender Credential Guard on Windows 10 computers, the computers must have Hyper-V installed.
Select `No adjustment required` if the underlined segment is accurate. If the underlined segment is inaccurate, select the accurate option.
What should you install on the computers?
To enable Windows Defender Credential Guard on Windows 10 computers, the computers must have Hyper-V installed.
Select `No adjustment required` if the underlined segment is accurate. If the underlined segment is inaccurate, select the accurate option.
What should you install on the computers?
- ANo adjustment required.Most Voted
- BWindows Defender Smartscreen
- Ca virtual machine
- Da container cluster
Correct Answer:
A
Credential Guard can protect secrets in a Hyper-V virtual machine, just as it would on a physical machine. When Credential Guard is deployed on a VM, secrets are protected from attacks inside the VM. Credential Guard does not provide additional protection from privileged system attacks originating from the host.
Note: Hardware and software requirements
To provide basic protections against OS level attempts to read Credential Manager domain credentials, NTLM and Kerberos derived credentials, Windows
Defender Credential Guard uses:
Support for Virtualization-based security (required)
Secure boot (required)
Trusted Platform Module (TPM, preferred - provides binding to hardware) versions 1.2 and 2.0 are supported, either discrete or firmware
UEFI lock (preferred - prevents attacker from disabling with a simple registry key change)
The Virtualization-based security requires:
64-bit CPU
CPU virtualization extensions plus extended page tables
Windows hypervisor (does not require Hyper-V Windows Feature to be installed)
Reference:
https://docs.microsoft.com/en-us/windows/security/identity-protection/credential-guard/credential-guard-requirements
A
Credential Guard can protect secrets in a Hyper-V virtual machine, just as it would on a physical machine. When Credential Guard is deployed on a VM, secrets are protected from attacks inside the VM. Credential Guard does not provide additional protection from privileged system attacks originating from the host.
Note: Hardware and software requirements
To provide basic protections against OS level attempts to read Credential Manager domain credentials, NTLM and Kerberos derived credentials, Windows
Defender Credential Guard uses:
Support for Virtualization-based security (required)
Secure boot (required)
Trusted Platform Module (TPM, preferred - provides binding to hardware) versions 1.2 and 2.0 are supported, either discrete or firmware
UEFI lock (preferred - prevents attacker from disabling with a simple registry key change)
The Virtualization-based security requires:
64-bit CPU
CPU virtualization extensions plus extended page tables
Windows hypervisor (does not require Hyper-V Windows Feature to be installed)
Reference:
https://docs.microsoft.com/en-us/windows/security/identity-protection/credential-guard/credential-guard-requirements
send
light_mode
delete
Question #35
You manage one hundred Microsoft Azure Active Directory (Azure AD) joined Windows 10 devices.
You want to make sure that users are unable to join their home PC's to Azure AD.
Which of the following actions should you take?
You want to make sure that users are unable to join their home PC's to Azure AD.
Which of the following actions should you take?
- AYou should configure the Enrollment restriction settings via the Device enrollment blade in the Intune admin center.Most Voted
- BYou should configure the Enrollment restriction settings via the Security & Compliance admin center.
- CYou should configure the Enrollment restriction settings via the Azure Active Directory admin center.
- DYou should configure the Enrollment restriction settings via the Windows Defender Security Center.
Correct Answer:
C
Azure Active Directory (Azure AD) provides a central place to manage device identities and monitor related event information.
Configure device settings.
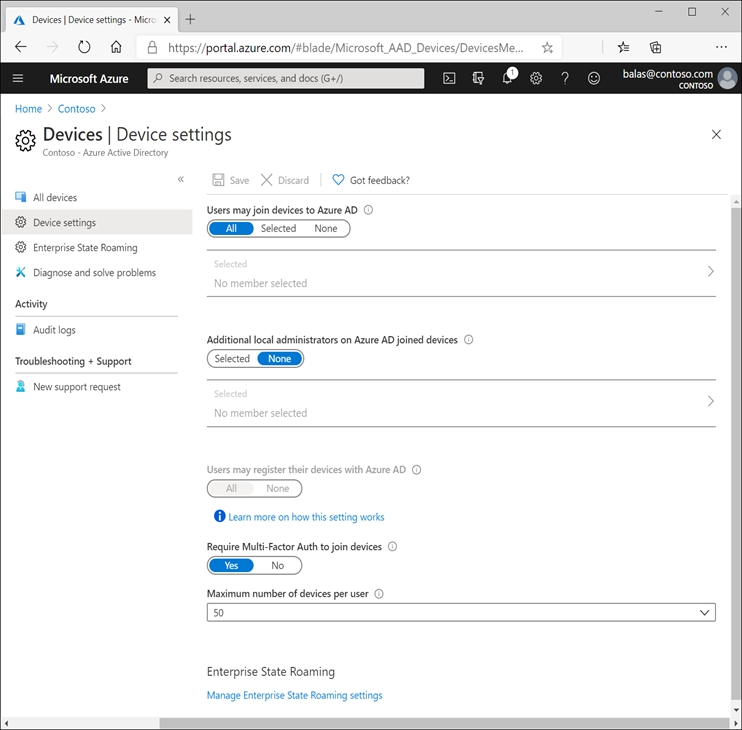
* Users may join devices to Azure AD: This setting enables you to select the users who can register their devices as Azure AD joined devices. The default is All.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/devices/device-management-azure-portal
C
Azure Active Directory (Azure AD) provides a central place to manage device identities and monitor related event information.
Configure device settings.

* Users may join devices to Azure AD: This setting enables you to select the users who can register their devices as Azure AD joined devices. The default is All.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/devices/device-management-azure-portal
send
light_mode
delete
Question #36
You need to consider the underlined segment to establish whether it is accurate.
To enable sideloading in Windows 10, you should navigate to the For developers setting via Update & Security in the Settings app.
Select `No adjustment required` if the underlined segment is accurate. If the underlined segment is inaccurate, select the accurate option.
To enable sideloading in Windows 10, you should navigate to the For developers setting via Update & Security in the Settings app.
Select `No adjustment required` if the underlined segment is accurate. If the underlined segment is inaccurate, select the accurate option.
- ANo adjustment required.Most Voted
- BWidows Insider
- CDelivery Optimization
- DActivation
Correct Answer:
A
How to allow Windows 10 to sideload apps on your computer
1. Open Settings.
2. Click on Update & security.
3. Click on For developers.
4. Under "Use developer features," select the Sideload apps option.
Reference:
https://www.windowscentral.com/how-enable-windows-10-sideload-apps-outside-store https://docs.microsoft.com/en-us/windows/application-management/sideload-apps-in-windows-10
A
How to allow Windows 10 to sideload apps on your computer
1. Open Settings.
2. Click on Update & security.
3. Click on For developers.
4. Under "Use developer features," select the Sideload apps option.
Reference:
https://www.windowscentral.com/how-enable-windows-10-sideload-apps-outside-store https://docs.microsoft.com/en-us/windows/application-management/sideload-apps-in-windows-10
send
light_mode
delete
Question #37
You need to consider the underlined segment to establish whether it is accurate.
To enable sideload a LOB application in Windows 10, you should run the Install-Package cmdlet.
Select `No adjustment required` if the underlined segment is accurate. If the underlined segment is inaccurate, select the accurate option.
To enable sideload a LOB application in Windows 10, you should run the Install-Package cmdlet.
Select `No adjustment required` if the underlined segment is accurate. If the underlined segment is inaccurate, select the accurate option.
- ANo adjustment required.
- BInstall-PackageProvider
- CSave-Package
- DAdd-AppxPackageMost Voted
Correct Answer:
D
Install the app -
From the folder with the .msix package, run the Windows PowerShell Add-AppxPackage command to install the .msix package.
Reference:
https://docs.microsoft.com/en-us/windows/application-management/sideload-apps-in-windows-10
D
Install the app -
From the folder with the .msix package, run the Windows PowerShell Add-AppxPackage command to install the .msix package.
Reference:
https://docs.microsoft.com/en-us/windows/application-management/sideload-apps-in-windows-10
send
light_mode
delete
Question #38
Note: The question is included in a number of questions that depicts the identical set-up. However, every question has a distinctive result. Establish if the solution satisfies the requirements.
Your company's environment includes a Microsoft 365 subscription.
Users in the company's sales division have personal iOS or Android devices that are enrolled in Microsoft Intune. New users are added to the sales division on a monthly basis.
After a mobile application is created for users in the sales division, you are instructed to make sure that the application can only be downloaded by the sales division users
Solution: You start by adding the application to Microsoft Store for Business.
Does the solution meet the goal?
Your company's environment includes a Microsoft 365 subscription.
Users in the company's sales division have personal iOS or Android devices that are enrolled in Microsoft Intune. New users are added to the sales division on a monthly basis.
After a mobile application is created for users in the sales division, you are instructed to make sure that the application can only be downloaded by the sales division users
Solution: You start by adding the application to Microsoft Store for Business.
Does the solution meet the goal?
- AYes
- BNoMost Voted
Correct Answer:
B
Before you can configure, assign, protect, or monitor apps, you must add them to Microsoft Intune.
Reference:
https://docs.microsoft.com/en-us/intune/apps-add
B
Before you can configure, assign, protect, or monitor apps, you must add them to Microsoft Intune.
Reference:
https://docs.microsoft.com/en-us/intune/apps-add
send
light_mode
delete
Question #39
Note: The question is included in a number of questions that depicts the identical set-up. However, every question has a distinctive result. Establish if the solution satisfies the requirements.
Your company's environment includes a Microsoft 365 subscription.
Users in the company's sales division have personal iOS or Android devices that are enrolled in Microsoft Intune. New users are added to the sales division on a monthly basis.
After a mobile application is created for users in the sales division, you are instructed to make sure that the application can only be downloaded by the sales division users
Solution: You start by assigning the application to a group.
Does the solution meet the goal?
Your company's environment includes a Microsoft 365 subscription.
Users in the company's sales division have personal iOS or Android devices that are enrolled in Microsoft Intune. New users are added to the sales division on a monthly basis.
After a mobile application is created for users in the sales division, you are instructed to make sure that the application can only be downloaded by the sales division users
Solution: You start by assigning the application to a group.
Does the solution meet the goal?
- AYes
- BNoMost Voted
Correct Answer:
B
Before you can configure, assign, protect, or monitor apps, you must add them to Microsoft Intune.
Reference:
https://docs.microsoft.com/en-us/intune/apps-add
B
Before you can configure, assign, protect, or monitor apps, you must add them to Microsoft Intune.
Reference:
https://docs.microsoft.com/en-us/intune/apps-add
send
light_mode
delete
Question #40
Note: The question is included in a number of questions that depicts the identical set-up. However, every question has a distinctive result. Establish if the solution satisfies the requirements.
Your company's environment includes a Microsoft 365 subscription.
Users in the company's sales division have personal iOS or Android devices that are enrolled in Microsoft Intune. New users are added to the sales division on a monthly basis.
After a mobile application is created for users in the sales division, you are instructed to make sure that the application can only be downloaded by the sales division users.
Solution: You start by adding the application to Intune.
Does the solution meet the goal?
Your company's environment includes a Microsoft 365 subscription.
Users in the company's sales division have personal iOS or Android devices that are enrolled in Microsoft Intune. New users are added to the sales division on a monthly basis.
After a mobile application is created for users in the sales division, you are instructed to make sure that the application can only be downloaded by the sales division users.
Solution: You start by adding the application to Intune.
Does the solution meet the goal?
- AYesMost Voted
- BNo
Correct Answer:
A
Before you can configure, assign, protect, or monitor apps, you must add them to Microsoft Intune.
Reference:
https://docs.microsoft.com/en-us/intune/apps-add
A
Before you can configure, assign, protect, or monitor apps, you must add them to Microsoft Intune.
Reference:
https://docs.microsoft.com/en-us/intune/apps-add
send
light_mode
delete
All Pages
