Microsoft MD-101 Exam Practice Questions (P. 2)
- Full Access (417 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #11
You need to consider the underlined segment to establish whether it is accurate.
After installing a feature update on a Windows 10 computer, you have 7 days to roll back the update
Select `No adjustment required` if the underlined segment is accurate. If the underlined segment is inaccurate, select the accurate option.
After installing a feature update on a Windows 10 computer, you have 7 days to roll back the update
Select `No adjustment required` if the underlined segment is accurate. If the underlined segment is inaccurate, select the accurate option.
- ANo adjustment required.
- B10Most Voted
- C90
- D30
Correct Answer:
B
By default settings, Windows 10 allows you to go back to the previous version of Windows in the first 10 days. And after that system Automatically delete this old windows folder, and can't go back to the previous build windows 10.
Reference:
https://howtofixwindows.com/roll-back-windows-10-upgrade-after-10-days-limit/
B
By default settings, Windows 10 allows you to go back to the previous version of Windows in the first 10 days. And after that system Automatically delete this old windows folder, and can't go back to the previous build windows 10.
Reference:
https://howtofixwindows.com/roll-back-windows-10-upgrade-after-10-days-limit/
send
light_mode
delete
Question #12
Your company has a Microsoft 365 subscription configured for their environment. All devices in the environment have Windows 10 installed.
You have been instructed to make sure that users are not allowed to enroll devices in the Windows Insider Program.
To achieve your goal, you access Microsoft 365 Device Management.
Which of the following actions should you take?
You have been instructed to make sure that users are not allowed to enroll devices in the Windows Insider Program.
To achieve your goal, you access Microsoft 365 Device Management.
Which of the following actions should you take?
- AYou should configure a Windows 10 security baseline.
- BYou should configure an app protection policy.
- CYou should configure device restriction policy.
- DYou should configure a Windows 10 update ring.Most Voted
Correct Answer:
D
Set up Insider Preview builds using Intune
1. Log in to the Azure portal and select Intune.
2. Go to Software Updates > Windows 10 Update Rings and select + Create to make an Update Ring policy.
Add a name and select the Settings section to configure its settings.
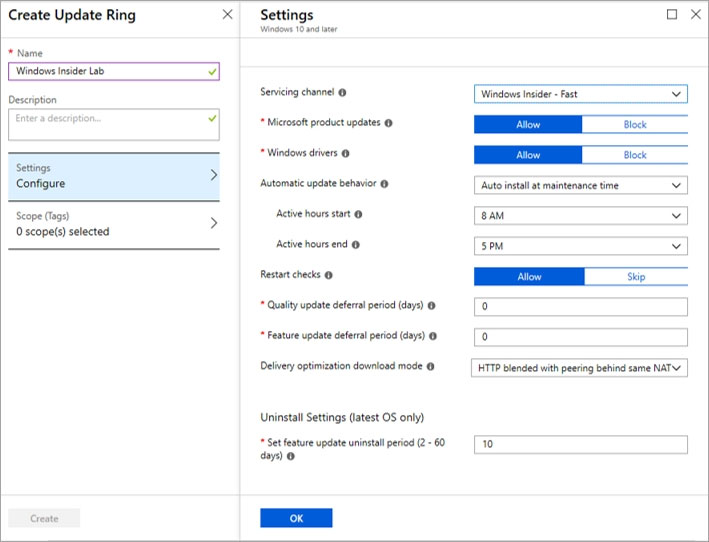
3. Etc.
Reference:
https://docs.microsoft.com/en-us/windows-insider/business/manage-builds
D
Set up Insider Preview builds using Intune
1. Log in to the Azure portal and select Intune.
2. Go to Software Updates > Windows 10 Update Rings and select + Create to make an Update Ring policy.
Add a name and select the Settings section to configure its settings.

3. Etc.
Reference:
https://docs.microsoft.com/en-us/windows-insider/business/manage-builds
send
light_mode
delete
Question #13
Note: The question is included in a number of questions that depicts the identical set-up. However, every question has a distinctive result. Establish if the solution satisfies the requirements.
Your company has a hybrid configuration of Microsoft Azure Active Directory (Azure AD). Your company also has a Microsoft 365 subscription.
After creating a conditional access policy for Microsoft Exchange Online, you are tasked with configuring the policy to block access to Exchange Online. However, the policy should allow access for hybrid Azure AD-joined devices
Solution: You should configure the Device platforms settings.
Does the solution meet the goal?
Your company has a hybrid configuration of Microsoft Azure Active Directory (Azure AD). Your company also has a Microsoft 365 subscription.
After creating a conditional access policy for Microsoft Exchange Online, you are tasked with configuring the policy to block access to Exchange Online. However, the policy should allow access for hybrid Azure AD-joined devices
Solution: You should configure the Device platforms settings.
Does the solution meet the goal?
- AYes
- BNoMost Voted
Correct Answer:
B
Within a Conditional Access policy, an administrator can make use of signals from conditions like risk, device platform, or location to enhance their policy decisions.
Client apps -
By default, all newly created Conditional Access policies will apply to all client app types even if the client apps condition isn't configured.
These conditions are commonly used when requiring a managed device, blocking legacy authentication, and blocking web applications but allowing mobile or desktop apps.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/conditions#device-state
B
Within a Conditional Access policy, an administrator can make use of signals from conditions like risk, device platform, or location to enhance their policy decisions.
Client apps -
By default, all newly created Conditional Access policies will apply to all client app types even if the client apps condition isn't configured.
These conditions are commonly used when requiring a managed device, blocking legacy authentication, and blocking web applications but allowing mobile or desktop apps.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/conditions#device-state
send
light_mode
delete
Question #14
Note: The question is included in a number of questions that depicts the identical set-up. However, every question has a distinctive result. Establish if the solution satisfies the requirements.
Your company has a hybrid configuration of Microsoft Azure Active Directory (Azure AD). Your company also has a Microsoft 365 subscription.
After creating a conditional access policy for Microsoft Exchange Online, you are tasked with configuring the policy to block access to Exchange Online. However, the policy should allow access for hybrid Azure AD-joined devices
Solution: You should configure the Client apps settings.
Does the solution meet the goal?
Your company has a hybrid configuration of Microsoft Azure Active Directory (Azure AD). Your company also has a Microsoft 365 subscription.
After creating a conditional access policy for Microsoft Exchange Online, you are tasked with configuring the policy to block access to Exchange Online. However, the policy should allow access for hybrid Azure AD-joined devices
Solution: You should configure the Client apps settings.
Does the solution meet the goal?
- AYes
- BNoMost Voted
Correct Answer:
B
Within a Conditional Access policy, an administrator can make use of signals from conditions like risk, device platform, or location to enhance their policy decisions.
Client apps -
By default, all newly created Conditional Access policies will apply to all client app types even if the client apps condition isn't configured.
These conditions are commonly used when requiring a managed device, blocking legacy authentication, and blocking web applications but allowing mobile or desktop apps.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/conditions#device-state
B
Within a Conditional Access policy, an administrator can make use of signals from conditions like risk, device platform, or location to enhance their policy decisions.
Client apps -
By default, all newly created Conditional Access policies will apply to all client app types even if the client apps condition isn't configured.
These conditions are commonly used when requiring a managed device, blocking legacy authentication, and blocking web applications but allowing mobile or desktop apps.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/conditions#device-state
send
light_mode
delete
Question #15
Note: The question is included in a number of questions that depicts the identical set-up. However, every question has a distinctive result. Establish if the solution satisfies the requirements.
Your company has a hybrid configuration of Microsoft Azure Active Directory (Azure AD). Your company also has a Microsoft 365 subscription.
After creating a conditional access policy for Microsoft Exchange Online, you are tasked with configuring the policy to block access to Exchange Online. However, the policy should allow access for hybrid Azure AD-joined devices
Solution: You should configure the Device state settings.
Does the solution meet the goal?
Your company has a hybrid configuration of Microsoft Azure Active Directory (Azure AD). Your company also has a Microsoft 365 subscription.
After creating a conditional access policy for Microsoft Exchange Online, you are tasked with configuring the policy to block access to Exchange Online. However, the policy should allow access for hybrid Azure AD-joined devices
Solution: You should configure the Device state settings.
Does the solution meet the goal?
- AYes
- BNoMost Voted
Correct Answer:
A
Within a Conditional Access policy, an administrator can make use of signals from conditions like risk, device platform, or location to enhance their policy decisions.
Client apps -
By default, all newly created Conditional Access policies will apply to all client app types even if the client apps condition isn't configured.
These conditions are commonly used when requiring a managed device, blocking legacy authentication, and blocking web applications but allowing mobile or desktop apps.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/conditions#device-state
A
Within a Conditional Access policy, an administrator can make use of signals from conditions like risk, device platform, or location to enhance their policy decisions.
Client apps -
By default, all newly created Conditional Access policies will apply to all client app types even if the client apps condition isn't configured.
These conditions are commonly used when requiring a managed device, blocking legacy authentication, and blocking web applications but allowing mobile or desktop apps.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/conditions#device-state
send
light_mode
delete
Question #16
Your company makes use of Microsoft Intune to manage computers.
You have been tasked with configuring Windows Hello for Business. You are preparing to create an Intune profile to achieve your goal.
Which of the following is an operating system that supports Windows Hello for Business?
You have been tasked with configuring Windows Hello for Business. You are preparing to create an Intune profile to achieve your goal.
Which of the following is an operating system that supports Windows Hello for Business?
- AWindows Vista
- BWindows 8.1
- CWindows 10Most Voted
- DmacOS
Correct Answer:
C
You can configure Windows Hello for Business settings in an Identity protection profile. Identity protection profiles are part of device configuration policy in
Microsoft Intune. With an Identity protection profile, you can configure settings on discrete groups of Windows 10/11 devices.
Reference:
https://docs.microsoft.com/en-us/intune/protect/identity-protection-windows-settings
C
You can configure Windows Hello for Business settings in an Identity protection profile. Identity protection profiles are part of device configuration policy in
Microsoft Intune. With an Identity protection profile, you can configure settings on discrete groups of Windows 10/11 devices.
Reference:
https://docs.microsoft.com/en-us/intune/protect/identity-protection-windows-settings
send
light_mode
delete
Question #17
Your company has a large number of Android and iOS devices, which are enrolled in Intune.
You are preparing to deploy new Intune policies will apply to devices, based on the version of Android or iOS that is being run.
You are required to make sure that the policies are able to target the devices according to your plan.
Which of the following actions should you take?
You are preparing to deploy new Intune policies will apply to devices, based on the version of Android or iOS that is being run.
You are required to make sure that the policies are able to target the devices according to your plan.
Which of the following actions should you take?
- AYou should start by accessing Intune and configuring corporate device identifiers.
- BYou should start by accessing Microsoft Azure Active Directory (Azure AD) and configuring Device settings.Most Voted
- CYou should start by accessing Microsoft Azure Active Directory (Azure AD) and configuring Application settings.
- DYou should start by creating a distribution group.
Correct Answer:
B
Device Properties -
Operating System Version -
Minimum OS version -
When a device doesn't meet the minimum OS version requirement, it's reported as noncompliant. A link with information about how to upgrade is shown. The end user can choose to upgrade their device, and then get access to company resources.
By default, no version is configured.
Maximum OS version -
When a device is using an OS version later than the version specified in the rule, access to company resources is blocked. The user is asked to contact their IT admin. Until a rule is changed to allow the OS version, this device can't access company resources.
Reference:
https://docs.microsoft.com/en-us/intune/compliance-policy-create-android https://docs.microsoft.com/en-us/intune/compliance-policy-create-ios
B
Device Properties -
Operating System Version -
Minimum OS version -
When a device doesn't meet the minimum OS version requirement, it's reported as noncompliant. A link with information about how to upgrade is shown. The end user can choose to upgrade their device, and then get access to company resources.
By default, no version is configured.
Maximum OS version -
When a device is using an OS version later than the version specified in the rule, access to company resources is blocked. The user is asked to contact their IT admin. Until a rule is changed to allow the OS version, this device can't access company resources.
Reference:
https://docs.microsoft.com/en-us/intune/compliance-policy-create-android https://docs.microsoft.com/en-us/intune/compliance-policy-create-ios
send
light_mode
delete
Question #18
You need to consider the underlined segment to establish whether it is accurate.
Your company has Microsoft Azure Active Directory (Azure AD) joined Windows 10 Pro computers that have been enrolled in Microsoft Intune.
You have been tasked with making sure that the computers are upgraded to Windows 10 Enterprise.
You start by configuring a device enrollment policy in Intune.
Select `No adjustment required` if the underlined segment is accurate. If the underlined segment is inaccurate, select the accurate option.
What should you configure in Intune?
Your company has Microsoft Azure Active Directory (Azure AD) joined Windows 10 Pro computers that have been enrolled in Microsoft Intune.
You have been tasked with making sure that the computers are upgraded to Windows 10 Enterprise.
You start by configuring a device enrollment policy in Intune.
Select `No adjustment required` if the underlined segment is accurate. If the underlined segment is inaccurate, select the accurate option.
What should you configure in Intune?
- ANo adjustment required
- Ban app protection policy
- Ca Windows AutoPilot deployment profile
- DA device configuration profileMost Voted
Correct Answer:
D
Do you have a bunch of Windows 10 Pro devices and would like upgrade them to Windows 10 Enterprise? Microsoft 365 (specifically Microsoft Intune) can help you!
First, create a Microsoft Intune configuration policy. In the Azure Portal navigate to Microsoft Intune -> Device Configuration -> Profiles. Click Create Profile
Reference:
https://blogs.technet.microsoft.com/skypehybridguy/2018/09/21/intune-upgrade-windows-from-pro-to-enterprise-automatically/
D
Do you have a bunch of Windows 10 Pro devices and would like upgrade them to Windows 10 Enterprise? Microsoft 365 (specifically Microsoft Intune) can help you!
First, create a Microsoft Intune configuration policy. In the Azure Portal navigate to Microsoft Intune -> Device Configuration -> Profiles. Click Create Profile
Reference:
https://blogs.technet.microsoft.com/skypehybridguy/2018/09/21/intune-upgrade-windows-from-pro-to-enterprise-automatically/
send
light_mode
delete
Question #19
Your company has a Microsoft 365 subscription.
You have enrolled all the company computers in Microsoft Intune.
You have been tasked with making sure that Microsoft Exchange Online is only accessible from known locations.
Which of the following actions should you take?
You have enrolled all the company computers in Microsoft Intune.
You have been tasked with making sure that Microsoft Exchange Online is only accessible from known locations.
Which of the following actions should you take?
- AYou should create a device configuration profile.
- BYou should create a device compliance policy.
- CYou should create a Windows AutoPilot deployment profile.
- DYou should create a conditional access policy.Most Voted
Correct Answer:
D
Within a Conditional Access policy, an administrator can make use of signals from conditions like risk, device platform, or location to enhance their policy decisions.
Locations -
When configuring location as a condition, organizations can choose to include or exclude locations. These named locations may include the public IPv4 network information, country or region, or even unknown areas that don't map to specific countries or regions. Only IP ranges can be marked as a trusted location.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/conditions
D
Within a Conditional Access policy, an administrator can make use of signals from conditions like risk, device platform, or location to enhance their policy decisions.
Locations -
When configuring location as a condition, organizations can choose to include or exclude locations. These named locations may include the public IPv4 network information, country or region, or even unknown areas that don't map to specific countries or regions. Only IP ranges can be marked as a trusted location.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/conditions
send
light_mode
delete
Question #20
Your company has a Microsoft 365 subscription.
You have enrolled all the company computers in Microsoft Intune.
You have been tasked with making sure that devices with a high Windows Defender Advanced Threat Protection (Windows Defender ATP) risk score are locked.
Which of the following actions should you take?
You have enrolled all the company computers in Microsoft Intune.
You have been tasked with making sure that devices with a high Windows Defender Advanced Threat Protection (Windows Defender ATP) risk score are locked.
Which of the following actions should you take?
- AYou should create a device configuration profile.
- BYou should create a device compliance policy.Most Voted
- CYou should create a Windows AutoPilot deployment profile.
- DYou should create a conditional access policy.
Correct Answer:
ABD
You can integrate Microsoft Defender for Endpoint with Microsoft Intune as a Mobile Threat Defense solution. Integration can help you prevent security breaches and limit the impact of breaches within an organization.
To be successful, you'll use the following configurations in concert:
* Establish a service-to-service connection between Intune and Microsoft Defender for Endpoint.
* Use a device configuration profile to onboard devices with Microsoft Defender for Endpoint. You onboard devices to configure them to communicate with
Microsoft Defender for Endpoint and to provide data that helps assess their risk level.
* Use a device compliance policy to set the level of risk you want to allow. Risk levels are reported by Microsoft Defender for Endpoint. Devices that exceed the allowed risk level are identified as noncompliant.
* Use a conditional access policy to block users from accessing corporate resources from devices that are noncompliant.
Reference:
https://docs.microsoft.com/en-us/mem/intune/protect/advanced-threat-protection
ABD
You can integrate Microsoft Defender for Endpoint with Microsoft Intune as a Mobile Threat Defense solution. Integration can help you prevent security breaches and limit the impact of breaches within an organization.
To be successful, you'll use the following configurations in concert:
* Establish a service-to-service connection between Intune and Microsoft Defender for Endpoint.
* Use a device configuration profile to onboard devices with Microsoft Defender for Endpoint. You onboard devices to configure them to communicate with
Microsoft Defender for Endpoint and to provide data that helps assess their risk level.
* Use a device compliance policy to set the level of risk you want to allow. Risk levels are reported by Microsoft Defender for Endpoint. Devices that exceed the allowed risk level are identified as noncompliant.
* Use a conditional access policy to block users from accessing corporate resources from devices that are noncompliant.
Reference:
https://docs.microsoft.com/en-us/mem/intune/protect/advanced-threat-protection
send
light_mode
delete
All Pages
