Microsoft MD-101 Exam Practice Questions (P. 3)
- Full Access (417 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #21
Your company plans to deploy tablets to 50 meeting rooms.
The tablets run Windows 10 and are managed by using Microsoft Intune. The tablets have an application named App1.
You need to configure the tablets so that any user can use App1 without having to sign in. Users must be prevented from using other applications on the tablets.
Which device configuration profile type should you use?
The tablets run Windows 10 and are managed by using Microsoft Intune. The tablets have an application named App1.
You need to configure the tablets so that any user can use App1 without having to sign in. Users must be prevented from using other applications on the tablets.
Which device configuration profile type should you use?
- AKiosk
- BEndpoint protection
- CIdentity protection
- DDevice restrictions
Correct Answer:
A
A single-app kiosk uses the Assigned Access feature to run a single app above the lock screen. When the kiosk account signs in, the app is launched automatically. The person using the kiosk cannot do anything on the device outside of the kiosk app.
Reference:
https://docs.microsoft.com/en-us/windows/configuration/kiosk-single-app
A
A single-app kiosk uses the Assigned Access feature to run a single app above the lock screen. When the kiosk account signs in, the app is launched automatically. The person using the kiosk cannot do anything on the device outside of the kiosk app.
Reference:
https://docs.microsoft.com/en-us/windows/configuration/kiosk-single-app
send
light_mode
delete
Question #22
All of your company's devices are managed via Microsoft Intune.
Conditional access is used to prevent devices that are not compliant with company security policies, from accessing Microsoft 365 services.
You need to access Device compliance to view the non-compliant devices.
Where should you access Device compliance from?
Conditional access is used to prevent devices that are not compliant with company security policies, from accessing Microsoft 365 services.
You need to access Device compliance to view the non-compliant devices.
Where should you access Device compliance from?
- ASystem Center Configuration Manager
- BWindows Defender Security Center.
- CThe Intune admin center.Most Voted
- DThe Azure Active Directory admin center.
Correct Answer:
C
Open the Intune Device compliance dashboard:
1. Sign in to the Microsoft Endpoint Manager admin center.
2. Select Devices > Overview > Compliance status tab.
Important: Devices must be enrolled into Intune to receive device compliance policies.
Note 1: Intune Admin portal URL, Microsoft Endpoint Manager admin center: https://endpoint.microsoft.com
Microsoft Intune, which is a part of Microsoft Endpoint Manager, provides the cloud infrastructure, the cloud-based mobile device management (MDM), cloud- based mobile application management (MAM), and cloud-based PC management for your organization.
Note 2: Compliance reports help you review device compliance and troubleshoot compliance-related issues in your organization. Using these reports, you can view information on:
The overall compliance states of devices
The compliance status for an individual setting
The compliance status for an individual policy
Drill down into individual devices to view specific settings and policies that affect the device
Reference:
https://docs.microsoft.com/en-us/mem/intune/protect/compliance-policy-monitor https://docs.microsoft.com/en-us/mem/intune/fundamentals/account-sign-up
C
Open the Intune Device compliance dashboard:
1. Sign in to the Microsoft Endpoint Manager admin center.
2. Select Devices > Overview > Compliance status tab.
Important: Devices must be enrolled into Intune to receive device compliance policies.
Note 1: Intune Admin portal URL, Microsoft Endpoint Manager admin center: https://endpoint.microsoft.com
Microsoft Intune, which is a part of Microsoft Endpoint Manager, provides the cloud infrastructure, the cloud-based mobile device management (MDM), cloud- based mobile application management (MAM), and cloud-based PC management for your organization.
Note 2: Compliance reports help you review device compliance and troubleshoot compliance-related issues in your organization. Using these reports, you can view information on:
The overall compliance states of devices
The compliance status for an individual setting
The compliance status for an individual policy
Drill down into individual devices to view specific settings and policies that affect the device
Reference:
https://docs.microsoft.com/en-us/mem/intune/protect/compliance-policy-monitor https://docs.microsoft.com/en-us/mem/intune/fundamentals/account-sign-up
send
light_mode
delete
Question #23
You manage a large number of Windows 10 computers.
You have been tasked with creating a provisioning package that will allow you to remove the Microsoft News and the Xbox Microsoft Store apps, as well as add a
VPN connection to the company network.
Which of the following are the customization settings you should configure?
You have been tasked with creating a provisioning package that will allow you to remove the Microsoft News and the Xbox Microsoft Store apps, as well as add a
VPN connection to the company network.
Which of the following are the customization settings you should configure?
- AConnections and Personalization
- BConnectivityProfiles and PoliciesMost Voted
- CConnections and Policies
- DConnectivityProfiles and Personalization
Correct Answer:
B
The Policy configuration service provider enables the enterprise to configure policies on Windows 10
ConnectivityProfiles is uses to configure profiles that a user will connect with, such as an email account or VPN profile.
Reference:
https://docs.microsoft.com/en-us/windows/configuration/wcd/wcd-connectivityprofiles https://docs.microsoft.com/en-us/windows/client-management/mdm/policy-configuration-service-provider#applicationmanagement-applicationrestrictions https://docs.microsoft.com/en-us/windows/configuration/wcd/wcd-policies
B
The Policy configuration service provider enables the enterprise to configure policies on Windows 10
ConnectivityProfiles is uses to configure profiles that a user will connect with, such as an email account or VPN profile.
Reference:
https://docs.microsoft.com/en-us/windows/configuration/wcd/wcd-connectivityprofiles https://docs.microsoft.com/en-us/windows/client-management/mdm/policy-configuration-service-provider#applicationmanagement-applicationrestrictions https://docs.microsoft.com/en-us/windows/configuration/wcd/wcd-policies
send
light_mode
delete
Question #24
All users at your company have Azure AD joined Windows 10 workstations that are managed via Microsoft Intune.
You have been tasked with making sure that Windows Analytics is used to monitor the workstations centrally.
Which of the following actions should you take?
You have been tasked with making sure that Windows Analytics is used to monitor the workstations centrally.
Which of the following actions should you take?
- AYou should create a device configuration profile via Intune.Most Voted
- BYou should create a device compliance policy via Intune.
- CYou should create a Windows AutoPilot deployment profile via Intune.
- DYou should create an app configuration policy via Intune.
Correct Answer:
A
To configure the setting go to Device configuration ג€" Profiles > Device Restriction ג€" Properties > Device restrictions > Reporting and Telemetry
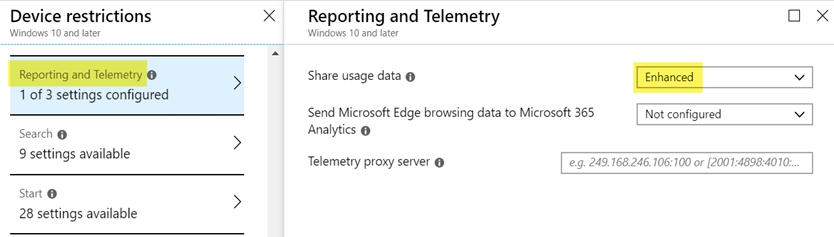
Reference:
https://www.scconfigmgr.com/2019/03/27/windows-analytics-onboarding-with-intune/
A
To configure the setting go to Device configuration ג€" Profiles > Device Restriction ג€" Properties > Device restrictions > Reporting and Telemetry

Reference:
https://www.scconfigmgr.com/2019/03/27/windows-analytics-onboarding-with-intune/
send
light_mode
delete
Question #25
Your company has a number of Windows 10 Microsoft Azure Active Directory (Azure AD) joined workstations. These workstations have been enrolled in Microsoft
Intune.
You are creating a device configuration profile for the workstations. You have been informed that a custom image should be displayed on the sign-in screen.
Which of the following is a Device restriction setting that should be configured?
Intune.
You are creating a device configuration profile for the workstations. You have been informed that a custom image should be displayed on the sign-in screen.
Which of the following is a Device restriction setting that should be configured?
- ALocked screen experienceMost Voted
- BPersonalization
- CDisplay
- DGeneral
Correct Answer:
A
Sign-in screen, or Locked screen, image is set under Locked screen experience
Reference:
https://docs.microsoft.com/en-us/intune/device-restrictions-windows-10
A
Sign-in screen, or Locked screen, image is set under Locked screen experience
Reference:
https://docs.microsoft.com/en-us/intune/device-restrictions-windows-10
send
light_mode
delete
Question #26
Your company has a number of Windows 10 Microsoft Azure Active Directory (Azure AD) joined workstations. These workstations have been enrolled in Microsoft
Intune.
You are creating a device configuration profile for the workstations. You have been informed that a custom image should be displayed as the Desktop background picture.
Which of the following is a Device restriction setting that should be configured?
Intune.
You are creating a device configuration profile for the workstations. You have been informed that a custom image should be displayed as the Desktop background picture.
Which of the following is a Device restriction setting that should be configured?
- ALocked screen experience
- BPersonalizationMost Voted
- CDisplay
- DGeneral
Correct Answer:
B
Wallpaper image, or Desktop background picture, URL is set under Personalization.
Reference:
https://docs.microsoft.com/en-us/intune/device-restrictions-windows-10
B
Wallpaper image, or Desktop background picture, URL is set under Personalization.
Reference:
https://docs.microsoft.com/en-us/intune/device-restrictions-windows-10
send
light_mode
delete
Question #27
Your company has a large number of Windows 10 workstations that are managed via Microsoft Intune.
Delivery Optimization is not being used for Windows updates at present.
You want to make sure that Delivery Optimization is configured for all of the workstations.
Which of the following actions should you take?
Delivery Optimization is not being used for Windows updates at present.
You want to make sure that Delivery Optimization is configured for all of the workstations.
Which of the following actions should you take?
- AYou should create a device configuration profile via Intune.Most Voted
- BYou should create a device compliance policy via Intune.
- CYou should create a Windows AutoPilot deployment profile via Intune.
- DYou should create a conditional access policy via Intune.
Correct Answer:
A
With Intune, use Delivery Optimization settings for your Windows devices to reduce bandwidth consumption when those devices download applications and updates. Configure Delivery Optimization as part of your device configuration profiles.
Reference:
https://docs.microsoft.com/en-us/intune/delivery-optimization-windows
A
With Intune, use Delivery Optimization settings for your Windows devices to reduce bandwidth consumption when those devices download applications and updates. Configure Delivery Optimization as part of your device configuration profiles.
Reference:
https://docs.microsoft.com/en-us/intune/delivery-optimization-windows
send
light_mode
delete
Question #28
Your company's environment includes the following:
✑ Microsoft Azure Active Directory (Azure AD)
✑ Microsoft 365
✑ Microsoft Intune
✑ Azure Information Protection.
A new security policy declares that enrollment for private devices in Intune is not required. However, to access corporate email information, users have to make use of a PIN for authentication purposes. Also, users are able to access corporate cloud services from their private iOS and Android devices. Furthermore, the copying corporate email information to a cloud storage service should not be allowed, unless users are copying the information to Microsoft OneDrive for
Business.
You have to make sure that security policy is enforced.
Which of the following actions should you take?
✑ Microsoft Azure Active Directory (Azure AD)
✑ Microsoft 365
✑ Microsoft Intune
✑ Azure Information Protection.
A new security policy declares that enrollment for private devices in Intune is not required. However, to access corporate email information, users have to make use of a PIN for authentication purposes. Also, users are able to access corporate cloud services from their private iOS and Android devices. Furthermore, the copying corporate email information to a cloud storage service should not be allowed, unless users are copying the information to Microsoft OneDrive for
Business.
You have to make sure that security policy is enforced.
Which of the following actions should you take?
- AYou should create a data loss prevention (DLP) policy.
- BYou should create a device enrollment policy.
- CYou should create an app protection policy.Most Voted
- DYou should create a Windows AutoPilot deployment profile.
Correct Answer:
C
App protection policies (APP) are rules that ensure an organization's data remains safe or contained in a managed app. A policy can be a rule that is enforced when the user attempts to access or move "corporate" data, or a set of actions that are prohibited or monitored when the user is inside the app. A managed app is an app that has app protection policies applied to it, and can be managed by Intune.
Reference:
https://docs.microsoft.com/en-us/intune/app-protection-policy
C
App protection policies (APP) are rules that ensure an organization's data remains safe or contained in a managed app. A policy can be a rule that is enforced when the user attempts to access or move "corporate" data, or a set of actions that are prohibited or monitored when the user is inside the app. A managed app is an app that has app protection policies applied to it, and can be managed by Intune.
Reference:
https://docs.microsoft.com/en-us/intune/app-protection-policy
send
light_mode
delete
Question #29
Note: The question is included in a number of questions that depicts the identical set-up. However, every question has a distinctive result. Establish if the solution satisfies the requirements.
Your company has a number of Windows 10 Microsoft Azure Active Directory (Azure AD) joined workstations. These workstations have been enrolled in Microsoft
Intune.
You have been tasked with making sure that the workstations are only able to run applications that you have explicitly permitted.
Solution: You make use of Windows Defender Antivirus.
Does the solution meet the goal?
Your company has a number of Windows 10 Microsoft Azure Active Directory (Azure AD) joined workstations. These workstations have been enrolled in Microsoft
Intune.
You have been tasked with making sure that the workstations are only able to run applications that you have explicitly permitted.
Solution: You make use of Windows Defender Antivirus.
Does the solution meet the goal?
- AYes
- BNoMost Voted
Correct Answer:
B
Instead use Windows Defender Application Control (WDAC).
Windows Defender Application Control and virtualization-based protection of code integrity.
Using WDAC to restrict devices to only authorized apps has these advantages over other solutions:
1. WDAC lets you set application control policy for code that runs in user mode, kernel mode hardware and software drivers, and even code that runs as part of
Windows.
2. WDAC policy is enforced by the Windows kernel itself, and the policy takes effect early in the boot sequence before nearly all other OS code and before traditional antivirus solutions run.
3. Etc.
Reference:
https://docs.microsoft.com/en-us/windows/security/threat-protection/device-guard/introduction-to-device-guard-virtualization-based-security-and-windows- defender-application-control
B
Instead use Windows Defender Application Control (WDAC).
Windows Defender Application Control and virtualization-based protection of code integrity.
Using WDAC to restrict devices to only authorized apps has these advantages over other solutions:
1. WDAC lets you set application control policy for code that runs in user mode, kernel mode hardware and software drivers, and even code that runs as part of
Windows.
2. WDAC policy is enforced by the Windows kernel itself, and the policy takes effect early in the boot sequence before nearly all other OS code and before traditional antivirus solutions run.
3. Etc.
Reference:
https://docs.microsoft.com/en-us/windows/security/threat-protection/device-guard/introduction-to-device-guard-virtualization-based-security-and-windows- defender-application-control
send
light_mode
delete
Question #30
Note: The question is included in a number of questions that depicts the identical set-up. However, every question has a distinctive result. Establish if the solution satisfies the requirements.
Your company has a number of Windows 10 Microsoft Azure Active Directory (Azure AD) joined workstations. These workstations have been enrolled in Microsoft
Intune.
You have been tasked with making sure that the workstations are only able to run applications that you have explicitly permitted.
Solution: You make use of Windows Defender SmartScreen.
Does the solution meet the goal?
Your company has a number of Windows 10 Microsoft Azure Active Directory (Azure AD) joined workstations. These workstations have been enrolled in Microsoft
Intune.
You have been tasked with making sure that the workstations are only able to run applications that you have explicitly permitted.
Solution: You make use of Windows Defender SmartScreen.
Does the solution meet the goal?
- AYes
- BNoMost Voted
Correct Answer:
B
Instead use Windows Defender Application Control (WDAC).
Windows Defender Application Control and virtualization-based protection of code integrity.
Using WDAC to restrict devices to only authorized apps has these advantages over other solutions:
1. WDAC lets you set application control policy for code that runs in user mode, kernel mode hardware and software drivers, and even code that runs as part of
Windows.
2. WDAC policy is enforced by the Windows kernel itself, and the policy takes effect early in the boot sequence before nearly all other OS code and before traditional antivirus solutions run.
3. Etc.
Reference:
https://docs.microsoft.com/en-us/windows/security/threat-protection/device-guard/introduction-to-device-guard-virtualization-based-security-and-windows- defender-application-control
B
Instead use Windows Defender Application Control (WDAC).
Windows Defender Application Control and virtualization-based protection of code integrity.
Using WDAC to restrict devices to only authorized apps has these advantages over other solutions:
1. WDAC lets you set application control policy for code that runs in user mode, kernel mode hardware and software drivers, and even code that runs as part of
Windows.
2. WDAC policy is enforced by the Windows kernel itself, and the policy takes effect early in the boot sequence before nearly all other OS code and before traditional antivirus solutions run.
3. Etc.
Reference:
https://docs.microsoft.com/en-us/windows/security/threat-protection/device-guard/introduction-to-device-guard-virtualization-based-security-and-windows- defender-application-control
send
light_mode
delete
All Pages
