Microsoft AZ-801 Exam Practice Questions (P. 4)
- Full Access (315 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #31
HOTSPOT -
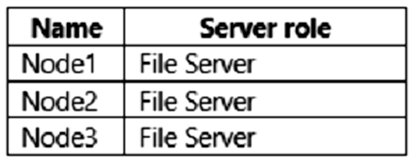
You have a failover cluster named Cluster1 that contains the nodes shown in the following table.
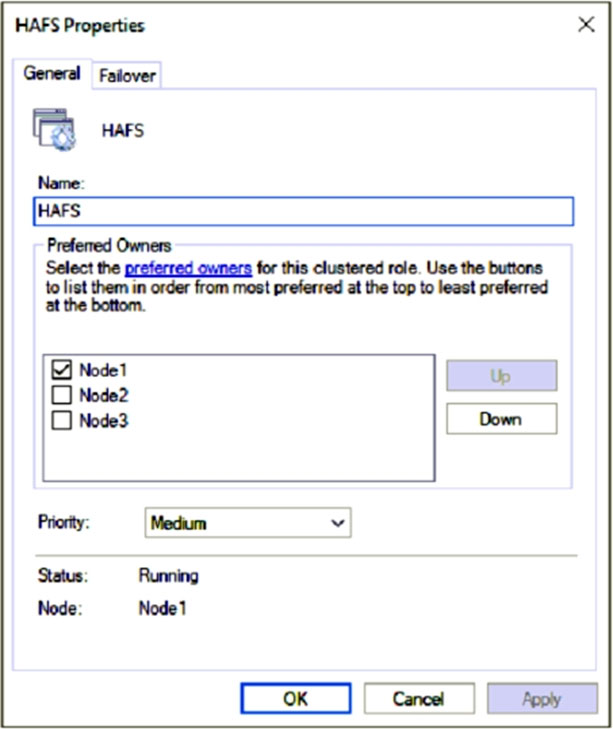
A File Server for general use cluster role named HAFS is configured as shown in the General exhibit. (Click the General tab.)
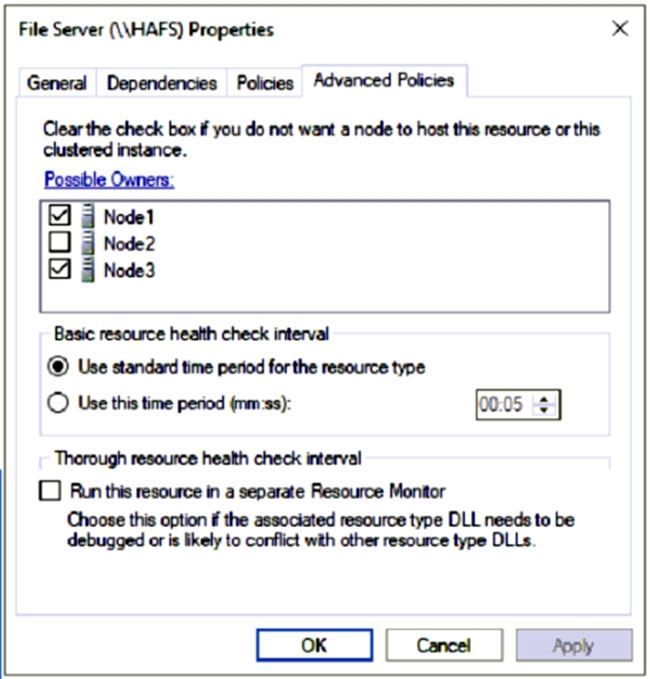
The Advanced Policies settings for HAFS are configured as shown in the Advanced Policies exhibit. (Click the Advanced Policies tab.)
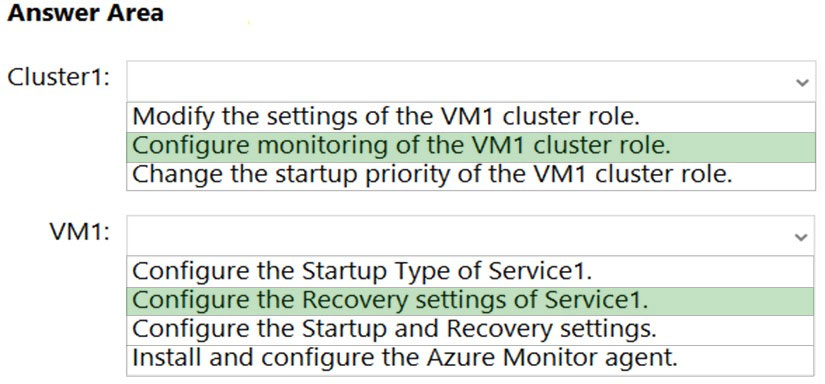
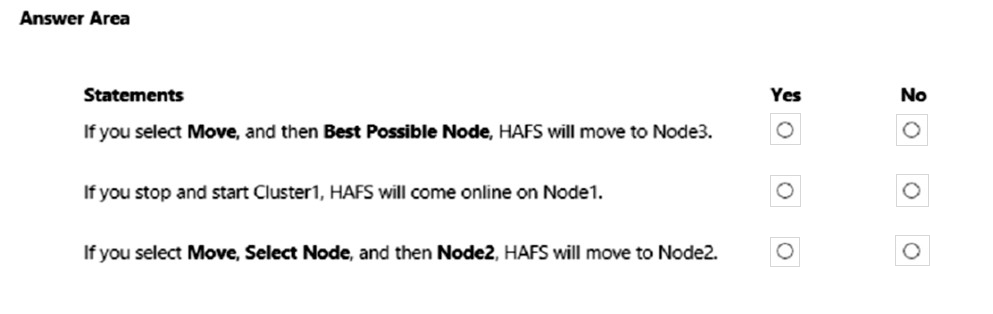
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
Hot Area:
You have a failover cluster named Cluster1 that contains the nodes shown in the following table.

A File Server for general use cluster role named HAFS is configured as shown in the General exhibit. (Click the General tab.)

The Advanced Policies settings for HAFS are configured as shown in the Advanced Policies exhibit. (Click the Advanced Policies tab.)

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
Hot Area:

Correct Answer:
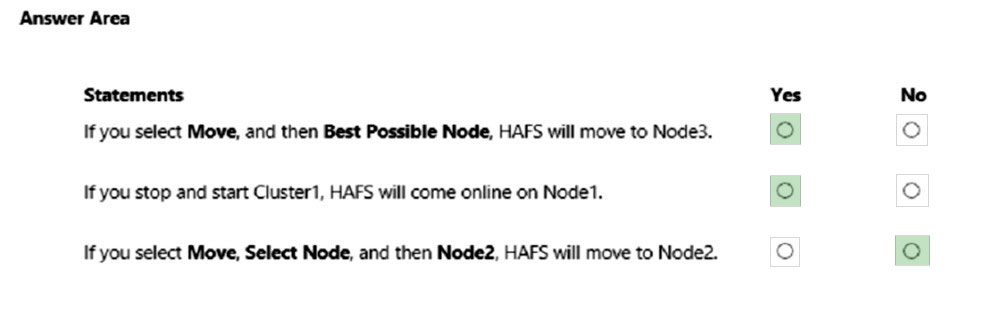
Box 1: Yes -
HAFS will move from Node1 to Node3 if we test failover for the cluster.
Note: Test failover.
Test failover of the clustered resource to validate cluster functionality.
Take the following steps:
1. Connect to one of the SQL Server cluster nodes by using RDP.
2. Open Failover Cluster Manager. Select Roles. Notice which node owns the SQL Server FCI role.
3. Right-click the SQL Server FCI role.
4. Select Move, and then select Best Possible Node.
5. Failover Cluster Manager shows the role, and its resources go offline. The resources then move and come back online in the other node.
Box 2: Yes -
Node1 is the preferred owner.
Box 3: No -
Node2 is not a possible owner of the cluster.
Reference:
https://docs.microsoft.com/en-us/azure/azure-sql/virtual-machines/windows/failover-cluster-instance-vnn-azure-load-balancer-configure

Box 1: Yes -
HAFS will move from Node1 to Node3 if we test failover for the cluster.
Note: Test failover.
Test failover of the clustered resource to validate cluster functionality.
Take the following steps:
1. Connect to one of the SQL Server cluster nodes by using RDP.
2. Open Failover Cluster Manager. Select Roles. Notice which node owns the SQL Server FCI role.
3. Right-click the SQL Server FCI role.
4. Select Move, and then select Best Possible Node.
5. Failover Cluster Manager shows the role, and its resources go offline. The resources then move and come back online in the other node.
Box 2: Yes -
Node1 is the preferred owner.
Box 3: No -
Node2 is not a possible owner of the cluster.
Reference:
https://docs.microsoft.com/en-us/azure/azure-sql/virtual-machines/windows/failover-cluster-instance-vnn-azure-load-balancer-configure
send
light_mode
delete
Question #32
You have two Azure virtual machines that run Windows Server.
You plan to create a failover cluster that will host the virtual machines.
You need to configure an Azure Storage account that will be used by the cluster as a cloud witness. The solution must maximize resiliency.
Which type of redundancy should you configure for the storage account?
You plan to create a failover cluster that will host the virtual machines.
You need to configure an Azure Storage account that will be used by the cluster as a cloud witness. The solution must maximize resiliency.
Which type of redundancy should you configure for the storage account?
- AGeo-zone-redundant storage (GZRS)
- BLocally-redundant storage (LRS)
- CZone-redundant storage (ZRS)Most Voted
- DGeo-redundant storage (GRS)
Correct Answer:
C
For Replication, you can select Locally-redundant storage (LRS) or Zone-redundant storage (ZRS) as applicable. ZRS offers more redundancy.
Reference:
https://docs.microsoft.com/en-us/windows-server/failover-clustering/deploy-cloud-witness
C
For Replication, you can select Locally-redundant storage (LRS) or Zone-redundant storage (ZRS) as applicable. ZRS offers more redundancy.
Reference:
https://docs.microsoft.com/en-us/windows-server/failover-clustering/deploy-cloud-witness
send
light_mode
delete
Question #33
DRAG DROP -
Your network contains an Active Directory Domain Services (AD DS) domain. The domain contains a failover cluster named Cluster1.
You need to configure Cluster-Aware Updating (CAU) on the cluster by using Windows Admin Center (WAC).
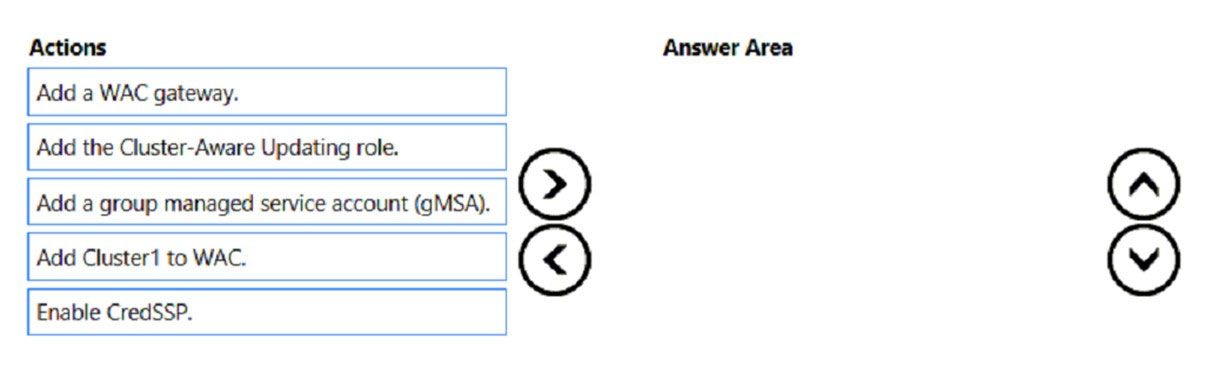
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:
Your network contains an Active Directory Domain Services (AD DS) domain. The domain contains a failover cluster named Cluster1.
You need to configure Cluster-Aware Updating (CAU) on the cluster by using Windows Admin Center (WAC).
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:

Correct Answer:
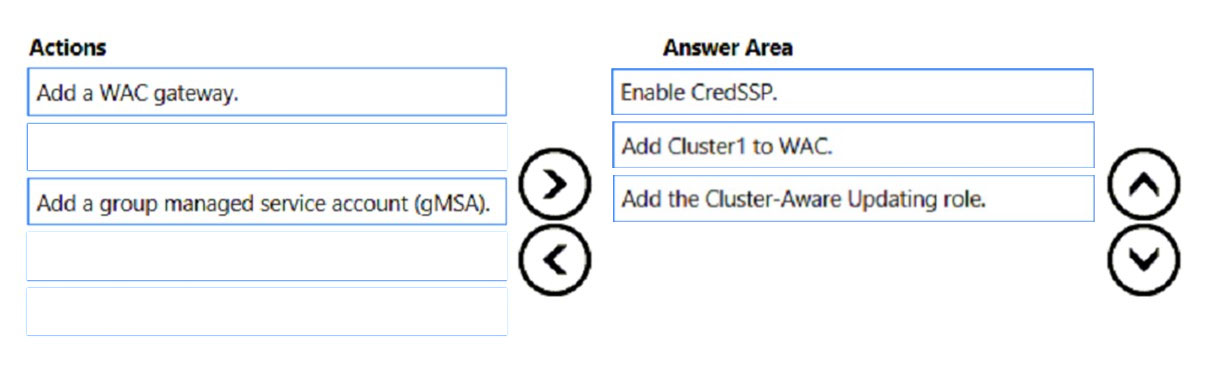
Step 1: Enable CredSSP -
Some tasks that require CredSSP to be enabled include:
Create Cluster wizard workflow -
Active Directory queries or updates
SQL Server queries or updates -
Locating accounts or computers on a different domain or non-domain joined environment
The Credential Security Support Provider protocol (CredSSP) is a Security Support Provider that is implemented by using the Security Support Provider Interface
(SSPI). CredSSP lets an application delegate the user's credentials from the client to the target server for remote authentication.
Step 2: Add Cluster1 to WAC -
Add the failover cluster to Windows Admin Center
Step 3: Add the Cluster-Aware Updating role.
Enabling self-updating mode.
To enable the self-updating mode, you must add the Cluster-Aware Updating clustered role to the failover cluster.
Incorrect:
* Failover clusters do not support gMSAs. However, services that run on top of the Cluster service can use a gMSA or a sMSA if they are a Windows service, an
App pool, a scheduled task, or natively support gMSA or sMSA.
* The Windows Admin Center gateway, when published to DNS and given access through corresponding corporate firewalls, lets you securely connect to, and manage, your servers from anywhere with Microsoft Edge or Google Chrome.
Reference:
https://docs.microsoft.com/en-us/azure-stack/hci/manage/troubleshoot-credssp https://docs.microsoft.com/en-us/windows-server/manage/windows-admin-center/use/manage-failover-clusters https://docs.microsoft.com/en-us/windows-server/failover-clustering/cluster-aware-updating

Step 1: Enable CredSSP -
Some tasks that require CredSSP to be enabled include:
Create Cluster wizard workflow -
Active Directory queries or updates
SQL Server queries or updates -
Locating accounts or computers on a different domain or non-domain joined environment
The Credential Security Support Provider protocol (CredSSP) is a Security Support Provider that is implemented by using the Security Support Provider Interface
(SSPI). CredSSP lets an application delegate the user's credentials from the client to the target server for remote authentication.
Step 2: Add Cluster1 to WAC -
Add the failover cluster to Windows Admin Center
Step 3: Add the Cluster-Aware Updating role.
Enabling self-updating mode.
To enable the self-updating mode, you must add the Cluster-Aware Updating clustered role to the failover cluster.
Incorrect:
* Failover clusters do not support gMSAs. However, services that run on top of the Cluster service can use a gMSA or a sMSA if they are a Windows service, an
App pool, a scheduled task, or natively support gMSA or sMSA.
* The Windows Admin Center gateway, when published to DNS and given access through corresponding corporate firewalls, lets you securely connect to, and manage, your servers from anywhere with Microsoft Edge or Google Chrome.
Reference:
https://docs.microsoft.com/en-us/azure-stack/hci/manage/troubleshoot-credssp https://docs.microsoft.com/en-us/windows-server/manage/windows-admin-center/use/manage-failover-clusters https://docs.microsoft.com/en-us/windows-server/failover-clustering/cluster-aware-updating
send
light_mode
delete
Question #34
You have a three-node failover cluster.
You need to run pre-scripts and post-scripts when Cluster-Aware Updating (CAU) runs. The solution must minimize administrative effort.
What should you use?
You need to run pre-scripts and post-scripts when Cluster-Aware Updating (CAU) runs. The solution must minimize administrative effort.
What should you use?
- AAzure Functions
- BRun profilesMost Voted
- CWindows Server Update Services (WSUS)
- DScheduled tasks
Correct Answer:
B
Cluster-Aware Updating advanced options and updating run profiles.
You can set the PreUpdateScript or PostUpdateScript the option.
Reference:
https://docs.microsoft.com/en-us/windows-server/failover-clustering/cluster-aware-updating-options
B
Cluster-Aware Updating advanced options and updating run profiles.
You can set the PreUpdateScript or PostUpdateScript the option.
Reference:
https://docs.microsoft.com/en-us/windows-server/failover-clustering/cluster-aware-updating-options
send
light_mode
delete
Question #35
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a failover cluster named Cluster1 that hosts an application named App1.
The General tab in App1 Properties is shown in the General exhibit. (Click the General tab.)
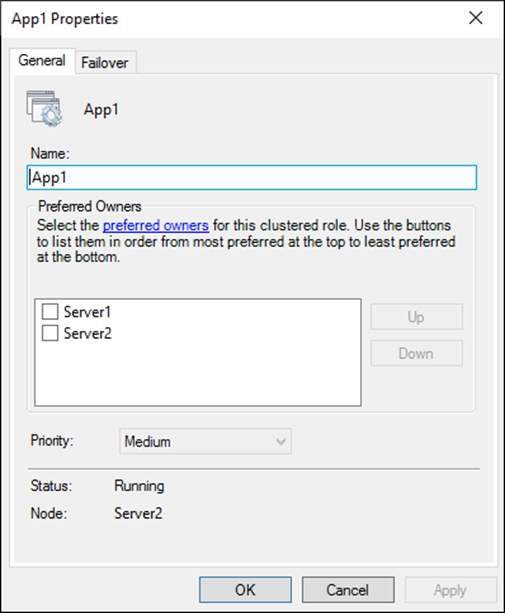
The Failover tab in App1 Properties is shown in the Failover exhibit. (Click the Failover tab.)
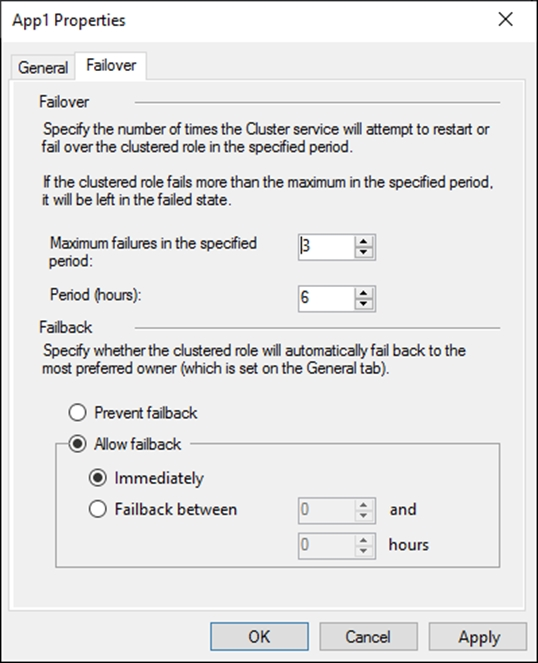
Server1 shuts down unexpectedly.
You need to ensure that when you start Server1, App1 continues to run on Server2.
Solution: You pause the Server1 node in Cluster1 and then start Server1.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a failover cluster named Cluster1 that hosts an application named App1.
The General tab in App1 Properties is shown in the General exhibit. (Click the General tab.)

The Failover tab in App1 Properties is shown in the Failover exhibit. (Click the Failover tab.)

Server1 shuts down unexpectedly.
You need to ensure that when you start Server1, App1 continues to run on Server2.
Solution: You pause the Server1 node in Cluster1 and then start Server1.
Does this meet the goal?
- AYes
- BNoMost Voted
Correct Answer:
B
Instead, from the Failover settings, you select Prevent failback
Note: The Prevent failback setting will prevent the cluster failing back to Server1.
Preventing failback.
A third potential setting is used after a resource's cluster node comes back online after a failover. Under the Failover tab is the Failback setting with the default setting "prevent failback." When failback is configured, the virtual machine will return back to its original host when that host is again available. If you want virtual machines to return to your known configuration after a host problem, this can be a good thing.
Reference:
https://www.computerweekly.com/tip/Configuring-cluster-failover-settings-for-Hyper-V-virtual-machines
B
Instead, from the Failover settings, you select Prevent failback
Note: The Prevent failback setting will prevent the cluster failing back to Server1.
Preventing failback.
A third potential setting is used after a resource's cluster node comes back online after a failover. Under the Failover tab is the Failback setting with the default setting "prevent failback." When failback is configured, the virtual machine will return back to its original host when that host is again available. If you want virtual machines to return to your known configuration after a host problem, this can be a good thing.
Reference:
https://www.computerweekly.com/tip/Configuring-cluster-failover-settings-for-Hyper-V-virtual-machines
send
light_mode
delete
Question #36
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a failover cluster named Cluster1 that hosts an application named App1.
The General tab in App1 Properties is shown in the General exhibit. (Click the General tab.)
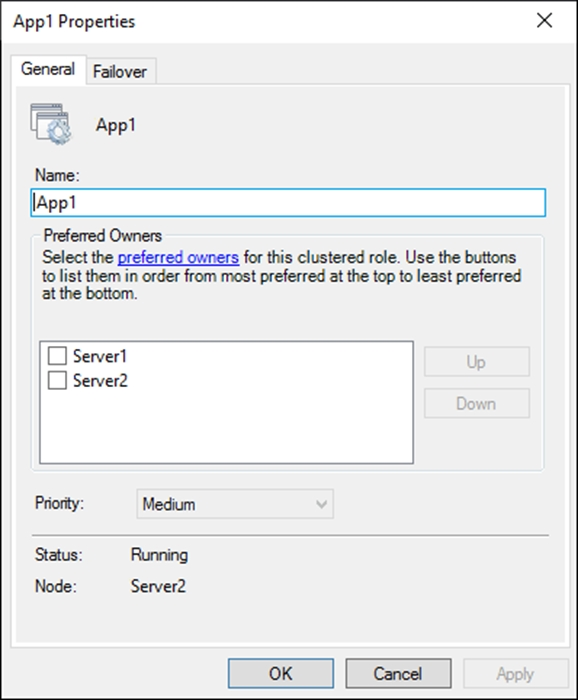
The Failover tab in App1 Properties is shown in the Failover exhibit. (Click the Failover tab.)
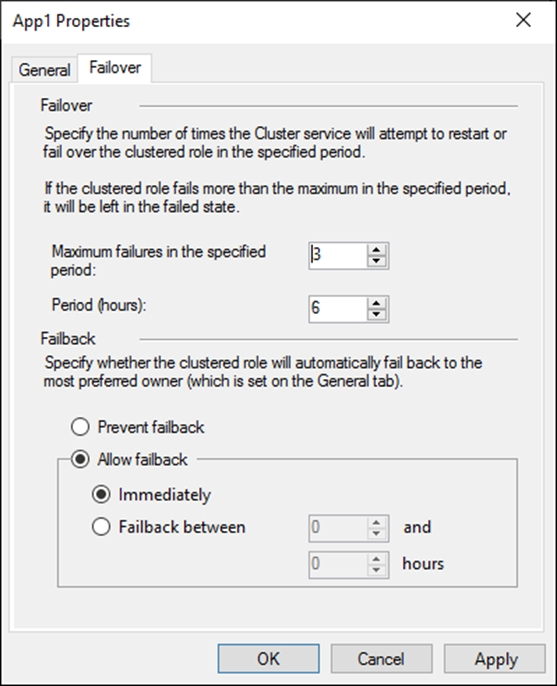
Server1 shuts down unexpectedly.
You need to ensure that when you start Server1, App1 continues to run on Server2.
Solution: From the General settings, you increase the priority of Server2 in the Preferred Owners list.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a failover cluster named Cluster1 that hosts an application named App1.
The General tab in App1 Properties is shown in the General exhibit. (Click the General tab.)

The Failover tab in App1 Properties is shown in the Failover exhibit. (Click the Failover tab.)

Server1 shuts down unexpectedly.
You need to ensure that when you start Server1, App1 continues to run on Server2.
Solution: From the General settings, you increase the priority of Server2 in the Preferred Owners list.
Does this meet the goal?
send
light_mode
delete
Question #37
HOTSPOT -
You have a Hyper-V failover cluster named Cluster1 at a main datacenter. Cluster1 contains two nodes that have the Hyper-V server role installed. Cluster1 hosts
10 highly available virtual machines.
You have a cluster named Cluster2 in a disaster recovery site. Cluster2 contains two nodes that have the Hyper-V server role installed.
You plan to use Hyper-V Replica to replicate the virtual machines from Cluster1 to Cluster2.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
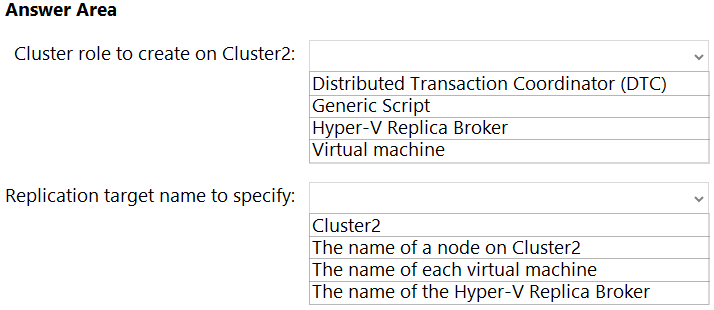
You have a Hyper-V failover cluster named Cluster1 at a main datacenter. Cluster1 contains two nodes that have the Hyper-V server role installed. Cluster1 hosts
10 highly available virtual machines.
You have a cluster named Cluster2 in a disaster recovery site. Cluster2 contains two nodes that have the Hyper-V server role installed.
You plan to use Hyper-V Replica to replicate the virtual machines from Cluster1 to Cluster2.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:
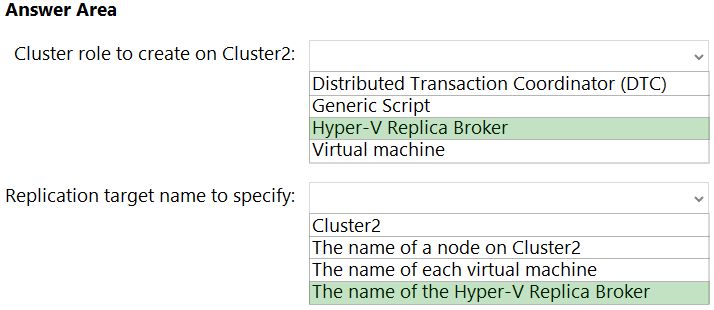
Reference:
https://docs.microsoft.com/en-us/virtualization/community/team-blog/2012/20120327-why-is-the-hyper-v-replica-broker-required

Reference:
https://docs.microsoft.com/en-us/virtualization/community/team-blog/2012/20120327-why-is-the-hyper-v-replica-broker-required
send
light_mode
delete
Question #38
You have two servers named Server1 and Server2 that run Windows Server. Both servers have the Hyper-V server role installed.
Server1 hosts three virtual machines named VM1, VM2, and VM3. The virtual machines replicate to Server2.
Server1 experiences a hardware failure.
You need to bring VM1, VM2, and VM3 back online as soon as possible.
From the Hyper-V Manager console on Server2, what should you run for each virtual machine?
Server1 hosts three virtual machines named VM1, VM2, and VM3. The virtual machines replicate to Server2.
Server1 experiences a hardware failure.
You need to bring VM1, VM2, and VM3 back online as soon as possible.
From the Hyper-V Manager console on Server2, what should you run for each virtual machine?
- AStart
- BMove
- CUnplanned FailoverMost Voted
- DPlanned Failover
Correct Answer:
C
Reference:
https://docs.microsoft.com/en-us/windows-server/virtualization/hyper-v/manage/set-up-hyper-v-replica
C
Reference:
https://docs.microsoft.com/en-us/windows-server/virtualization/hyper-v/manage/set-up-hyper-v-replica
send
light_mode
delete
Question #39
HOTSPOT -
You have a Hyper-V failover cluster named Cluster1 that uses a cloud witness. Cluster1 hosts a virtual machine named VM1 that runs Windows Server.
You need to fail over VM1 automatically to a different node when a service named Service1 on VM1 fails.
What should you do on Cluster1 and VM1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
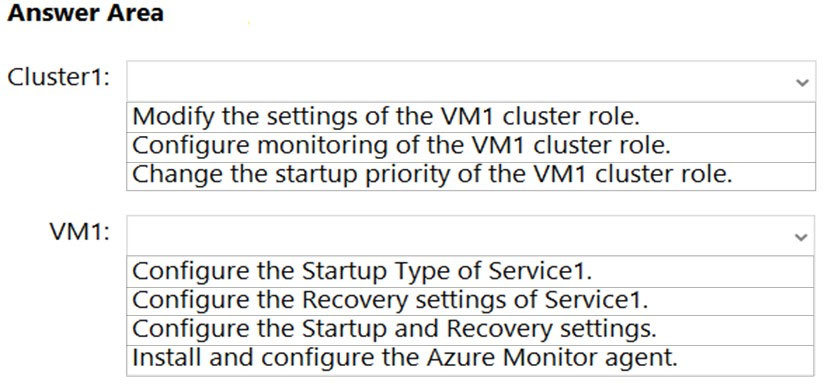
You have a Hyper-V failover cluster named Cluster1 that uses a cloud witness. Cluster1 hosts a virtual machine named VM1 that runs Windows Server.
You need to fail over VM1 automatically to a different node when a service named Service1 on VM1 fails.
What should you do on Cluster1 and VM1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:

send
light_mode
delete
Question #40
DRAG DROP -
You have two physical servers named AppSrv1 and AppSrv2 and an unconfigured server named Server1. All the servers run Windows Server. Only Server1 can access the internet.
You plan to use Azure Site Recovery to replicate AppSrv1 and AppSrv2 to Azure.
You need to deploy the required components to AppSrv1, AppSrv2, and Server1.
Which components should you deploy? To answer, drag the appropriate components to the correct servers. Each component may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:

You have two physical servers named AppSrv1 and AppSrv2 and an unconfigured server named Server1. All the servers run Windows Server. Only Server1 can access the internet.
You plan to use Azure Site Recovery to replicate AppSrv1 and AppSrv2 to Azure.
You need to deploy the required components to AppSrv1, AppSrv2, and Server1.
Which components should you deploy? To answer, drag the appropriate components to the correct servers. Each component may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:

Correct Answer:

Reference:
https://docs.microsoft.com/en-us/azure/site-recovery/physical-azure-architecture https://docs.microsoft.com/en-us/azure/site-recovery/physical-azure-set-up-source

Reference:
https://docs.microsoft.com/en-us/azure/site-recovery/physical-azure-architecture https://docs.microsoft.com/en-us/azure/site-recovery/physical-azure-set-up-source
send
light_mode
delete
All Pages