Microsoft 70-680 Exam Practice Questions (P. 4)
- Full Access (551 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #31
You have two computers named Computer1 and Computer2 that run Windows 7.
You need to ensure that you can remotely execute commands on Computer2 from Computer1.
What should you do?
You need to ensure that you can remotely execute commands on Computer2 from Computer1.
What should you do?
- ARun Winrm quickconfig on Computer1
- BRun Winrm quickconfig on Computer2
- CEnableWindows Remote Management (WinRM) through Windows Firewall on Computer1
- DEnable Windows Remote Management (WinRM) through Windows Firewall on Computer2
Correct Answer:
B
Windows Remote Management Service
The Windows Remote Management service allows you to execute commands on a remote computer, either from the command prompt using WinRS or from
Windows PowerShell. Before you can use WinRS or Windows PowerShell for remote management tasks, it is necessary to configure the target computer using the WinRM command. To configure the target computer, you must run the command WinRM quickconfig from an elevated command prompt. Executing WinRM quickconfig does the following:
✑ Starts the WinRM service
✑ Configures the WinRM service startup type to delayed automatic start
✑ Configures the LocalAccountTokenFilterPolicy to grant administrative rights remotely to local users
✑ Configures the WinRM listener on http://* to accept WS-Man requests
✑ Configures the WinRM firewall exception
B
Windows Remote Management Service
The Windows Remote Management service allows you to execute commands on a remote computer, either from the command prompt using WinRS or from
Windows PowerShell. Before you can use WinRS or Windows PowerShell for remote management tasks, it is necessary to configure the target computer using the WinRM command. To configure the target computer, you must run the command WinRM quickconfig from an elevated command prompt. Executing WinRM quickconfig does the following:
✑ Starts the WinRM service
✑ Configures the WinRM service startup type to delayed automatic start
✑ Configures the LocalAccountTokenFilterPolicy to grant administrative rights remotely to local users
✑ Configures the WinRM listener on http://* to accept WS-Man requests
✑ Configures the WinRM firewall exception
send
light_mode
delete
Question #32
You work in an international company which is named Wiikigo. Before entering this company, you have two years of experience in the IT field, as well as experience implementing and administering any Windows client operating system in a networked environment. You are professional in installing, upgrading and migrating to Windows 7, deploying Windows 7, and configuring Hardware and Applications and son on. You are in charge of two computers that are respectively named C01 and C02. C01 runs Windows 7 and C02 runs Windows XP Professional.
On C01, you enable Remote Desktop as shown in the Remote Desktop exhibit. What action should you perform?
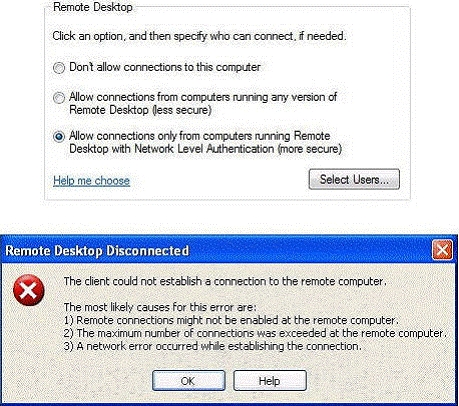
On C01, you enable Remote Desktop as shown in the Remote Desktop exhibit. What action should you perform?

- AYou should enable the Allow connections from computers running any version of Remote Desktop setting on C01.
- BThe Client (Respond Only) IPSec policy should be assigned on C02.
- CYour user account should be added to the Remote Desktop Users group on C01.
- DA firewall exception should be created for the Remote Desktop Protocol (RDP) should be assigned on C02.
Correct Answer:
A
A
send
light_mode
delete
Question #33
You have a computer that runs Windows 7. The computer connects to the corporate network by using a VPN connection.
You need to ensure that you can access the Internet when the VPN connection is active. The solution must prevent Internet traffic from being routed through the
VPN connection.
What should you do?
You need to ensure that you can access the Internet when the VPN connection is active. The solution must prevent Internet traffic from being routed through the
VPN connection.
What should you do?
- AConfigure a static DNS server address.
- BConfigure a static IP address and default gateway.
- CConfigure the security settings of the VPN connection.
- DConfigure the advanced TCP/IP settings of the VPN connection.
Correct Answer:
D
To prevent the default route from being created
In the properties of the TCP/IP protocol of the dial-up connection object, in the Advanced TCP/IP Settings dialog box, click the General tab, and then clear the Use default gateway on remote network check box.
D
To prevent the default route from being created
In the properties of the TCP/IP protocol of the dial-up connection object, in the Advanced TCP/IP Settings dialog box, click the General tab, and then clear the Use default gateway on remote network check box.
send
light_mode
delete
Question #34
You have a stand-alone computer that runs Windows 7.
You open Windows Update as shown in the exhibit. (Click the Exhibit button.)
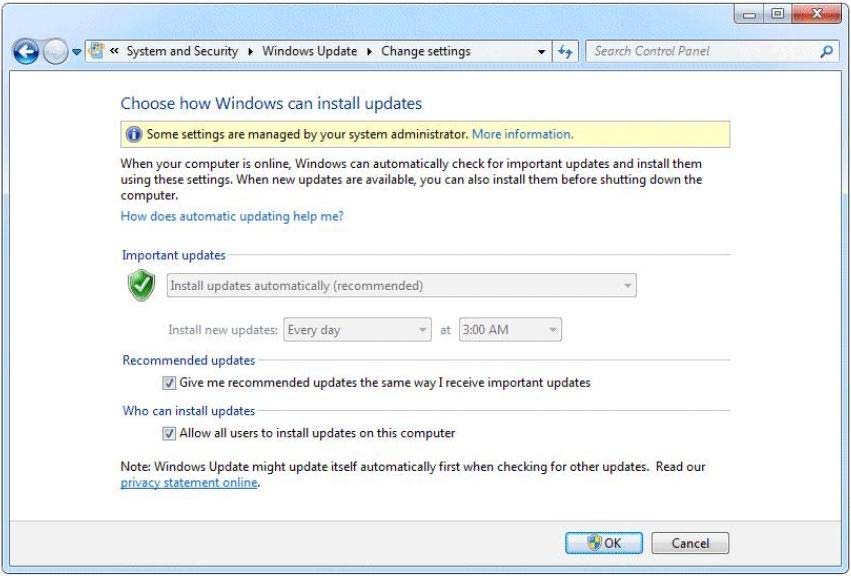
You need to ensure that you can manually change the Windows Update settings on the computer.
What should you do?
You open Windows Update as shown in the exhibit. (Click the Exhibit button.)

You need to ensure that you can manually change the Windows Update settings on the computer.
What should you do?
- ALog on to Windows 7 as member of the Administrators group.
- BFrom the local Group Policy, modify the Windows Update settings.
- CRight-click Windows Update and select Run as administrator.
- DRight-click the command prompt, select Run as administrator, and then run Wuapp.exe.
Correct Answer:
B
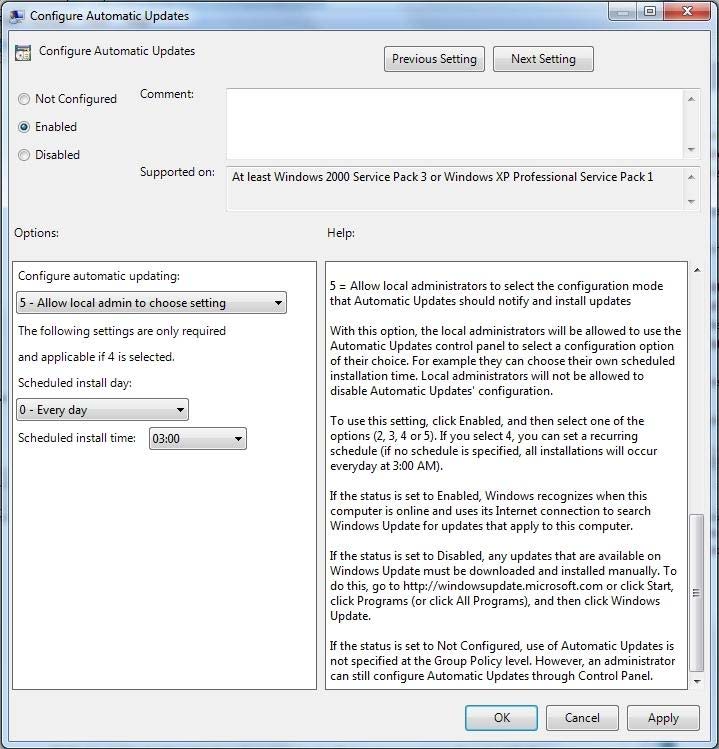
Configuring Automatic Updates by using local Group Policy
✑ Click Start, and then click Run.
✑ Type gpedit.msc, and then click OK.
✑ Expand Computer Configuration.
✑ Right-click Administrative Templates, and then click Add/Remove Templates.
✑ Click Add, click Wuau.adm in the Windows\Inf folder, and then click Open.
✑ Click Close.
Under Computer Configuration, expand Administrative Templates, expand Windows Components, and then expand Windows Update.

B
Configuring Automatic Updates by using local Group Policy
✑ Click Start, and then click Run.
✑ Type gpedit.msc, and then click OK.
✑ Expand Computer Configuration.
✑ Right-click Administrative Templates, and then click Add/Remove Templates.
✑ Click Add, click Wuau.adm in the Windows\Inf folder, and then click Open.
✑ Click Close.
Under Computer Configuration, expand Administrative Templates, expand Windows Components, and then expand Windows Update.


send
light_mode
delete
Question #35
You have a computer that runs Windows 7 Professional. A USB disk is attached to the computer.
You need to ensure that you can enable BitLocker to go on the USB disk.
What should you do?
You need to ensure that you can enable BitLocker to go on the USB disk.
What should you do?
- AEnable Encrypting File System (EFS).
- BUpgrade the computer to Windows 7 Enterprise.
- CInitialize the Trusted Platform Module (TPM) hardware.
- DObtain a client certificate from an enterprise certification authority (CA).
Correct Answer:
B
Windows 7 Professional -
Windows 7 Professional is available from retailers and on new computers installed by manufacturers. It supports all the features available in Windows Home
Premium, but you can join computers with this operating system installed to a domain. It supports EFS and Remote Desktop Host but does not support enterprise features such as AppLocker, DirectAccess, BitLocker, and Branch Cache.
Windows 7 Enterprise and Ultimate Editions
The Windows 7 Enterprise and Ultimate editions are identical except for the fact that Windows 7 Enterprise is available only to Microsofts volume licensing customers, and Windows 7 Ultimate is available from retailers and on new computers installed by manufacturers. The Enterprise and Ultimate editions support all the features available in other Windows 7 editions but also support all the enterprise features such as EFS, Remote Desktop Host, AppLocker, Direct Access,
BitLocker, BranchCache, and Boot from VHD.
B
Windows 7 Professional -
Windows 7 Professional is available from retailers and on new computers installed by manufacturers. It supports all the features available in Windows Home
Premium, but you can join computers with this operating system installed to a domain. It supports EFS and Remote Desktop Host but does not support enterprise features such as AppLocker, DirectAccess, BitLocker, and Branch Cache.
Windows 7 Enterprise and Ultimate Editions
The Windows 7 Enterprise and Ultimate editions are identical except for the fact that Windows 7 Enterprise is available only to Microsofts volume licensing customers, and Windows 7 Ultimate is available from retailers and on new computers installed by manufacturers. The Enterprise and Ultimate editions support all the features available in other Windows 7 editions but also support all the enterprise features such as EFS, Remote Desktop Host, AppLocker, Direct Access,
BitLocker, BranchCache, and Boot from VHD.
send
light_mode
delete
Question #36
You work in an international company which is named Wiikigo. Before entering this company, you have two years of experience in the IT field, as well as experience implementing and administering any Windows client operating system in a networked environment. You are professional in installing, upgrading and migrating to Windows 7, deploying Windows 7, and configuring Hardware and Applications and son on. You manage a stand-alone computer which has only one partition. Windows 7 is run by this computer. The computer is shared by two users that are respectively named User1 and User2. User01 uses Encrypting File
System (EFS) to encrypt a file. User01 tries to grant User2 access to the file as shown in the exhibit. You have to make sure that User1 are able to grant User2 access to the file. So what action should you perform to make sure of this?
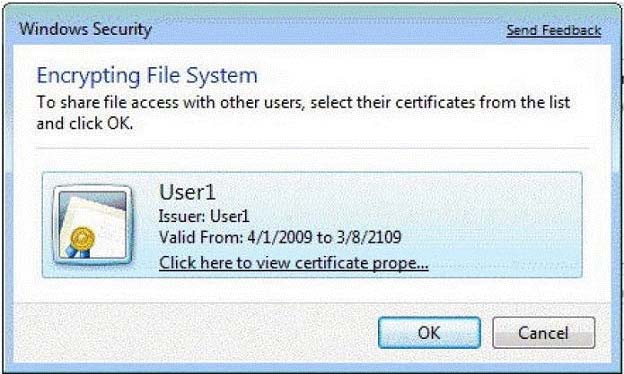
System (EFS) to encrypt a file. User01 tries to grant User2 access to the file as shown in the exhibit. You have to make sure that User1 are able to grant User2 access to the file. So what action should you perform to make sure of this?

- AUser02 should be instructed to log on to the computer and take ownership of the file.
- BUser02 should be instructed to log on to the computer and encrypt a file.
- CUser1 should be instructed to exporthis certificate to a certificate (.cer) file.
- DUser01 should be instructed to move the file to a shared folder on the computer.
Correct Answer:
B
B
send
light_mode
delete
Question #37
You have a computer that runs Windows 7.
You need to configure the computer to download updates from a local Windows Server Update Services (WSUS) server. What should you do?
You need to configure the computer to download updates from a local Windows Server Update Services (WSUS) server. What should you do?
- AFrom Windows Update, modify the Windows Update settings.
- BFrom the local Group Policy, modify the Windows Update settings.
- CFrom the System settings, modify the System Protection settings.
- DFrom the local Group Policy, modify the Location and Sensors settings.
Correct Answer:
B
B
send
light_mode
delete
Question #38
You have a reference computer that runs Windows 7.
You plan to create an image of the computer and then deploy the image to 100 computers.
You need to prepare the reference computer for imaging.
What should you do before you create the image?
You plan to create an image of the computer and then deploy the image to 100 computers.
You need to prepare the reference computer for imaging.
What should you do before you create the image?
- ARun Package Manager.
- BRun the System Preparation tool.
- CInstall the User State Migration Tool.
- DInstall Windows Automated Installation Kit.
Correct Answer:
B
Sysprep is a tool designed for corporate system administrators, OEMs, and others who need to deploy the Windows XP operating system on multiple computers.
After performing the initial setup steps on a single system, you can run Sysprep to prepare the sample computer for cloning. Sysprep prepares the image for capture by cleaning up various user-specific and computer-specific settings, as well as log files. The reference installation now is complete and ready to be imaged.
B
Sysprep is a tool designed for corporate system administrators, OEMs, and others who need to deploy the Windows XP operating system on multiple computers.
After performing the initial setup steps on a single system, you can run Sysprep to prepare the sample computer for cloning. Sysprep prepares the image for capture by cleaning up various user-specific and computer-specific settings, as well as log files. The reference installation now is complete and ready to be imaged.
send
light_mode
delete
Question #39
You plan to install Windows 7 by using a Windows 7 DVD.
You need to perform an automated installation of Windows 7.
What should you do?
You need to perform an automated installation of Windows 7.
What should you do?
- ACreate an answer file named oobe.xml. Copy the file to a network share.
- BCreate an answer file named winnt.sif. Place the file on a removable drive.
- CCreate an answer file named sysprep.inf. Copy the file to a network share.
- DCreate an answer file named autounattend.xml. Place the file on a removable drive.
Correct Answer:
D
D
send
light_mode
delete
Question #40
You have a computer that runs Windows 7.
You need to prevent Internet Explorer from saving any data during a browsing session.
What should you do?
You need to prevent Internet Explorer from saving any data during a browsing session.
What should you do?
- ADisable the BranchCache service.
- BModify the InPrivate Blocking list.
- COpen an InPrivate Browsing session.
- DModify the security settings for the Internet zone.
Correct Answer:
C
InPrivate Mode consists of two technologies: InPrivate Filtering and InPrivate Browsing. Both InPrivate Filtering and InPrivate Browsing are privacy technologies that restrict the amount of information available about a users browsing session. InPrivate Browsing restricts what data is recorded by the browser, and InPrivate
Filtering is used to restrict what information about a browsing session can be tracked by external third parties.
C
InPrivate Mode consists of two technologies: InPrivate Filtering and InPrivate Browsing. Both InPrivate Filtering and InPrivate Browsing are privacy technologies that restrict the amount of information available about a users browsing session. InPrivate Browsing restricts what data is recorded by the browser, and InPrivate
Filtering is used to restrict what information about a browsing session can be tracked by external third parties.
send
light_mode
delete
All Pages
