Microsoft 70-680 Exam Practice Questions (P. 3)
- Full Access (551 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #21
You have a computer named Computer1 that runs Windows 7.
You need to ensure that Computer1 can connect to File Transfer Protocol (FTP) servers only while it is connected to a private network.
What should you do?
You need to ensure that Computer1 can connect to File Transfer Protocol (FTP) servers only while it is connected to a private network.
What should you do?
- AFrom Windows Firewall with Advanced Security, create a new rule.
- BFrom the local Group Policy, modify the application control policies.
- CFrom Windows Firewall, modify the Allowed Programs and Features list.
- DFrom Network and Sharing Center, modify the Advanced Sharing settings.
Correct Answer:
A
Creating WFAS Rules -
The process for configuring inbound rules and outbound rules is essentially the same: In the WFAS console, select the node that represents the type of rule that you want to create and then click New Rule. This opens the New Inbound (or Outbound) Rule Wizard. The first page, shown in Figure 7-7, allows you to specify the type of rule that you are going to create. You can select between a program, port, predefined, or custom rule. The program and predefined rules are similar to what you can create using Windows Firewall. A custom rule allows you to configure a rule based on criteria not covered by any of the other options. You would create a custom rule if you wanted a rule that applied to a particular service rather than a program or port. You can also use a custom rule if you want to create a rule that involves both a specific program and a set of ports. For example, if you wanted to allow communication to a specific program on a certain port but not other ports, you would create a custom rule.
A
Creating WFAS Rules -
The process for configuring inbound rules and outbound rules is essentially the same: In the WFAS console, select the node that represents the type of rule that you want to create and then click New Rule. This opens the New Inbound (or Outbound) Rule Wizard. The first page, shown in Figure 7-7, allows you to specify the type of rule that you are going to create. You can select between a program, port, predefined, or custom rule. The program and predefined rules are similar to what you can create using Windows Firewall. A custom rule allows you to configure a rule based on criteria not covered by any of the other options. You would create a custom rule if you wanted a rule that applied to a particular service rather than a program or port. You can also use a custom rule if you want to create a rule that involves both a specific program and a set of ports. For example, if you wanted to allow communication to a specific program on a certain port but not other ports, you would create a custom rule.
send
light_mode
delete
Question #22
You work in an international company which is named Wiikigo. Before entering this company, you have two years of experience in the IT field, as well as experience implementing and administering any Windows client operating system in a networked environment. You are professional in installing, upgrading and migrating to Windows 7, deploying Windows 7, and configuring Hardware and Applications and son on. You use a computer that runs Windows 7.
Now your company assigns a task to you. You are asked to prevent users from copying unencrypted files to removable drives. What action should you perform?
Now your company assigns a task to you. You are asked to prevent users from copying unencrypted files to removable drives. What action should you perform?
- AThe Trusted Platform Module (TPM) settings should be modified from a local Group Policy.
- BTPM should be initialized from the Trusted Platform Module (TPM) snap-in.
- CThe BitLocker Drive Encryption settings should be modified from Control Panel.
- DThe BitLocker Drive Encryption settings should be modified from a local Group Policy.
Correct Answer:
D
D
send
light_mode
delete
Question #23
Your network has a main office and a branch office. The branch office has computers that run Windows 7. A network administrator enables BranchCache in the main office. You run Netsh on your computer as shown in the exhibit. (Click the Exhibit button.)
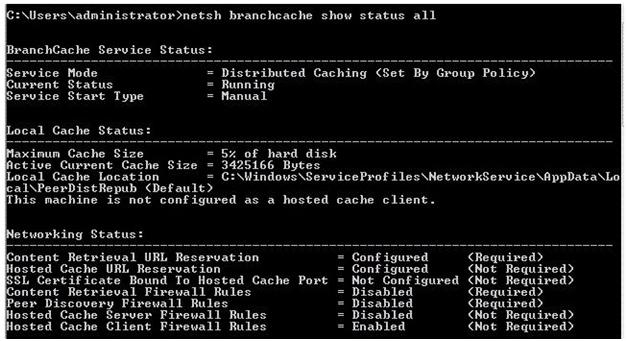
You need to ensure that other computers in the branch office can access the cached content on your computer.
What should you do?

You need to ensure that other computers in the branch office can access the cached content on your computer.
What should you do?
- ATurn on Internet Information Services (IIS).
- BConfigure the computer as a hosted cache client.
- CConfigure the BranchCache service to start automatically.
- DModify the Windows Firewall with Advanced Security rules.
Correct Answer:
D
Distributed Cache Mode -
Distributed Cache mode uses peer caching to host the branch office cache among clients running Windows 7 on the branch office network. This means that each
Distributed Cache mode client hosts part of the cache, but no single client hosts all the cache. When a client running Windows 7 retrieves content over the WAN, it places that content into its own cache. If another BranchCache client running Windows 7 attempts to access the same content, it is able to access that content directly from the first client rather than having to retrieve it over the WAN link. When it accesses the file from its peer, it also copies that file into its own cache.
When you configure BranchCache in distributed cache mode, BranchCache client computers use the Hypertext Transfer Protocol (HTTP) for data transfer with other client computers. BranchCache client computers also use the Web Services Dynamic Discovery (WS-Discovery) protocol when they attempt to discover content on client cache servers. You can use this procedure to configure client firewall exceptions to allow incoming HTTP and WS-Discovery traffic on client computers that are configured for distributed cache mode.
You must select Allow the connection for the BranchCache client to be able to send traffic on this port.
D
Distributed Cache Mode -
Distributed Cache mode uses peer caching to host the branch office cache among clients running Windows 7 on the branch office network. This means that each
Distributed Cache mode client hosts part of the cache, but no single client hosts all the cache. When a client running Windows 7 retrieves content over the WAN, it places that content into its own cache. If another BranchCache client running Windows 7 attempts to access the same content, it is able to access that content directly from the first client rather than having to retrieve it over the WAN link. When it accesses the file from its peer, it also copies that file into its own cache.
When you configure BranchCache in distributed cache mode, BranchCache client computers use the Hypertext Transfer Protocol (HTTP) for data transfer with other client computers. BranchCache client computers also use the Web Services Dynamic Discovery (WS-Discovery) protocol when they attempt to discover content on client cache servers. You can use this procedure to configure client firewall exceptions to allow incoming HTTP and WS-Discovery traffic on client computers that are configured for distributed cache mode.
You must select Allow the connection for the BranchCache client to be able to send traffic on this port.
send
light_mode
delete
Question #24
You have a computer that runs Windows 7.
A printer is installed on the computer.
You remove the Everyone group from the access control list (ACL) for the printer, and then you share the printer.
You need to ensure that members of the Sales group can modify all the print jobs that they submit.
You must prevent Sales group members from modifying the print jobs of other users.
What should you do?
A printer is installed on the computer.
You remove the Everyone group from the access control list (ACL) for the printer, and then you share the printer.
You need to ensure that members of the Sales group can modify all the print jobs that they submit.
You must prevent Sales group members from modifying the print jobs of other users.
What should you do?
- AFrom the printer's properties, assign the Print permission to the Sales group.
- BFrom the printer's properties, assign the Manage Documents permission to the Sales group.
- CFrom the local Group Policy, assign the Increase scheduling priority user right to the Sales group.
- DFrom the local Group Policy, assign the Take ownership of files or other objects user right to the Sales group.
Correct Answer:
A
The available permissions are:
✑ Print This permission allows a user to print to the printer and rearrange the documents that they have submitted to the printer.
✑ Manage This Printer Users assigned the Manage This Printer permission can pause and restart the printer, change spooler settings, adjust printer permissions, change printer properties, and share a printer.
✑ Manage Documents This permission allows users or groups to pause, resume, restart, cancel, or reorder the documents submitted by users that are in the current print queue.
A
The available permissions are:
✑ Print This permission allows a user to print to the printer and rearrange the documents that they have submitted to the printer.
✑ Manage This Printer Users assigned the Manage This Printer permission can pause and restart the printer, change spooler settings, adjust printer permissions, change printer properties, and share a printer.
✑ Manage Documents This permission allows users or groups to pause, resume, restart, cancel, or reorder the documents submitted by users that are in the current print queue.
send
light_mode
delete
Question #25
You work in an international company which is named Wiikigo. Before entering this company, you have two years of experience in the IT field, as well as experience implementing and administering any Windows client operating system in a networked environment. You are professional in installing, upgrading and migrating to Windows 7, deploying Windows 7, and configuring Hardware and Applications and son on. You have a computer that runs Windows 7.
You run Runas and specify the /savecred parameter to start an application.
The stored password needs to be deleted.
What action should you perform?
You run Runas and specify the /savecred parameter to start an application.
The stored password needs to be deleted.
What action should you perform?
- AThe Windows credentials should be modified from Credential Manager.
- BThe Authorization Manager options should be modified from Authorization Manager.
- CDel should be run and the /p parameter should be specified.
- DRun as should be run and the /noprofile parameter should be specified.
Correct Answer:
A
A
send
light_mode
delete
Question #26
You have a computer that runs Windows 7. The computer has System Protection enabled.
You need to retain only the last System Protection snapshot of the computer. All other snapshots must be deleted.
What should you do?
You need to retain only the last System Protection snapshot of the computer. All other snapshots must be deleted.
What should you do?
- ARun Disk Cleanup for Programs and features.
- BRun Disk Cleanup for System Restore and Shadow Copies.
- CFrom the System Protection Restore settings, select Turn off System Restore.
- DFrom the System Protection Restore settings, select Only restore previous versions of files.
Correct Answer:
B
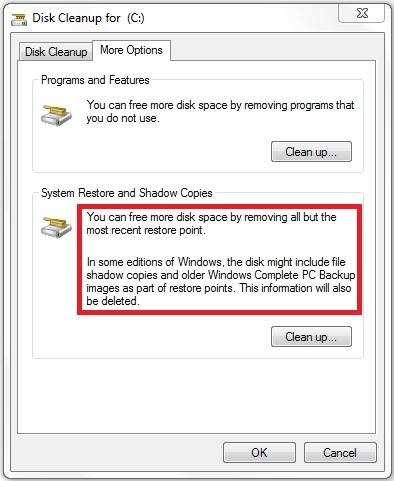
Shadow info:
Shadow copies are automatically saved as part of a restore point. If system protection is enabled, Windows 7 automatically creates shadow copies of files that have been modified since the last restore point was created. By default, new restore points are created every seven days or whenever a significant system change
(such as a driver or application installation) occurs.
B

Shadow info:
Shadow copies are automatically saved as part of a restore point. If system protection is enabled, Windows 7 automatically creates shadow copies of files that have been modified since the last restore point was created. By default, new restore points are created every seven days or whenever a significant system change
(such as a driver or application installation) occurs.
send
light_mode
delete
Question #27
You have a reference computer that runs Windows 7.
You plan to deploy an image of the computer.
You create an answer file named answer.xml.
You need to ensure that the installation applies the answer file after you deploy the image.
Which command should you run before you capture the image?
You plan to deploy an image of the computer.
You create an answer file named answer.xml.
You need to ensure that the installation applies the answer file after you deploy the image.
Which command should you run before you capture the image?
- AImagex.exe /append answer.xml /check
- BImagex.exe /mount answer.xml /verify
- CSysprep.exe /reboot /audit /unattend:answer.xml
- DSysprep.exe/generalize /oobe /unattend:answer.xml
Correct Answer:
D
To prepare the reference computer for the user, you use the Sysprep utility with the /generalize option to remove hardware-specific information from the Windows installation and the /oobe option to configure the computer to boot to Windows Welcome upon the next restart. Open an elevated command prompt on the reference computer and run the following command: c:\windows\system32\sysprep\sysprep.exe /oobe /generalize /shutdown Sysprep prepares the image for capture by cleaning up various user-specific and computer-specific settings, as well as log files. The reference installation now is complete and ready to be imaged.
D
To prepare the reference computer for the user, you use the Sysprep utility with the /generalize option to remove hardware-specific information from the Windows installation and the /oobe option to configure the computer to boot to Windows Welcome upon the next restart. Open an elevated command prompt on the reference computer and run the following command: c:\windows\system32\sysprep\sysprep.exe /oobe /generalize /shutdown Sysprep prepares the image for capture by cleaning up various user-specific and computer-specific settings, as well as log files. The reference installation now is complete and ready to be imaged.
send
light_mode
delete
Question #28
You have a Virtual Hard Disk (VHD) and a computer that runs Windows 7. The VHD has Windows 7 installed.
You need to start the computer from the VHD.
What should you do?
You need to start the computer from the VHD.
What should you do?
- AFrom Diskpart.exe, run Select vdisk.
- BFrom Disk Management, modify the active partition.
- CRun Bootcfg.exe and specify the /default parameter.
- DRun Bcdedit.exe and modify the Windows Boot Manager settings. D
Correct Answer:
Explanation
When you have created a VHD and installed a system image on it, you can use the BCDEdit tool Bcdedit.exe to add a boot entry for the VHD file in your computer running Windows 7.
Explanation
When you have created a VHD and installed a system image on it, you can use the BCDEdit tool Bcdedit.exe to add a boot entry for the VHD file in your computer running Windows 7.
send
light_mode
delete
Question #29
You have a computer that runs Windows 7. Your company has a corporate intranet Web site. You open Windows Internet Explorer as shown in the exhibit. (Click the Exhibit button.)
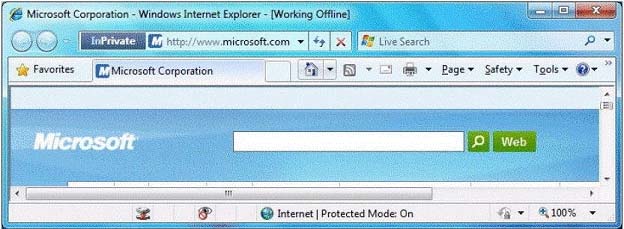
You need to ensure that you can access Web pages on both the Internet and the intranet.
What should you do?

You need to ensure that you can access Web pages on both the Internet and the intranet.
What should you do?
- AFrom the Files menu, click Work Offline.
- BFrom the Safety menu, click InPrivate Filtering.
- CFrom the Security tab, add the intranet Web site to the Trusted sites zone.
- DFrom the Safety menu, click InPrivate Browsing.
Correct Answer:
A
Working Offline is activated -
On Internet Explorer’s File menu is a "Work Offline" item that toggles Internet Explorer between online and offline modes of operation.
A
Working Offline is activated -
On Internet Explorer’s File menu is a "Work Offline" item that toggles Internet Explorer between online and offline modes of operation.
send
light_mode
delete
Question #30
You have a wireless access point that is configured to use Advanced Encryption Standard (AES) security. A pre-shared key is not configured on the wireless access point.
You need to connect a computer that runs Windows 7 to the wireless access point.
Which security setting should you select for the wireless connection?
You need to connect a computer that runs Windows 7 to the wireless access point.
Which security setting should you select for the wireless connection?
- A802.1x
- BWPA-Personal
- CWPA2-Enterprise
- DWPA2-Personal
Correct Answer:
C
WPA and WPA2 indicate compliance with the security protocol created by the Wi-Fi Alliance to secure wireless computer networks. WPA2 enhances WPA, which in turn addresses weaknesses in the previous system, WEP. WPA was intended as an intermediate measure to take the place of WEP while an IEEE 802.11i standard was prepared. 802.1X provides port-based authentication, which involves communications between a supplicant (a client computer), an authenticator (a wired Ethernet switch or WAP), and an authentication server (typically a Remote Authentication Dial In User Service, or RADIUS, server).
WPA2-Enterprise -
WPA-Enterprise and WPA2-Enterprise authenticate through the Extensible Authentication Protocol (EAP) and require computer security certificates rather than
PSKs. The following EAP types are included in the certification program:
✑ EAP-TLS
✑ EAP-TTLS/MSCHAPv2
✑ PEAPv0/EAP-MSCHAPv2
✑ PEAPv1/EAP-GTC
EAP-SIM -

If you want to use AES and to use computer certificates rather than a PSK, you would choose WPA2- Enterprise.
C
WPA and WPA2 indicate compliance with the security protocol created by the Wi-Fi Alliance to secure wireless computer networks. WPA2 enhances WPA, which in turn addresses weaknesses in the previous system, WEP. WPA was intended as an intermediate measure to take the place of WEP while an IEEE 802.11i standard was prepared. 802.1X provides port-based authentication, which involves communications between a supplicant (a client computer), an authenticator (a wired Ethernet switch or WAP), and an authentication server (typically a Remote Authentication Dial In User Service, or RADIUS, server).
WPA2-Enterprise -
WPA-Enterprise and WPA2-Enterprise authenticate through the Extensible Authentication Protocol (EAP) and require computer security certificates rather than
PSKs. The following EAP types are included in the certification program:
✑ EAP-TLS
✑ EAP-TTLS/MSCHAPv2
✑ PEAPv0/EAP-MSCHAPv2
✑ PEAPv1/EAP-GTC
EAP-SIM -

If you want to use AES and to use computer certificates rather than a PSK, you would choose WPA2- Enterprise.
send
light_mode
delete
All Pages
