Microsoft 70-341 Exam Practice Questions (P. 5)
- Full Access (183 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #21
DRAG DROP -
You have an Exchange Server 2013 organization that contains several custom RBAC management roles.
You need to identify which RBAC scopes must be used to meet the following requirements:
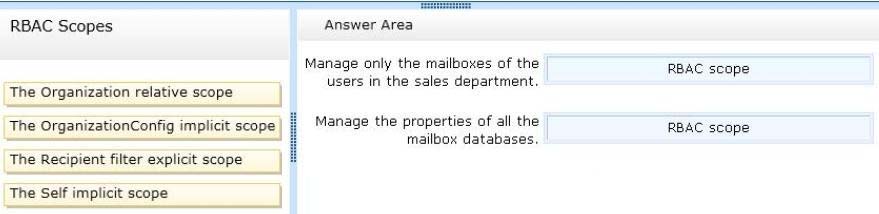
✑ Manage only the mailboxes of the users in the sales department.
✑ Manage the properties of all the mailbox databases.
Which RBAC scopes should you identify? (To answer, drag the appropriate RBAC scopes to the correct requirements. Each RBAC scope may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)
Select and Place:
You have an Exchange Server 2013 organization that contains several custom RBAC management roles.
You need to identify which RBAC scopes must be used to meet the following requirements:
✑ Manage only the mailboxes of the users in the sales department.
✑ Manage the properties of all the mailbox databases.
Which RBAC scopes should you identify? (To answer, drag the appropriate RBAC scopes to the correct requirements. Each RBAC scope may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)
Select and Place:
Correct Answer:
Management role scopes enable you to define the specific scope of impact or influence of a management role when a management role assignment is created.
When you apply a scope, the role assignee assigned to the role can only modify the objects contained within that scope.
A role assignee can be a management role group, management role, management role assignment policy, user, or universal security group (USG)
Every management role, whether it's a built-in role or a custom role, has management scopes. Management scopes can be either of the following:
Implicit scopes are the default scopes that apply to a management role type. Because implicit scopes are associated with a management role type, all of the parent and child management roles with the same role type also have the same implicit scopes.
Implicit scopes apply to both built-in management roles and also to custom management roles.
Implicit scopes defined on management roles
Implicit scopes Description -
Organization If Organization is present in the role's recipient write scope, the role can create or modify recipient objects across the Exchange organization.
If Organization is present in the role's recipient read scope, roles can view any recipient object across the Exchange organization.
Explicit scopes are scopes that you set yourself to control which objects a management role can modify. Although implicit scopes are defined on a management role, explicit scopes are defined on a management role assignment.
This enables the implicit scopes to be applied consistently across all management roles unless you choose to use an overriding explicit scope. For more information about management role assignments, see Understanding Management Role Assignments.
Explicit scopes override the implicit write and configuration scopes of a management role. They don't override the implicit read scope of a management role. The implicit read scope continues to define what objects the management role can read.
Explicit scopes are useful when the implicit write scope of a management role doesn't meet the needs of your business. You can add an explicit scope to include nearly anything you want as long as the new scope doesn't exceed the bounds of the implicit read scope. The cmdlets that are part of a management role must be able to read information about the objects or containers that contain objects for the cmdlets to create or modify objects. For example, if the implicit read scope on a management role is set to Self, you can't add an explicit write scope of Organization because the explicit write scope exceeds the bounds of the implicit read scope.
The OrganizationConfig implicit scope
If OrganizationConfig is present in the role's configuration write scope, the role can create or modify any server or database configuration object across the
Exchange organization.
If OrganizationConfig is present in the role's configuration read scope, the role can view any server or database configuration object across the Exchange organization.
The Recipient filter explicit scope
Recipient filter scopes use filters to target specific recipients based on recipient type or other recipient properties such as department, manager, location, and more.
References:

Management role scopes enable you to define the specific scope of impact or influence of a management role when a management role assignment is created.
When you apply a scope, the role assignee assigned to the role can only modify the objects contained within that scope.
A role assignee can be a management role group, management role, management role assignment policy, user, or universal security group (USG)
Every management role, whether it's a built-in role or a custom role, has management scopes. Management scopes can be either of the following:
Implicit scopes are the default scopes that apply to a management role type. Because implicit scopes are associated with a management role type, all of the parent and child management roles with the same role type also have the same implicit scopes.
Implicit scopes apply to both built-in management roles and also to custom management roles.
Implicit scopes defined on management roles
Implicit scopes Description -
Organization If Organization is present in the role's recipient write scope, the role can create or modify recipient objects across the Exchange organization.
If Organization is present in the role's recipient read scope, roles can view any recipient object across the Exchange organization.
Explicit scopes are scopes that you set yourself to control which objects a management role can modify. Although implicit scopes are defined on a management role, explicit scopes are defined on a management role assignment.
This enables the implicit scopes to be applied consistently across all management roles unless you choose to use an overriding explicit scope. For more information about management role assignments, see Understanding Management Role Assignments.
Explicit scopes override the implicit write and configuration scopes of a management role. They don't override the implicit read scope of a management role. The implicit read scope continues to define what objects the management role can read.
Explicit scopes are useful when the implicit write scope of a management role doesn't meet the needs of your business. You can add an explicit scope to include nearly anything you want as long as the new scope doesn't exceed the bounds of the implicit read scope. The cmdlets that are part of a management role must be able to read information about the objects or containers that contain objects for the cmdlets to create or modify objects. For example, if the implicit read scope on a management role is set to Self, you can't add an explicit write scope of Organization because the explicit write scope exceeds the bounds of the implicit read scope.
The OrganizationConfig implicit scope
If OrganizationConfig is present in the role's configuration write scope, the role can create or modify any server or database configuration object across the
Exchange organization.
If OrganizationConfig is present in the role's configuration read scope, the role can view any server or database configuration object across the Exchange organization.
The Recipient filter explicit scope
Recipient filter scopes use filters to target specific recipients based on recipient type or other recipient properties such as department, manager, location, and more.
References:
send
light_mode
delete
Question #22
Your network contains an Active Directory forest named contoso.com. The forest contains four sites named Site1, Site2, Site3, and Site4.
You have an Exchange Server 2013 organization that contains several servers in each site.
You need to prevent users who have mailboxes in Site2 from sending email messages that are larger than 2 MB to recipients in Site3.
What should you do?
You have an Exchange Server 2013 organization that contains several servers in each site.
You need to prevent users who have mailboxes in Site2 from sending email messages that are larger than 2 MB to recipients in Site3.
What should you do?
- AModify the attributes of the Active Directory IP site line between Site 2 and Site 3
- BCreate a custom Send connector that has all mailboxes servers from Site 2 as source servers.
- CCreate a custom Receive connector that has the remote IP address range of Site 2.
- DModify the attributes of the Active Directory SMTP site link between Site 2 and Site 3.
Correct Answer:
B
References: https://technet.microsoft.com/en-us/library/bb124345(v=exchg.150).aspx
B
References: https://technet.microsoft.com/en-us/library/bb124345(v=exchg.150).aspx
send
light_mode
delete
Question #23
You have an Exchange Server 2013 organization that contains two Client Access servers named SERVER1 and SERVER2 and two Mailbox servers named
SERVER3 and SERVER4.
You have a firewall that controls all of the traffic between the internal network and the Internet.
SERVER3 and SERVER4 are prevented from communicating with Internet hosts.
SERVER1 and SERVER3 are in a site named Main. SERVER2 and SERVER4 are in a site named Main_2.
All outbound email is sent through SERVER1.
Main fails.
You discover that email messages for the Internet are queued on SERVER4.
You create a new send connector in Main_2.
You discover that all of the outbound email is queued on SERVER4 and is not delivered to the Internet.
You verify that the client computers on the network can receive email messages from the Internet successfully.
You need to ensure that the email messages are delivered successfully to the Internet.
Which cmdlet should you run?
SERVER3 and SERVER4.
You have a firewall that controls all of the traffic between the internal network and the Internet.
SERVER3 and SERVER4 are prevented from communicating with Internet hosts.
SERVER1 and SERVER3 are in a site named Main. SERVER2 and SERVER4 are in a site named Main_2.
All outbound email is sent through SERVER1.
Main fails.
You discover that email messages for the Internet are queued on SERVER4.
You create a new send connector in Main_2.
You discover that all of the outbound email is queued on SERVER4 and is not delivered to the Internet.
You verify that the client computers on the network can receive email messages from the Internet successfully.
You need to ensure that the email messages are delivered successfully to the Internet.
Which cmdlet should you run?
- ASet-SendConnector
- BSet-TransportService
- CSet-ExchangeServer
- DSet-ADSite
Correct Answer:
A
Mailbox Server -
In an Exchange Server 2013 organization the Mailbox server role is responsible for sending outbound email via a Send Connector.
When this option is enabled outbound email that is being sent via a Send Connector does not go directly out from the Mailbox server, and instead is proxied through a Client Access server in the site.
There is nothing complicated going on here, the Client Access server simply acts as a proxy for the connection so that the receiving host out on the internet sees the connection as coming from the Client Access server name and IP address rather than the Mailbox server.
IN THIS QUESTION THE CLIENT ACCESS SERVER (SERVER1) IS ACTING AS A PROXY SERVER FOR THE MAILBOX SERVERS.
NEED TO CHANGE THE SEND CONNECTOR SETTINGS IN ORDER FOR MAIL TO FLOW OUT FROM SERVER4 TO THE INTERNET.
A: Set-SendConnector -
Use the Set-SendConnector cmdlet to modify a Send connector.
Send connectors that are created on Mailbox servers are stored in Active Directory and are available to all Mailbox servers running the Transport service in the organization.
References:
A
Mailbox Server -
In an Exchange Server 2013 organization the Mailbox server role is responsible for sending outbound email via a Send Connector.
When this option is enabled outbound email that is being sent via a Send Connector does not go directly out from the Mailbox server, and instead is proxied through a Client Access server in the site.
There is nothing complicated going on here, the Client Access server simply acts as a proxy for the connection so that the receiving host out on the internet sees the connection as coming from the Client Access server name and IP address rather than the Mailbox server.
IN THIS QUESTION THE CLIENT ACCESS SERVER (SERVER1) IS ACTING AS A PROXY SERVER FOR THE MAILBOX SERVERS.
NEED TO CHANGE THE SEND CONNECTOR SETTINGS IN ORDER FOR MAIL TO FLOW OUT FROM SERVER4 TO THE INTERNET.
A: Set-SendConnector -
Use the Set-SendConnector cmdlet to modify a Send connector.
Send connectors that are created on Mailbox servers are stored in Active Directory and are available to all Mailbox servers running the Transport service in the organization.
References:
send
light_mode
delete
Question #24
You have an Exchange Server 2013 organization named adatum.com. The organization contains five Mailbox servers and two Client Access servers.
You need to ensure that an administrator named user1 receives a daily email message that contains a log of all the Exchange Server administrative actions.
Which cmdlet should you use in a scheduled task?
You need to ensure that an administrator named user1 receives a daily email message that contains a log of all the Exchange Server administrative actions.
Which cmdlet should you use in a scheduled task?
- ASearch-AdminAuditLog
- BSet-Mailbox
- CNew-AdminAuditLogSearch
- DSet-ExchangeServer
- ESet-AdminAuditLogConfig
Correct Answer:
C
C: Use the New-AdminAuditLogSearch cmdlet to search the contents of the administrator audit log and send the results to one or more mailboxes that you specify.
References:
C
C: Use the New-AdminAuditLogSearch cmdlet to search the contents of the administrator audit log and send the results to one or more mailboxes that you specify.
References:
send
light_mode
delete
Question #25
You have an Exchange Server 2013 organization.
You plan to deploy Exchange ActiveSync for mobile devices. Each mobile device will be authenticated by using certificates issued by an internal certification authority (CA).
You need to configure the organization to authenticate the mobile devices by using the certificates.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
You plan to deploy Exchange ActiveSync for mobile devices. Each mobile device will be authenticated by using certificates issued by an internal certification authority (CA).
You need to configure the organization to authenticate the mobile devices by using the certificates.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
- AFrom Internet Information Services (IIS) Manager on each Client Access server, configure the Microsoft-Server-ActiveSync virtual directory to require client certificates.
- BFrom Exchange Admin Center, configure the Microsoft-Server-ActiveSync virtual directory to require client certificates.
- CFrom Internet Information Services (IIS) Manager on each Client Access server, enable Active Directory Client Certificate Authentication.
- DFrom Internet Information Services (IIS) Manager on each Mailbox server, enable Active Directory Client Certificate Authentication.
Correct Answer:
BC
B: After youve installed the Exchange 2013 Client Access server, there are a variety of configuration tasks that you can perform.
Although the Client Access server in Exchange 2013 doesnt handle processing for the client protocols, several settings need to be applied to the Client Access server, including virtual directory settings and certificate settings.
C: Configure certificate-based authentication for Exchange ActiveSync http://blogs.technet.com/b/exchange/archive/2012/11/28/configure-certificate-based-authentication-forexchange- activesync.aspx
Client Access Server Configuration
To configure the Client Access server to enforce certificate based authentication:
1. Verify if Certificate Mapping Authentication is installed on the server.
Right click on Computer in the start menu and choose Manage.
Expand Roles and click on Web Server (IIS)
Scroll down to the Role Services section. Under the Security section you should see Client Certificate Mapping
Authentication installed.
If you don't see Client Certificate Mapping Authentication installed, click add Role Services > (scroll) Security and select Client Certificate Mapping Authentication and then click Install.
Reboot your server.
References:
BC
B: After youve installed the Exchange 2013 Client Access server, there are a variety of configuration tasks that you can perform.
Although the Client Access server in Exchange 2013 doesnt handle processing for the client protocols, several settings need to be applied to the Client Access server, including virtual directory settings and certificate settings.
C: Configure certificate-based authentication for Exchange ActiveSync http://blogs.technet.com/b/exchange/archive/2012/11/28/configure-certificate-based-authentication-forexchange- activesync.aspx
Client Access Server Configuration
To configure the Client Access server to enforce certificate based authentication:
1. Verify if Certificate Mapping Authentication is installed on the server.
Right click on Computer in the start menu and choose Manage.
Expand Roles and click on Web Server (IIS)
Scroll down to the Role Services section. Under the Security section you should see Client Certificate Mapping
Authentication installed.
If you don't see Client Certificate Mapping Authentication installed, click add Role Services > (scroll) Security and select Client Certificate Mapping Authentication and then click Install.
Reboot your server.
References:
send
light_mode
delete
All Pages
