Microsoft 70-341 Exam Practice Questions (P. 3)
- Full Access (183 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #11
You have an Exchange Server 2013 organization named for Contoso.
A user named Admin1 is a member of the Domain Admins group.
Admin1 fails to synchronize a new Windows Phone device by using Exchange ActiveSync and receives an HTTP 500 error message. Admin1 successfully logs on to Outlook Web App and Outlook Anywhere.
You need to ensure that Admin1 can synchronize the new Windows Phone device by using Exchange ActiveSync.
What should you do?
A user named Admin1 is a member of the Domain Admins group.
Admin1 fails to synchronize a new Windows Phone device by using Exchange ActiveSync and receives an HTTP 500 error message. Admin1 successfully logs on to Outlook Web App and Outlook Anywhere.
You need to ensure that Admin1 can synchronize the new Windows Phone device by using Exchange ActiveSync.
What should you do?
- AInstall a trusted root certificate on the Windows Phone device.
- BCreate a new mobile device mailbox policy.
- CEnable permission inheritance on the Admin1 user account.
- DDisable permission inheritance on the Admin1 user account.
Correct Answer:
C
Mobile device mailbox policy -
In Microsoft Exchange Server 2013, you can create mobile device mailbox policies to apply a common set of policies or security settings to a collection of users.
After you deploy Exchange ActiveSync in your Exchange 2013 organization, you can create new mobile device mailbox policies or modify existing policies. When you install Exchange 2013, a default mobile device mailbox policy is created. All users are automatically assigned this default mobile device mailbox policy.
C
Mobile device mailbox policy -
In Microsoft Exchange Server 2013, you can create mobile device mailbox policies to apply a common set of policies or security settings to a collection of users.
After you deploy Exchange ActiveSync in your Exchange 2013 organization, you can create new mobile device mailbox policies or modify existing policies. When you install Exchange 2013, a default mobile device mailbox policy is created. All users are automatically assigned this default mobile device mailbox policy.
send
light_mode
delete
Question #12
You have an Exchange Server 2013 organization that contains a server named EX1.
Your network contains a non-critical internal application that regularly connects to the POP3 Service on EX1.
Users report that Outlook Web App performs more slowly than usual.
You discover that EX1 frequently has a CPU utilization that is greater than 85 percent.
You need to configure EX1 temporarily to allocate more processor resources to Outlook Web App and to allocate less processor resources to POP3.
Which two new policies should you create? (Each correct answer presents part of the solution. Choose two.)
Your network contains a non-critical internal application that regularly connects to the POP3 Service on EX1.
Users report that Outlook Web App performs more slowly than usual.
You discover that EX1 frequently has a CPU utilization that is greater than 85 percent.
You need to configure EX1 temporarily to allocate more processor resources to Outlook Web App and to allocate less processor resources to POP3.
Which two new policies should you create? (Each correct answer presents part of the solution. Choose two.)
- Aa throttling policy that sets OWAMaxConcurrency to 25
- Ba workload policy for POP3 that sets the WorkloadClassification to Discretionary
- Ca workload policy for Outlook Web App that sets the WorkloadClassification to Discretionary
- Da throttling policy that sets PopMaxConcurrency to 25
- Ea workload policy for POP3 that sets the WorkloadClassification to CustomerExpectation
- Fa workload policy for Outlook Web App that sets the WorkloadClassification to CustomerExpectation
Correct Answer:
BF
A workload policy:
An Exchange workload is an Exchange Server feature, protocol, or service thats been explicitly defined for the purposes of Exchange system resource management.
Each Exchange workload consumes system resources such as CPU, mailbox database operations, or Active Directory requests to run user requests or background work.
Examples of Exchange workloads include Outlook Web App, Exchange ActiveSync, mailbox migration, and mailbox assistants.
There are two ways to manage Exchange workloads: by monitoring the health of system resources or by controlling how resources are consumed by individual users (sometimes called user throttling in Exchange 2010).
Managing workloads based on the health of system resources is new in Microsoft Exchange Server 2013.
Controlling how resources are consumed by individual users was possible in Exchange Server 2010, and this capability has been expanded for Exchange Server
2013.
You can customize the workload management settings if you want to change the default behavior of the feature for the needs of your environment.
Workload classifications:
Each Exchange workload (for example, the Calendar Synchronization Assistant workload), is assigned a classification.
Workload policy settings are used to group each workload into a class. Classification is used to control both priority and target resource usage.
Discretionary classification:
Workloads in a higher classification group are given preference as resource health shows signs of degrading.
B: Need to allocate less priority to POP3
F: Outlook Web App is allocated the appropriate amount of resources with a WorkloadClassification of CustomerExpectation.
BF
A workload policy:
An Exchange workload is an Exchange Server feature, protocol, or service thats been explicitly defined for the purposes of Exchange system resource management.
Each Exchange workload consumes system resources such as CPU, mailbox database operations, or Active Directory requests to run user requests or background work.
Examples of Exchange workloads include Outlook Web App, Exchange ActiveSync, mailbox migration, and mailbox assistants.
There are two ways to manage Exchange workloads: by monitoring the health of system resources or by controlling how resources are consumed by individual users (sometimes called user throttling in Exchange 2010).
Managing workloads based on the health of system resources is new in Microsoft Exchange Server 2013.
Controlling how resources are consumed by individual users was possible in Exchange Server 2010, and this capability has been expanded for Exchange Server
2013.
You can customize the workload management settings if you want to change the default behavior of the feature for the needs of your environment.
Workload classifications:
Each Exchange workload (for example, the Calendar Synchronization Assistant workload), is assigned a classification.
Workload policy settings are used to group each workload into a class. Classification is used to control both priority and target resource usage.
Discretionary classification:
Workloads in a higher classification group are given preference as resource health shows signs of degrading.
B: Need to allocate less priority to POP3
F: Outlook Web App is allocated the appropriate amount of resources with a WorkloadClassification of CustomerExpectation.
send
light_mode
delete
Question #13
HOTSPOT -
Your company has an Exchange Server 2013 organization.
The company hires 200 temporary employees.
You create a mailbox for each temporary employee.
You create a new management role named CustomBaseOptions that uses MyBaseOptions as a parent. You create a new management role named
CustomContactInfo that uses MyContactInfo as a parent.
You plan to apply the new management roles to the temporary employees.
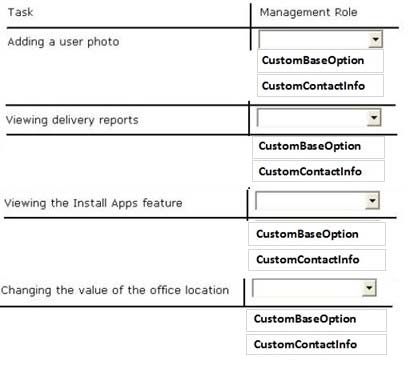
You need to identify which management roles must be modified to prevent the temporary employees from performing the following task:
✑ Adding a user photo
✑ Viewing delivery reports
✑ Viewing the Install Apps feature
✑ Changing the value of the office location
Which management roles should you identify?
To answer, select the appropriate management role for each task in the answer area.
Hot Area:
Your company has an Exchange Server 2013 organization.
The company hires 200 temporary employees.
You create a mailbox for each temporary employee.
You create a new management role named CustomBaseOptions that uses MyBaseOptions as a parent. You create a new management role named
CustomContactInfo that uses MyContactInfo as a parent.
You plan to apply the new management roles to the temporary employees.
You need to identify which management roles must be modified to prevent the temporary employees from performing the following task:
✑ Adding a user photo
✑ Viewing delivery reports
✑ Viewing the Install Apps feature
✑ Changing the value of the office location
Which management roles should you identify?
To answer, select the appropriate management role for each task in the answer area.
Hot Area:

Correct Answer:
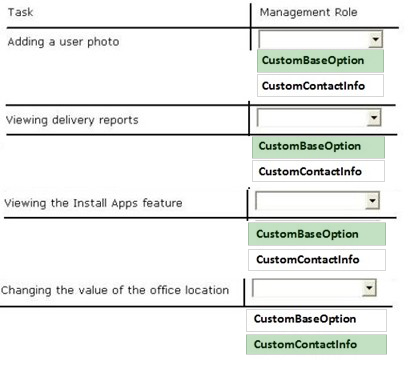
View and modify the basic configuration of their own mailbox and associated settings.
VIEWING DELIVERY REPORTS -
MyBaseOptions includes the following delivery reports information:
✑ Delivery Success
✑ Delivery Failure
✑ Email submission from the senders mailbox
✑ Message was read etc...
VIEWING THE INSTALL APPS FEATURE
MyBaseOptions -
View and modify the basic configuration of their own mailbox and associated settings.
CHANGING THE VALUE OF THE OFFICE LOCATION
The MyContactInformation management role enables individual users to modify their contact information, including address and phone numbers.
References:
Understanding Management Roles: Exchange 2013 Help

View and modify the basic configuration of their own mailbox and associated settings.
VIEWING DELIVERY REPORTS -
MyBaseOptions includes the following delivery reports information:
✑ Delivery Success
✑ Delivery Failure
✑ Email submission from the senders mailbox
✑ Message was read etc...
VIEWING THE INSTALL APPS FEATURE
MyBaseOptions -
View and modify the basic configuration of their own mailbox and associated settings.
CHANGING THE VALUE OF THE OFFICE LOCATION
The MyContactInformation management role enables individual users to modify their contact information, including address and phone numbers.
References:
Understanding Management Roles: Exchange 2013 Help
send
light_mode
delete
Question #14
HOTSPOT -
Your company has two offices. The offices are configured as shown in the following table.
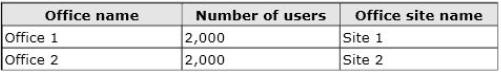
The offices connect to each other by using a WAN link that has a latency of more than 700 ms.
You plan to deploy an Exchange Server 2013 organization to meet the following requirements:
✑ Ensure that users can access their mailbox if the WAN link fails.
✑ Ensure that users can access their mailbox if a single server fails.
✑ Ensure that users can access their mailbox if a single database fails.
You recommend deploying one or more database availability groups (DAGs) and mailbox database copies.
You need to identify which design meets the requirements for the planned deployment.
Which design should you identify?
To answer, select the appropriate design in the answer area.
Hot Area:
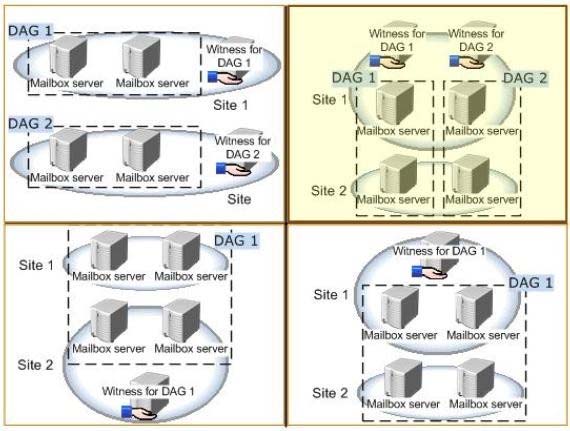
Your company has two offices. The offices are configured as shown in the following table.

The offices connect to each other by using a WAN link that has a latency of more than 700 ms.
You plan to deploy an Exchange Server 2013 organization to meet the following requirements:
✑ Ensure that users can access their mailbox if the WAN link fails.
✑ Ensure that users can access their mailbox if a single server fails.
✑ Ensure that users can access their mailbox if a single database fails.
You recommend deploying one or more database availability groups (DAGs) and mailbox database copies.
You need to identify which design meets the requirements for the planned deployment.
Which design should you identify?
To answer, select the appropriate design in the answer area.
Hot Area:

Correct Answer:
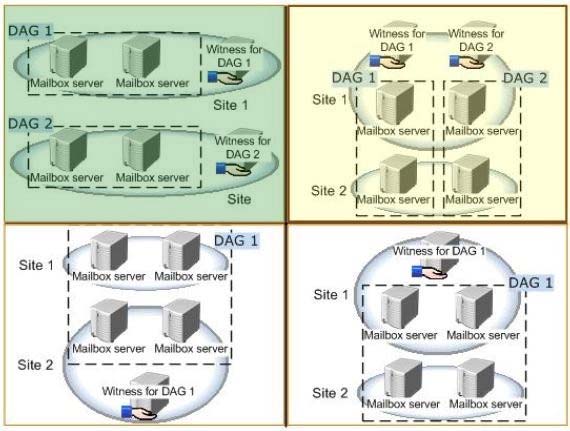
File Share Witness -
The file share witness is used to establish a majority node set. This is done by create a share on a server that gets a little file place into it automatically.
The server hosting the cluster resource (which in the DAG I think is the Primary Activation Manager server) keeps an open file lock on this file.
The other servers see this open file lock and interpret this as meaning another cluster node is online, healthy, and available.
A file share witness is used when the DAG contains an even number of servers within it.
When you initially create the DAG you must specify the server and file location that will act as the file share witness regardless of how many servers are in the
DAG (0 to start) to ensure that if you do add an even number of DAG members the FSW will be properly used.
Database Availability Group -
A database availability group (DAG) is a set of up to 16 Microsoft Exchange Server 2013 Mailbox servers that provide automatic database-level recovery from a database, server, or network failure. When a Mailbox server is added to a DAG, it works with the other servers in the DAG to provide automatic, database-level recovery from database, server, and network failures.
DAGs use continuous replication and a subset of Windows failover clustering technologies to provide high availability and site resilience.
Mailbox servers in a DAG monitor each other for failures. When a Mailbox server is added to a DAG, it works with the other servers in the DAG to provide automatic, database-level recovery from database failures.
When you create a DAG, it's initially empty, and a directory object is created in Active Directory that represents the DAG. The directory object is used to store relevant information about the DAG, such as server membership information. When you add the first server to a DAG, a failover cluster is automatically created for the DAG. In addition, the infrastructure that monitors the servers for network or server failures is initiated. The failover cluster heartbeat mechanism and cluster database are then used to track and manage information about the DAG that can change quickly, such as database mount status, replication status, and last mounted location.
Witness server and witness directory The witness server is a server outside the DAG that acts as a quorum voter when the DAG contains an even number of members. The witness directory is a directory created and shared on the witness server for use by the system in maintaining a quorum.
Lagged copy of a mailbox database
A Lagged Mailbox Database Copy is a mailbox database copy configured with a replay lag time value greater than 0.
A lagged database copy is one that is not updated by replaying transactions as they become available.
Instead, the transaction logs are kept for a certain period and are then replayed.
The lagged database copy is therefore maintained at a certain remove to the active database and the other non-lagged database copies. If you are planning to have more than two passive database copies of a database, think about a lagged copy also as an additional protection against unpredicted situations Lagged copies aren't considered highly available copies. Instead, they are designed for disaster recovery purposes, to protect against store logical corruption.
The greater the replay lag time set, the longer the database recovery process. Depending on the number of log files that need to replayed during recovery, and the speed at which your hardware can replay them, it may take several hours or more to recover a database.
References:
http://jaworskiblog.com/2011/05/17/exchange-2010-design-principles-for-high-availability-and-site-resiliency/

File Share Witness -
The file share witness is used to establish a majority node set. This is done by create a share on a server that gets a little file place into it automatically.
The server hosting the cluster resource (which in the DAG I think is the Primary Activation Manager server) keeps an open file lock on this file.
The other servers see this open file lock and interpret this as meaning another cluster node is online, healthy, and available.
A file share witness is used when the DAG contains an even number of servers within it.
When you initially create the DAG you must specify the server and file location that will act as the file share witness regardless of how many servers are in the
DAG (0 to start) to ensure that if you do add an even number of DAG members the FSW will be properly used.
Database Availability Group -
A database availability group (DAG) is a set of up to 16 Microsoft Exchange Server 2013 Mailbox servers that provide automatic database-level recovery from a database, server, or network failure. When a Mailbox server is added to a DAG, it works with the other servers in the DAG to provide automatic, database-level recovery from database, server, and network failures.
DAGs use continuous replication and a subset of Windows failover clustering technologies to provide high availability and site resilience.
Mailbox servers in a DAG monitor each other for failures. When a Mailbox server is added to a DAG, it works with the other servers in the DAG to provide automatic, database-level recovery from database failures.
When you create a DAG, it's initially empty, and a directory object is created in Active Directory that represents the DAG. The directory object is used to store relevant information about the DAG, such as server membership information. When you add the first server to a DAG, a failover cluster is automatically created for the DAG. In addition, the infrastructure that monitors the servers for network or server failures is initiated. The failover cluster heartbeat mechanism and cluster database are then used to track and manage information about the DAG that can change quickly, such as database mount status, replication status, and last mounted location.
Witness server and witness directory The witness server is a server outside the DAG that acts as a quorum voter when the DAG contains an even number of members. The witness directory is a directory created and shared on the witness server for use by the system in maintaining a quorum.
Lagged copy of a mailbox database
A Lagged Mailbox Database Copy is a mailbox database copy configured with a replay lag time value greater than 0.
A lagged database copy is one that is not updated by replaying transactions as they become available.
Instead, the transaction logs are kept for a certain period and are then replayed.
The lagged database copy is therefore maintained at a certain remove to the active database and the other non-lagged database copies. If you are planning to have more than two passive database copies of a database, think about a lagged copy also as an additional protection against unpredicted situations Lagged copies aren't considered highly available copies. Instead, they are designed for disaster recovery purposes, to protect against store logical corruption.
The greater the replay lag time set, the longer the database recovery process. Depending on the number of log files that need to replayed during recovery, and the speed at which your hardware can replay them, it may take several hours or more to recover a database.
References:
http://jaworskiblog.com/2011/05/17/exchange-2010-design-principles-for-high-availability-and-site-resiliency/
send
light_mode
delete
Question #15
DRAG DROP -
Your company plans to deploy an Exchange Server 2013 organization.
The network contains an Active Directory forest. The forest contains two domains named contoso.com and child.contoso.com. The forest contains one Active
Directory site.
To contoso.com, you plan to deploy two servers that have Exchange Server 2013 installed. To child.contoso.com, you plan to deploy two servers that have
Exchange Server 2013 installed.
To the contoso.com domain, you deploy a new member server named Server1 that runs Windows Server 2012.
You need to prepare the forest for the planned deployment of Exchange Server 2013.
Which three commands should you run from Server1?
To answer, move the three appropriate commands from the list of commands to the answer area and arrange them in the correct order.
Select and Place:
Your company plans to deploy an Exchange Server 2013 organization.
The network contains an Active Directory forest. The forest contains two domains named contoso.com and child.contoso.com. The forest contains one Active
Directory site.
To contoso.com, you plan to deploy two servers that have Exchange Server 2013 installed. To child.contoso.com, you plan to deploy two servers that have
Exchange Server 2013 installed.
To the contoso.com domain, you deploy a new member server named Server1 that runs Windows Server 2012.
You need to prepare the forest for the planned deployment of Exchange Server 2013.
Which three commands should you run from Server1?
To answer, move the three appropriate commands from the list of commands to the answer area and arrange them in the correct order.
Select and Place:

Correct Answer:
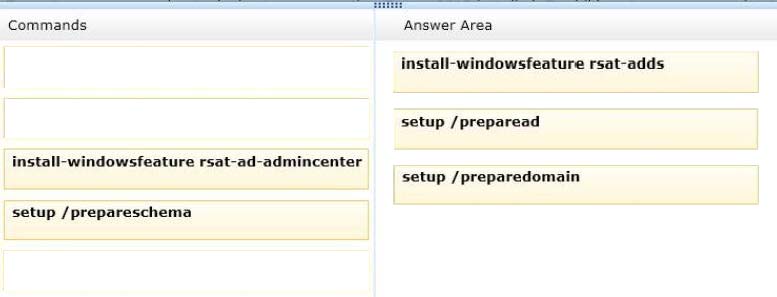
Before you install Microsoft Exchange Server 2013 on any servers in your organization, you must prepare Active Directory and domains.
To prepare Active Directory and domains
✑ From a Command Prompt window, run the following command.setup /PrepareSchemaorsetup /ps
✑ From a Command Prompt window, run the following command.setup /PrepareAD [/OrganizationName:<organization name>]orsetup /p [/on:<organization name>]
✑ From a Command Prompt window, run one of the following commands:
- Runsetup /PrepareDomainorsetup /pdto prepare the local domain. You don't need to run this in the domain where you ran Step 2. Runningsetup /- - -
PrepareADprepares the local domain.
- Runsetup /PrepareDomain:<FQDN of domain you want to prepare>to prepare a specific domain.
- Runsetup /PrepareAllDomainsorsetup /pad to prepare all domains in your organization.
References:

Before you install Microsoft Exchange Server 2013 on any servers in your organization, you must prepare Active Directory and domains.
To prepare Active Directory and domains
✑ From a Command Prompt window, run the following command.setup /PrepareSchemaorsetup /ps
✑ From a Command Prompt window, run the following command.setup /PrepareAD [/OrganizationName:<organization name>]orsetup /p [/on:<organization name>]
✑ From a Command Prompt window, run one of the following commands:
- Runsetup /PrepareDomainorsetup /pdto prepare the local domain. You don't need to run this in the domain where you ran Step 2. Runningsetup /- - -
PrepareADprepares the local domain.
- Runsetup /PrepareDomain:<FQDN of domain you want to prepare>to prepare a specific domain.
- Runsetup /PrepareAllDomainsorsetup /pad to prepare all domains in your organization.
References:
send
light_mode
delete
All Pages
