GIAC GPEN Exam Practice Questions (P. 5)
- Full Access (385 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #41
Which type of Cross-Sire Scripting (XSS> vulnerability is hardest for automated testing tools to detect, and for what reason?
- AStored XSS. because it may be located anywhere within static or dynamic sitecontent
- BStored XSS. because it depends on emails and instant messaging systems.
- CReflected XSS. because It can only be found by analyzing web server responses.
- DReflected XSS: because it is difficult to find within large web server logs.
Correct Answer:
A
A
send
light_mode
delete
Question #42
You are using the Nmap Scripting Engine and want detailed output of the script as it runs. Which option do you include in the command string?
- ANmap --script-output -script-SSH-hostkey.nse 155.65.3.221 -p 22
- BNmap --script-trace --script-ssh-hostkey.nse 155.65.3.221 -p 22
- CNmap -script-verbose --scrlpr-ssh-hostkey.nse 155.65.3.221 -p 22
- DNmap -v --script=ssh-hostkey.nse 155.65.3.221 -p 22
Correct Answer:
C
C
send
light_mode
delete
Question #43
What is the purpose of the following command?
C:\>wmic /node:[target IP] /user:[admin-user]
/password:[password] process call create [command]
C:\>wmic /node:[target IP] /user:[admin-user]
/password:[password] process call create [command]
- ARunning a command on a remote Windows machine
- BCreating a service on a remote Windows machine
- CCreating an admin account on a remote Windows machine
- DListing the running processes on a remote windows machine
Correct Answer:
D
D
send
light_mode
delete
Question #44
Approximately how many packets are usually required to conduct a successful FMS attack onWEP?
send
light_mode
delete
Question #45
What is the most likely cause of the responses on lines 10 and 11 of the output below?
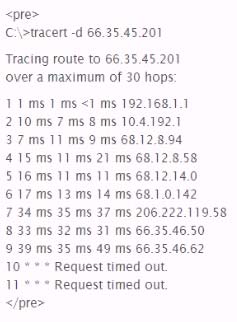

- AThe device at hop 10 silently drops UDP packets with a high destination port.
- BThe device at hop 10 is down and not forwarding any requests at all.
- CThe host running the tracer utility lost its network connection during the scan
- DThe devices at hops 10 and II did not return an "ICMP TTL Exceeded in Transit" message.
Correct Answer:
D
D
send
light_mode
delete
Question #46
A penetration tester wishes to stop the Windows Firewall process on a remote host running Windows Vista She issues the following commands:
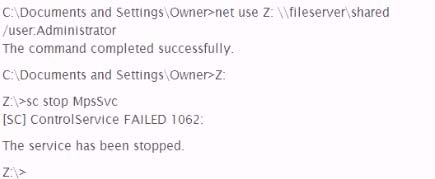
A check of the remote host indicates that Windows Firewall is still running. Why did the command fail?

A check of the remote host indicates that Windows Firewall is still running. Why did the command fail?
- AThe kernel prevented the command from being executed.
- BThe user does not have the access level needed to stop the firewall.
- CThe sc command needs to be passed the IP address of the target.
- DThe remote server timed out and did not complete the command.
Correct Answer:
C
C
send
light_mode
delete
Question #47
By default Active Directory Controllers store password representations in which file?
- A%system roots .system 32/ntds.dit
- B%System roots /ntds\ntds.dit
- C%System roots /ntds\sam.dat
- D%System roots /ntds\sam.dit
Correct Answer:
A
Reference:
http://www.scribd.com/doc/212238158/Windows-Administrator-L2-Interview-Question-System-Administrator#scribd
A
Reference:
http://www.scribd.com/doc/212238158/Windows-Administrator-L2-Interview-Question-System-Administrator#scribd
send
light_mode
delete
Question #48
192.168.116.9 Is an IP address forvvww.scanned-server.com. Why are the results from the two scans, shown below, different?
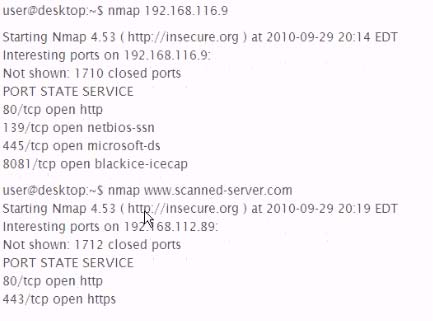

send
light_mode
delete
Question #49
You have been contracted to perform a black box pen test against the Internet facing servers for a company. They want to know, with a high level of confidence, if their servers are vulnerable to external attacks. Your contract states that you can use all tools available to you to pen test the systems. What course of action would you use to generate a report with the lowest false positive rate?
- AUse a port scanner to find open service ports and generate a report listing allvulnerabilities associated with those listening services.
- BUse a vulnerability or port scanner to find listening services and then try to exploitthose services.
- CUse a vulnerability scanner to generate a report of vulnerable services.
- DLog into the system and record the patch levels of each service then generate areport that lists known vulnerabilities for all the running services.
Correct Answer:
B
B
send
light_mode
delete
Question #50
You successfully compromise a target system's web application using blind command injection. The command you injected is ping-n 1 192.168.1.200. Assuming your machine is 192.168.1 200, which of the following would you see?
- APing-n 1 192.168.1 200 on the compromised system
- BA 'Destination host unreachable' error message on the compromised system
- CA packet containing 'Packets: Sent - 1 Received = 1, Loss = 0 (0% loss) on yoursniffer
- DAn ICMP Echo packet on your sniffer containing the source address of the target
Correct Answer:
A
A
send
light_mode
delete
All Pages
