GIAC GPEN Exam Practice Questions (P. 2)
- Full Access (385 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #11
You are pen testing a Windows system remotely via a raw netcat shell. You want to quickly change directories to where the Windows operating system resides, what command could you use?
send
light_mode
delete
Question #12
A client with 7200 employees in 14 cities (all connected via high speed WAN connections) has suffered a major external security breach via a desktop which cost them more than SI 72.000 and the loss of a high profile client. They ask you to perform a desktop vulnerability assessment to identify everything that needs to be patched. Using Nessus you find tens of thousands of vulnerabilities that need to be patched. In the report you find workstations running several Windows OS versions and service pack levels, anti-virus software from multiple vendors several major browser versions and different versions of Acrobat Reader. Which of the following recommendations should you provide with the report?
- AThe client should standardize their desktop softwareMost Voted
- BThe client should eliminate workstations to reduce workload
- CThe client should hire more people to catch up on patches
- DThe client should perform monthly vulnerability assessments
Correct Answer:
C
C
send
light_mode
delete
Question #13
Which Metasploit payload includes simple upload and download functionality for moving files to and from compromised systems?
- ADLL inject
- BUpexec
- CMeterpreterMost Voted
- DVncinject
Correct Answer:
D
Reference:
http://www.opensourceforu.com/2011/02/metasploit-meterpreter-payload/
D
Reference:
http://www.opensourceforu.com/2011/02/metasploit-meterpreter-payload/
send
light_mode
delete
Question #14
A junior penetration tester at your firm is using a non-transparent proxy for the first time to test a web server. He sees the web site In his browser but nothing shows up In the proxy. He tells you that he just installed the non-transparent proxy on his computer and didn't change any defaults. After verifying the proxy is running, you ask him to open up his browser configuration, as shown in the figure, which of the following recommendations will correctly allow him to use the transparent proxy with his browser?
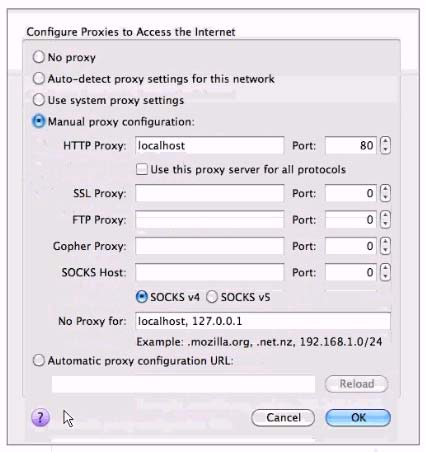

- AHe should change the PORT: value to match the port used by the non-transparentproxy.Most Voted
- BHe should select the checkbox "use this proxy server for all protocols" for theproxy to function correctly.
- CHe should change the HTTP PROXY value to 127.0.0.1 since the non-transparentproxy is running on the same machine as the browser.
- DHe should select NO PROXY instead of MANUAL PROXY CONFIGURATION as thissetting is only necessary to access the Internet behind protected
Correct Answer:
C
C
send
light_mode
delete
Question #15
Which of the following describe the benefits to a pass-the-hash attack over traditional password cracking?
- ANo triggering of IDS signatures from the attack privileges at the level of theacquired password hash and no corruption of the LSASS process.
- BNo triggering of IDS signatures from the attack, no account lockout and use ofnative windows file and print sharing tools on the compromised system.
- CNo account lockout, privileges at the level of the acquired password hash and useof native windows file and print Sharif tools on the compromised system.
- DNo account lockout, use of native file and print sharing tools on the compromisedsystem and no corruption of the LSASS process.
Correct Answer:
D
D
send
light_mode
delete
Question #16
You are pen testing a Linux target from your windows-based attack platform. You just moved a script file from the windows system to the Linux target, but it will not execute properly. What is the most likely problem?
- AThe byte length is different on the two machines
- BEnd of-line characters are different on the two machinesMost Voted
- CThe file must have become corrupt during transfer
- DASCII character sets are different on the two machines
Correct Answer:
A
A
send
light_mode
delete
Question #17
Which of the following is the JavaScript variable used to store a cookie?
- ABrowsercookie
- BWindowcookie
- CDocument cookie
- DSession cookie
Correct Answer:
C
Reference:
http://www.w3schools.com/js/js_cookies.asp
C
Reference:
http://www.w3schools.com/js/js_cookies.asp
send
light_mode
delete
Question #18
Analyze the command output below. Given this information, which is the appropriate next step for the tester?
Starting Nmap4.53 (hnp://insecure.org I at2010-09-30 19:13 EDT interesting ports on 192.163.116.101:
PORT STATE SERVICE -
130/tcp filtered cisco-fna
131/tcp filtered cisco-tna
132/tcp filtered cisco-sys
133/tcp filtered statsrv
134/tcp filtered Ingres-net
135/tcp filtered msrpc
136/tcp filtered profile
137/tcp filtered netbios-ns
138/tcp filtered netbios-dgm
139/tcp open netbios-ssn
140/tcp filtered emfis-data
MAC Address: 00:30:1&:B8:14:8B (Shuttle)
warning: OSS can results may be unreliable because we could not find at least l open and l closed port
Device type, general purpose -
Running: Microsoft Windows XP -
OS details: Microsoft Windows XP SP2
Network Distance : 1 hop -
Nmap done: I IP address (I host up) scanned in l .263 seconds
Starting Nmap4.53 (hnp://insecure.org I at2010-09-30 19:13 EDT interesting ports on 192.163.116.101:
PORT STATE SERVICE -
130/tcp filtered cisco-fna
131/tcp filtered cisco-tna
132/tcp filtered cisco-sys
133/tcp filtered statsrv
134/tcp filtered Ingres-net
135/tcp filtered msrpc
136/tcp filtered profile
137/tcp filtered netbios-ns
138/tcp filtered netbios-dgm
139/tcp open netbios-ssn
140/tcp filtered emfis-data
MAC Address: 00:30:1&:B8:14:8B (Shuttle)
warning: OSS can results may be unreliable because we could not find at least l open and l closed port
Device type, general purpose -
Running: Microsoft Windows XP -
OS details: Microsoft Windows XP SP2
Network Distance : 1 hop -
Nmap done: I IP address (I host up) scanned in l .263 seconds
- ADetermine the MAC address of the scanned host.
- BSend a single SYN packet to port 139/tcp on the host.
- CSend spoofed packets to attempt to evade any firewall
- DRequest a list of shares from the scanned host.Most Voted
Correct Answer:
B
B
send
light_mode
delete
Question #19
The resulting business impact, of the penetration test or ethical hacking engagement is explained in what section of the final report?
- AProblems
- BFindings
- CImpact Assessment
- DExecutive Summary
Correct Answer:
D
Reference:
http://www.frost.com/upld/get-data.do?id=1568233
D
Reference:
http://www.frost.com/upld/get-data.do?id=1568233
send
light_mode
delete
Question #20
You have been contracted to map me network and try to compromise the servers for a client. Which of the following would be an example of scope creep' with respect to this penetration testing project?
- ADisclosing information forbidden in the NDA
- BCompromising a server then escalating privileges
- CBeing asked to compromise workstations
- DScanning network systems slowly so you are not detected
Correct Answer:
B
B
send
light_mode
delete
All Pages
