GIAC GPEN Exam Practice Questions (P. 3)
- Full Access (385 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #21
You are running a vulnerability scan on a remote network and the traffic Is not making It to the target system. You investigate the connection issue and determine that the traffic is making it to the internal interface of your network firewall, but not making. It to the external Interface or to any systems outside your firewall. What is the most likely problem?
- AYour network firewall is blocking the traffic
- BThe NAT or pat tables on your network based firewall are filling up and droppingthe traffic
- CA host based firewall is blocking the traffic
- DYour ISP Is blocking the traffic
Correct Answer:
C
C
send
light_mode
delete
Question #22
Identify the network activity shown below;
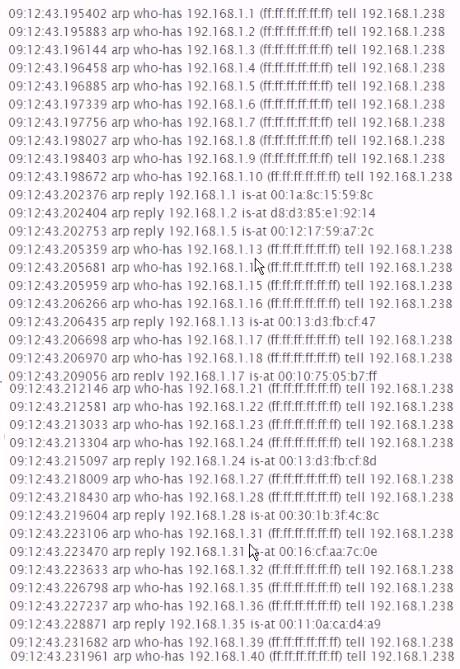

- AA sweep of available hosts on the local subnetMost Voted
- BA flood of the local switch's CAM table.
- CAn attempt to disassociate wireless clients.
- DAn attempt to impersonate the local gateway
Correct Answer:
D
D
send
light_mode
delete
Question #23
You have compromised a Windows workstation using Metasploit and have injected the Meterpreter payload into the svchost process. After modifying some files to set up a persistent backdoor you realize that you will need to change the modified and access times of the files to ensure that the administrator can't see the changes you made. Which Meterpreter module would you need to load in order to do this?
send
light_mode
delete
Question #24
How can web server logs be leveraged to perform Cross-Site Scripting (XSSI?
- AWeb logs containing XSS may execute shell scripts when opened In a GUI textbrowser
- BXSS attacks cause web logs to become unreadable and therefore are an effective DOS attack.
- CIf web logs are viewed in a web-based console, log entries containing XSS mayexecute on the browser.
- DWhen web logs are viewed in a terminal. XSS can escape to the shell and executecommands.
Correct Answer:
C
C
send
light_mode
delete
Question #25
What is the impact on pre-calculated Rainbow Tables of adding multiple salts to a set of passwords?
- ASalts increases the time to crack the original password by increasing the number oftables that must be calculated.Most Voted
- BSalts double the total size of a rainbow table database.
- CSalts can be reversed or removed from encoding quickly to produce unsaltedhashes.
- DSalts have little effect because they can be calculated on the fly with applicationssuch as Ophcrack.
Correct Answer:
B
B
send
light_mode
delete
Question #26
You are done pen testing a Windows system and need to clean up some of the changes you have made. You created an account pentester on the system, what command would you use to delete that account?
- ANet user pentester /delMost Voted
- BNet name pentester /del
- CNet localuser pentester /del
- DNet account pentester /del
Correct Answer:
A
A
send
light_mode
delete
Question #27
Your company has decided that the risk of performing a penetration test Is too great. You would like to figure out other ways to find vulnerabilities on their systems, which of the following is MOST likely to be a valid alternative?
- ANetwork scope Analysis
- BBaseline Data Reviews
- CPatch Policy Review
- DConfiguration ReviewsMost Voted
Correct Answer:
A
A
send
light_mode
delete
Question #28
Analyze the command output below, what action is being performed by the tester?
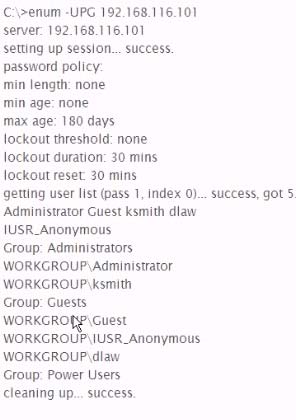

- ADisplaying a Windows SAM database
- BListing available workgroup services
- CDiscovering valid user accounts
- DQuerying locked out user accounts
Correct Answer:
C
C
send
light_mode
delete
Question #29
Raw netcat shells and telnet terminals share which characteristic?
- AAbility to send commands to a target machine.
- BAbility to adapt output to the size of display window
- CShells and terminals are exactly the same.
- DAbility to process standard output control sequences.
Correct Answer:
D
Reference:
http://tartarus.org/~simon/putty-snapshots/htmldoc/Chapter3.html
D
Reference:
http://tartarus.org/~simon/putty-snapshots/htmldoc/Chapter3.html
send
light_mode
delete
Question #30
How can a non-privileged user on a Unix system determine if shadow passwords are being used?
- ARead /etc/password and look for "x" or "II" in the second colon-delimited fieldMost Voted
- BRead /etc/shadow and look for "x" or "II" in the second colon-delimited field
- CVerify that /etc/password has been replaced with /etc/shadow
- DRead /etc/shadow and look NULL values In the second comma delimited field
Correct Answer:
B
B
send
light_mode
delete
All Pages
