GIAC GPEN Exam Practice Questions (P. 4)
- Full Access (385 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #31
When DNS is being used for load balancing, why would a penetration tester choose to identify a scan target by its IP address rather than its host name?
- AAsingle IP may have multiple domains.
- BA single domain name can only have one IP address.
- CScanning tools only recognize IP addresses
- DA single domain name may have multiple IP addresses.
Correct Answer:
C
Reference:
http://www.flashcardmachine.com/sec-midterm.html
C
Reference:
http://www.flashcardmachine.com/sec-midterm.html
send
light_mode
delete
Question #32
What problem occurs when executing the following command from within a netcat raw shell? sudo cat /etc/shadow
- ASudo does not work at all from a shell
- BSudo works fine if the user and command are both in the /etc/sudoers file
- CThe display blanks after typing the sudo command
- DYou will not be able to type the password at the password promptMost Voted
Correct Answer:
A
A
send
light_mode
delete
Question #33
You are pen testing a Windows system remotely via a raw netcat shell. You want to get a listing of all the local users in the administrators group, what command would you use?
- ANet account administrators
- BNet user administrators
- CNet localgroup administratorsMost Voted
- DNet localuser administrators
Correct Answer:
C
C
send
light_mode
delete
Question #34
Analyze the screenshot below. What type of vulnerability is being attacked?
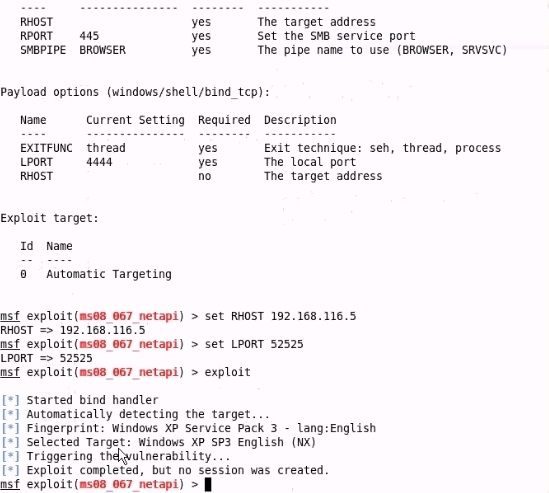

- AWindows Server serviceMost Voted
- BInternet Explorer
- CWindows Powershell
- DLocal Security Authority
Correct Answer:
B
B
send
light_mode
delete
Question #35
You have compromised a Windows workstation using Metasploit and have injected the Meterpreter payload into the smss process. You want to dump the SAM database of the remote system so you can crack it offline. Which Meterpreter module would you need to load in addition to the defaults so that you can accomplish this?
send
light_mode
delete
Question #36
Which of the following is the feature that separates the use of Rainbow Tables from other applications such as Cain or John the Ripper?
- ASalts are used to create massive password databases for comparison.
- BApplications take advantage of 64-bit CPU processor and multithread the crackingprocess.
- CData Is aligned efficiently in the rainbow tables making the search process quicker
- DRaw hashed passwords are compared to pre-calculated hash tables.Most Voted
Correct Answer:
B
B
send
light_mode
delete
Question #37
You suspect that system administrators In one part of the target organization are turning off their systems during the times when penetration tests are scheduled, what feature could you add to the ' Rules of engagement' that could help your team test that part of the target organization?
- AUn announced test
- BTell response personnel the exact lime the test will occur
- CTest systems after normal business hours
- DLimit tests to business hours
Correct Answer:
C
C
send
light_mode
delete
Question #38
You are conducting a penetration test for a private contractor located in Singapore. The scope extends to all internal hosts controlled by the company, you have gathered necessary hold-harmless and nondisclosure agreements. Which action by your group can incur criminal liability under Chapter 50a, Computer Misuse
Act?
Act?
- AExploiting vulnerable web services on internal hosts
- BAttempts at social engineering employees via telephone calls
- CTesting denial-of-service tolerance of the communications provider
- DCracking password hashes on the corporate domain server
Correct Answer:
D
D
send
light_mode
delete
Question #39
Which of the following is a WEP weakness that makes it easy to Inject arbitrary clear text packets onto a WEP network?
- AReversible hashes use for IVs
- BCryptographically weak CRC32 checksum
- CRC4 algorithm
- DSmall key space
Correct Answer:
D
D
send
light_mode
delete
Question #40
During a penetration test we determine that TCP port 22 is listening on a target host. Knowing that SSHD is the typical service that listens on that port we attempt to validate that assumption with an SSH client but our effort Is unsuccessful. It turns out that it is actually an Apache webserver listening on the port, which type of scan would have helped us to determine what service was listening on port 22?
- AVersion scanningMost Voted
- BPort scanning
- CNetwork sweeping
- DOS fingerprinting
Correct Answer:
C
C
send
light_mode
delete
All Pages
