CompTIA CS0-001 Exam Practice Questions (P. 5)
- Full Access (416 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #41
A security analyst has been asked to remediate a server vulnerability. Once the analyst has located a patch for the vulnerability, which of the following should happen NEXT?
- AStart the change control process.
- BRescan to ensure the vulnerability still exists.
- CImplement continuous monitoring.
- DBegin the incident response process.
Correct Answer:
A
A
send
light_mode
delete
Question #42
A software assurance lab is performing a dynamic assessment on an application by automatically generating and inputting different, random data sets to attempt to cause an error/failure condition. Which of the following software assessment capabilities is the lab performing AND during which phase of the SDLC should this occur? (Choose two.)
- AFuzzing
- BBehavior modeling
- CStatic code analysis
- DPrototyping phase
- ERequirements phase
- FPlanning phase
Correct Answer:
AD
Reference:
http://www.brighthub.com/computing/smb-security/articles/9956.aspx
AD
Reference:
http://www.brighthub.com/computing/smb-security/articles/9956.aspx
send
light_mode
delete
Question #43
Law enforcement has contacted a corporation's legal counsel because correlated data from a breach shows the organization as the common denominator from all indicators of compromise. An employee overhears the conversation between legal counsel and law enforcement, and then posts a comment about it on social media. The media then starts contacting other employees about the breach. Which of the following steps should be taken to prevent further disclosure of information about the breach?
- APerform security awareness training about incident communication.
- BRequest all employees verbally commit to an NDA about the breach.
- CTemporarily disable employee access to social media
- DHave law enforcement meet with employees.
Correct Answer:
A
A
send
light_mode
delete
Question #44
A recent vulnerability scan found four vulnerabilities on an organization's public Internet-facing IP addresses. Prioritizing in order to reduce the risk of a breach to the organization, which of the following should be remediated FIRST?
- AA cipher that is known to be cryptographically weak.
- BA website using a self-signed SSL certificate.
- CA buffer overflow that allows remote code execution.
- DAn HTTP response that reveals an internal IP address.
Correct Answer:
C
C
send
light_mode
delete
Question #45
A security professional is analyzing the results of a network utilization report. The report includes the following information:
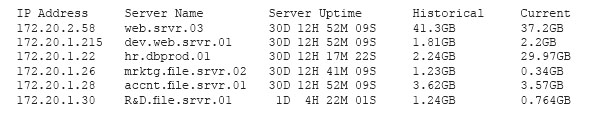
Which of the following servers needs further investigation?

Which of the following servers needs further investigation?
send
light_mode
delete
Question #46
A cybersecurity analyst has several SIEM event logs to review for possible APT activity. The analyst was given several items that include lists of indicators for both
IP addresses and domains. Which of the following actions is the BEST approach for the analyst to perform?
IP addresses and domains. Which of the following actions is the BEST approach for the analyst to perform?
- AUse the IP addresses to search through the event logs.
- BAnalyze the trends of the events while manually reviewing to see if any of the indicators match.
- CCreate an advanced query that includes all of the indicators, and review any of the matches.
- DScan for vulnerabilities with exploits known to have been used by an APT.
Correct Answer:
B
B
send
light_mode
delete
Question #47
A system administrator has reviewed the following output:
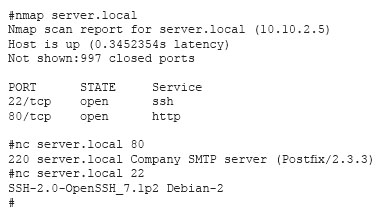
Which of the following can a system administrator infer from the above output?

Which of the following can a system administrator infer from the above output?
- AThe company email server is running a non-standard port.
- BThe company email server has been compromised.
- CThe company is running a vulnerable SSH server.
- DThe company web server has been compromised.
Correct Answer:
A
A
send
light_mode
delete
Question #48
An analyst has received unusual alerts on the SIEM dashboard. The analyst wants to get payloads that the hackers are sending toward the target systems without impacting the business operation. Which of the following should the analyst implement?
send
light_mode
delete
Question #49
An analyst finds that unpatched servers have undetected vulnerabilities because the vulnerability scanner does not have the latest set of signatures. Management directed the security team to have personnel update the scanners with the latest signatures at least 24 hours before conducting any scans, but the outcome is unchanged. Which of the following is the BEST logical control to address the failure?
- AConfigure a script to automatically update the scanning tool.
- BManually validate that the existing update is being performed.
- CTest vulnerability remediation in a sandbox before deploying.
- DConfigure vulnerability scans to run in credentialed mode.
Correct Answer:
A
A
send
light_mode
delete
Question #50
A cybersecurity analyst has received an alert that well-known "call home" messages are continuously observed by network sensors at the network boundary. The proxy firewall successfully drops the messages. After determining the alert was a true positive, which of the following represents the MOST likely cause?
- AAttackers are running reconnaissance on company resources.
- BAn outside command and control system is attempting to reach an infected system.
- CAn insider is trying to exfiltrate information to a remote network.
- DMalware is running on a company system.
Correct Answer:
B
B
send
light_mode
delete
All Pages
