CompTIA CS0-001 Exam Practice Questions (P. 2)
- Full Access (416 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #11
File integrity monitoring states the following files have been changed without a written request or approved change. The following change has been made: chmod 777 ""Rv /usr
Which of the following may be occurring?
Which of the following may be occurring?
- AThe ownership pf /usr has been changed to the current user.
- BAdministrative functions have been locked from users.Most Voted
- CAdministrative commands have been made world readable/writable.
- DThe ownership of/usr has been changed to the root user.
Correct Answer:
C
C
send
light_mode
delete
Question #12
A security analyst has created an image of a drive from an incident. Which of the following describes what the analyst should do NEXT?
- AThe analyst should create a backup of the drive and then hash the drive.
- BThe analyst should begin analyzing the image and begin to report findings.
- CThe analyst should create a hash of the image and compare it to the original drive's hash.
- DThe analyst should create a chain of custody document and notify stakeholders.
Correct Answer:
C
C
send
light_mode
delete
Question #13
A cybersecurity analyst is currently investigating a server outage. The analyst has discovered the following value was entered for the username: 0xbfff601a. Which of the following attacks may be occurring?
- ABuffer overflow attack
- BMan-in-the-middle attack
- CSmurf attack
- DFormat string attack
- EDenial of service attack
Correct Answer:
D
D
send
light_mode
delete
Question #14
External users are reporting that a web application is slow and frequently times out when attempting to submit information. Which of the following software development best practices would have helped prevent this issue?
send
light_mode
delete
Question #15
A vulnerability scan has returned the following information:
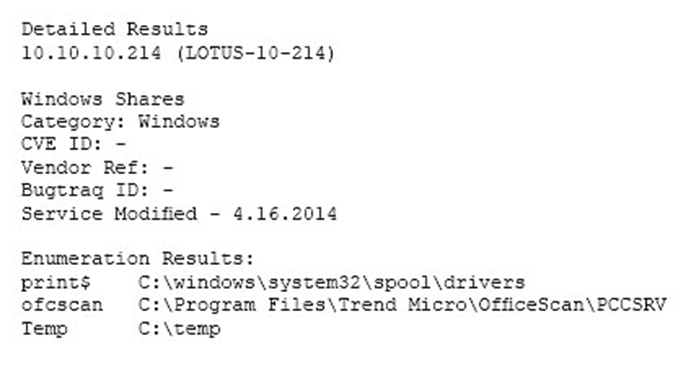
Which of the following describes the meaning of these results?

Which of the following describes the meaning of these results?
- AThere is an unknown bug in a Lotus server with no Bugtraq ID.
- BConnecting to the host using a null session allows enumeration of share names.
- CTrend Micro has a known exploit that must be resolved or patched.
- DNo CVE is present, so it is a false positive caused by Lotus running on a Windows server.
Correct Answer:
B
B
send
light_mode
delete
Question #16
A cybersecurity analyst is conducting a security test to ensure that information regarding the web server is protected from disclosure. The cybersecurity analyst requested an HTML file from the web server, and the response came back as follows:
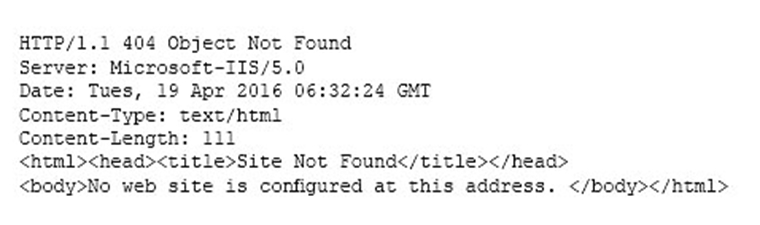
Which of the following actions should be taken to remediate this security issue?

Which of the following actions should be taken to remediate this security issue?
- ASet "Allowlatescanning" to 1 in the URLScan.ini configuration file.
- BSet "Removeserverheader" to 1 in the URLScan.ini configuration file.
- CSet "Enablelogging" to 0 in the URLScan.ini configuration file.
- DSet "Perprocesslogging" to 1 in the URLScan.ini configuration file.
Correct Answer:
B
Reference:
http://www.acunetix.com/blog/articles/configure-web-server-disclose-identity/
B
Reference:
http://www.acunetix.com/blog/articles/configure-web-server-disclose-identity/
send
light_mode
delete
Question #17
An analyst has initiated an assessment of an organization's security posture. As a part of this review, the analyst would like to determine how much information about the organization is exposed externally. Which of the following techniques would BEST help the analyst accomplish this goal? (Choose two.)
- AFingerprinting
- BDNS query log reviews
- CBanner grabbing
- DInternet searches
- EIntranet portal reviews
- FSourcing social network sites
- GTechnical control audits
Correct Answer:
DF
DF
send
light_mode
delete
Question #18
A cybersecurity professional typed in a URL and discovered the admin panel for the e-commerce application is accessible over the open web with the default password. Which of the following is the MOST secure solution to remediate this vulnerability?
- ARename the URL to a more obscure name, whitelist all corporate IP blocks, and require two-factor authentication.
- BChange the default password, whitelist specific source IP addresses, and require two-factor authentication.
- CWhitelist all corporate IP blocks, require an alphanumeric passphrase for the default password, and require two-factor authentication.
- DChange the username and default password, whitelist specific source IP addresses, and require two-factor authentication.
Correct Answer:
D
D
send
light_mode
delete
Question #19
An organization is requesting the development of a disaster recovery plan. The organization has grown and so has its infrastructure. Documentation, policies, and procedures do not exist. Which of the following steps should be taken to assist in the development of the disaster recovery plan?
- AConduct a risk assessment.
- BDevelop a data retention policy.
- CExecute vulnerability scanning.
- DIdentify assets.
Correct Answer:
D
D
send
light_mode
delete
Question #20
A company wants to update its acceptable use policy (AUP) to ensure it relates to the newly implemented password standard, which requires sponsored authentication of guest wireless devices. Which of the following is MOST likely to be incorporated in the AUP?
- ASponsored guest passwords must be at least ten characters in length and contain a symbol.
- BThe corporate network should have a wireless infrastructure that uses open authentication standards.
- CGuests using the wireless network should provide valid identification when registering their wireless devices.
- DThe network should authenticate all guest users using 802.1x backed by a RADIUS or LDAP server.
Correct Answer:
C
C
send
light_mode
delete
All Pages
