Microsoft SC-100 Exam Practice Questions (P. 5)
- Full Access (315 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #41
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your on-premises network contains an e-commerce web app that was developed in Angular and Node,js. The web app uses a MongoDB database.
You plan to migrate the web app to Azure. The solution architecture team proposes the following architecture as an Azure landing zone.
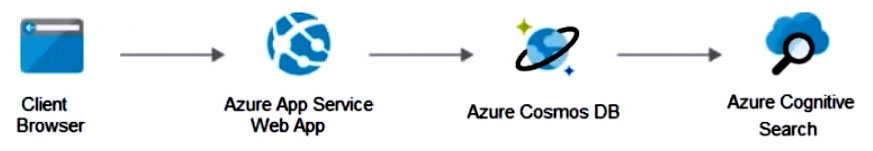
You need to provide recommendations to secure the connection between the web app and the database. The solution must follow the Zero Trust model.
Solution: You recommend implementing Azure Front Door with Azure Web Application Firewall (WAF).
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your on-premises network contains an e-commerce web app that was developed in Angular and Node,js. The web app uses a MongoDB database.
You plan to migrate the web app to Azure. The solution architecture team proposes the following architecture as an Azure landing zone.

You need to provide recommendations to secure the connection between the web app and the database. The solution must follow the Zero Trust model.
Solution: You recommend implementing Azure Front Door with Azure Web Application Firewall (WAF).
Does this meet the goal?
- AYes
- BNoMost Voted
Correct Answer:
B
Instead use solution: You recommend creating private endpoints for the web app and the database layer.
Note:
How to Use Azure Private Endpoints to Restrict Public Access to WebApps.
As an Azure administrator or architect, you are sometimes asked the question: ג€How can we safely deploy internal business applications to Azure App Services?ג€
These applications characteristically are:
Not accessible from the public internet.
Accessible from within the on-premises corporate network
Accessible via an authorized VPN client from outside the corporate network.
For such scenarios, we can use Azure Private Links, which enables private and secure access to Azure PaaS services over Azure Private Endpoints, along with the Site-to-Site VPN, Point-to-Site VPN, or the Express Route. Azure Private Endpoint is a read-only network interface service associated with the Azure PAAS
Services. It allows you to bring deployed sites into your virtual network, limiting access to them at the network level.
It uses one of the private IP addresses from your Azure VNet and associates it with the Azure App Services. These services are called Private Link resources.
They can be Azure Storage, Azure Cosmos DB, SQL, App Services Web App, your own / partner owned services, Azure Backups, Event Grids, Azure Service
Bus, or Azure Automations.
Reference:
https://www.varonis.com/blog/securing-access-azure-webapps
B
Instead use solution: You recommend creating private endpoints for the web app and the database layer.
Note:
How to Use Azure Private Endpoints to Restrict Public Access to WebApps.
As an Azure administrator or architect, you are sometimes asked the question: ג€How can we safely deploy internal business applications to Azure App Services?ג€
These applications characteristically are:
Not accessible from the public internet.
Accessible from within the on-premises corporate network
Accessible via an authorized VPN client from outside the corporate network.
For such scenarios, we can use Azure Private Links, which enables private and secure access to Azure PaaS services over Azure Private Endpoints, along with the Site-to-Site VPN, Point-to-Site VPN, or the Express Route. Azure Private Endpoint is a read-only network interface service associated with the Azure PAAS
Services. It allows you to bring deployed sites into your virtual network, limiting access to them at the network level.
It uses one of the private IP addresses from your Azure VNet and associates it with the Azure App Services. These services are called Private Link resources.
They can be Azure Storage, Azure Cosmos DB, SQL, App Services Web App, your own / partner owned services, Azure Backups, Event Grids, Azure Service
Bus, or Azure Automations.
Reference:
https://www.varonis.com/blog/securing-access-azure-webapps
send
light_mode
delete
Question #42
You have a customer that has a Microsoft 365 subscription and an Azure subscription.
The customer has devices that run either Windows, iOS, Android, or macOS. The Windows devices are deployed on-premises and in Azure.
You need to design a security solution to assess whether all the devices meet the customer's compliance rules.
What should you include in the solution?
The customer has devices that run either Windows, iOS, Android, or macOS. The Windows devices are deployed on-premises and in Azure.
You need to design a security solution to assess whether all the devices meet the customer's compliance rules.
What should you include in the solution?
- AMicrosoft Defender for Endpoint
- BMicrosoft Endpoint ManagerMost Voted
- CMicrosoft Information Protection
- DMicrosoft Sentinel
Correct Answer:
B
Microsoft Endpoint Manager includes Microsoft Intune.
Device compliance policies are a key feature when using Intune to protect your organization's resources. In Intune, you can create rules and settings that devices must meet to be considered compliant, such as a minimum OS version.
Microsoft Endpoint Manager helps deliver the modern workplace and modern management to keep your data secure, in the cloud and on-premises. Endpoint
Manager includes the services and tools you use to manage and monitor mobile devices, desktop computers, virtual machines, embedded devices, and servers.
Endpoint Manager combines services you may know and already be using, including Microsoft Intune, Configuration Manager, Desktop Analytics, co- management, and Windows Autopilot. These services are part of the Microsoft 365 stack to help secure access, protect data, respond to risk, and manage risk.
Note: Microsoft Defender for Endpoint Plan 2 protects your Windows and Linux machines whether they're hosted in Azure, hybrid clouds (on-premises), or multicloud.
Microsoft Defender for Endpoint on iOS offers protection against phishing and unsafe network connections from websites, emails, and apps.
Microsoft Defender for Endpoint on Android supports installation on both modes of enrolled devices - the legacy Device Administrator and Android Enterprise modes. Currently, Personally-owned devices with work profile and Corporate-owned fully managed user device enrollments are supported in Android Enterprise.
Reference:
https://docs.microsoft.com/en-us/mem/endpoint-manager-overview https://docs.microsoft.com/en-us/azure/defender-for-cloud/integration-defender-for-endpoint
B
Microsoft Endpoint Manager includes Microsoft Intune.
Device compliance policies are a key feature when using Intune to protect your organization's resources. In Intune, you can create rules and settings that devices must meet to be considered compliant, such as a minimum OS version.
Microsoft Endpoint Manager helps deliver the modern workplace and modern management to keep your data secure, in the cloud and on-premises. Endpoint
Manager includes the services and tools you use to manage and monitor mobile devices, desktop computers, virtual machines, embedded devices, and servers.
Endpoint Manager combines services you may know and already be using, including Microsoft Intune, Configuration Manager, Desktop Analytics, co- management, and Windows Autopilot. These services are part of the Microsoft 365 stack to help secure access, protect data, respond to risk, and manage risk.
Note: Microsoft Defender for Endpoint Plan 2 protects your Windows and Linux machines whether they're hosted in Azure, hybrid clouds (on-premises), or multicloud.
Microsoft Defender for Endpoint on iOS offers protection against phishing and unsafe network connections from websites, emails, and apps.
Microsoft Defender for Endpoint on Android supports installation on both modes of enrolled devices - the legacy Device Administrator and Android Enterprise modes. Currently, Personally-owned devices with work profile and Corporate-owned fully managed user device enrollments are supported in Android Enterprise.
Reference:
https://docs.microsoft.com/en-us/mem/endpoint-manager-overview https://docs.microsoft.com/en-us/azure/defender-for-cloud/integration-defender-for-endpoint
send
light_mode
delete
Question #43
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that has Microsoft Defender for Cloud enabled.
You are evaluating the Azure Security Benchmark V3 report.
In the Secure management ports controls, you discover that you have 0 out of a potential 8 points.
You need to recommend configurations to increase the score of the Secure management ports controls.
Solution: You recommend onboarding all virtual machines to Microsoft Defender for Endpoint.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that has Microsoft Defender for Cloud enabled.
You are evaluating the Azure Security Benchmark V3 report.
In the Secure management ports controls, you discover that you have 0 out of a potential 8 points.
You need to recommend configurations to increase the score of the Secure management ports controls.
Solution: You recommend onboarding all virtual machines to Microsoft Defender for Endpoint.
Does this meet the goal?
- AYes
- BNoMost Voted
Correct Answer:
B
Note: Secure management ports - Brute force attacks often target management ports. Use these recommendations to reduce your exposure with tools like just-in- time VM access and network security groups.
Recommendations:
- Internet-facing virtual machines should be protected with network security groups
- Management ports of virtual machines should be protected with just-in-time network access control
- Management ports should be closed on your virtual machines
Reference:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/secure-score-security-controls
B
Note: Secure management ports - Brute force attacks often target management ports. Use these recommendations to reduce your exposure with tools like just-in- time VM access and network security groups.
Recommendations:
- Internet-facing virtual machines should be protected with network security groups
- Management ports of virtual machines should be protected with just-in-time network access control
- Management ports should be closed on your virtual machines
Reference:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/secure-score-security-controls
send
light_mode
delete
Question #44
Your company has an Azure subscription that has enhanced security enabled for Microsoft Defender for Cloud.
The company signs a contract with the United States government.
You need to review the current subscription for NIST 800-53 compliance.
What should you do first?
The company signs a contract with the United States government.
You need to review the current subscription for NIST 800-53 compliance.
What should you do first?
- AFrom Defender for Cloud, review the secure score recommendations.
- BFrom Microsoft Sentinel, configure the Microsoft Defender for Cloud data connector.
- CFrom Defender for Cloud, review the Azure security baseline for audit report.
- DFrom Defender for Cloud, add a regulatory compliance standard.Most Voted
Correct Answer:
D
Add a regulatory standard to your dashboard
The following steps explain how to add a package to monitor your compliance with one of the supported regulatory standards.
Add a standard to your Azure resources
1. From Defender for Cloud's menu, select Regulatory compliance to open the regulatory compliance dashboard. Here you can see the compliance standards currently assigned to the currently selected subscriptions.
2. From the top of the page, select Manage compliance policies. The Policy Management page appears.
3. Select the subscription or management group for which you want to manage the regulatory compliance posture.
4. To add the standards relevant to your organization, expand the Industry & regulatory standards section and select Add more standards.
5. From the Add regulatory compliance standards page, you can search for any of the available standards:
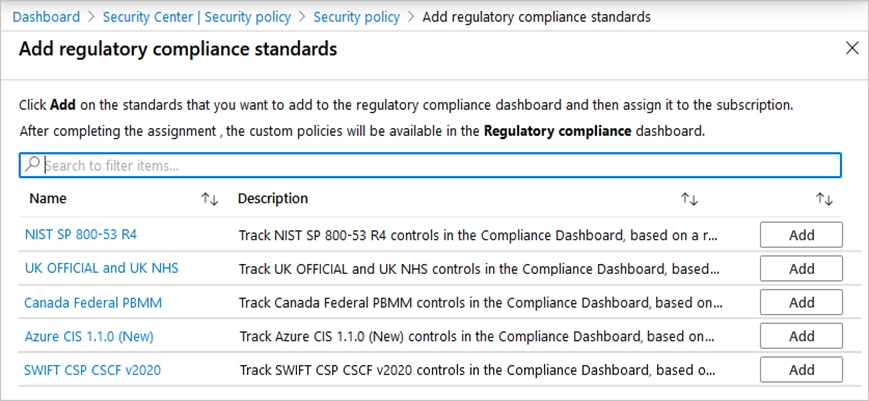
6. Select Add and enter all the necessary details for the specific initiative such as scope, parameters, and remediation.
7. From Defender for Cloud's menu, select Regulatory compliance again to go back to the regulatory compliance dashboard.
Your new standard appears in your list of Industry & regulatory standards.
Note: Customize the set of standards in your regulatory compliance dashboard.
Microsoft Defender for Cloud continually compares the configuration of your resources with requirements in industry standards, regulations, and benchmarks. The regulatory compliance dashboard provides insights into your compliance posture based on how you're meeting specific compliance requirements.
Reference:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/update-regulatory-compliance-packages
D
Add a regulatory standard to your dashboard
The following steps explain how to add a package to monitor your compliance with one of the supported regulatory standards.
Add a standard to your Azure resources
1. From Defender for Cloud's menu, select Regulatory compliance to open the regulatory compliance dashboard. Here you can see the compliance standards currently assigned to the currently selected subscriptions.
2. From the top of the page, select Manage compliance policies. The Policy Management page appears.
3. Select the subscription or management group for which you want to manage the regulatory compliance posture.
4. To add the standards relevant to your organization, expand the Industry & regulatory standards section and select Add more standards.
5. From the Add regulatory compliance standards page, you can search for any of the available standards:

6. Select Add and enter all the necessary details for the specific initiative such as scope, parameters, and remediation.
7. From Defender for Cloud's menu, select Regulatory compliance again to go back to the regulatory compliance dashboard.
Your new standard appears in your list of Industry & regulatory standards.
Note: Customize the set of standards in your regulatory compliance dashboard.
Microsoft Defender for Cloud continually compares the configuration of your resources with requirements in industry standards, regulations, and benchmarks. The regulatory compliance dashboard provides insights into your compliance posture based on how you're meeting specific compliance requirements.
Reference:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/update-regulatory-compliance-packages
send
light_mode
delete
Question #45
Your company has devices that run either Windows 10, Windows 11, or Windows Server.
You are in the process of improving the security posture of the devices.
You plan to use security baselines from the Microsoft Security Compliance Toolkit.
What should you recommend using to compare the baselines to the current device configurations?
You are in the process of improving the security posture of the devices.
You plan to use security baselines from the Microsoft Security Compliance Toolkit.
What should you recommend using to compare the baselines to the current device configurations?
- AMicrosoft Intune
- BLocal Group Policy Object (LGPO)
- CWindows Autopilot
- DPolicy AnalyzerMost Voted
Correct Answer:
D
Microsoft Security Compliance Toolkit 1.0, Policy Analyzer.
The Policy Analyzer is a utility for analyzing and comparing sets of Group Policy Objects (GPOs). Its main features include:
Highlight when a set of Group Policies has redundant settings or internal inconsistencies.
Highlight the differences between versions or sets of Group Policies.
Compare GPOs against current local policy and local registry settings
Export results to a Microsoft Excel spreadsheet
Policy Analyzer lets you treat a set of GPOs as a single unit. This treatment makes it easy to determine whether particular settings are duplicated across the
GPOs or are set to conflicting values. Policy Analyzer also lets you capture a baseline and then compare it to a snapshot taken at a later time to identify changes anywhere across the set.
Note: The Security Compliance Toolkit (SCT) is a set of tools that allows enterprise security administrators to download, analyze, test, edit, and store Microsoft- recommended security configuration baselines for Windows and other Microsoft products.
The SCT enables administrators to effectively manage their enterprise's Group Policy Objects (GPOs). Using the toolkit, administrators can compare their current
GPOs with Microsoft-recommended GPO baselines or other baselines, edit them, store them in GPO backup file format, and apply them broadly through Active
Directory or individually through local policy.
Security Compliance Toolkit Tools:
Policy Analyzer -
Local Group Policy Object (LGPO)
Set Object Security -
GPO to Policy Rules -
Incorrect:
Not B: Local Group Policy Object (LGPO)
What is the Local Group Policy Object (LGPO) tool?
LGPO.exe is a command-line utility that is designed to help automate management of Local Group Policy. Using local policy gives administrators a simple way to verify the effects of Group Policy settings, and is also useful for managing non-domain-joined systems. LGPO.exe can import and apply settings from Registry
Policy (Registry.pol) files, security templates, Advanced Auditing backup files, as well as from formatted ג€LGPO textג€ files. It can export local policy to a GPO backup. It can export the contents of a Registry Policy file to the ג€LGPO textג€ format that can then be edited, and can build a Registry Policy file from an LGPO text file.
Reference:
https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-security-configuration-framework/security-compliance-toolkit-10
D
Microsoft Security Compliance Toolkit 1.0, Policy Analyzer.
The Policy Analyzer is a utility for analyzing and comparing sets of Group Policy Objects (GPOs). Its main features include:
Highlight when a set of Group Policies has redundant settings or internal inconsistencies.
Highlight the differences between versions or sets of Group Policies.
Compare GPOs against current local policy and local registry settings
Export results to a Microsoft Excel spreadsheet
Policy Analyzer lets you treat a set of GPOs as a single unit. This treatment makes it easy to determine whether particular settings are duplicated across the
GPOs or are set to conflicting values. Policy Analyzer also lets you capture a baseline and then compare it to a snapshot taken at a later time to identify changes anywhere across the set.
Note: The Security Compliance Toolkit (SCT) is a set of tools that allows enterprise security administrators to download, analyze, test, edit, and store Microsoft- recommended security configuration baselines for Windows and other Microsoft products.
The SCT enables administrators to effectively manage their enterprise's Group Policy Objects (GPOs). Using the toolkit, administrators can compare their current
GPOs with Microsoft-recommended GPO baselines or other baselines, edit them, store them in GPO backup file format, and apply them broadly through Active
Directory or individually through local policy.
Security Compliance Toolkit Tools:
Policy Analyzer -
Local Group Policy Object (LGPO)
Set Object Security -
GPO to Policy Rules -
Incorrect:
Not B: Local Group Policy Object (LGPO)
What is the Local Group Policy Object (LGPO) tool?
LGPO.exe is a command-line utility that is designed to help automate management of Local Group Policy. Using local policy gives administrators a simple way to verify the effects of Group Policy settings, and is also useful for managing non-domain-joined systems. LGPO.exe can import and apply settings from Registry
Policy (Registry.pol) files, security templates, Advanced Auditing backup files, as well as from formatted ג€LGPO textג€ files. It can export local policy to a GPO backup. It can export the contents of a Registry Policy file to the ג€LGPO textג€ format that can then be edited, and can build a Registry Policy file from an LGPO text file.
Reference:
https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-security-configuration-framework/security-compliance-toolkit-10
send
light_mode
delete
Question #46
You have Microsoft Defender for Cloud assigned to Azure management groups.
You have a Microsoft Sentinel deployment.
During the triage of alerts, you require additional information about the security events, including suggestions for remediation.
Which two components can you use to achieve the goal? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
You have a Microsoft Sentinel deployment.
During the triage of alerts, you require additional information about the security events, including suggestions for remediation.
Which two components can you use to achieve the goal? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- AMicrosoft Sentinel threat intelligence workbooksMost Voted
- BMicrosoft Sentinel notebooks
- Cthreat intelligence reports in Defender for CloudMost Voted
- Dworkload protections in Defender for Cloud
Correct Answer:
AC
A: Workbooks provide insights about your threat intelligence
Workbooks provide powerful interactive dashboards that give you insights into all aspects of Microsoft Sentinel, and threat intelligence is no exception. You can use the built-in Threat Intelligence workbook to visualize key information about your threat intelligence, and you can easily customize the workbook according to your business needs. You can even create new dashboards combining many different data sources so you can visualize your data in unique ways. Since
Microsoft Sentinel workbooks are based on Azure Monitor workbooks, there is already extensive documentation available, and many more templates.
C: What is a threat intelligence report?
Defender for Cloud's threat protection works by monitoring security information from your Azure resources, the network, and connected partner solutions. It analyzes this information, often correlating information from multiple sources, to identify threats.
Defender for Cloud has three types of threat reports, which can vary according to the attack. The reports available are:
Activity Group Report: provides deep dives into attackers, their objectives, and tactics.
Campaign Report: focuses on details of specific attack campaigns.
Threat Summary Report: covers all of the items in the previous two reports.
This type of information is useful during the incident response process, where there's an ongoing investigation to understand the source of the attack, the attacker's motivations, and what to do to mitigate this issue in the future.
Incorrect:
Not B: When to use Jupyter notebooks
While many common tasks can be carried out in the portal, Jupyter extends the scope of what you can do with this data.
For example, use notebooks to:
Perform analytics that aren't provided out-of-the box in Microsoft Sentinel, such as some Python machine learning features
Create data visualizations that aren't provided out-of-the box in Microsoft Sentinel, such as custom timelines and process trees
Integrate data sources outside of Microsoft Sentinel, such as an on-premises data set.
Not D: Defender for Cloud offers security alerts that are powered by Microsoft Threat Intelligence. It also includes a range of advanced, intelligent, protections for your workloads. The workload protections are provided through Microsoft Defender plans specific to the types of resources in your subscriptions. For example, you can enable Microsoft Defender for Storage to get alerted about suspicious activities related to your Azure Storage accounts.
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/understand-threat-intelligence https://docs.microsoft.com/en-us/azure/defender-for-cloud/defender-for-cloud-introduction https://docs.microsoft.com/en-us/azure/defender-for-cloud/threat-intelligence-reports https://docs.microsoft.com/en-us/azure/sentinel/notebooks
AC
A: Workbooks provide insights about your threat intelligence
Workbooks provide powerful interactive dashboards that give you insights into all aspects of Microsoft Sentinel, and threat intelligence is no exception. You can use the built-in Threat Intelligence workbook to visualize key information about your threat intelligence, and you can easily customize the workbook according to your business needs. You can even create new dashboards combining many different data sources so you can visualize your data in unique ways. Since
Microsoft Sentinel workbooks are based on Azure Monitor workbooks, there is already extensive documentation available, and many more templates.
C: What is a threat intelligence report?
Defender for Cloud's threat protection works by monitoring security information from your Azure resources, the network, and connected partner solutions. It analyzes this information, often correlating information from multiple sources, to identify threats.
Defender for Cloud has three types of threat reports, which can vary according to the attack. The reports available are:
Activity Group Report: provides deep dives into attackers, their objectives, and tactics.
Campaign Report: focuses on details of specific attack campaigns.
Threat Summary Report: covers all of the items in the previous two reports.
This type of information is useful during the incident response process, where there's an ongoing investigation to understand the source of the attack, the attacker's motivations, and what to do to mitigate this issue in the future.
Incorrect:
Not B: When to use Jupyter notebooks
While many common tasks can be carried out in the portal, Jupyter extends the scope of what you can do with this data.
For example, use notebooks to:
Perform analytics that aren't provided out-of-the box in Microsoft Sentinel, such as some Python machine learning features
Create data visualizations that aren't provided out-of-the box in Microsoft Sentinel, such as custom timelines and process trees
Integrate data sources outside of Microsoft Sentinel, such as an on-premises data set.
Not D: Defender for Cloud offers security alerts that are powered by Microsoft Threat Intelligence. It also includes a range of advanced, intelligent, protections for your workloads. The workload protections are provided through Microsoft Defender plans specific to the types of resources in your subscriptions. For example, you can enable Microsoft Defender for Storage to get alerted about suspicious activities related to your Azure Storage accounts.
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/understand-threat-intelligence https://docs.microsoft.com/en-us/azure/defender-for-cloud/defender-for-cloud-introduction https://docs.microsoft.com/en-us/azure/defender-for-cloud/threat-intelligence-reports https://docs.microsoft.com/en-us/azure/sentinel/notebooks
send
light_mode
delete
Question #47
A customer is deploying Docker images to 10 Azure Kubernetes Service (AKS) resources across four Azure subscriptions.
You are evaluating the security posture of the customer.
You discover that the AKS resources are excluded from the secure score recommendations.
You need to produce accurate recommendations and update the secure score.
Which two actions should you recommend in Microsoft Defender for Cloud? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You are evaluating the security posture of the customer.
You discover that the AKS resources are excluded from the secure score recommendations.
You need to produce accurate recommendations and update the secure score.
Which two actions should you recommend in Microsoft Defender for Cloud? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- AEnable Defender plans.Most Voted
- BConfigure auto provisioning.Most Voted
- CAdd a workflow automation.
- DAssign regulatory compliance policies.
- EReview the inventory.
send
light_mode
delete
Question #48
Your company has an office in Seattle.
The company has two Azure virtual machine scale sets hosted on different virtual networks.
The company plans to contract developers in India.
You need to recommend a solution provide the developers with the ability to connect to the virtual machines over SSL from the Azure portal. The solution must meet the following requirements:
✑ Prevent exposing the public IP addresses of the virtual machines.
✑ Provide the ability to connect without using a VPN.
✑ Minimize costs.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
The company has two Azure virtual machine scale sets hosted on different virtual networks.
The company plans to contract developers in India.
You need to recommend a solution provide the developers with the ability to connect to the virtual machines over SSL from the Azure portal. The solution must meet the following requirements:
✑ Prevent exposing the public IP addresses of the virtual machines.
✑ Provide the ability to connect without using a VPN.
✑ Minimize costs.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- ACreate a hub and spoke network by using virtual network peering.Most Voted
- BDeploy Azure Bastion to each virtual network.
- CDeploy Azure Bastion to one virtual network.Most Voted
- DCreate NAT rules and network rules in Azure Firewall.
- EEnable just-in-time VM access on the virtual machines.
Correct Answer:
AC
Azure Bastion is deployed to a virtual network and supports virtual network peering. Specifically, Azure Bastion manages RDP/SSH connectivity to VMs created in the local or peered virtual networks.
Note: Azure Bastion is a service you deploy that lets you connect to a virtual machine using your browser and the Azure portal. The Azure Bastion service is a fully platform-managed PaaS service that you provision inside your virtual network. It provides secure and seamless RDP/SSH connectivity to your virtual machines directly from the Azure portal over TLS. When you connect via Azure Bastion, your virtual machines don't need a public IP address, agent, or special client software.
Incorrect:
Not B: Two Azure Bastions would increase the cost.
Reference:
https://docs.microsoft.com/en-us/azure/bastion/bastion-overview
AC
Azure Bastion is deployed to a virtual network and supports virtual network peering. Specifically, Azure Bastion manages RDP/SSH connectivity to VMs created in the local or peered virtual networks.
Note: Azure Bastion is a service you deploy that lets you connect to a virtual machine using your browser and the Azure portal. The Azure Bastion service is a fully platform-managed PaaS service that you provision inside your virtual network. It provides secure and seamless RDP/SSH connectivity to your virtual machines directly from the Azure portal over TLS. When you connect via Azure Bastion, your virtual machines don't need a public IP address, agent, or special client software.
Incorrect:
Not B: Two Azure Bastions would increase the cost.
Reference:
https://docs.microsoft.com/en-us/azure/bastion/bastion-overview
send
light_mode
delete
Question #49
HOTSPOT -
You are designing security for a runbook in an Azure Automation account. The runbook will copy data to Azure Data Lake Storage Gen2.
You need to recommend a solution to secure the components of the copy process.
What should you include in the recommendation for each component? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
You are designing security for a runbook in an Azure Automation account. The runbook will copy data to Azure Data Lake Storage Gen2.
You need to recommend a solution to secure the components of the copy process.
What should you include in the recommendation for each component? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:
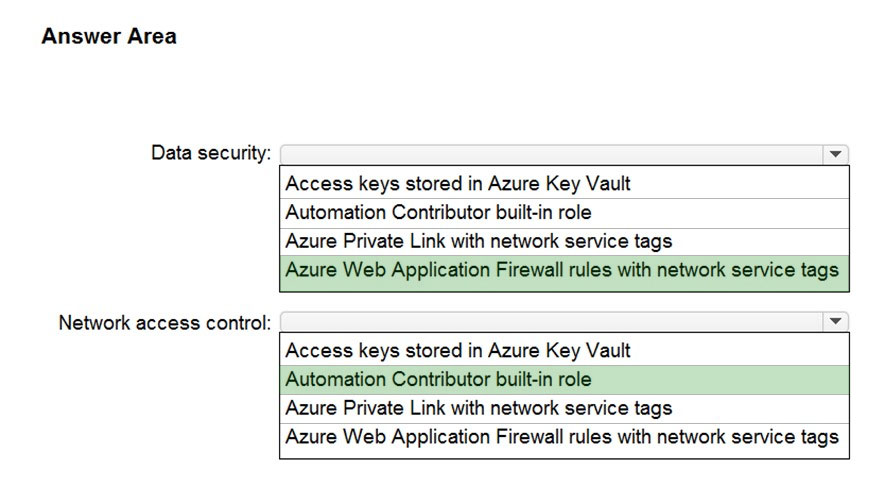
Box 1: Azure Web Application Firewall with network service tags
A service tag represents a group of IP address prefixes from a given Azure service. Microsoft manages the address prefixes encompassed by the service tag and automatically updates the service tag as addresses change, minimizing the complexity of frequent updates to network security rules.
You can use service tags to define network access controls on network security groups, Azure Firewall, and user-defined routes.
Incorrect:
* Not Azure private link with network service tags
Network service tags are not used with Private links.
Box 2: Automation Contributor built-in role
The Automation Contributor role allows you to manage all resources in the Automation account, except modifying other user's access permissions to an
Automation account.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/service-tags-overview https://docs.microsoft.com/en-us/azure/automation/automation-role-based-access-control

Box 1: Azure Web Application Firewall with network service tags
A service tag represents a group of IP address prefixes from a given Azure service. Microsoft manages the address prefixes encompassed by the service tag and automatically updates the service tag as addresses change, minimizing the complexity of frequent updates to network security rules.
You can use service tags to define network access controls on network security groups, Azure Firewall, and user-defined routes.
Incorrect:
* Not Azure private link with network service tags
Network service tags are not used with Private links.
Box 2: Automation Contributor built-in role
The Automation Contributor role allows you to manage all resources in the Automation account, except modifying other user's access permissions to an
Automation account.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/service-tags-overview https://docs.microsoft.com/en-us/azure/automation/automation-role-based-access-control
send
light_mode
delete
Question #50
You have Windows 11 devices and Microsoft 365 E5 licenses.
You need to recommend a solution to prevent users from accessing websites that contain adult content such as gambling sites.
What should you include in the recommendation?
You need to recommend a solution to prevent users from accessing websites that contain adult content such as gambling sites.
What should you include in the recommendation?
- ACompliance Manager
- BMicrosoft Defender for Cloud Apps
- CMicrosoft Endpoint Manager
- DMicrosoft Defender for EndpointMost Voted
Correct Answer:
D
Web content filtering is part of the Web protection capabilities in Microsoft Defender for Endpoint. It enables your organization to track and regulate access to websites based on their content categories. Many of these websites, while not malicious, might be problematic because of compliance regulations, bandwidth usage, or other concerns.
Note: Turn on web content filtering
From the left-hand navigation in Microsoft 365 Defender portal, select Settings > Endpoints > General > Advanced Features. Scroll down until you see the entry for Web content filtering. Switch the toggle to On and Save preferences.
Configure web content filtering policies
Web content filtering policies specify which site categories are blocked on which device groups. To manage the policies, go to Settings > Endpoints > Web content filtering (under Rules).
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/web-content-filtering
D
Web content filtering is part of the Web protection capabilities in Microsoft Defender for Endpoint. It enables your organization to track and regulate access to websites based on their content categories. Many of these websites, while not malicious, might be problematic because of compliance regulations, bandwidth usage, or other concerns.
Note: Turn on web content filtering
From the left-hand navigation in Microsoft 365 Defender portal, select Settings > Endpoints > General > Advanced Features. Scroll down until you see the entry for Web content filtering. Switch the toggle to On and Save preferences.
Configure web content filtering policies
Web content filtering policies specify which site categories are blocked on which device groups. To manage the policies, go to Settings > Endpoints > Web content filtering (under Rules).
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/web-content-filtering
send
light_mode
delete
All Pages
