Microsoft SC-100 Exam Practice Questions (P. 2)
- Full Access (315 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #11
Your company has a third-party security information and event management (SIEM) solution that uses Splunk and Microsoft Sentinel.
You plan to integrate Microsoft Sentinel with Splunk.
You need to recommend a solution to send security events from Microsoft Sentinel to Splunk.
What should you include in the recommendation?
You plan to integrate Microsoft Sentinel with Splunk.
You need to recommend a solution to send security events from Microsoft Sentinel to Splunk.
What should you include in the recommendation?
- Aa Microsoft Sentinel data connector
- BAzure Event HubsMost Voted
- Ca Microsoft Sentinel workbook
- DAzure Data Factory
Correct Answer:
B
Microsoft Sentinel Add-On for Splunk allows Azure Log Analytics and Microsoft Sentinel users to ingest security logs from Splunk platform using the Azure HTTP
Data Collector API.
Reference:
https://splunkbase.splunk.com/app/5312/
B
Microsoft Sentinel Add-On for Splunk allows Azure Log Analytics and Microsoft Sentinel users to ingest security logs from Splunk platform using the Azure HTTP
Data Collector API.
Reference:
https://splunkbase.splunk.com/app/5312/
send
light_mode
delete
Question #12
A customer follows the Zero Trust model and explicitly verifies each attempt to access its corporate applications.
The customer discovers that several endpoints are infected with malware.
The customer suspends access attempts from the infected endpoints.
The malware is removed from the endpoints.
Which two conditions must be met before endpoint users can access the corporate applications again? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
The customer discovers that several endpoints are infected with malware.
The customer suspends access attempts from the infected endpoints.
The malware is removed from the endpoints.
Which two conditions must be met before endpoint users can access the corporate applications again? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- AThe client access tokens are refreshed.
- BMicrosoft Intune reports the endpoints as compliant.Most Voted
- CA new Azure Active Directory (Azure AD) Conditional Access policy is enforced.
- DMicrosoft Defender for Endpoint reports the endpoints as compliant.Most Voted
send
light_mode
delete
Question #13
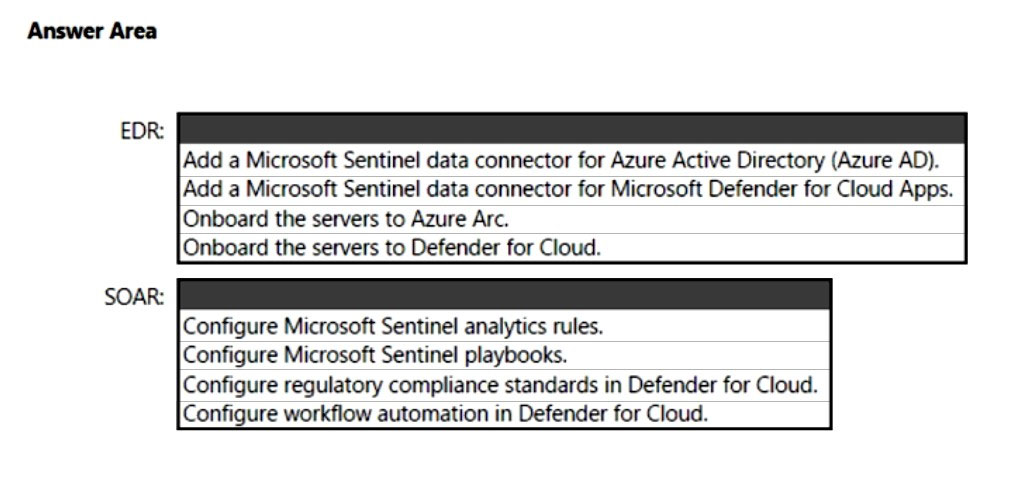
HOTSPOT -
You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender and Microsoft Defender for Cloud are enabled.
The Azure subscription contains a Microsoft Sentinel workspace. Microsoft Sentinel data connectors are configured for Microsoft 365, Microsoft 365 Defender,
Defender for Cloud, and Azure.
You plan to deploy Azure virtual machines that will run Windows Server.
You need to enable extended detection and response (EDR) and security orchestration, automation, and response (SOAR) capabilities for Microsoft Sentinel.
How should you recommend enabling each capability? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender and Microsoft Defender for Cloud are enabled.
The Azure subscription contains a Microsoft Sentinel workspace. Microsoft Sentinel data connectors are configured for Microsoft 365, Microsoft 365 Defender,
Defender for Cloud, and Azure.
You plan to deploy Azure virtual machines that will run Windows Server.
You need to enable extended detection and response (EDR) and security orchestration, automation, and response (SOAR) capabilities for Microsoft Sentinel.
How should you recommend enabling each capability? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:
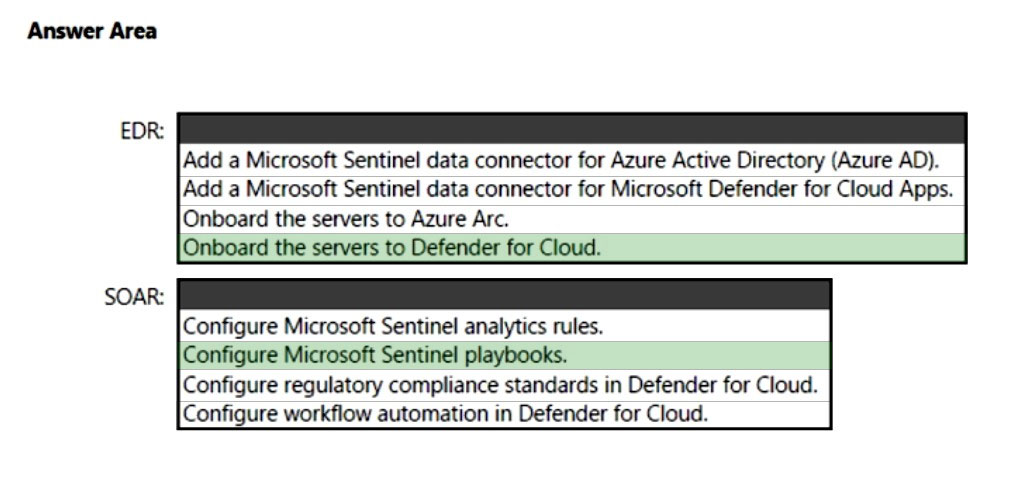
Box 1: Onboard the servers to Defender for Cloud.
Extended detection and response (XDR) is a new approach defined by industry analysts that are designed to deliver intelligent, automated, and integrated security across domains to help defenders connect seemingly disparate alerts and get ahead of attackers.
As part of this announcement, we are unifying all XDR technologies under the Microsoft Defender brand. The new Microsoft Defender is the most comprehensive
XDR in the market today and prevents, detects, and responds to threats across identities, endpoints, applications, email, IoT, infrastructure, and cloud platforms.
Box 2: Configure Microsoft Sentinel playbooks.
As a SOAR platform, its primary purposes are to automate any recurring and predictable enrichment, response and remediation tasks that are the responsibility of
Security Operations Centers (SOC/SecOps). Leveraging SOAR frees up time and resources for more in-depth investigation of and hunting for advanced threats.
Automation takes a few different forms in Microsoft Sentinel, from automation rules that centrally manage the automation of incident handling and response to playbooks that run predetermined sequences of actions to provide robust and flexible advanced automation to your threat response tasks.
Reference:
https://www.microsoft.com/security/blog/2020/09/22/microsoft-unified-siem-xdr-modernize-security-operations/ https://techcommunity.microsoft.com/t5/microsoft-sentinel-blog/become-a-microsoft-sentinel-automation-ninja/ba-p/3563377

Box 1: Onboard the servers to Defender for Cloud.
Extended detection and response (XDR) is a new approach defined by industry analysts that are designed to deliver intelligent, automated, and integrated security across domains to help defenders connect seemingly disparate alerts and get ahead of attackers.
As part of this announcement, we are unifying all XDR technologies under the Microsoft Defender brand. The new Microsoft Defender is the most comprehensive
XDR in the market today and prevents, detects, and responds to threats across identities, endpoints, applications, email, IoT, infrastructure, and cloud platforms.
Box 2: Configure Microsoft Sentinel playbooks.
As a SOAR platform, its primary purposes are to automate any recurring and predictable enrichment, response and remediation tasks that are the responsibility of
Security Operations Centers (SOC/SecOps). Leveraging SOAR frees up time and resources for more in-depth investigation of and hunting for advanced threats.
Automation takes a few different forms in Microsoft Sentinel, from automation rules that centrally manage the automation of incident handling and response to playbooks that run predetermined sequences of actions to provide robust and flexible advanced automation to your threat response tasks.
Reference:
https://www.microsoft.com/security/blog/2020/09/22/microsoft-unified-siem-xdr-modernize-security-operations/ https://techcommunity.microsoft.com/t5/microsoft-sentinel-blog/become-a-microsoft-sentinel-automation-ninja/ba-p/3563377
send
light_mode
delete
Question #14
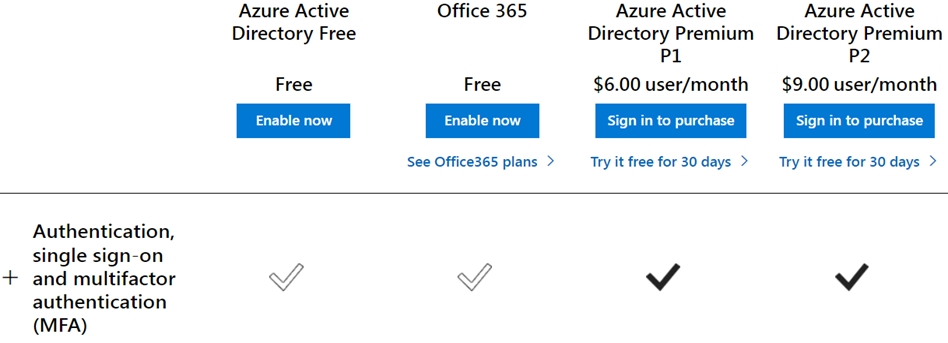
You have a customer that has a Microsoft 365 subscription and uses the Free edition of Azure Active Directory (Azure AD).
The customer plans to obtain an Azure subscription and provision several Azure resources.
You need to evaluate the customer's security environment.
What will necessitate an upgrade from the Azure AD Free edition to the Premium edition?
The customer plans to obtain an Azure subscription and provision several Azure resources.
You need to evaluate the customer's security environment.
What will necessitate an upgrade from the Azure AD Free edition to the Premium edition?
- AAzure AD Privileged Identity Management (PIM)Most Voted
- Brole-based authorization
- Cresource-based authorization
- DAzure AD Multi-Factor Authentication
Correct Answer:
A
Multifactor authentication (MFA), an important component of the Zero Trust Model, is missing in Azure AD Free edition.
Reference:
https://www.microsoft.com/en-us/security/business/identity-access/azure-active-directory-pricing
A
Multifactor authentication (MFA), an important component of the Zero Trust Model, is missing in Azure AD Free edition.

Reference:
https://www.microsoft.com/en-us/security/business/identity-access/azure-active-directory-pricing
send
light_mode
delete
Question #15
You are designing the security standards for a new Azure environment.
You need to design a privileged identity strategy based on the Zero Trust model.
Which framework should you follow to create the design?
You need to design a privileged identity strategy based on the Zero Trust model.
Which framework should you follow to create the design?
- AMicrosoft Security Development Lifecycle (SDL)
- BEnhanced Security Admin Environment (ESAE)
- CRapid Modernization Plan (RaMP)Most Voted
- DMicrosoft Operational Security Assurance (OSA)
Correct Answer:
C
RaMP initiatives for Zero Trust.
To rapidly adopt Zero Trust in your organization, RaMP offers technical deployment guidance organized in these initiatives.
In particular, meet these deployment objectives to protect your privileged identities with Zero Trust.
1. Deploy secured privileged access to protect administrative user accounts.
2. Deploy Azure AD Privileged Identity Management (PIM) for a time-bound, just-in-time approval process for the use of privileged user accounts.
Note 1: RaMP guidance takes a project management and checklist approach:
* User access and productivity
1. Explicitly validate trust for all access requests
Identities -
Endpoints (devices)
Apps -
Network -
* Data, compliance, and governance
2. Ransomware recovery readiness
3. Data
* Modernize security operations
4. Streamline response
5. Unify visibility
6. Reduce manual effort
Note 2: As an alternative to deployment guidance that provides detailed configuration steps for each of the technology pillars being protected by Zero Trust principles, Rapid Modernization Plan (RaMP) guidance is based on initiatives and gives you a set of deployment paths to more quickly implement key layers of protection.
By providing a suggested mapping of key stakeholders, implementers, and their accountabilities, you can more quickly organize an internal project and define the tasks and owners to drive them to conclusion.
By providing a checklist of deployment objectives and implementation steps, you can see the bigger picture of infrastructure requirements and track your progress.
Incorrect:
Not B: Enhanced Security Admin Environment (ESAE)
The Enhanced Security Admin Environment (ESAE) architecture (often referred to as red forest, admin forest, or hardened forest) is an approach to provide a secure environment for Windows Server Active Directory (AD) administrators.
Microsoft's recommendation to use this architectural pattern has been replaced by the modern privileged access strategy and rapid modernization plan (RAMP) guidance as the default recommended approach for securing privileged users. The ESAE hardened administrative forest pattern (on-prem or cloud-based) is now considered a custom configuration suitable only for exception cases listed below.
What are the valid ESAE use cases?
While not a mainstream recommendation, this architectural pattern is valid in a limited set of scenarios.
In these exception cases, the organization must accept the increased technical complexity and operational costs of the solution. The organization must have a sophisticated security program to measure risk, monitor risk, and apply consistent operational rigor to the usage and maintenance of the ESAE implementation.
Example scenarios include:
Isolated on-premises environments - where cloud services are unavailable such as offline research laboratories, critical infrastructure or utilities, disconnected operational technology (OT) environments such as Supervisory control and data acquisition (SCADA) / Industrial Control Systems (ICS), and public sector customers that are fully reliant on on-premises technology.
Highly regulated environments ג€" industry or government regulation may specifically require an administrative forest configuration.
High level security assurance is mandated - organizations with low risk tolerance that are willing to accept the increased complexity and operational cost of the solution.
Reference:
https://docs.microsoft.com/en-us/security/zero-trust/zero-trust-ramp-overview https://docs.microsoft.com/en-us/security/zero-trust/user-access-productivity-validate-trust#identities https://docs.microsoft.com/en-us/security/compass/esae-retirement
C
RaMP initiatives for Zero Trust.
To rapidly adopt Zero Trust in your organization, RaMP offers technical deployment guidance organized in these initiatives.
In particular, meet these deployment objectives to protect your privileged identities with Zero Trust.
1. Deploy secured privileged access to protect administrative user accounts.
2. Deploy Azure AD Privileged Identity Management (PIM) for a time-bound, just-in-time approval process for the use of privileged user accounts.
Note 1: RaMP guidance takes a project management and checklist approach:
* User access and productivity
1. Explicitly validate trust for all access requests
Identities -
Endpoints (devices)
Apps -
Network -
* Data, compliance, and governance
2. Ransomware recovery readiness
3. Data
* Modernize security operations
4. Streamline response
5. Unify visibility
6. Reduce manual effort
Note 2: As an alternative to deployment guidance that provides detailed configuration steps for each of the technology pillars being protected by Zero Trust principles, Rapid Modernization Plan (RaMP) guidance is based on initiatives and gives you a set of deployment paths to more quickly implement key layers of protection.
By providing a suggested mapping of key stakeholders, implementers, and their accountabilities, you can more quickly organize an internal project and define the tasks and owners to drive them to conclusion.
By providing a checklist of deployment objectives and implementation steps, you can see the bigger picture of infrastructure requirements and track your progress.
Incorrect:
Not B: Enhanced Security Admin Environment (ESAE)
The Enhanced Security Admin Environment (ESAE) architecture (often referred to as red forest, admin forest, or hardened forest) is an approach to provide a secure environment for Windows Server Active Directory (AD) administrators.
Microsoft's recommendation to use this architectural pattern has been replaced by the modern privileged access strategy and rapid modernization plan (RAMP) guidance as the default recommended approach for securing privileged users. The ESAE hardened administrative forest pattern (on-prem or cloud-based) is now considered a custom configuration suitable only for exception cases listed below.
What are the valid ESAE use cases?
While not a mainstream recommendation, this architectural pattern is valid in a limited set of scenarios.
In these exception cases, the organization must accept the increased technical complexity and operational costs of the solution. The organization must have a sophisticated security program to measure risk, monitor risk, and apply consistent operational rigor to the usage and maintenance of the ESAE implementation.
Example scenarios include:
Isolated on-premises environments - where cloud services are unavailable such as offline research laboratories, critical infrastructure or utilities, disconnected operational technology (OT) environments such as Supervisory control and data acquisition (SCADA) / Industrial Control Systems (ICS), and public sector customers that are fully reliant on on-premises technology.
Highly regulated environments ג€" industry or government regulation may specifically require an administrative forest configuration.
High level security assurance is mandated - organizations with low risk tolerance that are willing to accept the increased complexity and operational cost of the solution.
Reference:
https://docs.microsoft.com/en-us/security/zero-trust/zero-trust-ramp-overview https://docs.microsoft.com/en-us/security/zero-trust/user-access-productivity-validate-trust#identities https://docs.microsoft.com/en-us/security/compass/esae-retirement
send
light_mode
delete
Question #16
A customer has a hybrid cloud infrastructure that contains a Microsoft 365 E5 subscription and an Azure subscription.
All on-premises servers in the perimeter network are prevented from connecting directly to the internet.
The customer recently recovered from a ransomware attack.
The customer plans to deploy Microsoft Sentinel.
You need to recommend solutions to meet the following requirements:
✑ Ensure that the security operations team can access the security logs and the operation logs.
✑ Ensure that the IT operations team can access only the operations logs, including the event logs of the servers in the perimeter network.
Which two solutions should you include in the recommendation? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
All on-premises servers in the perimeter network are prevented from connecting directly to the internet.
The customer recently recovered from a ransomware attack.
The customer plans to deploy Microsoft Sentinel.
You need to recommend solutions to meet the following requirements:
✑ Ensure that the security operations team can access the security logs and the operation logs.
✑ Ensure that the IT operations team can access only the operations logs, including the event logs of the servers in the perimeter network.
Which two solutions should you include in the recommendation? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- Aa custom collector that uses the Log Analytics agent
- Bthe Azure Monitor agentMost Voted
- Cresource-based role-based access control (RBAC)Most Voted
- DAzure Active Directory (Azure AD) Conditional Access policies
Correct Answer:
BC
A: You can collect data in custom log formats to Microsoft Sentinel with the Log Analytics agent.
Note: You can use the Log Analytics agent to collect data in text files of nonstandard formats from both Windows and Linux computers. Once collected, you can either parse the data into individual fields in your queries or extract the data during collection to individual fields.
You can connect your data sources to Microsoft Sentinel using custom log formats.
C: Microsoft Sentinel uses Azure role-based access control (Azure RBAC) to provide built-in roles that can be assigned to users, groups, and services in Azure.
Use Azure RBAC to create and assign roles within your security operations team to grant appropriate access to Microsoft Sentinel. The different roles give you fine-grained control over what Microsoft Sentinel users can see and do. Azure roles can be assigned in the Microsoft Sentinel workspace directly (see note below), or in a subscription or resource group that the workspace belongs to, which Microsoft Sentinel inherits.
Incorrect:
A: You can collect data in custom log formats to Microsoft Sentinel with the Log Analytics agent.
Note: You can use the Log Analytics agent to collect data in text files of nonstandard formats from both Windows and Linux computers. Once collected, you can either parse the data into individual fields in your queries or extract the data during collection to individual fields.
You can connect your data sources to Microsoft Sentinel using custom log formats.
Reference:
https://docs.microsoft.com/en-us/azure/azure-monitor/agents/agents-overview https://docs.microsoft.com/en-us/azure/sentinel/connect-custom-logs?tabs=DCG https://docs.microsoft.com/en-us/azure/sentinel/roles
BC
A: You can collect data in custom log formats to Microsoft Sentinel with the Log Analytics agent.
Note: You can use the Log Analytics agent to collect data in text files of nonstandard formats from both Windows and Linux computers. Once collected, you can either parse the data into individual fields in your queries or extract the data during collection to individual fields.
You can connect your data sources to Microsoft Sentinel using custom log formats.
C: Microsoft Sentinel uses Azure role-based access control (Azure RBAC) to provide built-in roles that can be assigned to users, groups, and services in Azure.
Use Azure RBAC to create and assign roles within your security operations team to grant appropriate access to Microsoft Sentinel. The different roles give you fine-grained control over what Microsoft Sentinel users can see and do. Azure roles can be assigned in the Microsoft Sentinel workspace directly (see note below), or in a subscription or resource group that the workspace belongs to, which Microsoft Sentinel inherits.
Incorrect:
A: You can collect data in custom log formats to Microsoft Sentinel with the Log Analytics agent.
Note: You can use the Log Analytics agent to collect data in text files of nonstandard formats from both Windows and Linux computers. Once collected, you can either parse the data into individual fields in your queries or extract the data during collection to individual fields.
You can connect your data sources to Microsoft Sentinel using custom log formats.
Reference:
https://docs.microsoft.com/en-us/azure/azure-monitor/agents/agents-overview https://docs.microsoft.com/en-us/azure/sentinel/connect-custom-logs?tabs=DCG https://docs.microsoft.com/en-us/azure/sentinel/roles
send
light_mode
delete
Question #17
Your company is developing a serverless application in Azure that will have the architecture shown in the following exhibit.
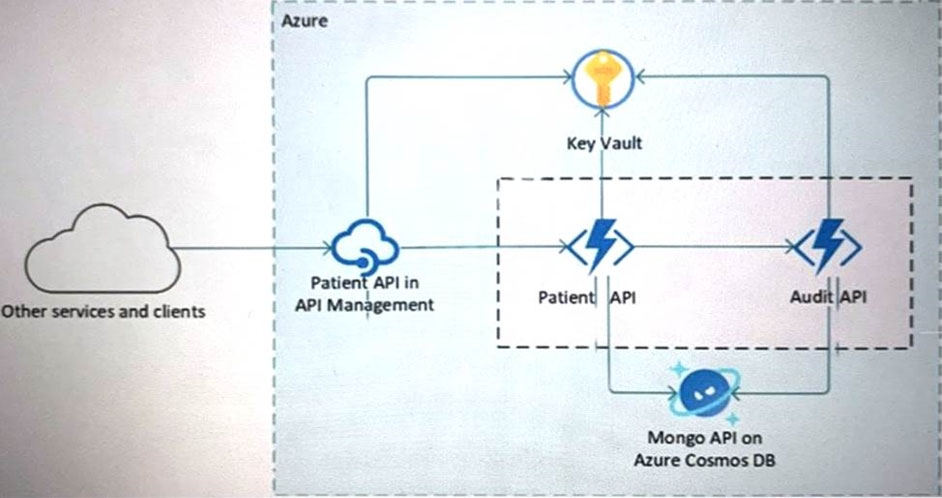
You need to recommend a solution to isolate the compute components on an Azure virtual network.
What should you include in the recommendation?

You need to recommend a solution to isolate the compute components on an Azure virtual network.
What should you include in the recommendation?
- AAzure Active Directory (Azure AD) enterprise applications
- Ban Azure App Service Environment (ASE)Most Voted
- CAzure service endpoints
- Dan Azure Active Directory (Azure AD) application proxy
Correct Answer:
B
The Azure App Service Environment v2 is an Azure App Service feature that provides a fully isolated and dedicated environment for securely running App Service apps at high scale. This capability can host your:
Windows web apps -
Linux web apps -
Docker containers -
Mobile apps -
Functions -
App Service environments (ASEs) are appropriate for application workloads that require:
Very high scale.
Isolation and secure network access.
High memory utilization.
Customers can create multiple ASEs within a single Azure region or across multiple Azure regions. This flexibility makes ASEs ideal for horizontally scaling stateless application tiers in support of high requests per second (RPS) workloads.
Reference:
https://docs.microsoft.com/en-us/azure/app-service/environment/intro
B
The Azure App Service Environment v2 is an Azure App Service feature that provides a fully isolated and dedicated environment for securely running App Service apps at high scale. This capability can host your:
Windows web apps -
Linux web apps -
Docker containers -
Mobile apps -
Functions -
App Service environments (ASEs) are appropriate for application workloads that require:
Very high scale.
Isolation and secure network access.
High memory utilization.
Customers can create multiple ASEs within a single Azure region or across multiple Azure regions. This flexibility makes ASEs ideal for horizontally scaling stateless application tiers in support of high requests per second (RPS) workloads.
Reference:
https://docs.microsoft.com/en-us/azure/app-service/environment/intro
send
light_mode
delete
Question #18
You are evaluating an Azure environment for compliance.
You need to design an Azure Policy implementation that can be used to evaluate compliance without changing any resources.
Which effect should you use in Azure Policy?
You need to design an Azure Policy implementation that can be used to evaluate compliance without changing any resources.
Which effect should you use in Azure Policy?
- ADenyMost Voted
- BModify
- CAppend
- DDisabled
Correct Answer:
D
This effect is useful for testing situations or for when the policy definition has parameterized the effect. This flexibility makes it possible to disable a single assignment instead of disabling all of that policy's assignments.
An alternative to the Disabled effect is enforcementMode, which is set on the policy assignment. When enforcementMode is Disabled, resources are still evaluated.
Incorrect:
Not A: Deny is used to prevent a resource request that doesn't match defined standards through a policy definition and fails the request.
Not B: Modify evaluates before the request gets processed by a Resource Provider during the creation or updating of a resource. The Modify operations are applied to the request content when the if condition of the policy rule is met. Each Modify operation can specify a condition that determines when it's applied.
Operations with conditions that are evaluated to false are skipped.
Not C: Append is used to add additional fields to the requested resource during creation or update.
Reference:
https://docs.microsoft.com/en-us/azure/governance/policy/concepts/effects
D
This effect is useful for testing situations or for when the policy definition has parameterized the effect. This flexibility makes it possible to disable a single assignment instead of disabling all of that policy's assignments.
An alternative to the Disabled effect is enforcementMode, which is set on the policy assignment. When enforcementMode is Disabled, resources are still evaluated.
Incorrect:
Not A: Deny is used to prevent a resource request that doesn't match defined standards through a policy definition and fails the request.
Not B: Modify evaluates before the request gets processed by a Resource Provider during the creation or updating of a resource. The Modify operations are applied to the request content when the if condition of the policy rule is met. Each Modify operation can specify a condition that determines when it's applied.
Operations with conditions that are evaluated to false are skipped.
Not C: Append is used to add additional fields to the requested resource during creation or update.
Reference:
https://docs.microsoft.com/en-us/azure/governance/policy/concepts/effects
send
light_mode
delete
Question #19
You have an Azure subscription that has Microsoft Defender for Cloud enabled.
You are evaluating the Azure Security Benchmark V3 report as shown in the following exhibit.
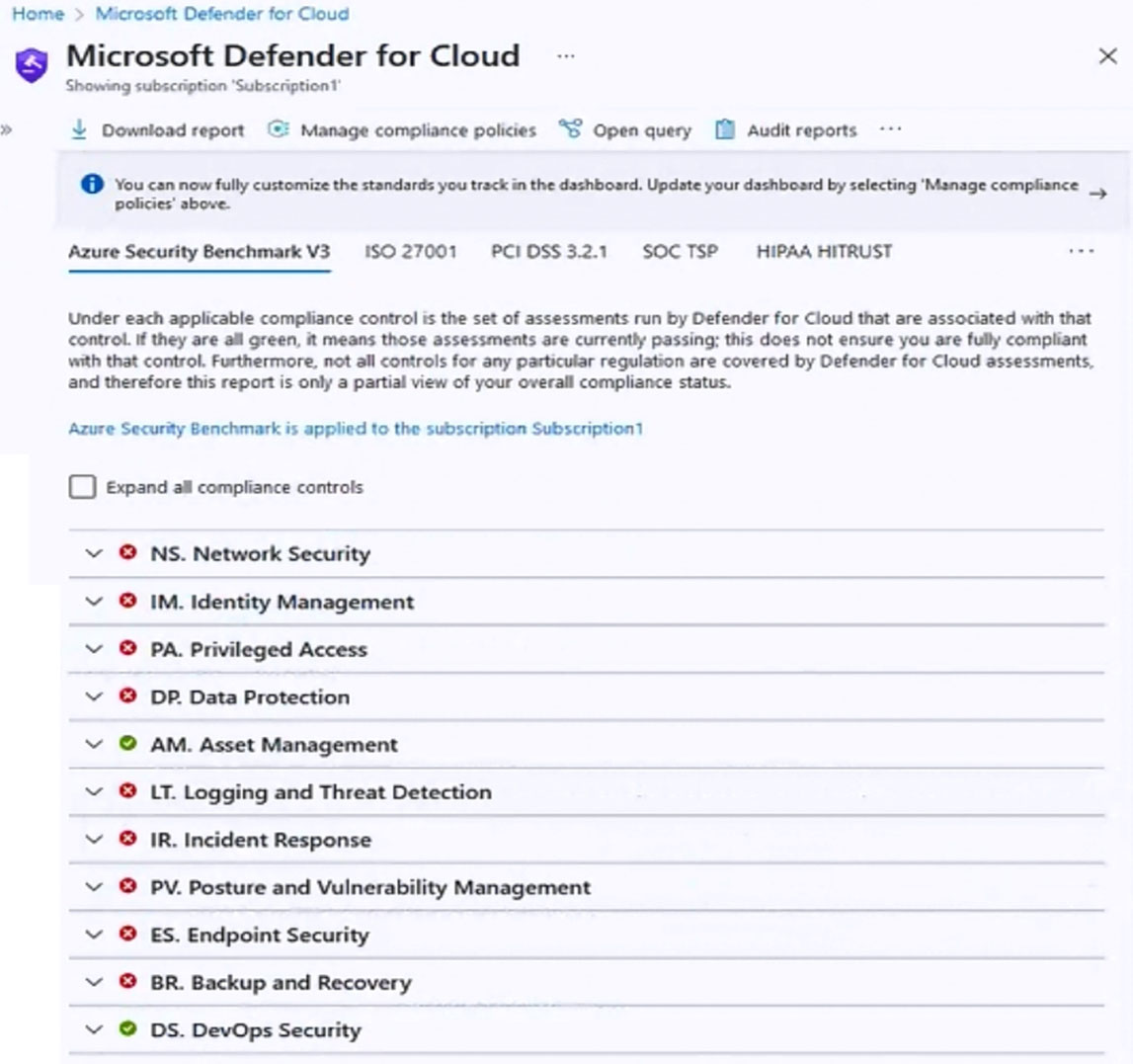
You need to verify whether Microsoft Defender for servers is installed on all the virtual machines that run Windows.
Which compliance control should you evaluate?
You are evaluating the Azure Security Benchmark V3 report as shown in the following exhibit.

You need to verify whether Microsoft Defender for servers is installed on all the virtual machines that run Windows.
Which compliance control should you evaluate?
- AAsset Management
- BPosture and Vulnerability Management
- CData Protection
- DEndpoint SecurityMost Voted
- EIncident Response
Correct Answer:
D
Microsoft Defender for servers compliance control installed on Windows
Defender for clout "Endpoint Security" azure security benchmark v3
Endpoint Security covers controls in endpoint detection and response, including use of endpoint detection and response (EDR) and anti-malware service for endpoints in Azure environments.
Security Principle: Enable Endpoint Detection and Response (EDR) capabilities for VMs and integrate with SIEM and security operations processes.
Azure Guidance: Azure Defender for servers (with Microsoft Defender for Endpoint integrated) provides EDR capability to prevent, detect, investigate, and respond to advanced threats.
Use Microsoft Defender for Cloud to deploy Azure Defender for servers for your endpoint and integrate the alerts to your SIEM solution such as Azure Sentinel.
Incorrect:
Not A: Asset Management covers controls to ensure security visibility and governance over Azure resources, including recommendations on permissions for security personnel, security access to asset inventory, and managing approvals for services and resources (inventory, track, and correct).
Not B: Posture and Vulnerability Management focuses on controls for assessing and improving Azure security posture, including vulnerability scanning, penetration testing and remediation, as well as security configuration tracking, reporting, and correction in Azure resources.
Not C: Data Protection covers control of data protection at rest, in transit, and via authorized access mechanisms, including discover, classify, protect, and monitor sensitive data assets using access control, encryption, key and certificate management in Azure.
Not E: Incident Response covers controls in incident response life cycle - preparation, detection and analysis, containment, and post-incident activities, including using Azure services such as Microsoft Defender for Cloud and Sentinel to automate the incident response process.
Reference:
https://docs.microsoft.com/en-us/security/benchmark/azure/security-controls-v3-endpoint-security
D
Microsoft Defender for servers compliance control installed on Windows
Defender for clout "Endpoint Security" azure security benchmark v3
Endpoint Security covers controls in endpoint detection and response, including use of endpoint detection and response (EDR) and anti-malware service for endpoints in Azure environments.
Security Principle: Enable Endpoint Detection and Response (EDR) capabilities for VMs and integrate with SIEM and security operations processes.
Azure Guidance: Azure Defender for servers (with Microsoft Defender for Endpoint integrated) provides EDR capability to prevent, detect, investigate, and respond to advanced threats.
Use Microsoft Defender for Cloud to deploy Azure Defender for servers for your endpoint and integrate the alerts to your SIEM solution such as Azure Sentinel.
Incorrect:
Not A: Asset Management covers controls to ensure security visibility and governance over Azure resources, including recommendations on permissions for security personnel, security access to asset inventory, and managing approvals for services and resources (inventory, track, and correct).
Not B: Posture and Vulnerability Management focuses on controls for assessing and improving Azure security posture, including vulnerability scanning, penetration testing and remediation, as well as security configuration tracking, reporting, and correction in Azure resources.
Not C: Data Protection covers control of data protection at rest, in transit, and via authorized access mechanisms, including discover, classify, protect, and monitor sensitive data assets using access control, encryption, key and certificate management in Azure.
Not E: Incident Response covers controls in incident response life cycle - preparation, detection and analysis, containment, and post-incident activities, including using Azure services such as Microsoft Defender for Cloud and Sentinel to automate the incident response process.
Reference:
https://docs.microsoft.com/en-us/security/benchmark/azure/security-controls-v3-endpoint-security
send
light_mode
delete
Question #20
HOTSPOT -
You have a Microsoft 365 E5 subscription and an Azure subscription.
You need to evaluate the existing environment to increase the overall security posture for the following components:
✑ Windows 11 devices managed by Microsoft Intune
✑ Azure Storage accounts
✑ Azure virtual machines
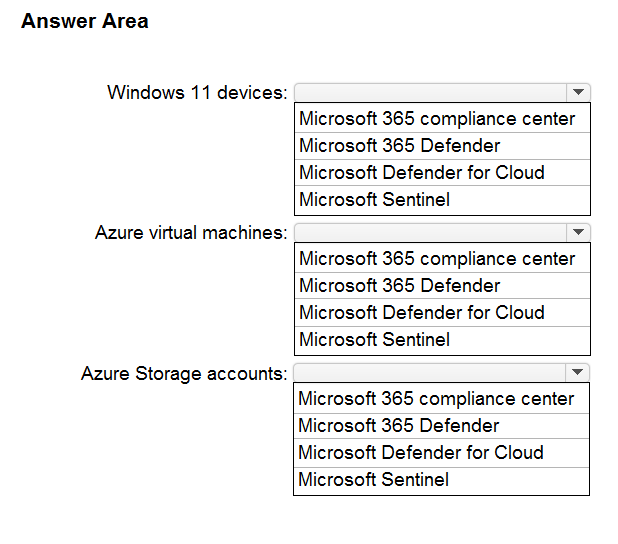
What should you use to evaluate the components? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
You have a Microsoft 365 E5 subscription and an Azure subscription.
You need to evaluate the existing environment to increase the overall security posture for the following components:
✑ Windows 11 devices managed by Microsoft Intune
✑ Azure Storage accounts
✑ Azure virtual machines
What should you use to evaluate the components? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:
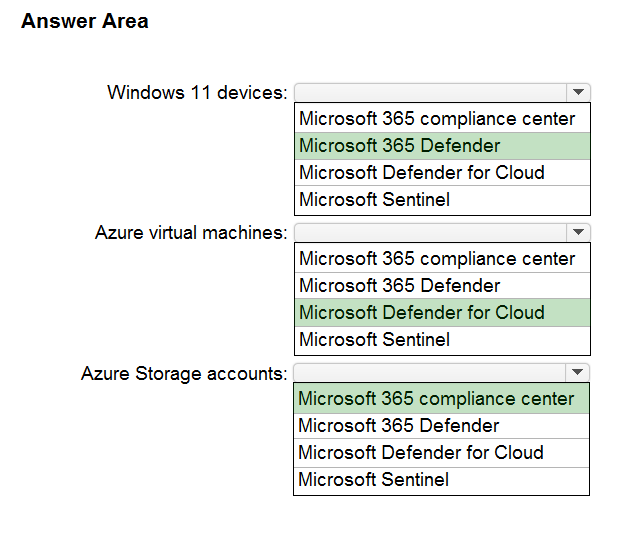
Box 1: Microsoft 365 Defender -
The Microsoft 365 Defender portal emphasizes quick access to information, simpler layouts, and bringing related information together for easier use. It includes
Microsoft Defender for Endpoint.
Microsoft Defender for Endpoint is an enterprise endpoint security platform designed to help enterprise networks prevent, detect, investigate, and respond to advanced threats.
You can integrate Microsoft Defender for Endpoint with Microsoft Intune as a Mobile Threat Defense solution. Integration can help you prevent security breaches and limit the impact of breaches within an organization.
Microsoft Defender for Endpoint works with devices that run:
Android -
iOS/iPadOS
Windows 10 -
Windows 11 -
Box 2: Microsoft Defender for Cloud
Microsoft Defender for Cloud currently protects Azure Blobs, Azure Files and Azure Data Lake Storage Gen2 resources. Microsoft Defender for SQL on Azure price applies to SQL servers on Azure SQL Database, Azure SQL Managed Instance and Azure Virtual Machines.
Box 3: Microsoft 365 Compliance Center
Azure Storage Security Assessment: Microsoft 365 Compliance Center monitors and recommends encryption for Azure Storage, and within a few clicks customers can enable built-in encryption for their Azure Storage Accounts.
Note: Microsoft 365 compliance is now called Microsoft Purview and the solutions within the compliance area have been rebranded.
Microsoft Purview can be setup to manage policies for one or more Azure Storage accounts.
Reference:
https://docs.microsoft.com/en-us/azure/purview/tutorial-data-owner-policies-storage https://docs.microsoft.com/en-us/microsoft-365/security/defender/microsoft-365-defender
?
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/microsoft-defender-endpoint https://azure.microsoft.com/en-gb/pricing/details/defender-for-cloud/

Box 1: Microsoft 365 Defender -
The Microsoft 365 Defender portal emphasizes quick access to information, simpler layouts, and bringing related information together for easier use. It includes
Microsoft Defender for Endpoint.
Microsoft Defender for Endpoint is an enterprise endpoint security platform designed to help enterprise networks prevent, detect, investigate, and respond to advanced threats.
You can integrate Microsoft Defender for Endpoint with Microsoft Intune as a Mobile Threat Defense solution. Integration can help you prevent security breaches and limit the impact of breaches within an organization.
Microsoft Defender for Endpoint works with devices that run:
Android -
iOS/iPadOS
Windows 10 -
Windows 11 -
Box 2: Microsoft Defender for Cloud
Microsoft Defender for Cloud currently protects Azure Blobs, Azure Files and Azure Data Lake Storage Gen2 resources. Microsoft Defender for SQL on Azure price applies to SQL servers on Azure SQL Database, Azure SQL Managed Instance and Azure Virtual Machines.
Box 3: Microsoft 365 Compliance Center
Azure Storage Security Assessment: Microsoft 365 Compliance Center monitors and recommends encryption for Azure Storage, and within a few clicks customers can enable built-in encryption for their Azure Storage Accounts.
Note: Microsoft 365 compliance is now called Microsoft Purview and the solutions within the compliance area have been rebranded.
Microsoft Purview can be setup to manage policies for one or more Azure Storage accounts.
Reference:
https://docs.microsoft.com/en-us/azure/purview/tutorial-data-owner-policies-storage https://docs.microsoft.com/en-us/microsoft-365/security/defender/microsoft-365-defender
?
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/microsoft-defender-endpoint https://azure.microsoft.com/en-gb/pricing/details/defender-for-cloud/
send
light_mode
delete
All Pages
