Microsoft MS-500 Exam Practice Questions (P. 4)
- Full Access (352 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #31
You have a Microsoft 365 subscription linked to an Azure Active Directory (Azure AD) tenant that contains a user named User1.
You have a Data Subject Request (DSR) case named Case1.
You need to allow User1 to export the results of Case1. The solution must use the principle of least privilege.
Which role should you assign to User1 for Case1?
You have a Data Subject Request (DSR) case named Case1.
You need to allow User1 to export the results of Case1. The solution must use the principle of least privilege.
Which role should you assign to User1 for Case1?
- AeDiscovery ManagerMost Voted
- BSecurity Operator
- CeDiscovery Administrator
- DGlobal Reader
Correct Answer:
A
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/manage-gdpr-data-subject-requests-with-the-dsr-case-tool?view=o365-worldwide#step-1-assign- ediscovery-permissions-to-potential-case-members
A
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/manage-gdpr-data-subject-requests-with-the-dsr-case-tool?view=o365-worldwide#step-1-assign- ediscovery-permissions-to-potential-case-members
send
light_mode
delete
Question #32
HOTSPOT -
You have a Microsoft 365 subscription that contains the users shown in the following table.
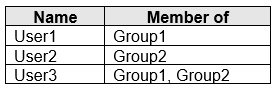
You create and enforce an Azure Active Directory (Azure AD) Identity Protection user risk policy that has the following settings:
✑ Assignments: Include Group1, Exclude Group2
✑ User-risk: User risk level of Medium and above
✑ Access: Allow access, Require password change
The users attempt to sign in. The risk level for each user is shown in the following table.
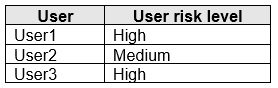
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
You have a Microsoft 365 subscription that contains the users shown in the following table.

You create and enforce an Azure Active Directory (Azure AD) Identity Protection user risk policy that has the following settings:
✑ Assignments: Include Group1, Exclude Group2
✑ User-risk: User risk level of Medium and above
✑ Access: Allow access, Require password change
The users attempt to sign in. The risk level for each user is shown in the following table.

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:
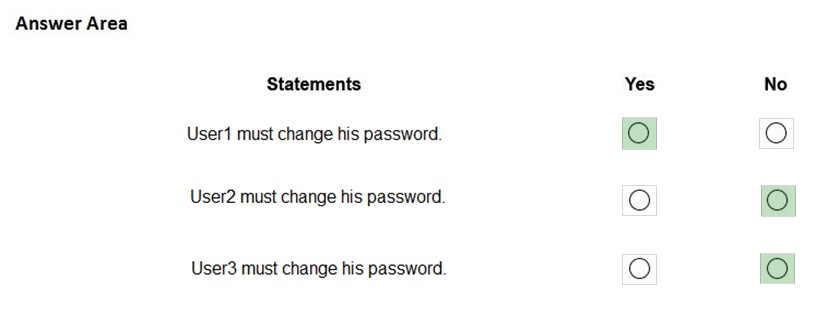
Box 1: Yes.
User1 is in Group1 which the policy applies to.
Box 2: No -
User2 is in Group2 which is excluded from the policy.
Box 3: No -
User3 is in Group1 which is included in the policy and Group2 which is excluded from the policy. In this case, the exclusion wins so the policy does not apply to
User3.

Box 1: Yes.
User1 is in Group1 which the policy applies to.
Box 2: No -
User2 is in Group2 which is excluded from the policy.
Box 3: No -
User3 is in Group1 which is included in the policy and Group2 which is excluded from the policy. In this case, the exclusion wins so the policy does not apply to
User3.
send
light_mode
delete
Question #33
You configure several Advanced Threat Protection (ATP) policies in a Microsoft 365 subscription.
You need to allow a user named User1 to view ATP reports from the Threat management dashboard.
Which role provides User1 with the required role permissions?
You need to allow a user named User1 to view ATP reports from the Threat management dashboard.
Which role provides User1 with the required role permissions?
- ACompliance administrator
- BSecurity readerMost Voted
- CMessage center reader
- DReports reader
Correct Answer:
B
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/view-reports-for-atp?view=o365-worldwide#what-permissions-are-needed-to-view-the- atp-reports
B
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/view-reports-for-atp?view=o365-worldwide#what-permissions-are-needed-to-view-the- atp-reports
send
light_mode
delete
Question #34
HOTSPOT -
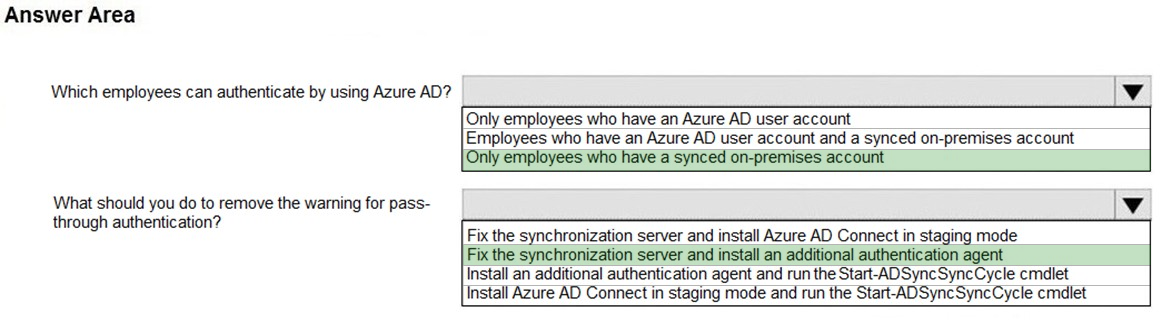
Your network contains an on-premises Active Directory domain that syncs to Azure Active Directory (Azure AD) as shown in the following exhibit.
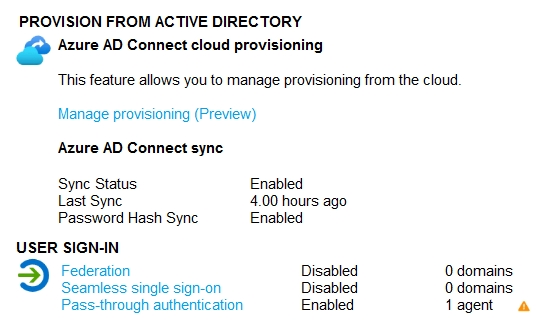
The synchronization schedule is configured as shown in the following exhibit.
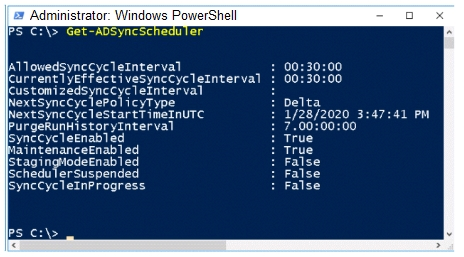
Use the drop-down menus to select the answer choice that answers each question based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
Hot Area:
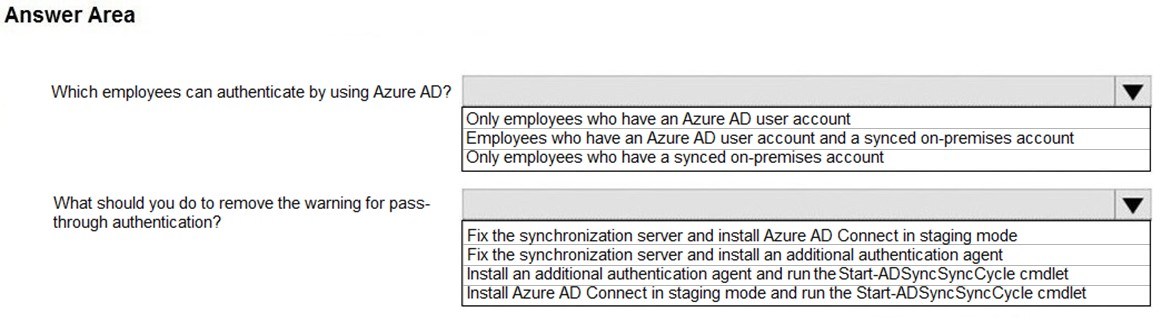
Your network contains an on-premises Active Directory domain that syncs to Azure Active Directory (Azure AD) as shown in the following exhibit.

The synchronization schedule is configured as shown in the following exhibit.

Use the drop-down menus to select the answer choice that answers each question based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
Hot Area:

send
light_mode
delete
Question #35
HOTSPOT -
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
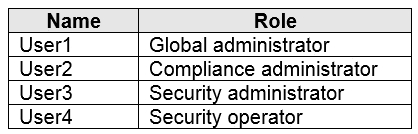
You plan to implement Azure Active Directory (Azure AD) Identity Protection.
You need to identify which users can perform the following actions:
✑ Configure a user risk policy.
✑ View the risky users report.
Which users should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
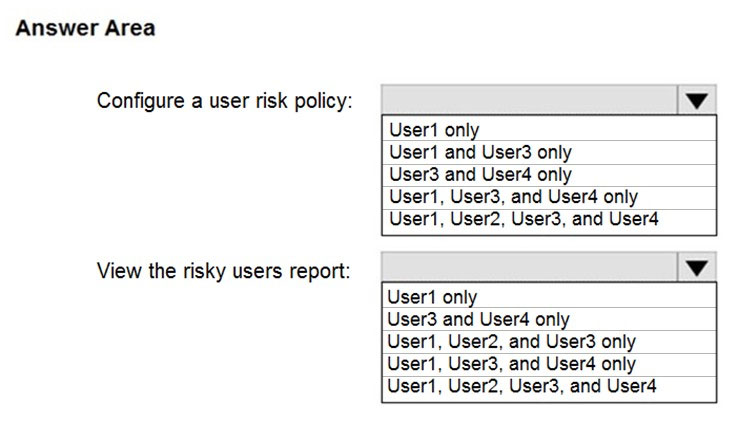
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.

You plan to implement Azure Active Directory (Azure AD) Identity Protection.
You need to identify which users can perform the following actions:
✑ Configure a user risk policy.
✑ View the risky users report.
Which users should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:
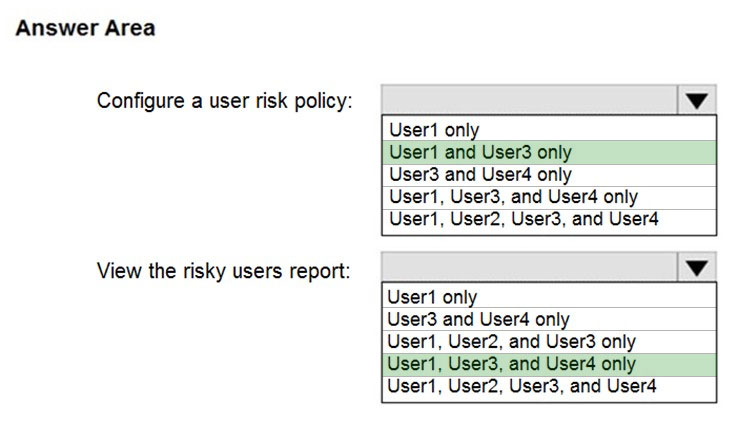
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/overview-identity-protection

Reference:
https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/overview-identity-protection
send
light_mode
delete
Question #36
HOTSPOT -
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.

You add internal as a blocked word in the group naming policy for contoso.com.
You add Contoso- as prefix in the group naming policy for contoso.com.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
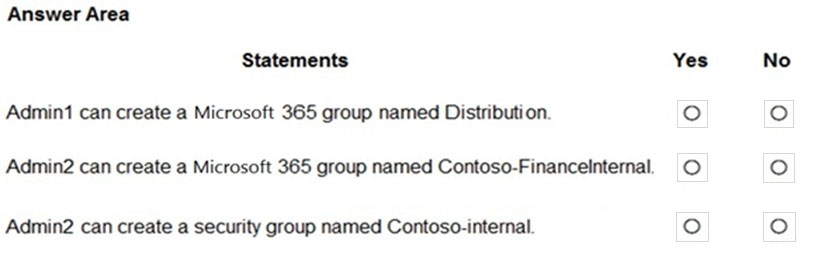
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.

You add internal as a blocked word in the group naming policy for contoso.com.
You add Contoso- as prefix in the group naming policy for contoso.com.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:
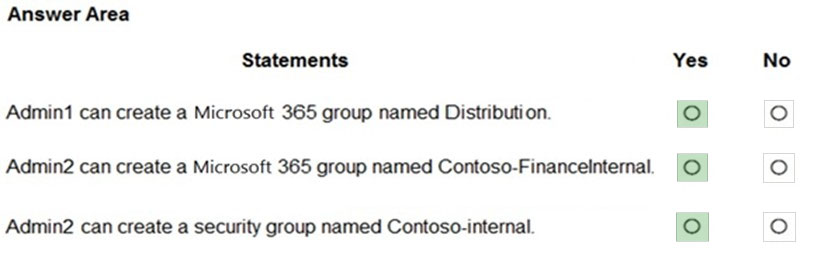
User Admin and Global Admin are exempt from group password policies.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/solutions/groups-naming-policy?view=o365-worldwide

User Admin and Global Admin are exempt from group password policies.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/solutions/groups-naming-policy?view=o365-worldwide
send
light_mode
delete
Question #37
DRAG DROP -
You have a Microsoft 365 tenant.
User attributes are synced from your company's human resources (HR) system to Azure Active Directory (Azure AD).
The company has four departments that each has its own Microsoft SharePoint Online site. Each site must be accessed only by the users from its respective department.
You are designing an access management solution that has the following requirements:
✑ Users must be added automatically to the security group of their department.
✑ All security group owners must verify once quarterly that only the users in their department belong to their group.
Which components should you recommend to meet the requirements? To answer, drag the appropriate components to the correct requirements. Each component may only be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:
You have a Microsoft 365 tenant.
User attributes are synced from your company's human resources (HR) system to Azure Active Directory (Azure AD).
The company has four departments that each has its own Microsoft SharePoint Online site. Each site must be accessed only by the users from its respective department.
You are designing an access management solution that has the following requirements:
✑ Users must be added automatically to the security group of their department.
✑ All security group owners must verify once quarterly that only the users in their department belong to their group.
Which components should you recommend to meet the requirements? To answer, drag the appropriate components to the correct requirements. Each component may only be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:

Correct Answer:
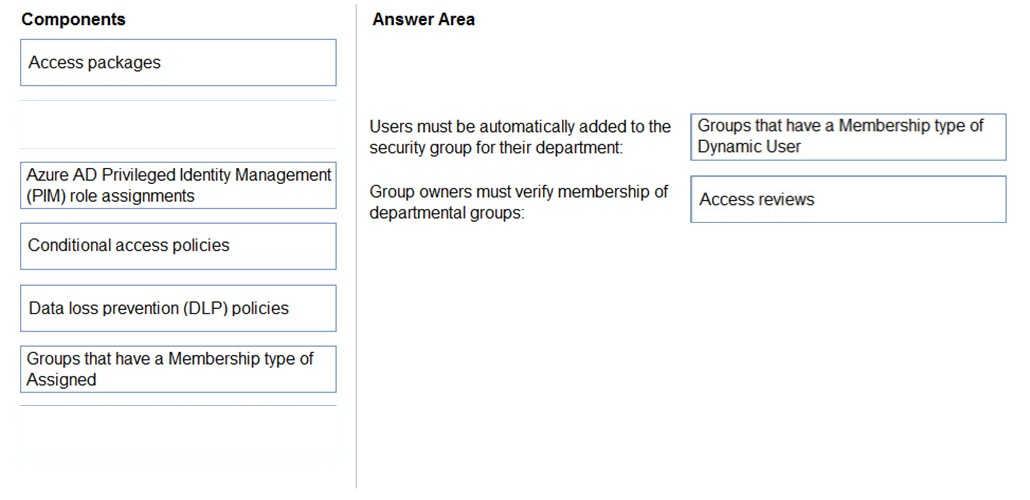
Reference:
https://cloudbuild.co.uk/tag/create-a-dynamic-security-group-in-azure-ad/ https://docs.microsoft.com/en-us/azure/active-directory/governance/access-reviews-overview

Reference:
https://cloudbuild.co.uk/tag/create-a-dynamic-security-group-in-azure-ad/ https://docs.microsoft.com/en-us/azure/active-directory/governance/access-reviews-overview
send
light_mode
delete
Question #38
HOTSPOT -
You have a Microsoft 365 E5 subscription that uses Microsoft Endpoint Manager.
The Compliance policy settings are configured as shown in the following exhibit.
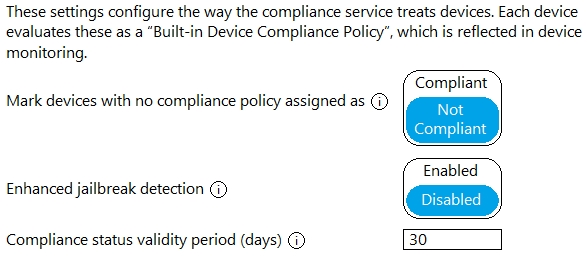
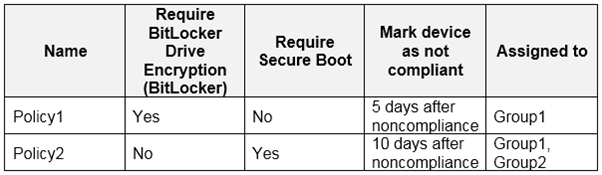
On February 25, 2020, you create the device compliance policies shown in the following table.
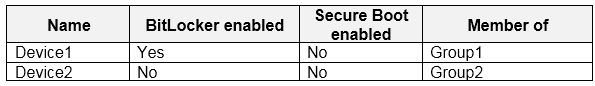
On March 1. 2020, users enroll Windows 10 devices in Microsoft Endpoint Manager as shown in the following table
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
You have a Microsoft 365 E5 subscription that uses Microsoft Endpoint Manager.
The Compliance policy settings are configured as shown in the following exhibit.

On February 25, 2020, you create the device compliance policies shown in the following table.

On March 1. 2020, users enroll Windows 10 devices in Microsoft Endpoint Manager as shown in the following table

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:
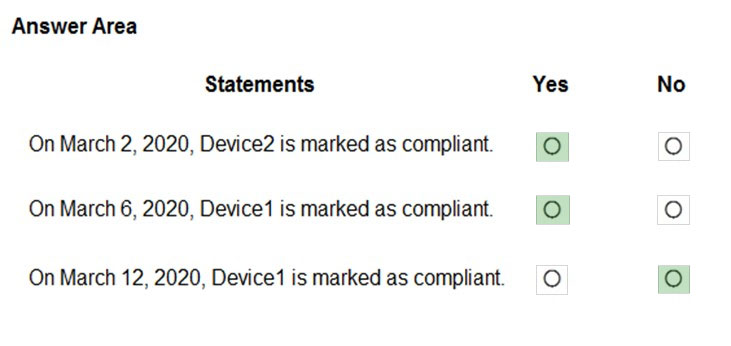
Box 1: Yes -
Device2 is in Group2 so Policy2 applies.
Device2 is not compliant with Policy2. However, the device won't be marked as non-compliant until 10 days after the device was enrolled.
Box 2: Yes -
Device1 is in Group1 and Group2 so both Policy1 and Policy2 apply.
Device1 is compliant with Policy1 but non-compliant with Policy2. However, the device won't be marked as non-compliant until 10 days after the device was enrolled.
Box 3: No -
Device1 is in Group1 and Group2 so both Policy1 and Policy2 apply.
Device1 is compliant with Policy1 but non-compliant with Policy2. th
March 12 -
is more than 10 days after the device was enrolled so it will now be marked as non-compliant by Policy2.

Box 1: Yes -
Device2 is in Group2 so Policy2 applies.
Device2 is not compliant with Policy2. However, the device won't be marked as non-compliant until 10 days after the device was enrolled.
Box 2: Yes -
Device1 is in Group1 and Group2 so both Policy1 and Policy2 apply.
Device1 is compliant with Policy1 but non-compliant with Policy2. However, the device won't be marked as non-compliant until 10 days after the device was enrolled.
Box 3: No -
Device1 is in Group1 and Group2 so both Policy1 and Policy2 apply.
Device1 is compliant with Policy1 but non-compliant with Policy2. th
March 12 -
is more than 10 days after the device was enrolled so it will now be marked as non-compliant by Policy2.
send
light_mode
delete
Question #39
You have a Microsoft 365 tenant.
From the Azure Active Directory admin center, you review the Risky sign-ins report as shown in the following exhibit.
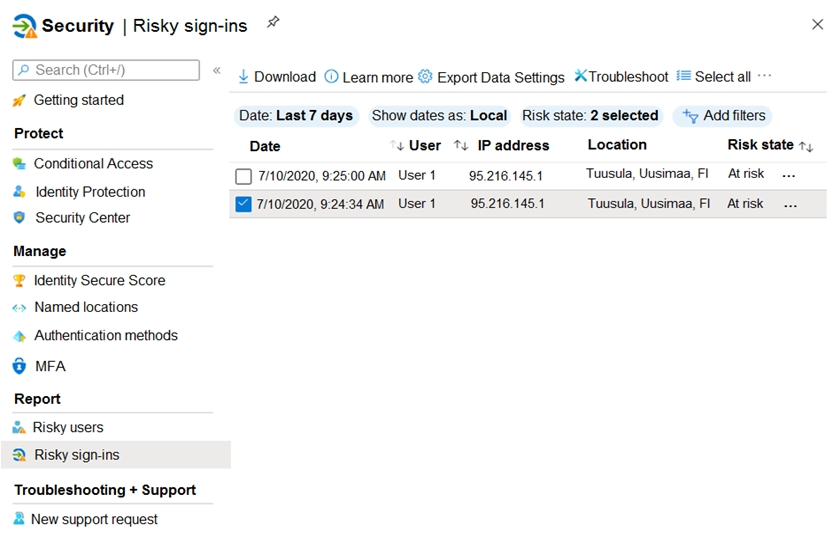
You need to ensure that you can see additional details including the risk level and the risk detection type.
What should you do?
From the Azure Active Directory admin center, you review the Risky sign-ins report as shown in the following exhibit.

You need to ensure that you can see additional details including the risk level and the risk detection type.
What should you do?
- APurchase Microsoft 365 Enterprise E5 licenses.Most Voted
- BActivate an instance of Microsoft Defender for Identity.
- CConfigure Diagnostic settings in Azure Active Directory (Azure AD).
- DDeploy Azure Sentinel and add a Microsoft Office 365 connector.
Correct Answer:
A
A
send
light_mode
delete
Question #40
You have a Microsoft 365 E5 subscription.
You plan to create a conditional access policy named Policy1.
You need to be able to use the sign-in risk level condition in Policy1.
What should you do first?
You plan to create a conditional access policy named Policy1.
You need to be able to use the sign-in risk level condition in Policy1.
What should you do first?
- AConnect Microsoft Endpoint Manager and Microsoft Defender for Endpoint.
- BFrom the Azure Active Directory admin center, configure the Diagnostics settings.
- CFrom the Endpoint Management admin center, create a device compliance policy.
- DOnboard Azure Active Directory (Azure AD) Identity Protection.
Correct Answer:
D
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/howto-conditional-access-policy-risk
D
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/howto-conditional-access-policy-risk
send
light_mode
delete
All Pages