Microsoft 70-745 Exam Practice Questions (P. 3)
- Full Access (73 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #11
You manage Microsoft System Center Virtual Machine Manager (SCVMM).
You need to block specific packets on the virtual switch.
Which two types of virtual switch extensions can you use? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
You need to block specific packets on the virtual switch.
Which two types of virtual switch extensions can you use? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- Acapturing extensions
- Bforwarding extensions
- Cmonitoring extensions
- Dfiltering extensions
Correct Answer:
BD
A Hyper-V extensible switch filtering extension can inspect, modify, and insert packets into the extensible switch data path. Based on extensible switch port and switch policy settings, the extension can drop a packet or exclude its delivery to one or more destination ports.
A forwarding extension has the same capabilities as a filtering extension, but is responsible for performing the core packet forwarding and filtering tasks of the extensible switch.
References:
https://docs.microsoft.com/en-us/windows-hardware/drivers/network/overview-of-the-hyper-v-extensible-switch
BD
A Hyper-V extensible switch filtering extension can inspect, modify, and insert packets into the extensible switch data path. Based on extensible switch port and switch policy settings, the extension can drop a packet or exclude its delivery to one or more destination ports.
A forwarding extension has the same capabilities as a filtering extension, but is responsible for performing the core packet forwarding and filtering tasks of the extensible switch.
References:
https://docs.microsoft.com/en-us/windows-hardware/drivers/network/overview-of-the-hyper-v-extensible-switch
send
light_mode
delete
Question #12
You manage a Microsoft Hyper-V host server that has several high-speed physical network adapters.
You need to attach a physical network adapter directly to a virtual machine (VM).
What should you do first?
You need to attach a physical network adapter directly to a virtual machine (VM).
What should you do first?
- AAssign the adapter to the VM.
- BDisable the adapter on the Hyper-V host.
- CInstall the device driver on the Hyper-V host.
- DInstall the device driver on the VM.
Correct Answer:
B
B
send
light_mode
delete
Question #13
HOTSPOT -
You deploy Microsoft System Center Virtual Machine Manager (SCVMM) and System Center Configuration Manager in an Active Directory Domain Services (AD
DS) domain.
You must deploy a Software Defined Networking (SDN) network controller.
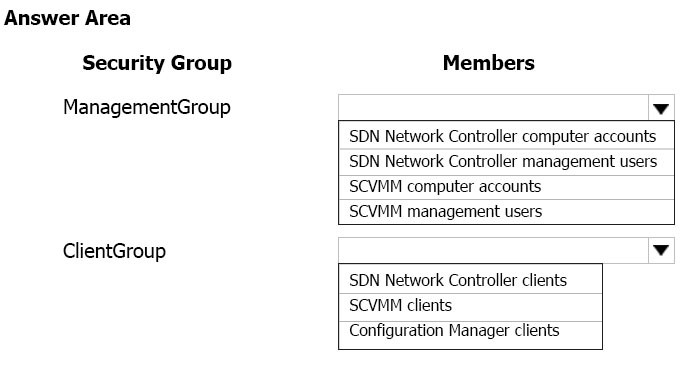
You need to create the required AD DS security groups for management users and network controller clients.
Which members should you add to each group? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
You deploy Microsoft System Center Virtual Machine Manager (SCVMM) and System Center Configuration Manager in an Active Directory Domain Services (AD
DS) domain.
You must deploy a Software Defined Networking (SDN) network controller.
You need to create the required AD DS security groups for management users and network controller clients.
Which members should you add to each group? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:
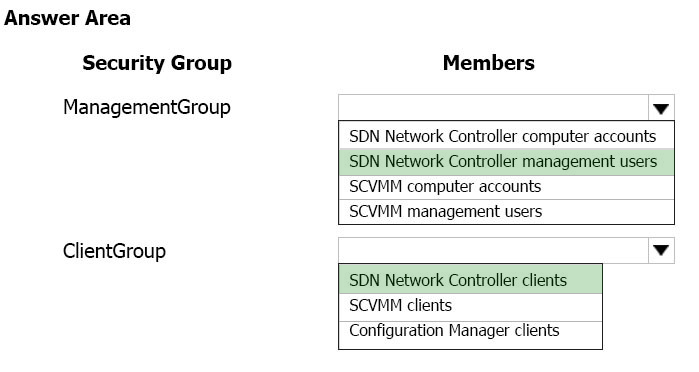
1. Create security groups for network controller management and clients.
✑ In Active Directory Users and Computers, create a security group for network controller management.
✑ In the group, add all the users who have permission to configure the network controller. For example, create a group named Network Controller Admins.
✑ All of the users that you add to this group must also be members of the Domain Users group in Active Directory.
✑ The group for network controller management should be a domain local group. Members of this group will be able to create, delete, and update the deployed network controller configuration.
✑ Create at least one user account that is a member of this group and have access to its credentials. After the network controller is deployed, VMM can be configured to use the user account credentials to establish communication with the network controller.
1. Create another security group for network controller clients
✑ Add users with permission to configure and manage networks using network controller. For example, create a group named Network Controller Users.
✑ All of the users that you add to the new group must also be members of the Domain Users group in Active Directory.
✑ All Network Controller configuration and management is performed using Representational State Transfer (DNS).
The group should be a Domain Local group. After the network controller is deployed, any members of this group will have permissions to communicate with the
 network controller via the REST based interface.
network controller via the REST based interface.
✑ Create at least one user account that is a member of this group. After the network controller is deployed, VMM can be configured to use the user account credentials to establish communication with the network controller.
References:
https://docs.microsoft.com/en-us/system-center/vmm/sdn-controller?view=sc-vmm-1801

1. Create security groups for network controller management and clients.
✑ In Active Directory Users and Computers, create a security group for network controller management.
✑ In the group, add all the users who have permission to configure the network controller. For example, create a group named Network Controller Admins.
✑ All of the users that you add to this group must also be members of the Domain Users group in Active Directory.
✑ The group for network controller management should be a domain local group. Members of this group will be able to create, delete, and update the deployed network controller configuration.
✑ Create at least one user account that is a member of this group and have access to its credentials. After the network controller is deployed, VMM can be configured to use the user account credentials to establish communication with the network controller.
1. Create another security group for network controller clients
✑ Add users with permission to configure and manage networks using network controller. For example, create a group named Network Controller Users.
✑ All of the users that you add to the new group must also be members of the Domain Users group in Active Directory.
✑ All Network Controller configuration and management is performed using Representational State Transfer (DNS).
The group should be a Domain Local group. After the network controller is deployed, any members of this group will have permissions to communicate with the
 network controller via the REST based interface.
network controller via the REST based interface.✑ Create at least one user account that is a member of this group. After the network controller is deployed, VMM can be configured to use the user account credentials to establish communication with the network controller.
References:
https://docs.microsoft.com/en-us/system-center/vmm/sdn-controller?view=sc-vmm-1801
send
light_mode
delete
Question #14
DRAG DROP -
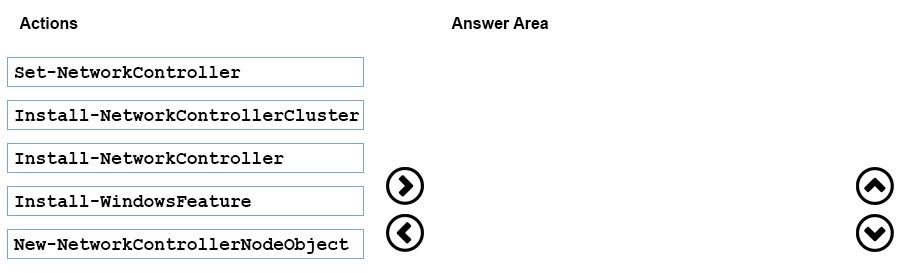
You plan to deploy a Windows Server Gateway (WSG). The gateway will be managed by Network Controller.
You need to install and configure a Network Controller cluster.
Which four Windows PowerShell cmdlets should you run in sequence? To answer, move the appropriate Windows PowerShell cmdlets from the list of actions to the answer area and arrange them in the correct order.
Select and Place:
You plan to deploy a Windows Server Gateway (WSG). The gateway will be managed by Network Controller.
You need to install and configure a Network Controller cluster.
Which four Windows PowerShell cmdlets should you run in sequence? To answer, move the appropriate Windows PowerShell cmdlets from the list of actions to the answer area and arrange them in the correct order.
Select and Place:

Correct Answer:
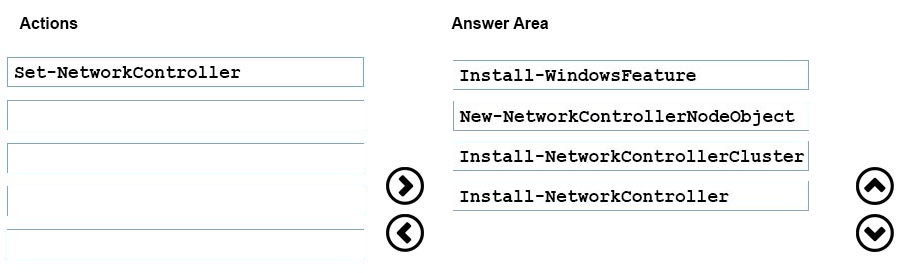
1. Install the Network Controller server role
Install-WindowsFeature -Name NetworkController ""IncludeManagementTools
2. Configure the Network Controller cluster
✑ Create a node object
New-NetworkControllerNodeObject ""Name <string> ""Server <String> ""FaultDomain <string> ""RestInterface <string>
[-NodeCertificate <X509Certificate2>]
1. Configure the cluster
Install-NetworkControllerCluster ""Node <NetworkControllerNode[]> ""ClusterAuthentication <ClusterAuthentication> [""ManagementSecurityGroup <string>]
[""DiagnosticLogLocation <string>][""LogLocationCredential <PSCredential>]
[""CredentialEncryptionCertificate <X509Certificate2>][""Credential <PSCredential>]
[""-CertificateThumbprint <String> ] [""UseSSL][ ""ComputerName <string>]
2. Configure the Network Controller application
Install-NetworkController ""Node <NetworkControllerNode[]> ""ClientAuthentication
<ClientAuthentication> [""ClientCertificateThumbprint <string[]>]
[""ClientSecurityGroup <string>] -ServerCertificate <X509Certificate2>
[""RESTIPAddress <String>] [""RESTName <String>] [""Credential <PSCredential>]
[""CertificateThumbprint <String> ] [""UseSSL]
References:
https://technet.microsoft.com/en-us/library/mt282165.aspx

1. Install the Network Controller server role
Install-WindowsFeature -Name NetworkController ""IncludeManagementTools
2. Configure the Network Controller cluster
✑ Create a node object
New-NetworkControllerNodeObject ""Name <string> ""Server <String> ""FaultDomain <string> ""RestInterface <string>
[-NodeCertificate <X509Certificate2>]
1. Configure the cluster
Install-NetworkControllerCluster ""Node <NetworkControllerNode[]> ""ClusterAuthentication <ClusterAuthentication> [""ManagementSecurityGroup <string>]
[""DiagnosticLogLocation <string>][""LogLocationCredential <PSCredential>]
[""CredentialEncryptionCertificate <X509Certificate2>][""Credential <PSCredential>]
[""-CertificateThumbprint <String> ] [""UseSSL][ ""ComputerName <string>]
2. Configure the Network Controller application
Install-NetworkController ""Node <NetworkControllerNode[]> ""ClientAuthentication
<ClientAuthentication> [""ClientCertificateThumbprint <string[]>]
[""ClientSecurityGroup <string>] -ServerCertificate <X509Certificate2>
[""RESTIPAddress <String>] [""RESTName <String>] [""Credential <PSCredential>]
[""CertificateThumbprint <String> ] [""UseSSL]
References:
https://technet.microsoft.com/en-us/library/mt282165.aspx
send
light_mode
delete
Question #15
You deploy Microsoft System Center Virtual Machine Manager (SCVMM) and System Center Operations Manager (SCOM). You integrate SCVMM with SCOM.
You need to view the reports for SCVMM.
What are two possible ways to achieve the goal? Each correct answer presents a complete solution.
You need to view the reports for SCVMM.
What are two possible ways to achieve the goal? Each correct answer presents a complete solution.
- ALaunch the SCOM console.
- BLaunch the SCVMM console.
- CRun the Windows PowerShell cmdlet Get-SCOMMonitor.
- DRun the Windows PowerShell cmdlet Get-SCOMReportingSetting.
- EView the Reporting server website for SCOM.
Correct Answer:
AE
You can view reports in the Reporting workspace in System Center Operations Manager, or by using a web browser and entering this address: http://
ReportingServerName:port/reports.
References:
https://docs.microsoft.com/en-us/system-center/vmm/monitor?view=sc-vmm-1801
AE
You can view reports in the Reporting workspace in System Center Operations Manager, or by using a web browser and entering this address: http://
ReportingServerName:port/reports.
References:
https://docs.microsoft.com/en-us/system-center/vmm/monitor?view=sc-vmm-1801
send
light_mode
delete
All Pages
