Microsoft 70-417 Exam Practice Questions (P. 4)
- Full Access (691 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #31
Your network contains an Active Directory domain named contoso.com. All user accounts reside in an organizational unit (OU) named OU1. All of the users in the marketing department are members of a group named Marketing. All of the users in the human resources department are members of a group named HR.
You create a Group Policy object (GPO) named GPO1. You link GPO1 to OU1.
You configure the Group Policy preferences of GPO1 to add two shortcuts named Link1 and Link2 to the desktop of each user.
You need to ensure that Link1 only appears on the desktop of client computers that have more than 80 GB of free disk space and Link2 only appears on the desktop of client computers that have less than 80 GB of free disk space.
What should you configure?
You create a Group Policy object (GPO) named GPO1. You link GPO1 to OU1.
You configure the Group Policy preferences of GPO1 to add two shortcuts named Link1 and Link2 to the desktop of each user.
You need to ensure that Link1 only appears on the desktop of client computers that have more than 80 GB of free disk space and Link2 only appears on the desktop of client computers that have less than 80 GB of free disk space.
What should you configure?
- AGroup Policy Inheritance
- BWMI Filtering
- CSecurity Filtering
- DItem-level targeting
Correct Answer:
B
References: https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/cc733022(v%3dws.11)
B
References: https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/cc733022(v%3dws.11)
send
light_mode
delete
Question #32
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that has the Remote Access server role installed.
DirectAccess is implemented on Server1 by using the default configuration.
You discover that DirectAccess clients do not use DirectAccess when accessing websites on the Internet.
You need to ensure that DirectAccess clients access all Internet websites by using their DirectAccess connection.
What should you do?
DirectAccess is implemented on Server1 by using the default configuration.
You discover that DirectAccess clients do not use DirectAccess when accessing websites on the Internet.
You need to ensure that DirectAccess clients access all Internet websites by using their DirectAccess connection.
What should you do?
- AConfigure a DNS suffix search list on the DirectAccess clients.
- BEnable the Route all traffic through the internal network policy setting in the DirectAccess Server Settings Group Policy object (GPO).
- CConfigure DirectAccess to enable force tunneling.
- DDisable the DirectAccess Passive Mode policy setting in the DirectAccess Client Settings Group Policy object (GPO).
Correct Answer:
C
C
send
light_mode
delete
Question #33
Your network contains an Active Directory domain named contoso.com. The domain contains a Web server named www.contoso.com. The Web server is available on the Internet.
You implement DirectAccess by using the default configuration.
You need to ensure that users never attempt to connect to www.contoso.com by using DirectAccess. The solution must not prevent the users from using
DirectAccess to access other resources in contoso.com.
Which settings should you configure in a Group Policy object (GPO)?
You implement DirectAccess by using the default configuration.
You need to ensure that users never attempt to connect to www.contoso.com by using DirectAccess. The solution must not prevent the users from using
DirectAccess to access other resources in contoso.com.
Which settings should you configure in a Group Policy object (GPO)?
- ADirectAccess Client Experience Settings
- BName Resolution Policy
- CDNS Client
- DNetwork Connections
Correct Answer:
B
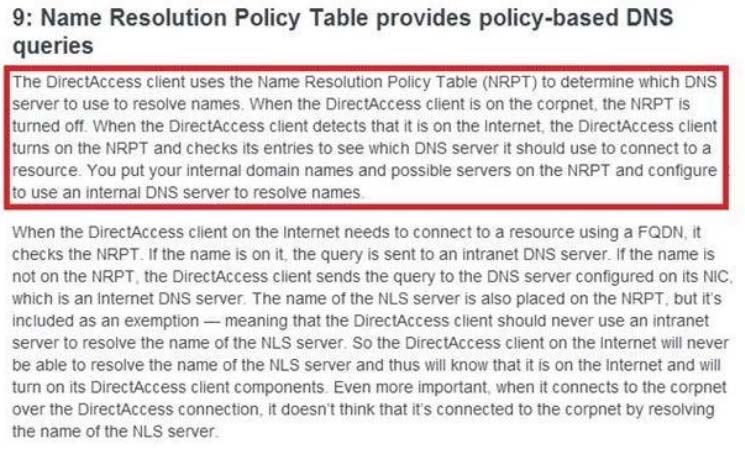
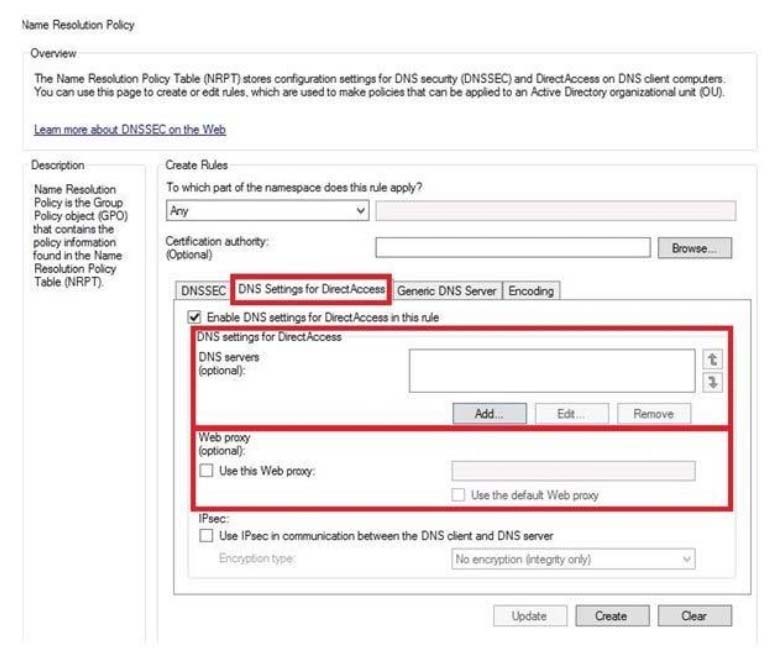
Notice this could have been Network connection:
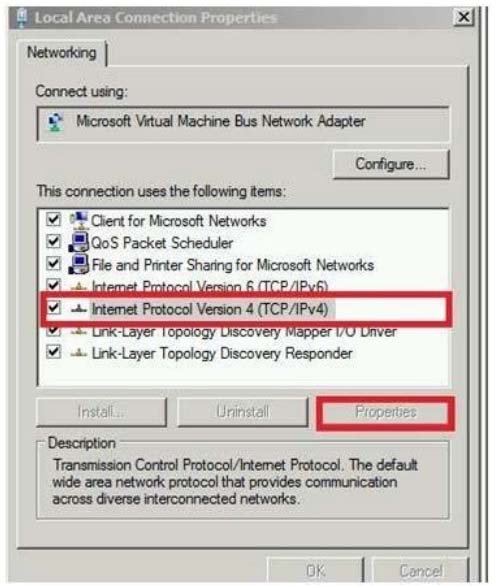
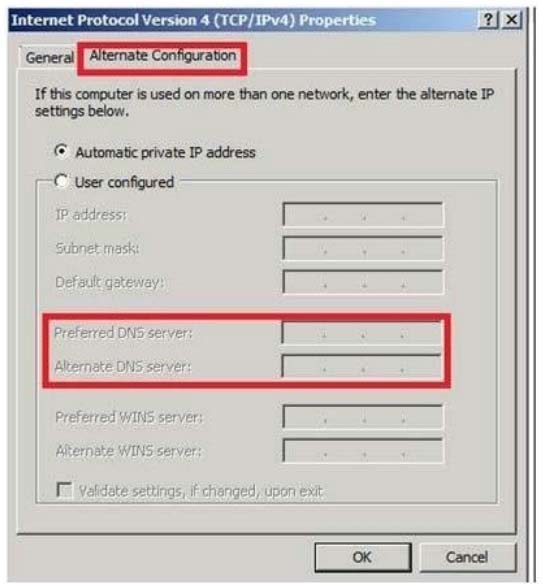
BUT "The solution must not prevent the users from using DirectAccess to access other resources in contoso.com"
References:
http://www.techrepublic.com/blog/10things/10-things-you-should-know-aboutdirectaccess/1371
B


Notice this could have been Network connection:


BUT "The solution must not prevent the users from using DirectAccess to access other resources in contoso.com"
References:
http://www.techrepublic.com/blog/10things/10-things-you-should-know-aboutdirectaccess/1371
send
light_mode
delete
Question #34
Your network contains an Active Directory domain named contoso.com. The domain contains a member server named Server1. Server1 runs Windows Server
2012 R2 and has the Hyper-V server role installed.
Server1 hosts 10 virtual machines. A virtual machine named VM1 runs Windows Server 2012 R2 and hosts a processor-intensive application named App1.
Users report that App1 responds more slowly than expected.
You need to monitor the processor usage on VM1 to identify whether changes must be made to the hardware settings of VM1.
Which performance object should you monitor on Server1?
2012 R2 and has the Hyper-V server role installed.
Server1 hosts 10 virtual machines. A virtual machine named VM1 runs Windows Server 2012 R2 and hosts a processor-intensive application named App1.
Users report that App1 responds more slowly than expected.
You need to monitor the processor usage on VM1 to identify whether changes must be made to the hardware settings of VM1.
Which performance object should you monitor on Server1?
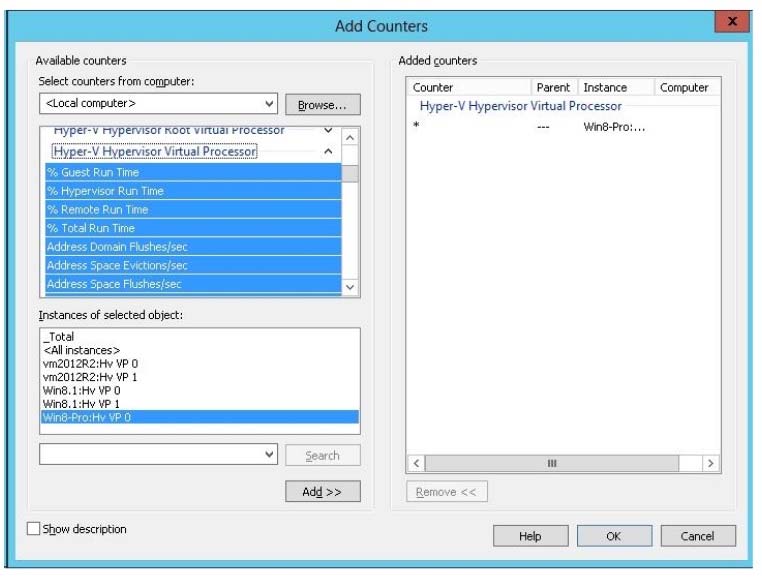
- AHyper-V Hypervisor Logical Processor
- BHyper-V Hypervisor Root Virtual Processor
- CProcessor
- DHyper-V Hypervisor Virtual Processor
- EProcess
Correct Answer:
D
The "Hyper-V Hypervisor Root Virtual Processor"and "Hyper-V Hypervisor Virtual Processor" are just slices of the LP counter and can help you understand how much total CPU the root and guests are using on the system.
The goal here is to monitor VM1 through Server1.
Hyper-V Hypervisor Virtual Processor will do that.
References:
http://social.technet.microsoft.com/wiki/contents/articles/1234.hyper-v-concepts-vcpu-virtual-processor.aspx http://blogs.msdn.com/b/tvoellm/archive/2008/05/12/hyper-v-performance-counters-part-four-of-many-hyper-v-hypervisor-virtual-processor-and- hyper-v- hypervisor-root-virtual-processor-counter-set.aspx
D
The "Hyper-V Hypervisor Root Virtual Processor"and "Hyper-V Hypervisor Virtual Processor" are just slices of the LP counter and can help you understand how much total CPU the root and guests are using on the system.
The goal here is to monitor VM1 through Server1.
Hyper-V Hypervisor Virtual Processor will do that.

References:
http://social.technet.microsoft.com/wiki/contents/articles/1234.hyper-v-concepts-vcpu-virtual-processor.aspx http://blogs.msdn.com/b/tvoellm/archive/2008/05/12/hyper-v-performance-counters-part-four-of-many-hyper-v-hypervisor-virtual-processor-and- hyper-v- hypervisor-root-virtual-processor-counter-set.aspx
send
light_mode
delete
Question #35
Your network contains two servers named Server1 and Server2. Both servers run Windows Server 2012 R2. On Server1, you create a Data Collector Set (DCS) named Data1.
You need to export Data1 to Server2.
What should you do first?
You need to export Data1 to Server2.
What should you do first?
- ARight-click Data1 and click Save template...
- BRight-click Data1 and click Export list...
- CRight-click Data1 and click Data Manager...
- DRight-click Data1 and click Properties.
Correct Answer:
A
Exporting Templates -
To export a Data Collector Set you create as a template for use on other computers, open Windows Performance Monitor, expand Data Collector Sets, right-click the Data Collector Set you want to export, and click Save Template. Select a directory in which to store theXML file and click Save.
A
Exporting Templates -
To export a Data Collector Set you create as a template for use on other computers, open Windows Performance Monitor, expand Data Collector Sets, right-click the Data Collector Set you want to export, and click Save Template. Select a directory in which to store theXML file and click Save.
send
light_mode
delete
Question #36
You have a server named Server1 that runs Windows Server 2012 R2.
You discover that the performance of Server1 is poor.
The results of a performance report generated on Server1 are shown in the following table.
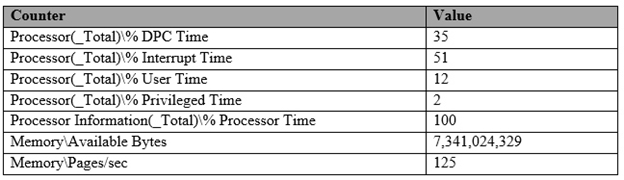
You need to identify the cause of the performance issue.
What should you identify?
You discover that the performance of Server1 is poor.
The results of a performance report generated on Server1 are shown in the following table.

You need to identify the cause of the performance issue.
What should you identify?
- AInsufficient processors
- BExcessive paging
- CDriver malfunction
- DInsufficient RAM
- ENUMA fragmentation
Correct Answer:
C
Processor: %DPC Time. Much like the other values, this counter shows the amount of time that the processor spends servicing DPC requests.
DPC requests are more often than not associated with the network interface.
Processor: % Interrupt Time. This is the percentage of time that the processor is spending on handling Interrupts. Generally, if this value exceeds 50% of the processor time you may have a hardware issue. Some components on the computer can force this issue and not really be a problem. For example a programmable I/O card like an old disk controller card, can take up to 40% of the CPU time. A NIC on a busy IIS server can likewise generate a large percentage of processor activity.
Processor: % User Time. The value of this counter helps to determine the kind of processing that is affecting the system. Of course the resulting value is the total amount of non-idle time that was spent on User mode operations. This generally means application code.
Processor: %Privilege Time. This is the amount of time the processor was busy with Kernel mode operations. If the processor is very busy and this mode is high, it is usually an indication of some type of NT service having difficulty, although user mode programs can make calls to the Kernel mode NT components to occasionally cause this type of performance issue.
Memory: Pages/sac This value is often confused with Page Faults/sec.
The Pages/sec counter is a combination of Pages Input/sec and Pages
Output/sec counters. Recall that Page Faults/sec is a combination of hard page faults and soft page faults. This counter, however, is a general indicator of how often the system is using the hard drive to store or retrieve memory associated data.
References:
http://technet.microsoft.com/en-us/library/cc768048.aspx
C
Processor: %DPC Time. Much like the other values, this counter shows the amount of time that the processor spends servicing DPC requests.
DPC requests are more often than not associated with the network interface.
Processor: % Interrupt Time. This is the percentage of time that the processor is spending on handling Interrupts. Generally, if this value exceeds 50% of the processor time you may have a hardware issue. Some components on the computer can force this issue and not really be a problem. For example a programmable I/O card like an old disk controller card, can take up to 40% of the CPU time. A NIC on a busy IIS server can likewise generate a large percentage of processor activity.
Processor: % User Time. The value of this counter helps to determine the kind of processing that is affecting the system. Of course the resulting value is the total amount of non-idle time that was spent on User mode operations. This generally means application code.
Processor: %Privilege Time. This is the amount of time the processor was busy with Kernel mode operations. If the processor is very busy and this mode is high, it is usually an indication of some type of NT service having difficulty, although user mode programs can make calls to the Kernel mode NT components to occasionally cause this type of performance issue.
Memory: Pages/sac This value is often confused with Page Faults/sec.
The Pages/sec counter is a combination of Pages Input/sec and Pages
Output/sec counters. Recall that Page Faults/sec is a combination of hard page faults and soft page faults. This counter, however, is a general indicator of how often the system is using the hard drive to store or retrieve memory associated data.
References:
http://technet.microsoft.com/en-us/library/cc768048.aspx
send
light_mode
delete
Question #37
Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2. All servers run
Windows Server 2012 R2.
Server1 and Server2 are nodes in a Hyper-V cluster named Cluster1. Cluster1 hosts 10 virtual machines. All of the virtual machines run Windows Server 2012 R2 and are members of the domain.
You need to ensure that the first time a service named Service1 fails on a virtual machine, the virtual machine is moved to a different node.
You configure Service1 to be monitored from Failover Cluster Manager.
What should you configure on the virtual machine?
Windows Server 2012 R2.
Server1 and Server2 are nodes in a Hyper-V cluster named Cluster1. Cluster1 hosts 10 virtual machines. All of the virtual machines run Windows Server 2012 R2 and are members of the domain.
You need to ensure that the first time a service named Service1 fails on a virtual machine, the virtual machine is moved to a different node.
You configure Service1 to be monitored from Failover Cluster Manager.
What should you configure on the virtual machine?
- AFrom the General settings, modify the Startup type.
- BFrom the Recovery settings of Service1, set the First failure recovery action to Take No Action.
- CFrom the Recovery settings of Service1, set the First failure recovery action to Restart the Service.
- DFrom the General settings, modify the Service status.
Correct Answer:
B
C. Configure the virtual machine to take no action through Hyper-V if the physical computer shuts down by modifying the Automatic Stop Action setting to None.
Virtual machine state must be managed through the Failover Clustering feature. http://technet.microsoft.com/en-us/library/cc742396.aspx http://windowsitpro.com/windows-server-2012/enable-windows-server-2012-failover-cluster-hyper-v-vmmonitoring
B
C. Configure the virtual machine to take no action through Hyper-V if the physical computer shuts down by modifying the Automatic Stop Action setting to None.
Virtual machine state must be managed through the Failover Clustering feature. http://technet.microsoft.com/en-us/library/cc742396.aspx http://windowsitpro.com/windows-server-2012/enable-windows-server-2012-failover-cluster-hyper-v-vmmonitoring
send
light_mode
delete
Question #38
You have a server named Server1 that runs Windows Server 2012 R2.
You need to configure Server1 to create an entry in an event log when the processor usage exceeds 60 percent.
Which type of data collector should you create?
You need to configure Server1 to create an entry in an event log when the processor usage exceeds 60 percent.
Which type of data collector should you create?
- AA performance counter data collector
- BAn event trace data collector
- CA performance counter alert
- DA configuration data collector
Correct Answer:
C
C
send
light_mode
delete
Question #39
Your network contains an Active Directory forest named contoso.com. All servers run Windows Server 2012 R2.
You need to create a custom Active Directory application partition.
Which tool should you use?
You need to create a custom Active Directory application partition.
Which tool should you use?
- AEseutil
- BDsadd
- CDsmod
- DNtdsutil
Correct Answer:
D
* To create or delete an application directory partition
* partition management
Manages directory partitions for Active Directory Domain Services (AD DS) or Active Directory Lightweight Directory Services (AD LDS).
This is a subcommand of Ntdsutil and Dsmgmt. Ntdsutil and Dsmgmt are command-line tools that are built into Windows Server 2008 and Windows Server 2008
R2.
* partition management create nc %s1 %s2
Creates the application directory partition with distinguished name %s1, on the Active Directory domain controller or AD LDS instance with full DNS name %s2. If you specify "NULL" for %s2, this command uses the currently connected Active Directory domain controller.
Use this command only with AD DS. For AD LDS, use createnc %s1 %s2 %s3.
Note:
An application directory partition is a directory partition that is replicated only to specific domain controllers. A domain controller that participates in the replication of a particular application directory partition hosts a replica of that partition.
D
* To create or delete an application directory partition
* partition management
Manages directory partitions for Active Directory Domain Services (AD DS) or Active Directory Lightweight Directory Services (AD LDS).
This is a subcommand of Ntdsutil and Dsmgmt. Ntdsutil and Dsmgmt are command-line tools that are built into Windows Server 2008 and Windows Server 2008
R2.
* partition management create nc %s1 %s2
Creates the application directory partition with distinguished name %s1, on the Active Directory domain controller or AD LDS instance with full DNS name %s2. If you specify "NULL" for %s2, this command uses the currently connected Active Directory domain controller.
Use this command only with AD DS. For AD LDS, use createnc %s1 %s2 %s3.
Note:
An application directory partition is a directory partition that is replicated only to specific domain controllers. A domain controller that participates in the replication of a particular application directory partition hosts a replica of that partition.
send
light_mode
delete
Question #40
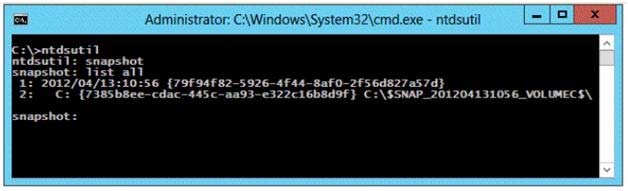
Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1.
You run ntdsutil as shown in the exhibit. (Click the Exhibit button.)
You need to ensure that you can access the contents of the mounted snapshot.
What should you do?
You run ntdsutil as shown in the exhibit. (Click the Exhibit button.)

You need to ensure that you can access the contents of the mounted snapshot.
What should you do?
- AFrom a command prompt, run dsamain.exe -dbpath c:\$snap_201204131056_volumec$\windows\ntds\ntds.dit -Idapport 33389.
- BFrom the snapshot context of ntdsutil, run mount {79f94f82-5926-4f44-8af0-2f56d827a57d>.
- CFrom the snapshot context of ntdsutil, run activate instance "NTDS".
- DFrom a command prompt, run dsamain.exe -dbpath c:\$snap_201204131056_volumec$\windows\ntds\ntds.dit -Idapport 389.
Correct Answer:
A
This is a live DC, so 389 is already in use; 33389 would not be so is a valid port.
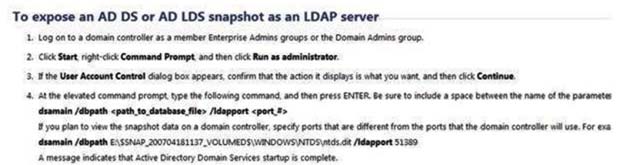
References:
http://technet.microsoft.com/en-us/library/cc753609(v=ws.10).aspx
A
This is a live DC, so 389 is already in use; 33389 would not be so is a valid port.

References:
http://technet.microsoft.com/en-us/library/cc753609(v=ws.10).aspx
send
light_mode
delete
All Pages
