Microsoft 70-417 Exam Practice Questions (P. 3)
- Full Access (691 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #21
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1. Server1 has the DHCP Server server role and the Network Policy Server role service installed.
Server1 contains three non-overlapping scopes named Scope1, Scope2, and Scope3. Server1 currently provides the same Network Access Protection (NAP) settings to the three scopes.
You modify the settings of Scope1 as shown in the exhibit. (Click the Exhibit button.)
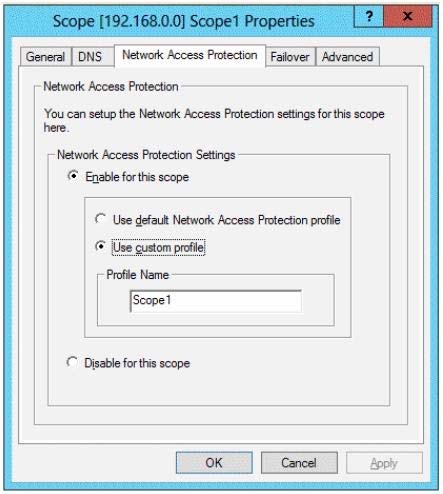
You need to configure Server1 to provide unique NAP enforcement settings to the NAP non-compliant DHCP clients from Scope1.
What should you create?
Server1 contains three non-overlapping scopes named Scope1, Scope2, and Scope3. Server1 currently provides the same Network Access Protection (NAP) settings to the three scopes.
You modify the settings of Scope1 as shown in the exhibit. (Click the Exhibit button.)

You need to configure Server1 to provide unique NAP enforcement settings to the NAP non-compliant DHCP clients from Scope1.
What should you create?
- AA network policy that has the MS-Service Class condition
- BA connection request policy that has the Service Type condition
- CA network policy that has the Identity Type condition
- DA connection request policy that has the Identity Type condition
Correct Answer:
A
A. Restricts the policy to clients that have received an IP address from a DHCP scope that matches the specified DHCP profile name. This condition is used only when you are deployingNAP with the DHCP enforcement method. To use the MS-Service Class attribute, in Specify the profile name that identifies your DHCP scope, type the name of an existing DHCP profile. http://technet.microsoft.com/en-us/library/cc731220(v=ws.10).aspx
A
A. Restricts the policy to clients that have received an IP address from a DHCP scope that matches the specified DHCP profile name. This condition is used only when you are deployingNAP with the DHCP enforcement method. To use the MS-Service Class attribute, in Specify the profile name that identifies your DHCP scope, type the name of an existing DHCP profile. http://technet.microsoft.com/en-us/library/cc731220(v=ws.10).aspx
send
light_mode
delete
Question #22
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2.
Server1 has the Network Policy Server role service installed.
You plan to configure Server1 as a Network Access Protection (NAP) health policy server for VPN enforcement by using the Configure NAPwizard.
You need to ensure that you can configure the VPN enforcement method on Server1 successfully.
What should you install on Server1 before you run the Configure NAP wizard?
Server1 has the Network Policy Server role service installed.
You plan to configure Server1 as a Network Access Protection (NAP) health policy server for VPN enforcement by using the Configure NAPwizard.
You need to ensure that you can configure the VPN enforcement method on Server1 successfully.
What should you install on Server1 before you run the Configure NAP wizard?
- AA computer certificate
- BA system health validator (SHV)
- CThe Remote Access server role
- DThe Host Credential Authorization Protocol (HCAP)
Correct Answer:
A
Configure Policies for VPN Enforcement
The NAP health policy server uses the Network Policy Server (NPS) role service with configured network policies, health policies, and system health validators
(SHVs) to evaluate client health based on administrator defined requirements. Based on the results of this evaluation, NPS instructs the virtual private network
(VPN) server to provide full access to compliant NAP client computers and to restrict access to noncompliant client computers when NAP is deployed using full enforcement mode.
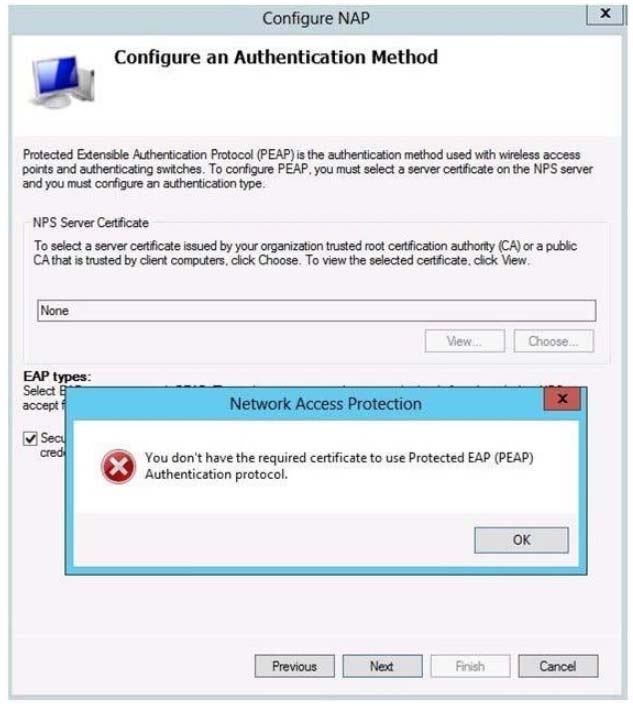
Before performing this procedure, you must install a certificate for Protected Extensible Authentication Protocol (PEAP) authentication. For more information, see
Install a Computer -
Certificate for PEAP -
You cannot continue without a valid certificate:
References:
http://technet.microsoft.com/fr-fr/library/dd314165%28v=ws.10%29.aspx
A
Configure Policies for VPN Enforcement
The NAP health policy server uses the Network Policy Server (NPS) role service with configured network policies, health policies, and system health validators
(SHVs) to evaluate client health based on administrator defined requirements. Based on the results of this evaluation, NPS instructs the virtual private network
(VPN) server to provide full access to compliant NAP client computers and to restrict access to noncompliant client computers when NAP is deployed using full enforcement mode.
Before performing this procedure, you must install a certificate for Protected Extensible Authentication Protocol (PEAP) authentication. For more information, see
Install a Computer -
Certificate for PEAP -

You cannot continue without a valid certificate:

References:
http://technet.microsoft.com/fr-fr/library/dd314165%28v=ws.10%29.aspx
send
light_mode
delete
Question #23
Your network contains an Active Directory domain named contoso.com. The domain contains client computers that run Either Windows XP, Windows 7, or
Windows 8.
Network Policy Server (NPS) is deployed to the domain.
You plan to create a system health validator (SHV).
You need to identify which policy settings can be applied to all of the computers.
Which three policy settings should you identify? (Each correct answer presents part of the solution. Choose three.)
Windows 8.
Network Policy Server (NPS) is deployed to the domain.
You plan to create a system health validator (SHV).
You need to identify which policy settings can be applied to all of the computers.
Which three policy settings should you identify? (Each correct answer presents part of the solution. Choose three.)
- AAutomatic updating is enabled.
- BA firewall is enabled for all network connections.
- CAn antispyware application is on.
- DAntispyware is up to date.
- EAntivirus is up to date.
Correct Answer:
ABE
http://technet.microsoft.com/en-us/library/cc731260.aspx
* System health agent (SHA) is a NAP component.
* System health agent (SHA)
A component that checks the state of the client computer to determine whether the settings monitored by the SHA are up-to-date and configured correctly. For example, the Windows Security Health Agent (WSHA) can monitor Windows Firewall, whether antivirus software is installed, enabled, and updated, whether antispyware software is installed, enabled, and updated, and whether Microsoft Update Services is enabled and the computer has the most recent security updates from Microsoft Update Services. There might also be SHAs (and corresponding system health validators) available from other companies that provide different functionality.
ABE
http://technet.microsoft.com/en-us/library/cc731260.aspx
* System health agent (SHA) is a NAP component.
* System health agent (SHA)
A component that checks the state of the client computer to determine whether the settings monitored by the SHA are up-to-date and configured correctly. For example, the Windows Security Health Agent (WSHA) can monitor Windows Firewall, whether antivirus software is installed, enabled, and updated, whether antispyware software is installed, enabled, and updated, and whether Microsoft Update Services is enabled and the computer has the most recent security updates from Microsoft Update Services. There might also be SHAs (and corresponding system health validators) available from other companies that provide different functionality.
send
light_mode
delete
Question #24
Your network contains an Active Directory domain named adatum.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 is configured as a Network Policy Server (NPS) server and as a DHCP server.
The network contains two subnets named Subnet1 and Subnet2. Server1 has a DHCP scope for each subnet.
You need to ensure that noncompliant computers on Subnet1 receive different network policies than noncompliant computers on Subnet2.
Which two settings should you configure? (Each correct answer presents part of the solution. Choose two.)
The network contains two subnets named Subnet1 and Subnet2. Server1 has a DHCP scope for each subnet.
You need to ensure that noncompliant computers on Subnet1 receive different network policies than noncompliant computers on Subnet2.
Which two settings should you configure? (Each correct answer presents part of the solution. Choose two.)
- AThe NAS Port Type constraints
- BThe Health Policies conditions
- CThe Called Station ID constraints
- DThe NAP-Capable Computers conditions
- EThe MS-Service Class conditions
Correct Answer:
DE
The NAP health policy server uses the NPS role service with configured health policies and system health validators (SHVs) to evaluate client health based on administrator-defined requirements. Based on results of this evaluation, NPS instructs the DHCP server to provide full access to compliant NAP client computers and to restrict access to client computers that are noncompliant with health requirements. If policies are filtered by DHCP scope, then MS-Service Class is configured in policy conditions.
DE
The NAP health policy server uses the NPS role service with configured health policies and system health validators (SHVs) to evaluate client health based on administrator-defined requirements. Based on results of this evaluation, NPS instructs the DHCP server to provide full access to compliant NAP client computers and to restrict access to client computers that are noncompliant with health requirements. If policies are filtered by DHCP scope, then MS-Service Class is configured in policy conditions.
send
light_mode
delete
Question #25
Your network contains a single Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2.
The domain contains 400 desktop computers that run Windows 8 and 200 desktop computers that run Windows Vista Service Pack 2 (SP2).
All of the desktop computers are located in an organizational unit (OU) named OU1.
You create a Group Policy object (GPO) named GPO1. GPO1 contains startup script settings.
You link GPO1 to OU1.
You need to ensure that GPO1 is applied only to computers that run Windows 8.
What should you do?
The domain contains 400 desktop computers that run Windows 8 and 200 desktop computers that run Windows Vista Service Pack 2 (SP2).
All of the desktop computers are located in an organizational unit (OU) named OU1.
You create a Group Policy object (GPO) named GPO1. GPO1 contains startup script settings.
You link GPO1 to OU1.
You need to ensure that GPO1 is applied only to computers that run Windows 8.
What should you do?
- AModify the Security settings of OU1.
- BCreate and link a WMI filter to GPO1.
- CRun the Set-GPInheritancecmdlet and specify the -target parameter.
- DRun the Set-GPLinkcmdlet and specify the -target parameter.
Correct Answer:
B
WMI Filtering is used to get information of the system and apply the GPO on it with the condition is met.Security filtering: apply a GPO to a specific group
(members of the group)
B
WMI Filtering is used to get information of the system and apply the GPO on it with the condition is met.Security filtering: apply a GPO to a specific group
(members of the group)
send
light_mode
delete
Question #26
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012. Server1 has the Remote Desktop Session Host role service installed. The computer account of Server1 resides in an organizational unit (OU) named OU1.
You create and link a Group Policy object (GPO) named GPO1 to OU1. GPO1 is configured as shown in the exhibit. (Click the Exhibit button.)
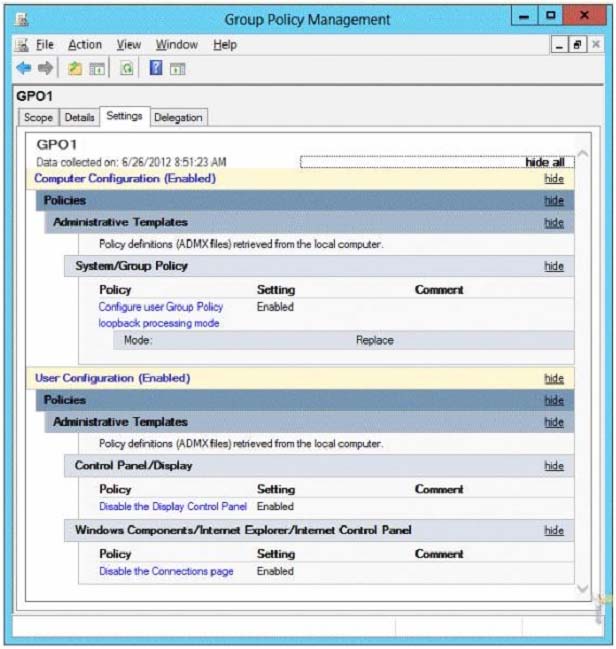
You need to prevent GPO1 from applying to your user account when you log on to Server1. GPO1 must apply to every other user who logs on to Server1.
What should you configure?
You create and link a Group Policy object (GPO) named GPO1 to OU1. GPO1 is configured as shown in the exhibit. (Click the Exhibit button.)

You need to prevent GPO1 from applying to your user account when you log on to Server1. GPO1 must apply to every other user who logs on to Server1.
What should you configure?
- AItem-level targeting
- BSecurity Filtering
- CBlock Inheritance
- DWMI Filtering
Correct Answer:
B
Security filtering is a way of refining which users and computers will receive and apply the settings in a Group Policy object (GPO). Using security filtering, you can specify that only certain security principals within a container where the GPO is linked apply the GPO. Security group filtering determines whether the GPO as a whole applies to groups, users, or computers; it cannot be used selectively on different settings within a GPO.
B
Security filtering is a way of refining which users and computers will receive and apply the settings in a Group Policy object (GPO). Using security filtering, you can specify that only certain security principals within a container where the GPO is linked apply the GPO. Security group filtering determines whether the GPO as a whole applies to groups, users, or computers; it cannot be used selectively on different settings within a GPO.
send
light_mode
delete
Question #27
DRAG DROP -
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012.
The domain contains an organizational unit (OU) named OU1. OU1 contains an OU named OU2. OU2 contains a user named User1.
User1 is the member of a group named Group1. Group1 is in the Users container.
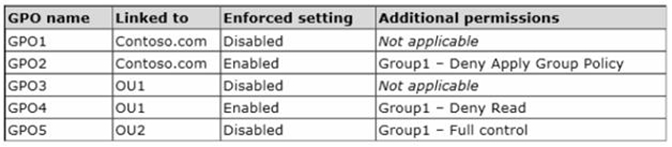
You create five Group Policy objects (GPO). The GPOs are configured as shown in the following table.
The Authenticated Users group is assigned the default permissions to all of the GPOs.
There are no site-level GPOs.
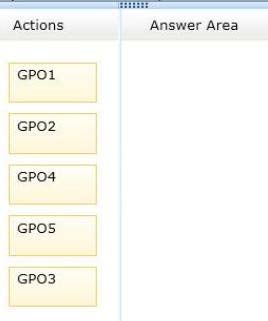
You need to identify which three GPOs will be applied to User1 and in which order the GPOs will be applied to User1.
Which three GPOs should you identify in sequence?
To answer, move the appropriate three GPOs from the list of GPOs to the answer area and arrange them in the correct order.
Select and Place:
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012.
The domain contains an organizational unit (OU) named OU1. OU1 contains an OU named OU2. OU2 contains a user named User1.
User1 is the member of a group named Group1. Group1 is in the Users container.
You create five Group Policy objects (GPO). The GPOs are configured as shown in the following table.

The Authenticated Users group is assigned the default permissions to all of the GPOs.
There are no site-level GPOs.
You need to identify which three GPOs will be applied to User1 and in which order the GPOs will be applied to User1.
Which three GPOs should you identify in sequence?
To answer, move the appropriate three GPOs from the list of GPOs to the answer area and arrange them in the correct order.
Select and Place:

Correct Answer:
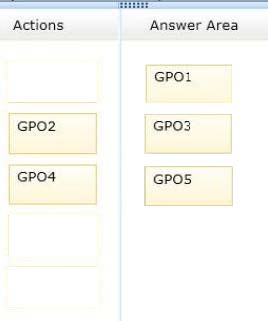
Box 1: GPO1 -
Box 2: GPO3 -
Box 3: GPO5 -
Note:
* Box 1: Domain GPOs are applied before OU GPOs.

Box 1: GPO1 -
Box 2: GPO3 -
Box 3: GPO5 -
Note:
* Box 1: Domain GPOs are applied before OU GPOs.
send
light_mode
delete
Question #28
DRAG DROP -
Your network contains an Active Directory domain named contoso.com. All client computers run Windows 8.
Group Policy objects (GPOs) are linked to the domain as shown in the exhibit. (Click the Exhibit button.)
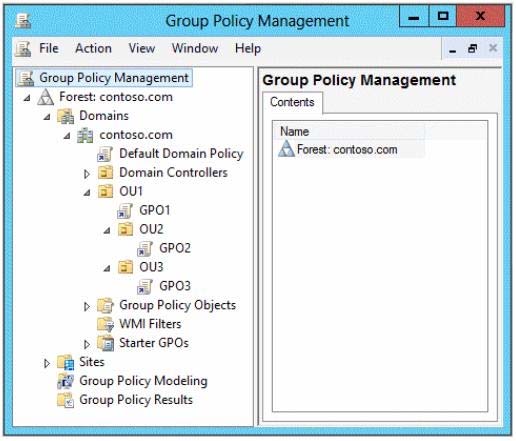
GPO2 contains computer configurations only and GPO3 contains user configurations only.
You need to configure the GPOs to meet the following requirements:
Ensure that GPO2 only applies to the computer accounts in OU2 that have more than one processor.
Ensure that GPO3 only applies to the user accounts in OU3 that are members of a security group named SecureUsers.
Which setting should you configure in each GPO?
To answer, drag the appropriate setting to the correct GPO. Each setting may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
Select and Place:
Your network contains an Active Directory domain named contoso.com. All client computers run Windows 8.
Group Policy objects (GPOs) are linked to the domain as shown in the exhibit. (Click the Exhibit button.)

GPO2 contains computer configurations only and GPO3 contains user configurations only.
You need to configure the GPOs to meet the following requirements:
Ensure that GPO2 only applies to the computer accounts in OU2 that have more than one processor.
Ensure that GPO3 only applies to the user accounts in OU3 that are members of a security group named SecureUsers.
Which setting should you configure in each GPO?
To answer, drag the appropriate setting to the correct GPO. Each setting may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
Select and Place:
send
light_mode
delete
Question #29
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2.
An organizational unit (OU) named OU1 contains 200 client computers that run Windows 8 Enterprise. A Group Policy object (GPO) named GPO1 is linked to
OU1.
You make a change to GPO1.
You need to force all of the computers in OU1 to refresh their Group Policy settings immediately. The solution must minimize administrative effort.
Which tool should you use?
An organizational unit (OU) named OU1 contains 200 client computers that run Windows 8 Enterprise. A Group Policy object (GPO) named GPO1 is linked to
OU1.
You make a change to GPO1.
You need to force all of the computers in OU1 to refresh their Group Policy settings immediately. The solution must minimize administrative effort.
Which tool should you use?
- AThe Secedit command
- BThe Invoke-GpUpdate cmdlet
- CGroup Policy Object Editor
- DServer Manager
Correct Answer:
B
References: https://technet.microsoft.com/en-us/library/jj134201.aspx
B
References: https://technet.microsoft.com/en-us/library/jj134201.aspx
send
light_mode
delete
Question #30
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012.
The domain contains an Edge Server named Server1. Server1 is configured as a DirectAccess server. Server1 has the following settings:
✑ Internal DNS name: Server1.contoso.com
✑ External DNS name: dal.contoso.com
✑ Internal IPv6 address: 2002:cla8:6a:3333::1
✑ External IPv4 address:65.55.37.62
Your company uses split-brain DNS for the contoso.com zone.
You run the Remote Access Setup wizard as shown in the following exhibit. (Click the Exhibit button.)
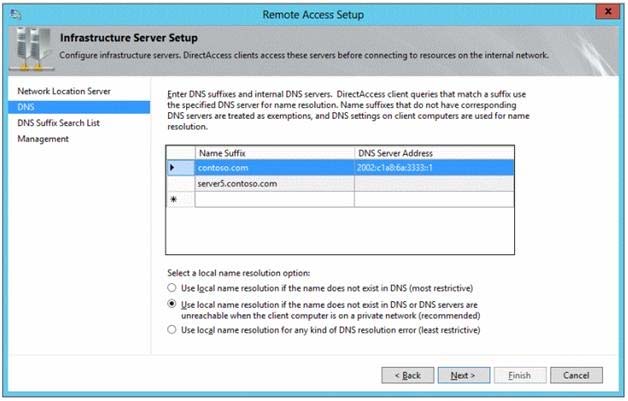
You need to ensure that client computers on the Internet can establish DirectAccess connections to Server1.
Which additional name suffix entry should you add from the Remote Access Setup wizard?
The domain contains an Edge Server named Server1. Server1 is configured as a DirectAccess server. Server1 has the following settings:
✑ Internal DNS name: Server1.contoso.com
✑ External DNS name: dal.contoso.com
✑ Internal IPv6 address: 2002:cla8:6a:3333::1
✑ External IPv4 address:65.55.37.62
Your company uses split-brain DNS for the contoso.com zone.
You run the Remote Access Setup wizard as shown in the following exhibit. (Click the Exhibit button.)

You need to ensure that client computers on the Internet can establish DirectAccess connections to Server1.
Which additional name suffix entry should you add from the Remote Access Setup wizard?
- AA Name Suffix value of Server1.contoso.com and a blank DNS Server Address value
- BA Name Suffix value of dal.contoso.com and a blank DNS Server Address value
- CA Name Suffix value of Server1.contoso.com and a DNS Server Address value of 65.55.37.62
- DA Name Suffix value of dal.contoso.com and a DNS Server Address value of 65.55.37.62
Correct Answer:
A
* In a non-split-brain DNS environment, the Internet namespace is different from the intranet namespace. For example, the Contoso Corporation uses contoso.com on the Internet and corp.contoso.com on the intranet. Because all intranet resources use the corp.contoso.com DNS suffix, the NRPT rule for corp.contoso.com routes all DNS name queries for intranet resources to intranet DNS servers. DNS name queries for names with the contoso.com suffix do not match the corp.contoso.com intranet namespace rule in the NRPT and are sent to Internet DNS servers.
* Split-brain DNS is a configuration method that enables proper resolution of names (e.g., example.com) from both inside and outside of your local network.
Note: For split-brain DNS deployments, you must list the FQDNs that are duplicated on the Internet and intranet and decide which resources the DirectAccess client should reach, the intranet version or the public (Internet) version. For each name that corresponds to a resource for which you want DirectAccess clients to reach the public version, you must add the corresponding FQDN as an exemption rule to the NRPT for your DirectAccess clients. Name suffixes that do not have corresponding DNS servers are treated as exemptions.
A
* In a non-split-brain DNS environment, the Internet namespace is different from the intranet namespace. For example, the Contoso Corporation uses contoso.com on the Internet and corp.contoso.com on the intranet. Because all intranet resources use the corp.contoso.com DNS suffix, the NRPT rule for corp.contoso.com routes all DNS name queries for intranet resources to intranet DNS servers. DNS name queries for names with the contoso.com suffix do not match the corp.contoso.com intranet namespace rule in the NRPT and are sent to Internet DNS servers.
* Split-brain DNS is a configuration method that enables proper resolution of names (e.g., example.com) from both inside and outside of your local network.
Note: For split-brain DNS deployments, you must list the FQDNs that are duplicated on the Internet and intranet and decide which resources the DirectAccess client should reach, the intranet version or the public (Internet) version. For each name that corresponds to a resource for which you want DirectAccess clients to reach the public version, you must add the corresponding FQDN as an exemption rule to the NRPT for your DirectAccess clients. Name suffixes that do not have corresponding DNS servers are treated as exemptions.
send
light_mode
delete
All Pages