Microsoft 70-412 Exam Practice Questions (P. 4)
- Full Access (448 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #31
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2 and has the DHCP Server server role installed.
You need to create an IPv6 scope on Server1. The scope must use an address space that is reserved for private networks. The addresses must be routable.
Which IPV6 scope prefix should you use?
You need to create an IPv6 scope on Server1. The scope must use an address space that is reserved for private networks. The addresses must be routable.
Which IPV6 scope prefix should you use?
- A2001:123:4567:890A::
- BFE80:123:4567::
- CFF00:123:4567:890A::
- DFD00:123:4567::
Correct Answer:
D
* A unique local address (ULA) is an IPv6 address in the block fc00::/7, defined in RFC 4193. It is the approximate IPv6 counterpart of the IPv4 private address.
The address block fc00::/7 is divided into two /8 groups:
/ The block fc00::/8 has not been defined yet.
/ The block fd00::/8 is defined for /48 prefixes, formed by setting the 40 least-significant bits of the prefix to a randomly generated bit string.
* Prefixes in the fd00::/8 range have similar properties as those of the IPv4 private address ranges:
/ They are not allocated by an address registry and may be used in networks by anyone without outside involvement.
/ They are not guaranteed to be globally unique.
/ Reverse Domain Name System (DNS) entries (under ip6.arpa) for fd00::/8 ULAs cannot be delegated in the global DNS.
Reference: RFC 4193
D
* A unique local address (ULA) is an IPv6 address in the block fc00::/7, defined in RFC 4193. It is the approximate IPv6 counterpart of the IPv4 private address.
The address block fc00::/7 is divided into two /8 groups:
/ The block fc00::/8 has not been defined yet.
/ The block fd00::/8 is defined for /48 prefixes, formed by setting the 40 least-significant bits of the prefix to a randomly generated bit string.
* Prefixes in the fd00::/8 range have similar properties as those of the IPv4 private address ranges:
/ They are not allocated by an address registry and may be used in networks by anyone without outside involvement.
/ They are not guaranteed to be globally unique.
/ Reverse Domain Name System (DNS) entries (under ip6.arpa) for fd00::/8 ULAs cannot be delegated in the global DNS.
Reference: RFC 4193
send
light_mode
delete
Question #32
Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 that runs Windows Server 2012 R2.
DC1 has the DNS Server server role installed.
The network contains client computers that run either Linux, Windows 7, or Windows 8. You have a standard primary zone named adatum.com as shown in the exhibit. (Click the Exhibit button.)
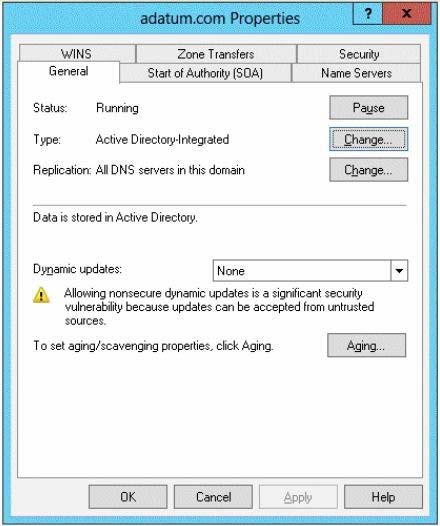
You plan to configure Name Protection on all of the DHCP servers.
You need to configure the adatum.com zone to support Name Protection.
Which two configurations should you perform from DNS Manager? (Each correct answer presents part of the solution. Choose two.)
DC1 has the DNS Server server role installed.
The network contains client computers that run either Linux, Windows 7, or Windows 8. You have a standard primary zone named adatum.com as shown in the exhibit. (Click the Exhibit button.)

You plan to configure Name Protection on all of the DHCP servers.
You need to configure the adatum.com zone to support Name Protection.
Which two configurations should you perform from DNS Manager? (Each correct answer presents part of the solution. Choose two.)
- ASign the zone.
- BStore the zone in Active Directory.
- CModify the Security settings of the zone.
- DConfigure Dynamic updates.
- EAdd a DNS key record
Correct Answer:
BD
Name protection requires secure update to work. Without name protection DNS names may be hijacked.
You can use the following procedures to allow only secure dynamic updates for a zone. Secure dynamic update is supported only for Active Directoryintegrated zones. If the zone type is configured differently, you must change the zone type and directory-integrate the zone before securing it for Domain Name System
(DNS) dynamic updates.
1. (B) Convert primary DNS server to Active Directory integrated primary
2. (D) Enable secure dynamic updates
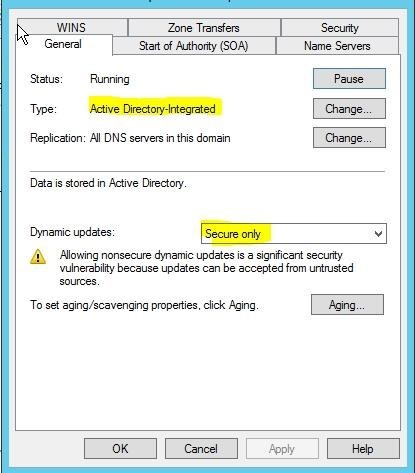
Reference: DHCP: Secure DNS updates should be configured if Name Protection is enabled on any IPv4 scope http://technet.microsoft.com/en-us/library/ee941152(v=ws.10).aspx
BD
Name protection requires secure update to work. Without name protection DNS names may be hijacked.
You can use the following procedures to allow only secure dynamic updates for a zone. Secure dynamic update is supported only for Active Directoryintegrated zones. If the zone type is configured differently, you must change the zone type and directory-integrate the zone before securing it for Domain Name System
(DNS) dynamic updates.
1. (B) Convert primary DNS server to Active Directory integrated primary
2. (D) Enable secure dynamic updates

Reference: DHCP: Secure DNS updates should be configured if Name Protection is enabled on any IPv4 scope http://technet.microsoft.com/en-us/library/ee941152(v=ws.10).aspx
send
light_mode
delete
Question #33
HOTSPOT -
Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Server1 and Server2. All servers run Windows
Server 2012 R2.
You install the DHCP Server server role on both servers.
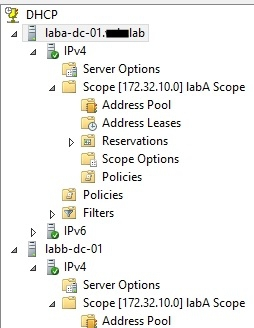
On Server1, you have the DHCP scope configured as shown in the exhibit. (Click the Exhibit button.)
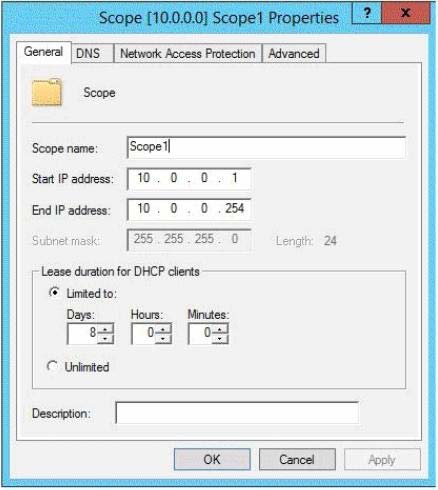
You need to configure the scope to be load-balanced across Server1 and Server2.
What Windows PowerShell cmdlet should you run on Server1?
To answer, select the appropriate options in the answer area.
Hot Area:
Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Server1 and Server2. All servers run Windows
Server 2012 R2.
You install the DHCP Server server role on both servers.
On Server1, you have the DHCP scope configured as shown in the exhibit. (Click the Exhibit button.)

You need to configure the scope to be load-balanced across Server1 and Server2.
What Windows PowerShell cmdlet should you run on Server1?
To answer, select the appropriate options in the answer area.
Hot Area:
Correct Answer:
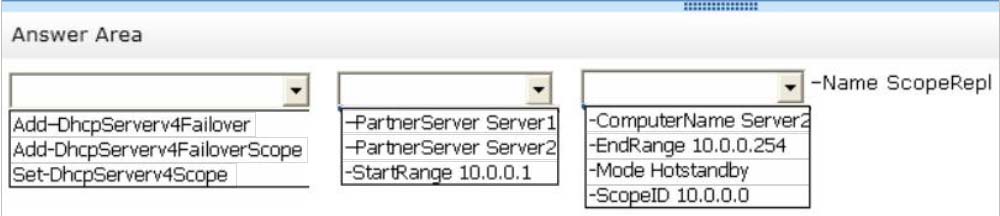
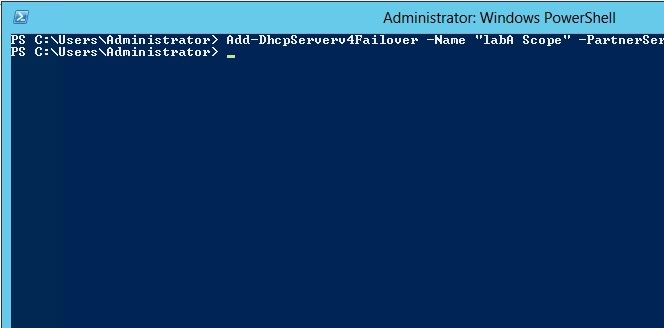
* Add-DhcpServerv4Failover
The Add-DhcpServerv4Failover cmdlet adds a new IPv4 failover relationship to a Dynamic Host Configuration Protocol (DHCP) server service.
/ -PartnerServer<String>
Specifies the IPv4 address, or host name, of the partner DHCP server service with which the failover relationship is created.
/ -ScopeId<IPAddress[]>
Specifies the scope identifiers, in IPv4 address format, which are to be added to the failover relationship.
* Example:
Reference: Add-DhcpServerv4Failover

* Add-DhcpServerv4Failover
The Add-DhcpServerv4Failover cmdlet adds a new IPv4 failover relationship to a Dynamic Host Configuration Protocol (DHCP) server service.
/ -PartnerServer<String>
Specifies the IPv4 address, or host name, of the partner DHCP server service with which the failover relationship is created.
/ -ScopeId<IPAddress[]>
Specifies the scope identifiers, in IPv4 address format, which are to be added to the failover relationship.
* Example:


Reference: Add-DhcpServerv4Failover
send
light_mode
delete
Question #34
HOTSPOT -
Your network contains an Active Directory domain named contoso.com. The domain contains two DHCP servers named Server1 and Server2. Both servers have multiple IPv4 scopes.
Server1 and Server2 are used to assign IP addresses for the network IDs of 172.20.0.0/16 and 131.107.0.0/16.
You install the IP Address Management (IPAM) Server feature on a server named IPAM1 and configure IPAM1 to manage Server1 and Server2.
Some users from the 172.20.0.0 network report that they occasionally receive an IP address conflict error message.
You need to identify whether any scopes in the 172.20.0.0 network ID conflict with one another.
What Windows PowerShell cmdlet should you run?
To answer, select the appropriate options in the answer area.
Hot Area:
Your network contains an Active Directory domain named contoso.com. The domain contains two DHCP servers named Server1 and Server2. Both servers have multiple IPv4 scopes.
Server1 and Server2 are used to assign IP addresses for the network IDs of 172.20.0.0/16 and 131.107.0.0/16.
You install the IP Address Management (IPAM) Server feature on a server named IPAM1 and configure IPAM1 to manage Server1 and Server2.
Some users from the 172.20.0.0 network report that they occasionally receive an IP address conflict error message.
You need to identify whether any scopes in the 172.20.0.0 network ID conflict with one another.
What Windows PowerShell cmdlet should you run?
To answer, select the appropriate options in the answer area.
Hot Area:

Correct Answer:
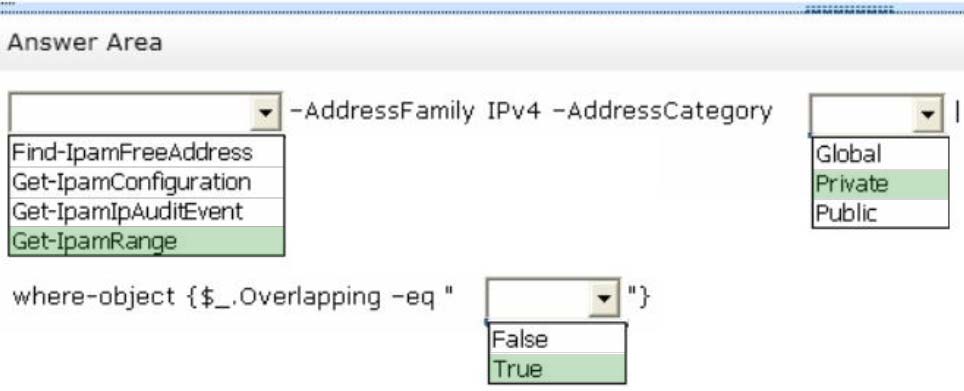
Type the following command at a Windows PowerShell prompt and press ENTER:
PS C:\> Get-IpamRange –AddressFamily IPv4 –AddressCategory Private|where-object {$_.Overlapping –eq "True"}
The previous command will display any overlapping IP address ranges, if they exist.
Reference: Walkthrough: Demonstrate IPAM in Windows Server 2012 R2.

Type the following command at a Windows PowerShell prompt and press ENTER:
PS C:\> Get-IpamRange –AddressFamily IPv4 –AddressCategory Private|where-object {$_.Overlapping –eq "True"}
The previous command will display any overlapping IP address ranges, if they exist.
Reference: Walkthrough: Demonstrate IPAM in Windows Server 2012 R2.
send
light_mode
delete
Question #35
Your network contains two DNS servers named DNS1 and DNS2 that run Windows Server 2012 R2.
DNS1 has a primary zone named contoso.com. DNS2 has a secondary copy of the contoso.com zone.
You need to log the zone transfer packets sent between DNS1 and DNS2.
What should you configure?
DNS1 has a primary zone named contoso.com. DNS2 has a secondary copy of the contoso.com zone.
You need to log the zone transfer packets sent between DNS1 and DNS2.
What should you configure?
- AMonitoring from DNS Manager
- BLogging from Windows Firewall with Advanced Security
- CA Data Collector Set (DCS) from Performance Monitor
- DDebug logging from DNS Manager
Correct Answer:
D
Debug logging allows you to log the packets sent and received by a DNS server. Debug logging is disabled by default, and because it is resource intensive, you should only activate it temporarily when you need more specific detailed information about server performance.
Reference: Active Directory 2008: DNS Debug Logging Facts.
D
Debug logging allows you to log the packets sent and received by a DNS server. Debug logging is disabled by default, and because it is resource intensive, you should only activate it temporarily when you need more specific detailed information about server performance.
Reference: Active Directory 2008: DNS Debug Logging Facts.
send
light_mode
delete
Question #36
Your network contains an Active Directory forest named contoso.com.
Users frequently access the website of an external partner company. The URL of the website is http://partners.adatum.com.
The partner company informs you that it will perform maintenance on its Web server and that the IP addresses of the Web server will change.
After the change is complete, the users on your internal network report that they fail to access the website. However, some users who work from home report that they can access the website.
You need to ensure that your DNS servers can resolve partners.adatum.com to the correct IP address immediately.
What should you do?
Users frequently access the website of an external partner company. The URL of the website is http://partners.adatum.com.
The partner company informs you that it will perform maintenance on its Web server and that the IP addresses of the Web server will change.
After the change is complete, the users on your internal network report that they fail to access the website. However, some users who work from home report that they can access the website.
You need to ensure that your DNS servers can resolve partners.adatum.com to the correct IP address immediately.
What should you do?
- ARun dnscmd and specify the CacheLockingPercent parameter.
- BRun Set-DnsServerGlobalQueryBlockList.
- CRun ipconfig and specify the Renew parameter.
- DRun Set-DnsServerCache.
Correct Answer:
D
The Set-DnsServerCache cmdlet modifies cache settings for a DomainName System (DNS) server.
Run Set-DnsServerCache with the -LockingPercent switch.
/ -LockingPercent<UInt32>
Specifies a percentage of the original Time to Live (TTL) value that caching can consume.
Cache locking is configured as a percent value. For example, if the cache locking value is set to 50, the DNS server does not overwrite a cached entry for half of the duration of the TTL. By default, the cache locking percent value is 100. This value means that the DNS server will not overwrite cached entries for the entire duration of the TTL.
Note. A better way would be clear the DNS cache on the DNS server with either Dnscmd /ClearCache (from command prompt), or Clear-DnsServerCache (from
Windows PowerShell).
References: https://technet.microsoft.com/en-us/library/jj649852.aspx
Incorrect Answers:
A. You need to use the /config parameter as well:
You can change this value if you like by using the dnscmd command: dnscmd /Config /CacheLockingPercent<percent>
D
The Set-DnsServerCache cmdlet modifies cache settings for a DomainName System (DNS) server.
Run Set-DnsServerCache with the -LockingPercent switch.
/ -LockingPercent<UInt32>
Specifies a percentage of the original Time to Live (TTL) value that caching can consume.
Cache locking is configured as a percent value. For example, if the cache locking value is set to 50, the DNS server does not overwrite a cached entry for half of the duration of the TTL. By default, the cache locking percent value is 100. This value means that the DNS server will not overwrite cached entries for the entire duration of the TTL.
Note. A better way would be clear the DNS cache on the DNS server with either Dnscmd /ClearCache (from command prompt), or Clear-DnsServerCache (from
Windows PowerShell).
References: https://technet.microsoft.com/en-us/library/jj649852.aspx
Incorrect Answers:
A. You need to use the /config parameter as well:
You can change this value if you like by using the dnscmd command: dnscmd /Config /CacheLockingPercent<percent>
send
light_mode
delete
Question #37
You have a server named Server1.
You install the IP Address Management (IPAM) Server feature on Server1.
You need to provide a user named User1 with the ability to set the access scope of all the DHCP servers that are managed by IPAM. The solution must use the principle of least privilege.
Which user role should you assign to User1?
You install the IP Address Management (IPAM) Server feature on Server1.
You need to provide a user named User1 with the ability to set the access scope of all the DHCP servers that are managed by IPAM. The solution must use the principle of least privilege.
Which user role should you assign to User1?
- ADNS Record Administrator Role
- BIPAM DHCP Reservations Administrator Role
- CIPAM Administrator Role
- DIPAM DHCP Administrator Role
Correct Answer:
D
The IPAM DHCP administrator role completely manages DHCP servers.
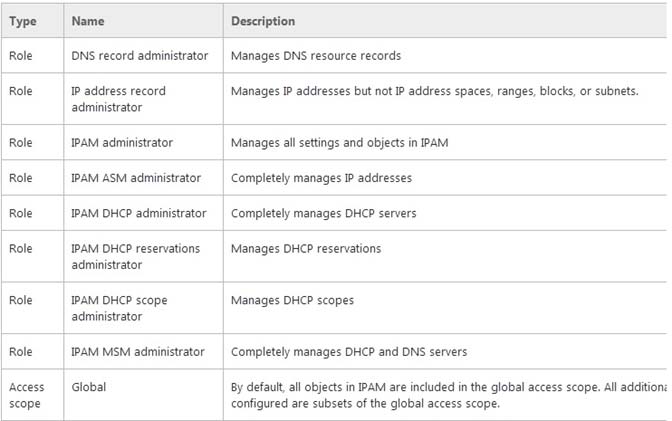
Reference: What's New in IPAM
D
The IPAM DHCP administrator role completely manages DHCP servers.

Reference: What's New in IPAM
send
light_mode
delete
Question #38
Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 and a member server named
Server1. Server1 has the IP Address Management (IPAM) Server feature installed.
On Dc1, you configure Windows Firewall to allow all of the necessary inbound ports for IPAM.
On Server1, you open Server Manager as shown in the exhibit. (Click the Exhibit button.)
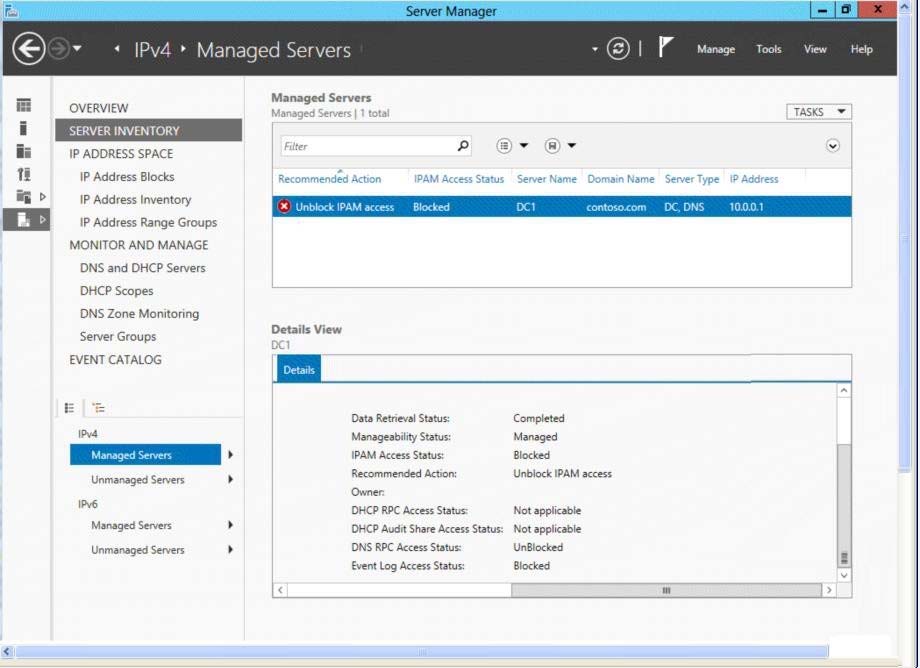
You need to ensure that you can use IPAM on Server1 to manage DNS on DC1.
What should you do?
Server1. Server1 has the IP Address Management (IPAM) Server feature installed.
On Dc1, you configure Windows Firewall to allow all of the necessary inbound ports for IPAM.
On Server1, you open Server Manager as shown in the exhibit. (Click the Exhibit button.)

You need to ensure that you can use IPAM on Server1 to manage DNS on DC1.
What should you do?
- AModify the outbound firewall rules on Server1.
- BModify the inbound firewall rules on Server1.
- CAdd Server1 to the Remote Management Users group.
- DAdd Server1 to the Event Log Readers group.
Correct Answer:
D
To access configuration data and server event logs, the IPAM server must be a member of the domain IPAM Users Group (IPAMUG). The IPAM server must also be a member of the Event Log Readers security group.
Note: The computer account of the IPAM server must be a member of the Event Log Readers security group.
Reference: Manually Configure DC and NPS Access Settings.
http://technet.microsoft.com/en-us/library/jj878317.aspx
http://technet.microsoft.com/en-us/library/jj878313.aspx
D
To access configuration data and server event logs, the IPAM server must be a member of the domain IPAM Users Group (IPAMUG). The IPAM server must also be a member of the Event Log Readers security group.
Note: The computer account of the IPAM server must be a member of the Event Log Readers security group.
Reference: Manually Configure DC and NPS Access Settings.
http://technet.microsoft.com/en-us/library/jj878317.aspx
http://technet.microsoft.com/en-us/library/jj878313.aspx
send
light_mode
delete
Question #39
You have a server named SCI that runs a Server Core Installation of Windows Server 2012 R2. Shadow copies are enabled on all volumes.
You need to delete a specific shadow copy. The solution must minimize server downtime.
Which tool should you use?
You need to delete a specific shadow copy. The solution must minimize server downtime.
Which tool should you use?
- AShadow
- BDiskshadow
- CWbadmin
- DDiskpart
Correct Answer:
B
DiskShadow.exe is a tool that exposes the functionality offered by the Volume Shadow Copy Service (VSS).
The diskshadow command delete shadows deletes shadow copies.
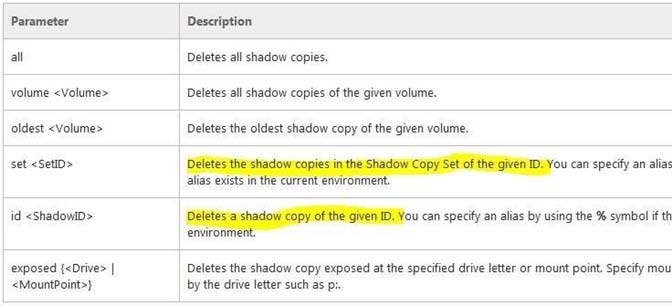
References: Technet, Diskshadow -
https://technet.microsoft.com/en-us/library/cc772172(v=ws.11).aspx
B
DiskShadow.exe is a tool that exposes the functionality offered by the Volume Shadow Copy Service (VSS).
The diskshadow command delete shadows deletes shadow copies.

References: Technet, Diskshadow -
https://technet.microsoft.com/en-us/library/cc772172(v=ws.11).aspx
send
light_mode
delete
Question #40
You have 20 servers that run Windows Server 2012 R2.
You need to create a Windows PowerShell script that registers each server in Microsoft Azure Backup and sets an encryption passphrase.
Which two PowerShell cmdlets should you run in the script? (Each correct answer presents part of the solution. Choose two.)
You need to create a Windows PowerShell script that registers each server in Microsoft Azure Backup and sets an encryption passphrase.
Which two PowerShell cmdlets should you run in the script? (Each correct answer presents part of the solution. Choose two.)
- ANew-OBPolicy
- BNew-OBRetentionPolicy
- CAdd-OBFileSpec
- DStart-OBRegistration
- ESet OBMachineSetting
Correct Answer:
DE
D. Start-OBRegistration -
Registers the current computer with Windows Azure Online Backup using the credentials (username and password) created during enrollment.
E. The Set-OBMachineSetting cmdlet sets a OBMachineSetting object for the server that includes proxy server settings for accessing the internet, network bandwidth throttling settings, and the encryption passphrase that is required to decrypt the files during recovery to another server.
Incorrect:
Not C. TheAdd-OBFileSpeccmdlet adds theOBFileSpecobject, which specifies the items to include or exclude from a backup, to the backup policy
(OBPolicyobject). TheOBFileSpecobject can include or exclude multiple files, folders, or volumes. T
Reference: Start-OBRegistration; Set OBMachineSetting
http://technet.microsoft.com/en-us/library/hh770398.aspx
http://technet.microsoft.com/en-us/library/hh770409.aspx
DE
D. Start-OBRegistration -
Registers the current computer with Windows Azure Online Backup using the credentials (username and password) created during enrollment.
E. The Set-OBMachineSetting cmdlet sets a OBMachineSetting object for the server that includes proxy server settings for accessing the internet, network bandwidth throttling settings, and the encryption passphrase that is required to decrypt the files during recovery to another server.
Incorrect:
Not C. TheAdd-OBFileSpeccmdlet adds theOBFileSpecobject, which specifies the items to include or exclude from a backup, to the backup policy
(OBPolicyobject). TheOBFileSpecobject can include or exclude multiple files, folders, or volumes. T
Reference: Start-OBRegistration; Set OBMachineSetting
http://technet.microsoft.com/en-us/library/hh770398.aspx
http://technet.microsoft.com/en-us/library/hh770409.aspx
send
light_mode
delete
All Pages
