Microsoft 70-342 Exam Practice Questions (P. 5)
- Full Access (191 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #21
DRAG DROP -
You have an Exchange Server 2013 organization.
Your company identifies the following security requirements:
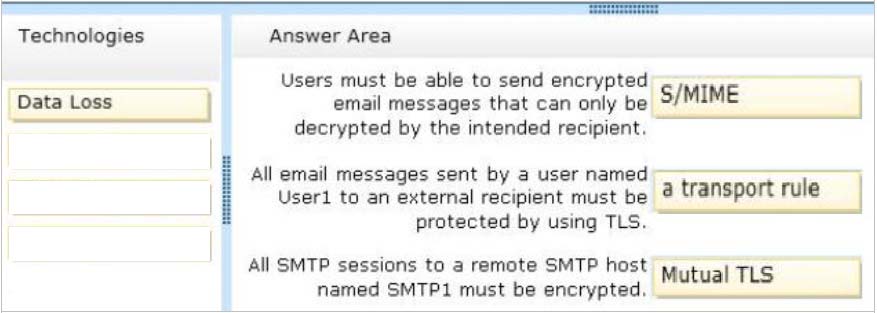
✑ Users must be able to send encrypted email messages that can only be decrypted by the intended recipient.
✑ All email messages sent by a user named User1 to an external recipient must be protected by using TLS.
✑ All SMTP sessions to a remote SMTP host named SMTP1 must be encrypted.
You need to recommend which technology must be used to meet each requirement.
Which technologies should you recommend? (To answer, drag the appropriate technologies to the requirements in the answer area. Each technology may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)
Select and Place:
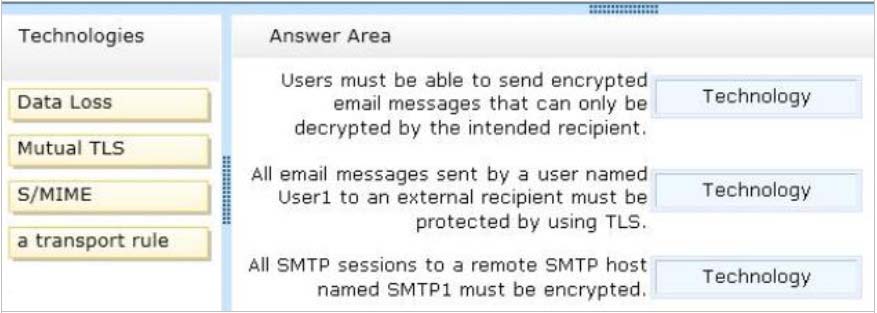
You have an Exchange Server 2013 organization.
Your company identifies the following security requirements:
✑ Users must be able to send encrypted email messages that can only be decrypted by the intended recipient.
✑ All email messages sent by a user named User1 to an external recipient must be protected by using TLS.
✑ All SMTP sessions to a remote SMTP host named SMTP1 must be encrypted.
You need to recommend which technology must be used to meet each requirement.
Which technologies should you recommend? (To answer, drag the appropriate technologies to the requirements in the answer area. Each technology may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)
Select and Place:

send
light_mode
delete
Question #22
HOTSPOT -
Your company has a main office and a disaster recovery site. An Active Directory site named MainSite exists for the main office. An Active Directory site named
DRSite exists for the disaster recovery site. The two sites connect to each other by using a WAN link. All users work in the main office.
You have an Exchange Server 2013 organization. The organization contains six servers. The servers are configured as shown in the following table.

All of the Mailbox servers are members of a database availability group (DAG) named DAG1.
After a WAN link failure, you discover that all of the active mailbox database copies are located on MBX3, even though MBX1 and MBX2 are still running.
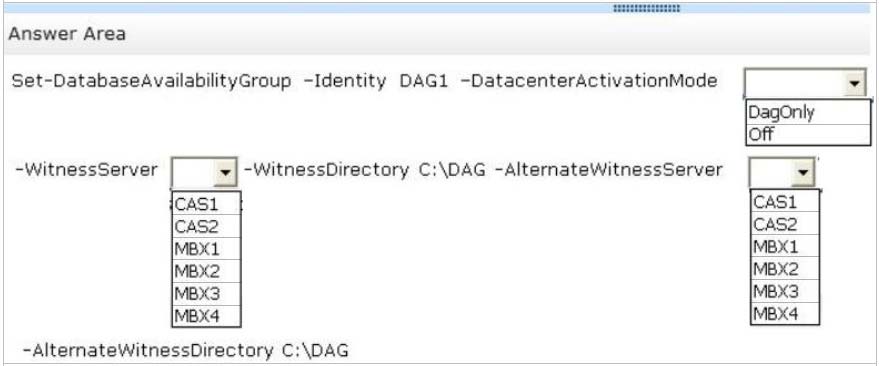
You need to prevent an automatic failover of DAG1 if the WAN link between the two sites fails but the servers in both sites are still running.
The solution must prevent two active copies of the same database.
What should you do? (To answer, select the appropriate options in the answer area.)
Hot Area:
Your company has a main office and a disaster recovery site. An Active Directory site named MainSite exists for the main office. An Active Directory site named
DRSite exists for the disaster recovery site. The two sites connect to each other by using a WAN link. All users work in the main office.
You have an Exchange Server 2013 organization. The organization contains six servers. The servers are configured as shown in the following table.

All of the Mailbox servers are members of a database availability group (DAG) named DAG1.
After a WAN link failure, you discover that all of the active mailbox database copies are located on MBX3, even though MBX1 and MBX2 are still running.
You need to prevent an automatic failover of DAG1 if the WAN link between the two sites fails but the servers in both sites are still running.
The solution must prevent two active copies of the same database.
What should you do? (To answer, select the appropriate options in the answer area.)
Hot Area:

Correct Answer:
Note:
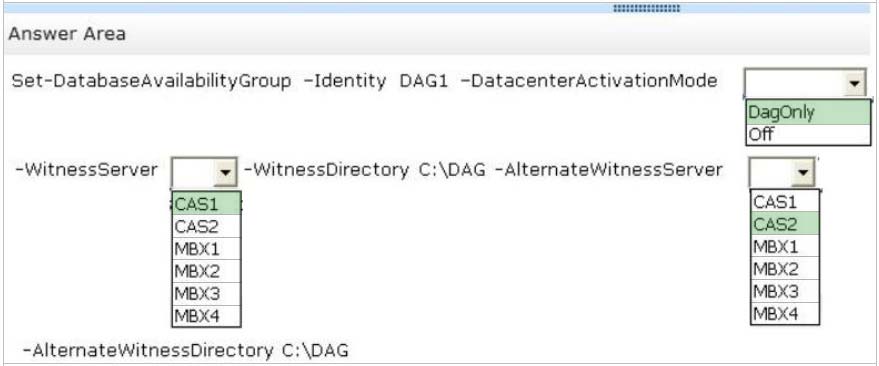
Set-DatabaseAvailabilityGroup -
The Set-DatabaseAvailabilityGroup cmdlet enables you to manage DAG properties that can't be managed from the Exchange Administration Center (EAC), such as configuring network discovery, selecting the TCP port used for replication, and enabling datacenter activation coordination (DAC) mode.
Parameters include:
✑ DatacenterActivationMode
The DatacenterActivationMode parameter specifies whether datacenter activation mode is disabled (Off) or enabled for the DAG (DagOnly).
✑ WitnessServer
The WitnessServer parameter specifies the name of a server that will act as a witness for the DAG. The server specified can't be a member of the DAG.
✑ AlternateWitnessServer
The AlternateWitnessServer parameter specifies the name of an alternate server that's used to store file share witness data. The specified server must not be a member of the DAG that's configured to use it. This parameter is used only as part of a datacenter switchover process. If the DAG is extended across multiple datacenters in a site resilience configuration, we recommend preconfiguring the alternate witness server and directory.

Note:
Set-DatabaseAvailabilityGroup -
The Set-DatabaseAvailabilityGroup cmdlet enables you to manage DAG properties that can't be managed from the Exchange Administration Center (EAC), such as configuring network discovery, selecting the TCP port used for replication, and enabling datacenter activation coordination (DAC) mode.
Parameters include:
✑ DatacenterActivationMode
The DatacenterActivationMode parameter specifies whether datacenter activation mode is disabled (Off) or enabled for the DAG (DagOnly).
✑ WitnessServer
The WitnessServer parameter specifies the name of a server that will act as a witness for the DAG. The server specified can't be a member of the DAG.
✑ AlternateWitnessServer
The AlternateWitnessServer parameter specifies the name of an alternate server that's used to store file share witness data. The specified server must not be a member of the DAG that's configured to use it. This parameter is used only as part of a datacenter switchover process. If the DAG is extended across multiple datacenters in a site resilience configuration, we recommend preconfiguring the alternate witness server and directory.
send
light_mode
delete
Question #23
You have an Exchange Server 2010 organization that contains three servers. The servers are configured as shown in the following table.
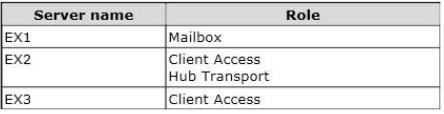
Microsoft Outlook is configured to connect to an FQDN of mail.adatum.com. Mail.adatum.com resolves to the IP address of a Layer 7 hardware load balancer. The hardware load balancer is configured to send traffic to EX2 and EX3.
You deploy an Exchange Server 2013 Mailbox server named EX4 and an Exchange Server 2013 Client Access server named EX5.
You plan to migrate all mailboxes to Exchange Server 2013.
You need to recommend a solution to ensure that users can access their mailbox on EX1 or EX4 during the migration.
What should you do?

Microsoft Outlook is configured to connect to an FQDN of mail.adatum.com. Mail.adatum.com resolves to the IP address of a Layer 7 hardware load balancer. The hardware load balancer is configured to send traffic to EX2 and EX3.
You deploy an Exchange Server 2013 Mailbox server named EX4 and an Exchange Server 2013 Client Access server named EX5.
You plan to migrate all mailboxes to Exchange Server 2013.
You need to recommend a solution to ensure that users can access their mailbox on EX1 or EX4 during the migration.
What should you do?
- ACreate a Client Access server array that contains EX1 and EX5.
- BModify the autodiscover.contoso.com resource record to point to EX5.
- CModify the properties of the hardware load balancer to point to EX5.
- DCreate a DNS record named legacy.contoso.com in the internal DNS zone.
Correct Answer:
C
Note: So what is the Client Access server in Exchange 2013? The Client Access server role is comprised of three components, client protocols, SMTP, and a UM
Call Router. The CAS role is a thin, protocol session stateless server that is organized into a load balanced configuration. Unlike previous versions, session affinity is not required at the load balancer (but you still want a load balancer to handle connection management policies and health checking). This is because logic now exists in CAS to authenticate the request, and then route the request to the Mailbox server that hosts the active copy of the mailbox database.
The Mailbox server role now hosts all the components and/or protocols that process, render and store the data. No clients will ever connect directly to the Mailbox server role; all client connections are handled by the Client Access server role.
Reference: Exchange 2013 Server Role Architecture
C
Note: So what is the Client Access server in Exchange 2013? The Client Access server role is comprised of three components, client protocols, SMTP, and a UM
Call Router. The CAS role is a thin, protocol session stateless server that is organized into a load balanced configuration. Unlike previous versions, session affinity is not required at the load balancer (but you still want a load balancer to handle connection management policies and health checking). This is because logic now exists in CAS to authenticate the request, and then route the request to the Mailbox server that hosts the active copy of the mailbox database.
The Mailbox server role now hosts all the components and/or protocols that process, render and store the data. No clients will ever connect directly to the Mailbox server role; all client connections are handled by the Client Access server role.
Reference: Exchange 2013 Server Role Architecture
send
light_mode
delete
Question #24
Your company has three data centers. The data centers are located in Montreal, New York, and Seattle.
You have an Exchange Server 2013 organization that contains six servers. The servers are configured as shown in the following table.
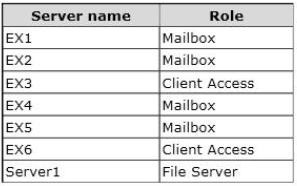
The organization is configured as shown in the following exhibit. (Click the Exhibit button.)
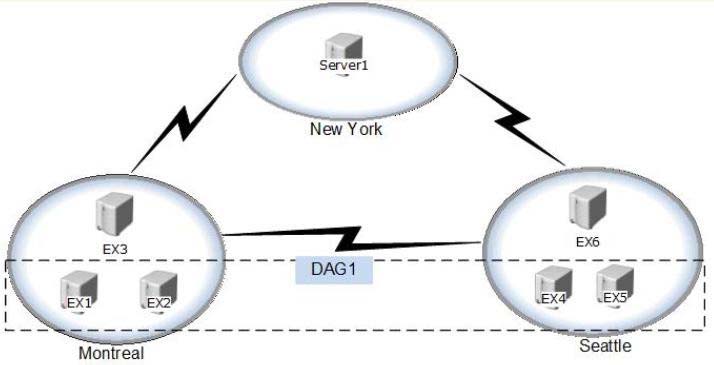
The file share witness for DAG1 is located on EX3.
You plan to implement site resiliency and use a single name space named mail.contoso.com.
You need to recommend a solution to minimize the amount of time that the Exchange Server services are unavailable if either the data center in Montreal or the data center in Seattle fails.
Which two tasks should you recommend performing? (Each correct answer presents part of solution. Choose two.)
You have an Exchange Server 2013 organization that contains six servers. The servers are configured as shown in the following table.

The organization is configured as shown in the following exhibit. (Click the Exhibit button.)

The file share witness for DAG1 is located on EX3.
You plan to implement site resiliency and use a single name space named mail.contoso.com.
You need to recommend a solution to minimize the amount of time that the Exchange Server services are unavailable if either the data center in Montreal or the data center in Seattle fails.
Which two tasks should you recommend performing? (Each correct answer presents part of solution. Choose two.)
- ADeploy a hardware load balancer to EX3 and EX6.
- BCreate two DNS host (A) records for mail.contoso.com.
- CConfigure EX6 as an alternate file share witness.
- DMove the file share witness to Server1. AD
Correct Answer:
Explanation
When a DAG has been deployed across two datacenters, a new configuration option in Exchange 2013 is to use a third location for hosting the witness server. If your organization has a third location with a network infrastructure that is isolated from network failures that affect the two datacenters in which your DAG is deployed, then you can deploy the DAG's witness server in that third location, thereby configuring your DAG with the ability automatically failover databases to the other datacenter in response to a datacenter-level failure event.
By creating two DNS host (A) records for mail.contoso.com, we can use DNS Round Robin to distribute connections between the two CAS servers. If one server goes down, a client will attempt to connect to the CAS server specified in the second DNS record.
Explanation
When a DAG has been deployed across two datacenters, a new configuration option in Exchange 2013 is to use a third location for hosting the witness server. If your organization has a third location with a network infrastructure that is isolated from network failures that affect the two datacenters in which your DAG is deployed, then you can deploy the DAG's witness server in that third location, thereby configuring your DAG with the ability automatically failover databases to the other datacenter in response to a datacenter-level failure event.
By creating two DNS host (A) records for mail.contoso.com, we can use DNS Round Robin to distribute connections between the two CAS servers. If one server goes down, a client will attempt to connect to the CAS server specified in the second DNS record.
send
light_mode
delete
Question #25
You have an Exchange Server 2013 organization.
You create a data loss prevention (DLP) policy. The mode of the DLP policy is set to Enforce.
You need to ensure that email messages containing social security numbers from the United States are blocked.
Which two possible rules achieve this goal? (Each correct answer presents a complete solution. Choose two.)
You create a data loss prevention (DLP) policy. The mode of the DLP policy is set to Enforce.
You need to ensure that email messages containing social security numbers from the United States are blocked.
Which two possible rules achieve this goal? (Each correct answer presents a complete solution. Choose two.)
- AU.S. State Breach: Allow Override
- BU.S. State Breach: Scan email sent outside - low count
- CU.S. State Breach: Scan email sent outside - high count
- DU.S. State Breach: Scan text limit exceeded
- EU.S. State Breach: Attachment not supported
Correct Answer:
BC
Note:
* In Microsoft Exchange Server 2013, you can use data loss prevention (DLP) policy templates to help meet the messaging policy and compliance needs of your organization. These templates contain pre-built sets of rules that can help you manage message data that is associated with several common legal and regulatory requirements.
* DLP policy templates in Exchange include:
U.S. State Breach Notification Laws
Helps detect the presence of information subject to U.S. State Breach Notification Laws, including data like social security and credit card numbers.
BC
Note:
* In Microsoft Exchange Server 2013, you can use data loss prevention (DLP) policy templates to help meet the messaging policy and compliance needs of your organization. These templates contain pre-built sets of rules that can help you manage message data that is associated with several common legal and regulatory requirements.
* DLP policy templates in Exchange include:
U.S. State Breach Notification Laws
Helps detect the presence of information subject to U.S. State Breach Notification Laws, including data like social security and credit card numbers.
send
light_mode
delete
All Pages