HP HP0-Y47 Exam Practice Questions (P. 4)
- Full Access (55 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #16
Refer to the exhibit.
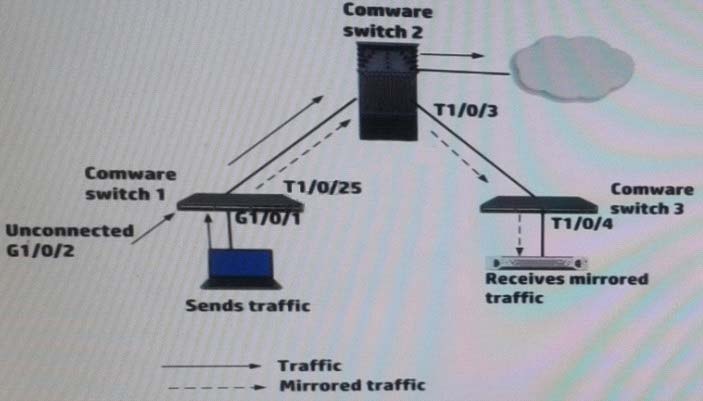
A network administrator up a remote mirroring on the HP Comware switches in the exhibit. The administrator must define several port while entering mirroring- group commands on these switches. Which port should be the reflector port (sometimes called monitor-egress port)?

A network administrator up a remote mirroring on the HP Comware switches in the exhibit. The administrator must define several port while entering mirroring- group commands on these switches. Which port should be the reflector port (sometimes called monitor-egress port)?
- ASwitch 1, G1/0/2
- BSwitch3, T1/0/4
- CSwitch 1, T1/0/25
- DSwitch 1, G1/0/1 B
Correct Answer:
Explanation
Put it in on the switch that receives remote mirrored traffic.
Reference: HP Networking and Cisco CLI Reference Guide
http://h17007.www1.hp.com/docs/interoperability/Cisco/HP-Networking-and-Cisco-CLI-Reference-Guide_June_10_WW_Eng_ltr.pdf
Explanation
Put it in on the switch that receives remote mirrored traffic.
Reference: HP Networking and Cisco CLI Reference Guide
http://h17007.www1.hp.com/docs/interoperability/Cisco/HP-Networking-and-Cisco-CLI-Reference-Guide_June_10_WW_Eng_ltr.pdf
send
light_mode
delete
Question #17
Two HP 10500 Series Switches connect on a 10G fiber link. One of the two fibers in the link breaks, and a broadcast storm occurs. How could a network administrator prevent a problem like this from happening again?
- AConfigure Device Link Detection Protocol (DLDP) on both sides of the link.
- BUse Rapid Per VLAN Spanning Tree Plus (RPVST+) instead of Multiple Spanning Tree Protocol (MSTP).
- CImplement sFlow or NetStream on both sides of the link, setting the collector to an Intelligent Management Center (IMC) server.
- DAdd another 10G link and create a link aggregation group on each switch that includes both links.
Correct Answer:
A
* The Device Link Detection Protocol (DLDP) can detect the link status of a fiber cable or twisted pair. Upon detecting a unidirectional link, DLDP shuts down the faulty port automatically or prompts the user to do so manually depending on the configuration to avoid forwarding problems.
* As a link layer protocol, DLDP can identify remote devices, detect unidirectional links, and shut down unreachable ports at the link layer.
/ If both ends of a link are operating normally at the physical layer, DLDP detects whether the link is correctly connected at the link layer and whether the two ends can exchange packets properly. This is beyond the capability of the auto-negotiation mechanism at the physical layer.
/ In conjunction with the physical layer auto-negotiation mechanism where physical signals and faults can be detected, DLDP can detect and shut down physically/ logically unidirectional links.
2 DLDP Implementation
Reference: DLDP Technology White Paper
http://www.h3c.com/portal/Products___Solutions/Technology/LAN/Technology_White_Paper/200812/623012_57_0.htm
A
* The Device Link Detection Protocol (DLDP) can detect the link status of a fiber cable or twisted pair. Upon detecting a unidirectional link, DLDP shuts down the faulty port automatically or prompts the user to do so manually depending on the configuration to avoid forwarding problems.
* As a link layer protocol, DLDP can identify remote devices, detect unidirectional links, and shut down unreachable ports at the link layer.
/ If both ends of a link are operating normally at the physical layer, DLDP detects whether the link is correctly connected at the link layer and whether the two ends can exchange packets properly. This is beyond the capability of the auto-negotiation mechanism at the physical layer.
/ In conjunction with the physical layer auto-negotiation mechanism where physical signals and faults can be detected, DLDP can detect and shut down physically/ logically unidirectional links.
2 DLDP Implementation
Reference: DLDP Technology White Paper
http://www.h3c.com/portal/Products___Solutions/Technology/LAN/Technology_White_Paper/200812/623012_57_0.htm
send
light_mode
delete
Question #18
HP Comware Switch 1 connects to switch 2 on GigabitEthernet 1/0/1. Switch 2 implements an inbound rate limit of 600 Mbps. The network administrator wants switch 1 to buffer traffic that exceeds the Switch 2 rate limit of 600 Mbps and send the traffic at 600 Mbps. All traffic has the same 802.1p priority and is forwarded in priority queue 2.
What should the administrator apply to the Switch 1 interface GigabitEthernet 1/0/1?
What should the administrator apply to the Switch 1 interface GigabitEthernet 1/0/1?
- AA line rate limit of 600 Mbps on queue 2
- BA QoS policy with a classifier that matches all traffic and a CAR behavior that sets a CIR of 600 Mbps
- CA weighted random early discard (WRED) table with a limit of 600 for queue 2
- DA traffic shaping rate limit of 600 Mbps on queue 2
Correct Answer:
A
The line rate of a physical interface specifies the maximum rate of incoming packets or outgoing packets.
Note: Configuring the line rate -
Perform the following steps:
1. Enter system view by using the following command:
system-view
2. Enter interface view.
interface interface-type interface-number
3. Configure the line rate for the interface. Use the following command: qos lr outbound cir committed-informationrate [ cbs committed-burst-size [ ebs excessburst- size ] ]
Reference: HP 6600 Router Series - Configuring Traffic Policing/Traffic Shaping/Line Rate http://h20564.www2.hp.com/hpsc/doc/public/display?docId=emr_na-c03146192&sp4ts.oid=5179297#N101D6
A
The line rate of a physical interface specifies the maximum rate of incoming packets or outgoing packets.
Note: Configuring the line rate -
Perform the following steps:
1. Enter system view by using the following command:
system-view
2. Enter interface view.
interface interface-type interface-number
3. Configure the line rate for the interface. Use the following command: qos lr outbound cir committed-informationrate [ cbs committed-burst-size [ ebs excessburst- size ] ]
Reference: HP 6600 Router Series - Configuring Traffic Policing/Traffic Shaping/Line Rate http://h20564.www2.hp.com/hpsc/doc/public/display?docId=emr_na-c03146192&sp4ts.oid=5179297#N101D6
send
light_mode
delete
Question #19
What distinguishes an HP switch with a CLOS fabric from an HP switch with a crossbar fabric?
- AThe CLOS fabric can integrate with a virtual switch, which is deployed in a virtualized server.
- BThe CLOS fabric is a requirement for an Intelligent Resilient Framework (IRF) virtual switch with more than two members.
- CThe CLOS fabric can dynamically shut down power to unused switch ports, proving better energy efficiency.
- DThe CLOS fabric can dynamically load-balance internal traffic over many paths, helping the switch support 40G/100G.
Correct Answer:
D
In a modern Clos topology, every lower-tier switch is connected to each of the top-tier switches in a full-mesh topology. If there isn't any oversubscription taking place between the lower-tier switches and their uplinks, then a non-blocking architecture can be achieved. The advantage of the Clos network is you can use a set of identical and inexpensive devices to create the tree and gain high performance and resilience that would otherwise cost must more to construct. To prevent any one uplink path from being chosen, the path is randomly chosen so that the traffic load is evenly distributed between the top-tier switches. If one of the top tier switches were to fail, it only slightly degrades performance through the data center.
Reference: Clos Networks: What's Old Is New Again, What goes around, comes around Clos Networks are back http://www.networkworld.com/article/2226122/cisco-subnet/clos-networks--what-s-old-is-new-again.html
D
In a modern Clos topology, every lower-tier switch is connected to each of the top-tier switches in a full-mesh topology. If there isn't any oversubscription taking place between the lower-tier switches and their uplinks, then a non-blocking architecture can be achieved. The advantage of the Clos network is you can use a set of identical and inexpensive devices to create the tree and gain high performance and resilience that would otherwise cost must more to construct. To prevent any one uplink path from being chosen, the path is randomly chosen so that the traffic load is evenly distributed between the top-tier switches. If one of the top tier switches were to fail, it only slightly degrades performance through the data center.
Reference: Clos Networks: What's Old Is New Again, What goes around, comes around Clos Networks are back http://www.networkworld.com/article/2226122/cisco-subnet/clos-networks--what-s-old-is-new-again.html
send
light_mode
delete
Question #20
A company needs a simple guest access solution. On each HP Provision access layer switch, the network administrator (Web-Auth) to an external Web server.
Which guidelines must the administrator follow while setting up the Web server?
Which guidelines must the administrator follow while setting up the Web server?
- AThe Web server must be able to ping IP addresses in the Web-Auth subnet on each switch.
- BThe server must have a certificate that is signed by a CA certificate loaded on the access layer switches.
- CThe login pages must exactly match template pages provided by HP. with the exception of the logo image.
- DThe login pages must use specific names, which are documented in switch manuals.
Correct Answer:
A
Incorrect -
Not B: No certificate is required.
Not C, D: . Specifying the URL for Web-Auth Pages That Are Stored on an External Web Server
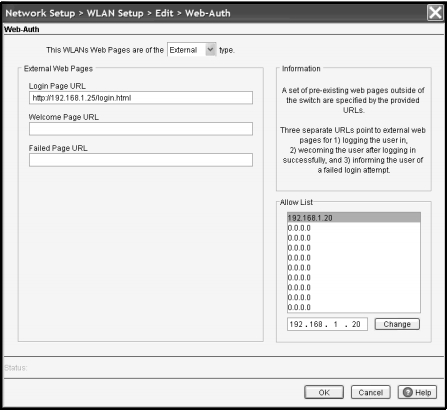
Under External Web Pages, specify the correct URL for each page. a. In the Login Page URL field, specify the URL of the login page, which users see when they try to access a Web site. For example, you might enter a URL such as http://192.168.1.1/login.html or http:// www.yourcompany.com/login.html
.
b. In the Welcome Page URL field, specify the URL of the welcome page that users see if they log in successfully. c. In the Failed Page URL, specify the URL of the page that users see if they do not enter a valid username and password or if a RADIUS server is unavailable.
Reference: Web Authentication for Mobile Users
ftp://ftp.hp.com/pub/networking/software/08-C05-WebAuth.pdf
A
Incorrect -
Not B: No certificate is required.
Not C, D: . Specifying the URL for Web-Auth Pages That Are Stored on an External Web Server

Under External Web Pages, specify the correct URL for each page. a. In the Login Page URL field, specify the URL of the login page, which users see when they try to access a Web site. For example, you might enter a URL such as http://192.168.1.1/login.html or http:// www.yourcompany.com/login.html
.
b. In the Welcome Page URL field, specify the URL of the welcome page that users see if they log in successfully. c. In the Failed Page URL, specify the URL of the page that users see if they do not enter a valid username and password or if a RADIUS server is unavailable.
Reference: Web Authentication for Mobile Users
ftp://ftp.hp.com/pub/networking/software/08-C05-WebAuth.pdf
send
light_mode
delete
All Pages
