CompTIA SY0-501 Exam Practice Questions (P. 3)
- Full Access (1132 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #21
Which of the following types of keys is found in a key escrow?
- APublic
- BPrivate
- CShared
- DSession
Correct Answer:
B
https:/
/www.professormesser.com/security
-
plus/sy0-401/key-escrow-3/
B
https:/
/www.professormesser.com/security
-
plus/sy0-401/key-escrow-3/
send
light_mode
delete
Question #22
A security analyst is reviewing the following output from an IPS:
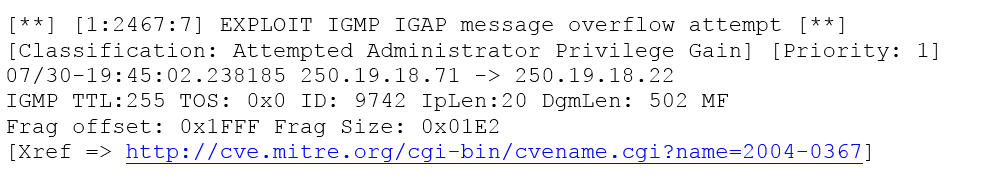
Given this output, which of the following can be concluded? (Choose two.)

Given this output, which of the following can be concluded? (Choose two.)
- AThe source IP of the attack is coming from 250.19.18.22.
- BThe source IP of the attack is coming from 250.19.18.71.
- CThe attacker sent a malformed IGAP packet, triggering the alert.
- DThe attacker sent a malformed TCP packet, triggering the alert.
- EThe TTL value is outside of the expected range, triggering the alert.
Correct Answer:
BC
BC
send
light_mode
delete
Question #23
Despite having implemented password policies, users continue to set the same weak passwords and reuse old passwords. Which of the following technical controls would help prevent these policy violations? (Choose two.)
- APassword expiration
- BPassword length
- CPassword complexity
- DPassword history
- EPassword lockout
Correct Answer:
CD
CD
send
light_mode
delete
Question #24
Which of the following types of cloud infrastructures would allow several organizations with similar structures and interests to realize the benefits of shared storage and resources?
send
light_mode
delete
Question #25
A company is currently using the following configuration:
✑ IAS server with certificate-based EAP-PEAP and MSCHAP
✑ Unencrypted authentication via PAP
A security administrator needs to configure a new wireless setup with the following configurations:
✑ PAP authentication method
✑ PEAP and EAP provide two-factor authentication
Which of the following forms of authentication are being used? (Choose two.)
✑ IAS server with certificate-based EAP-PEAP and MSCHAP
✑ Unencrypted authentication via PAP
A security administrator needs to configure a new wireless setup with the following configurations:
✑ PAP authentication method
✑ PEAP and EAP provide two-factor authentication
Which of the following forms of authentication are being used? (Choose two.)
send
light_mode
delete
Question #26
An auditor wants to test the security posture of an organization by running a tool that will display the following:

Which of the following commands should be used?

Which of the following commands should be used?
send
light_mode
delete
Question #27
A company determines that it is prohibitively expensive to become compliant with new credit card regulations. Instead, the company decides to purchase insurance to cover the cost of any potential loss. Which of the following is the company doing?
- ATransferring the risk
- BAccepting the risk
- CAvoiding the risk
- DMigrating the risk
Correct Answer:
A
A
send
light_mode
delete
Question #28
A company is using a mobile device deployment model in which employees use their personal devices for work at their own discretion. Some of the problems the company is encountering include the following:
✑ There is no standardization.
✑ Employees ask for reimbursement for their devices.
✑ Employees do not replace their devices often enough to keep them running efficiently.
✑ The company does not have enough control over the devices.
Which of the following is a deployment model that would help the company overcome these problems?
✑ There is no standardization.
✑ Employees ask for reimbursement for their devices.
✑ Employees do not replace their devices often enough to keep them running efficiently.
✑ The company does not have enough control over the devices.
Which of the following is a deployment model that would help the company overcome these problems?
send
light_mode
delete
Question #29
A botnet has hit a popular website with a massive number of GRE-encapsulated packets to perform a DDoS attack. News outlets discover a certain type of refrigerator was exploited and used to send outbound packets to the website that crashed. To which of the following categories does the refrigerator belong?
send
light_mode
delete
Question #30
Users report the following message appears when browsing to the company's secure site: This website cannot be trusted. Which of the following actions should a security analyst take to resolve these messages? (Choose two.)
- AVerify the certificate has not expired on the server.
- BEnsure the certificate has a .pfx extension on the server.
- CUpdate the root certificate into the client computer certificate store.
- DInstall the updated private key on the web server.
- EHave users clear their browsing history and relaunch the session.
Correct Answer:
AC
AC
send
light_mode
delete
All Pages
