CompTIA CS0-002 Exam Practice Questions (P. 5)
- Full Access (422 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #41
The SOC has received reports of slowness across all workstation network segments. The currently installed antivirus has not detected anything, but a different anti-malware product was just downloaded and has revealed a worm is spreading. Which of the following should be the NEXT step in this incident response?
- ASend a sample of the malware to the antivirus vendor and request urgent signature creation.
- BBegin deploying the new anti-malware on all uninfected systems.
- CEnable an ACL on all VLANs to contain each segment.
- DCompile a list of IoCs so the IPS can be updated to halt the spread.Most Voted
Correct Answer:
A
A
send
light_mode
delete
Question #42
A vulnerability assessment solution is hosted in the cloud. This solution will be used as an accurate inventory data source for both the configuration management database and the governance, risk, and compliance tool. An analyst has been asked to automate the data acquisition. Which of the following would be the BEST way to acquire the data?
send
light_mode
delete
Question #43
Which of the following is MOST closely related to the concept of privacy?
- AThe implementation of confidentiality, integrity, and availability
- BA system's ability to protect the confidentiality of sensitive information
- CAn individual's control over personal informationMost Voted
- DA policy implementing strong identity management processes
Correct Answer:
C
C
send
light_mode
delete
Question #44
An organization is focused on restructuring its data governance programs, and an analyst has been tasked with surveying sensitive data within the organization.
Which of the following is the MOST accurate method for the security analyst to complete this assignment?
Which of the following is the MOST accurate method for the security analyst to complete this assignment?
- APerform an enterprise-wide discovery scan.
- BConsult with an internal data custodian.
- CReview enterprise-wide asset inventory.
- DCreate a survey and distribute it to data owners.Most Voted
Correct Answer:
A
A
send
light_mode
delete
Question #45
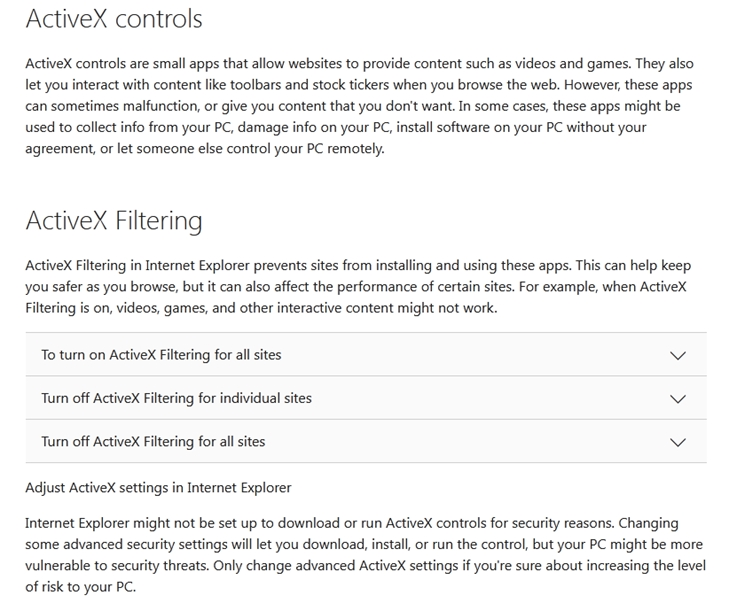
Which of the following is the BEST security practice to prevent ActiveX controls from running malicious code on a user's web application?
- ADeploying HIPS to block malicious ActiveX code
- BInstalling network-based IPS to block malicious ActiveX code
- CAdjusting the web-browser settings to block ActiveX controlsMost Voted
- DConfiguring a firewall to block traffic on ports that use ActiveX controls
Correct Answer:
C
Reference:
https://support.microsoft.com/en-us/windows/use-activex-controls-for-internet-explorer-11-25738d05-d357-39b4-eb2f-fdd074bbf347
C
Reference:
https://support.microsoft.com/en-us/windows/use-activex-controls-for-internet-explorer-11-25738d05-d357-39b4-eb2f-fdd074bbf347

send
light_mode
delete
Question #46
A company wants to ensure confidential data from its storage media files is sanitized so the drives cannot be reused. Which of the following is the BEST approach?
send
light_mode
delete
Question #47
During the forensic analysis of a compromised machine, a security analyst discovers some binaries that are exhibiting abnormal behaviors. After extracting the strings, the analyst finds unexpected content. Which of the following is the NEXT step the analyst should take?
- AValidate the binaries' hashes from a trusted source.
- BUse file integrity monitoring to validate the digital signature.
- CRun an antivirus against the binaries to check for malware.Most Voted
- DOnly allow whitelisted binaries to execute.
Correct Answer:
A
A
send
light_mode
delete
Question #48
An organization recently discovered that spreadsheet files containing sensitive financial data were improperly stored on a web server. The management team wants to find out if any of these files were downloaded by public users accessing the server. The results should be written to a text file and should include the date, time, and IP address associated with any spreadsheet downloads. The web server's log file is named webserver.log, and the report file name should be accessreport.txt. Following is a sample of the web server's log file:
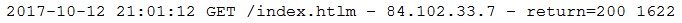
Which of the following commands should be run if an analyst only wants to include entries in which a spreadsheet was successfully downloaded?
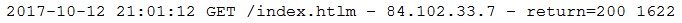
Which of the following commands should be run if an analyst only wants to include entries in which a spreadsheet was successfully downloaded?
- Amore webserver.log | grep *.xls > accessreport.txt
- Bmore webserver.log > grep ג€*xlsג€ | egrep ג€"E 'success' > accessreport.txt
- Cmore webserver.log | grep ג€"E ג€return=200 | xlsג€ > accessreport.txtMost Voted
- Dmore webserver.log | grep ג€"A *.xls < accessreport.txt
Correct Answer:
B
B
send
light_mode
delete
Question #49
A security analyst is running a tool against an executable of an unknown source. The input supplied by the tool to the executable program and the output from the executable are shown below:
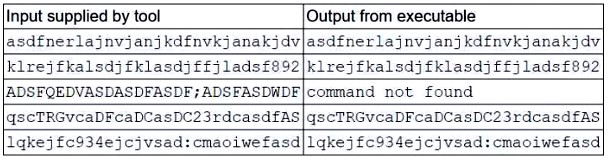
Which of the following should the analyst report after viewing this information?

Which of the following should the analyst report after viewing this information?
- AA dynamic library that is needed by the executable is missing.
- BInput can be crafted to trigger an injection attack in the executable.Most Voted
- CThe tool caused a buffer overflow in the executable's memory.
- DThe executable attempted to execute a malicious command.
Correct Answer:
D
D
send
light_mode
delete
Question #50
A Chief Information Security Officer (CISO) is concerned about new privacy regulations that apply to the company. The CISO has tasked a security analyst with finding the proper control functions to verify that a user's data is not altered without the user's consent. Which of the following would be an appropriate course of action?
- AAutomate the use of a hashing algorithm after verified users make changes to their data.Most Voted
- BUse encryption first and then hash the data at regular, defined times.
- CUse a DLP product to monitor the data sets for unauthorized edits and changes.
- DReplicate the data sets at regular intervals and continuously compare the copies for unauthorized changes.
Correct Answer:
A
A
send
light_mode
delete
All Pages
