CompTIA CS0-002 Exam Practice Questions (P. 3)
- Full Access (422 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #21
A security team implemented a SIEM as part of its security-monitoring program. There is a requirement to integrate a number of sources into the SIEM to provide better context relative to the events being processed. Which of the following BEST describes the result the security team hopes to accomplish by adding these sources?
- AData enrichmentMost Voted
- BContinuous integration
- CMachine learning
- DWorkflow orchestration
Correct Answer:
A
A
 GPT-4o - Answer
GPT-4o - Answer
Incorporating various sources into a SIEM system is primarily about enriching the data it processes. This means integrating additional context and details to enhance the accuracy and usefulness of security-related insights provided by the SIEM. Data enrichment helps in building a more comprehensive security outlook by causally linking diverse information bits, which significantly improves event analysis and threat detection capabilities.
send
light_mode
delete
Question #22
Which of the following organizational initiatives would be MOST impacted by data sovereignty issues?
- AMoving to a cloud-based environmentMost Voted
- BMigrating to locally hosted virtual servers
- CImplementing non-repudiation controls
- DEncrypting local database queries
Correct Answer:
A
A
send
light_mode
delete
Question #23
A help desk technician inadvertently sent the credentials of the company's CRM in cleartext to an employee's personal email account. The technician then reset the employee's account using the appropriate process and the employee's corporate email, and notified the security team of the incident. According to the incident response procedure, which of the following should the security team do NEXT?
- AContact the CRM vendor.Most Voted
- BPrepare an incident summary report.
- CPerform postmortem data correlation.
- DUpdate the incident response plan.
Correct Answer:
D
D
send
light_mode
delete
Question #24
Which of the following is MOST dangerous to the client environment during a vulnerability assessment/penetration test?
- AThere is a longer period of time to assess the environment.
- BThe testing is outside the contractual scope.Most Voted
- CThere is a shorter period of time to assess the environment.
- DNo status reports are included with the assessment.
Correct Answer:
C
C
send
light_mode
delete
Question #25
An organization is adopting IoT devices at an increasing rate and will need to account for firmware updates in its vulnerability management programs. Despite the number of devices being deployed, the organization has only focused on software patches so far, leaving hardware-related weaknesses open to compromise.
Which of the following best practices will help the organization to track and deploy trusted firmware updates as part of its vulnerability management programs?
Which of the following best practices will help the organization to track and deploy trusted firmware updates as part of its vulnerability management programs?
- AUtilize threat intelligence to guide risk evaluation activities and implement critical updates after proper testing.Most Voted
- BApply all firmware updates as soon as they are released to mitigate the risk of compromise.
- CSign up for vendor emails and create firmware update change plans for affected devices.
- DImplement an automated solution that detects when vendors release firmware updates and immediately deploy updates to production.
Correct Answer:
D
D
send
light_mode
delete
Question #26
A company's blocklist has outgrown the current technologies in place. The ACLs are at maximum, and the IPS signatures only allow a certain amount of space for domains to be added, creating the need for multiple signatures. Which of the following configuration changes to the existing controls would be the MOST appropriate to improve performance?
- AImplement a host-file-based solution that will use a list of all domains to deny for all machines on the network.
- BCreate an IDS for the current blocklist to determine which domains are showing activity and may need to be removed.
- CReview the current blocklist and prioritize it based on the level of threat severity. Add the domains with the highest severity to the blocklist and remove the lower-severity threats from it.
- DReview the current blocklist to determine which domains can be removed from the list and then update the ACLs and IPS signatures.Most Voted
Correct Answer:
D
D
send
light_mode
delete
Question #27
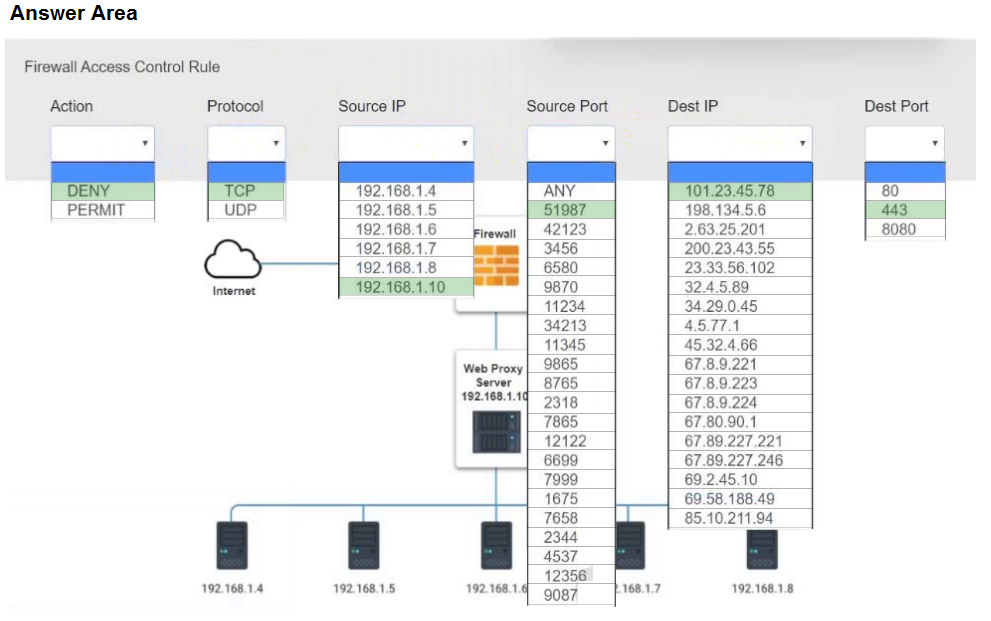
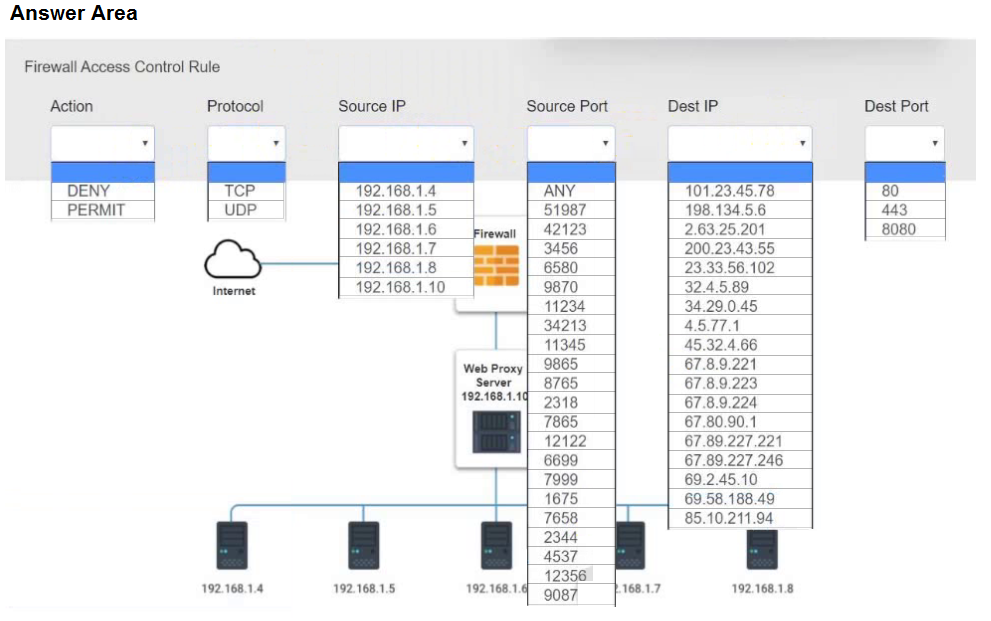
HOTSPOT -
A security analyst suspects that a workstation may be beaconing to a command and control server.
Inspect the logs from the company's web proxy server and the firewall to determine the best course of action to take in order to neutralize the threat with minimum impact to the organization.
INSTRUCTIONS -
Modify the Firewall Access Control rule to mitigate the issue.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
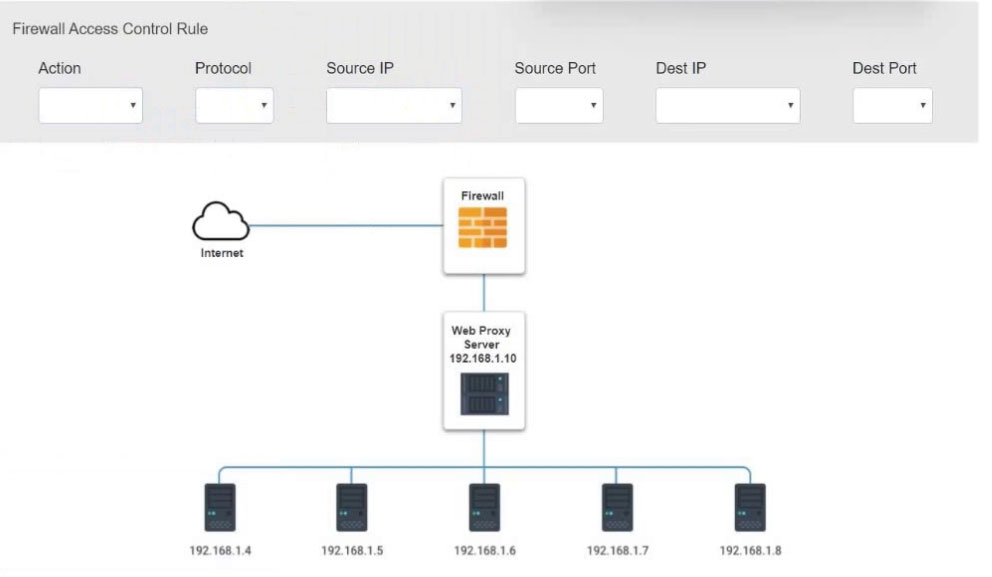
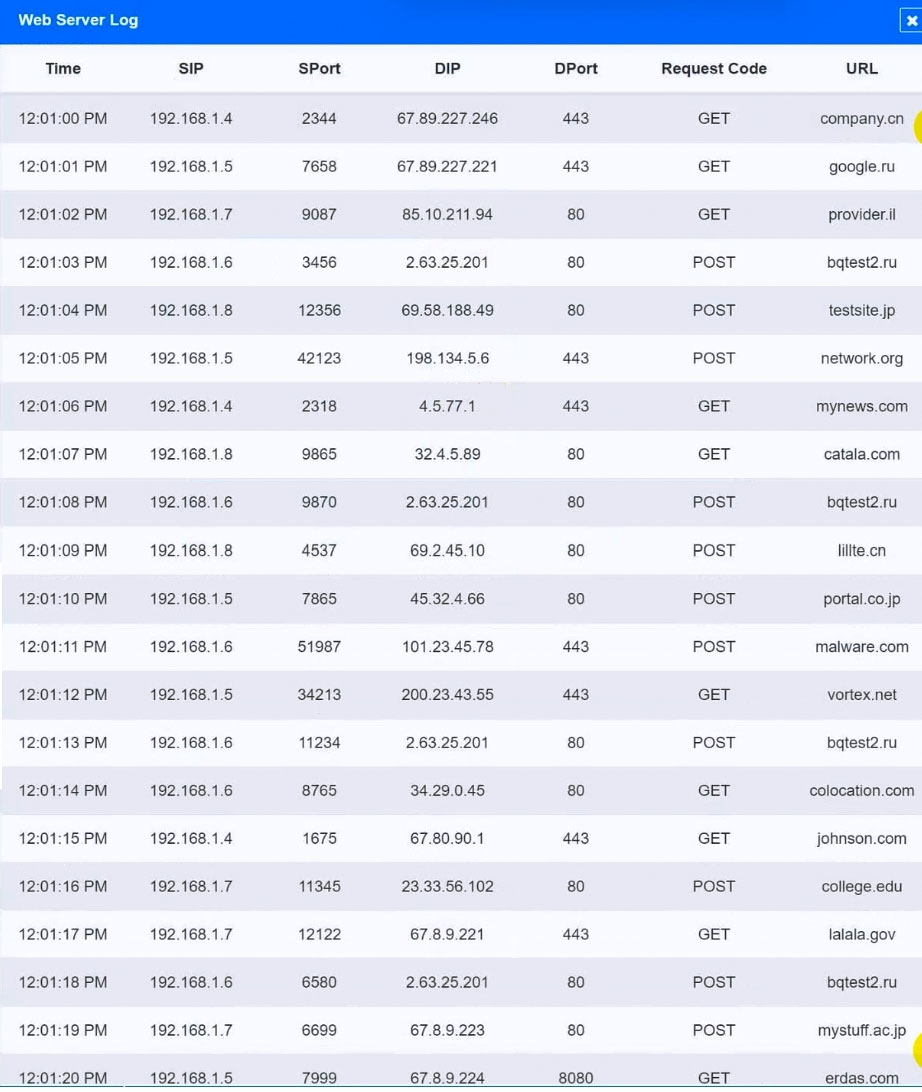
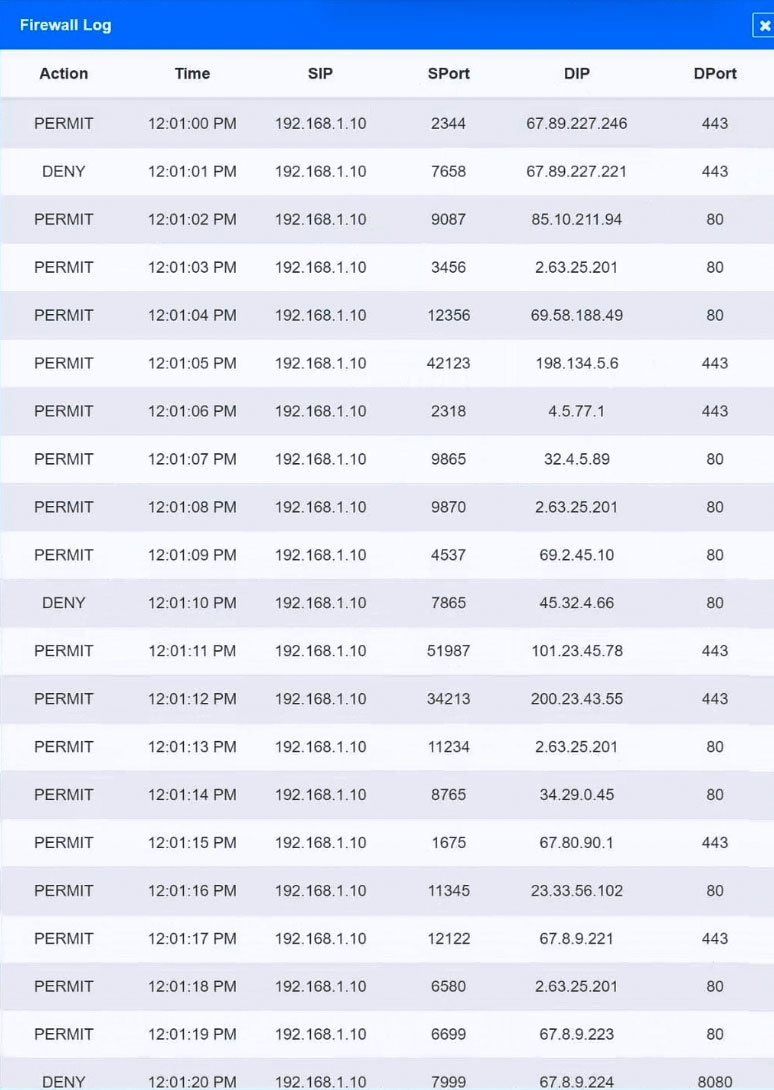
Hot Area:
A security analyst suspects that a workstation may be beaconing to a command and control server.
Inspect the logs from the company's web proxy server and the firewall to determine the best course of action to take in order to neutralize the threat with minimum impact to the organization.
INSTRUCTIONS -
Modify the Firewall Access Control rule to mitigate the issue.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.



Hot Area:

send
light_mode
delete
Question #28
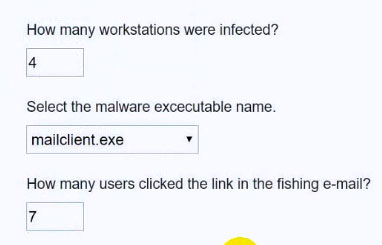
SIMULATION -
Approximately 100 employees at your company have received a phishing email. As a security analyst, you have been tasked with handling this situation.
INSTRUCTIONS -
Review the information provided and determine the following:
1. How many employees clicked on the link in the phishing email?
2. On how many workstations was the malware installed?
3. What is the executable file name of the malware?
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
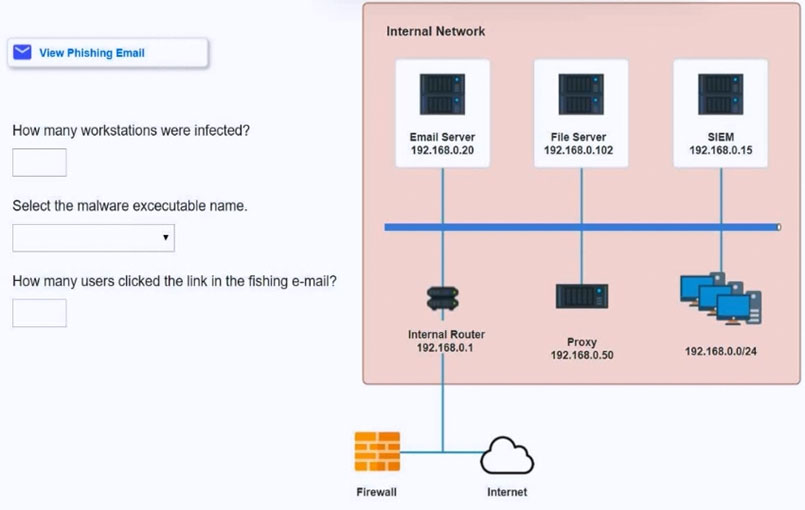
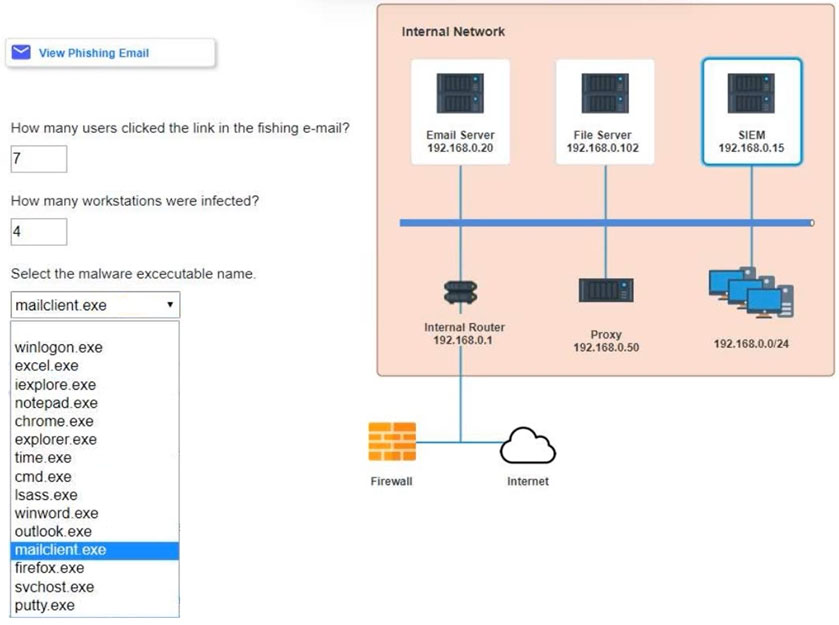
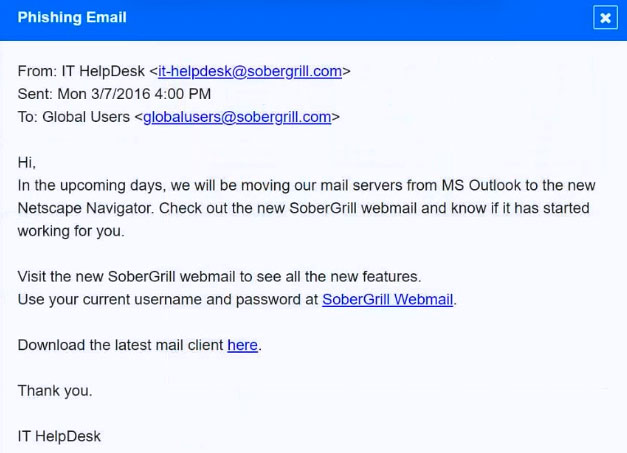
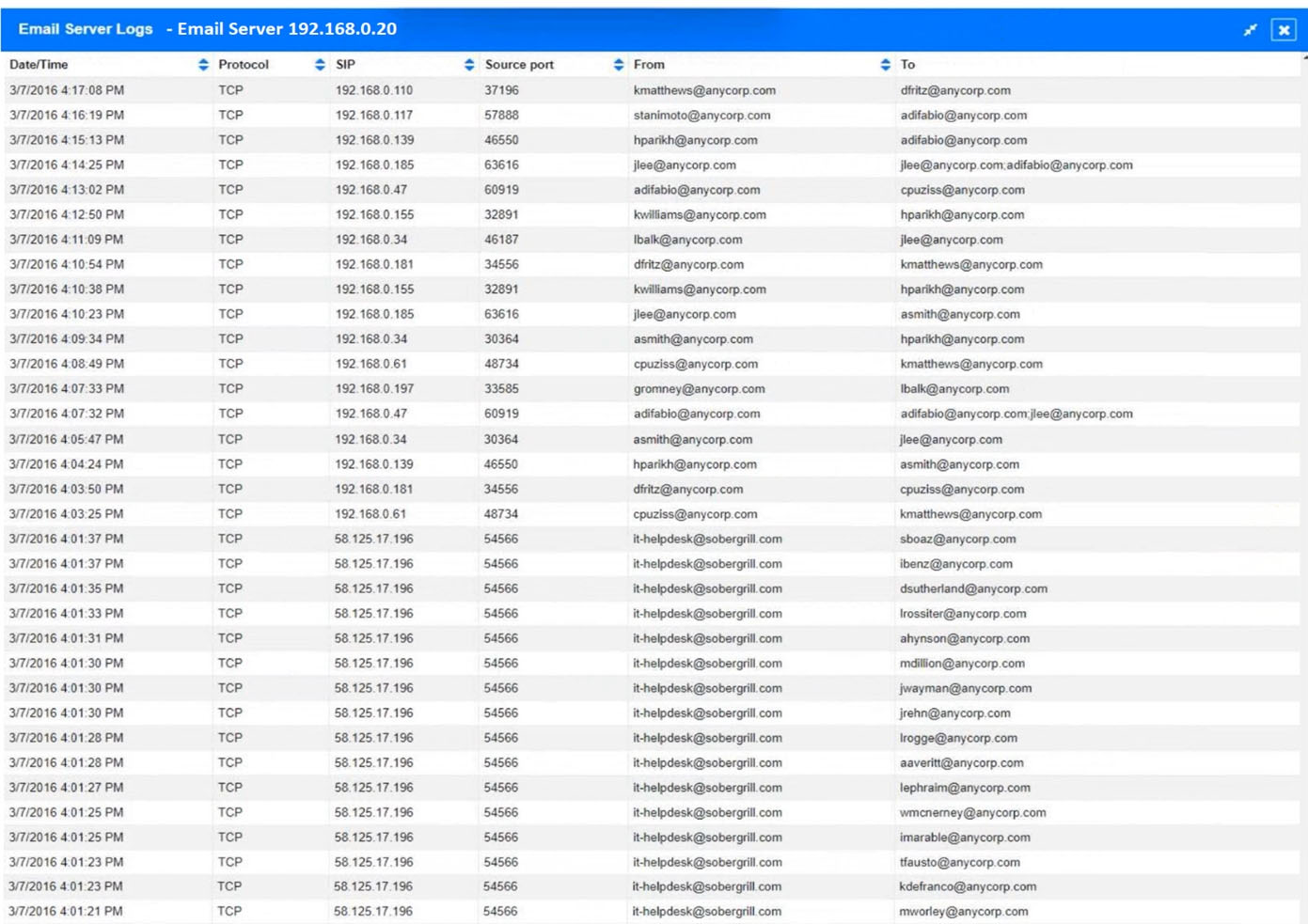
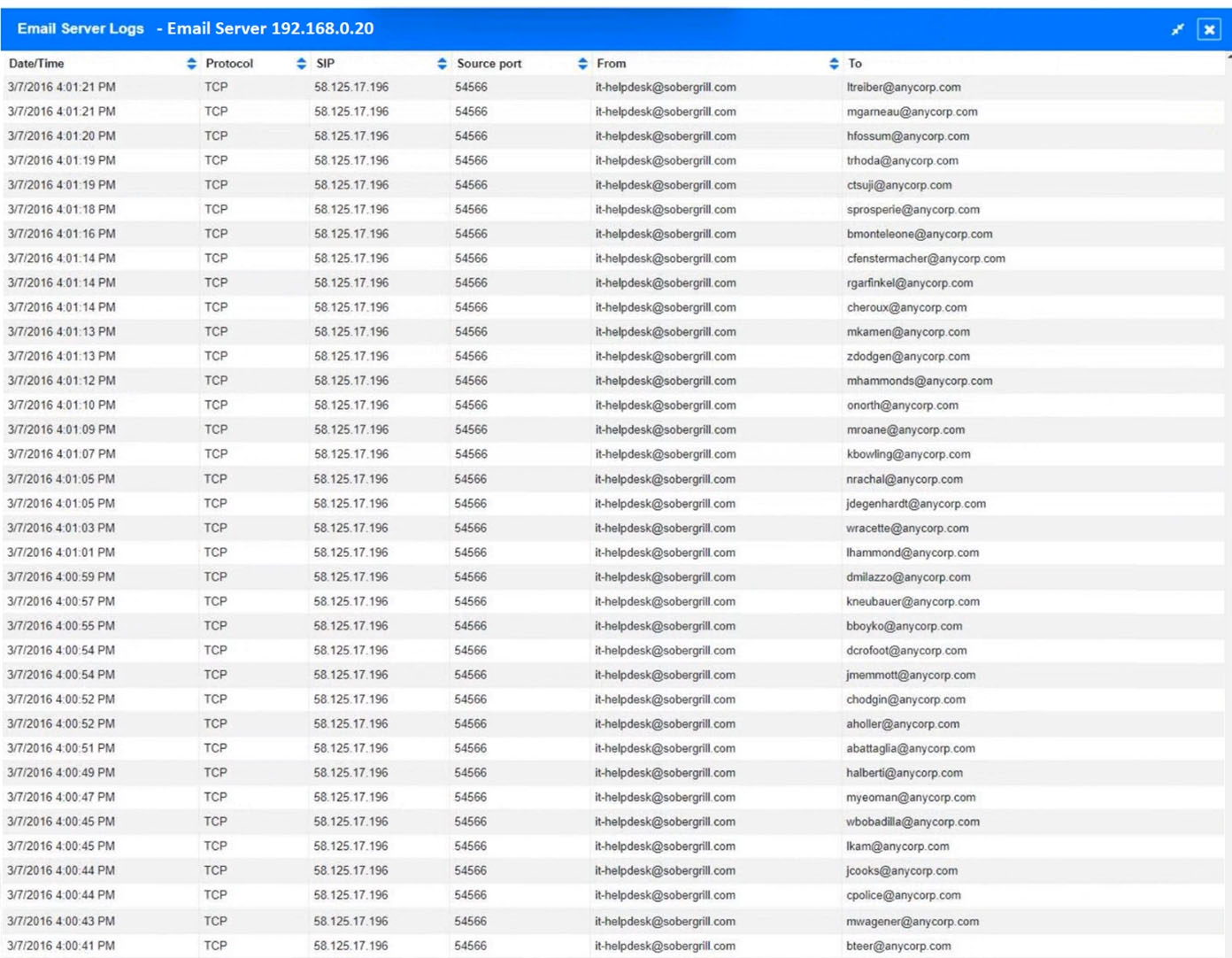
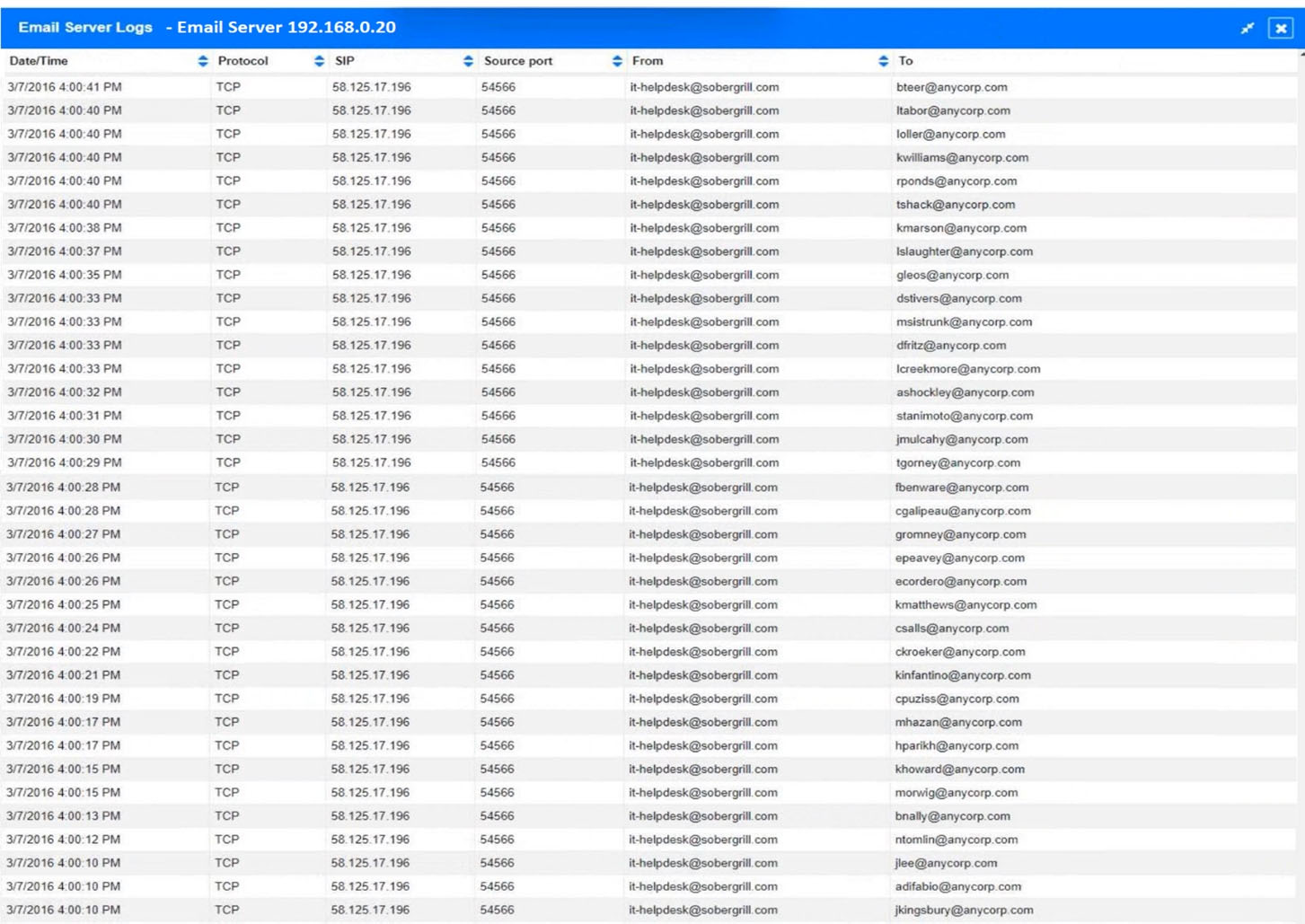
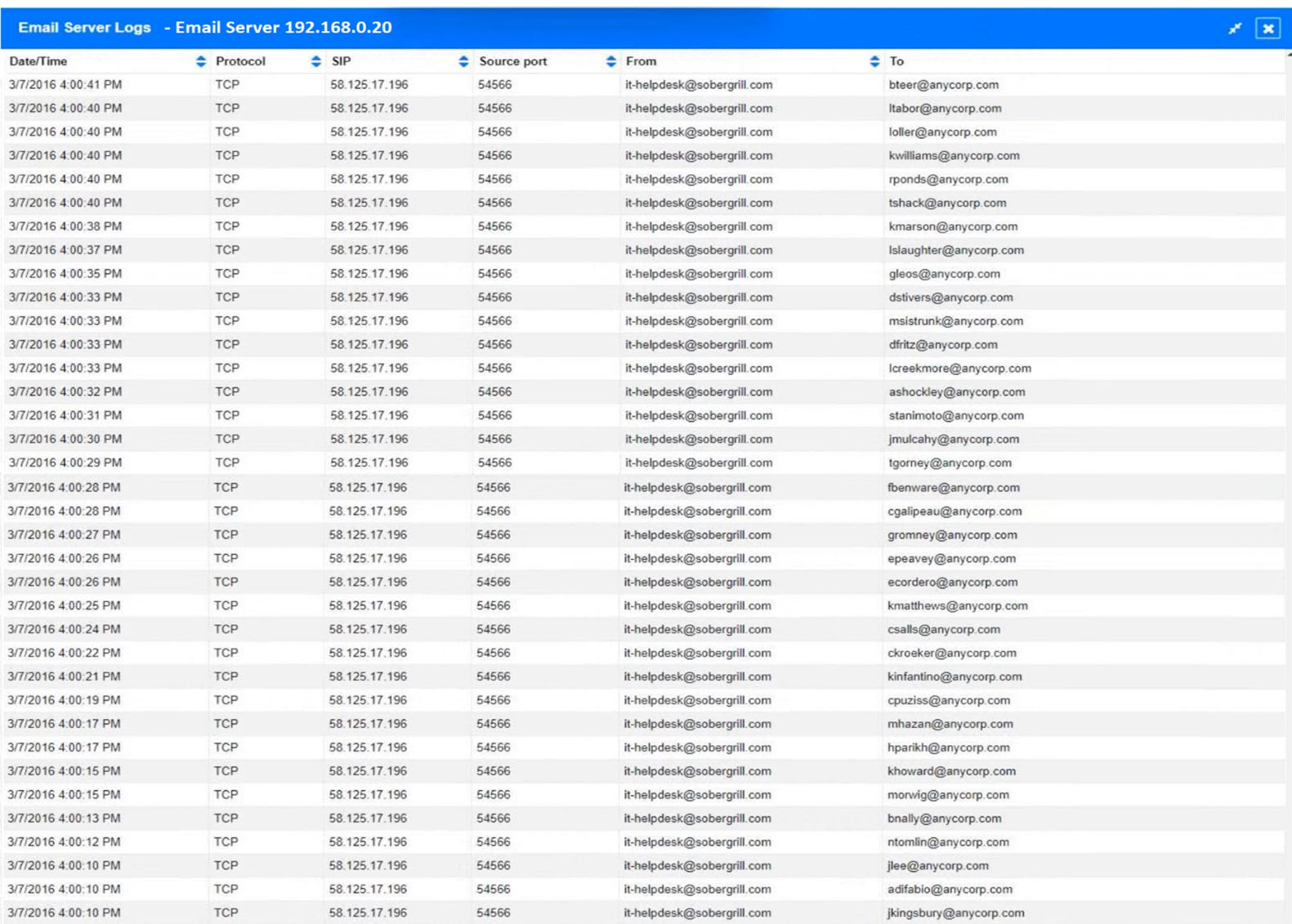
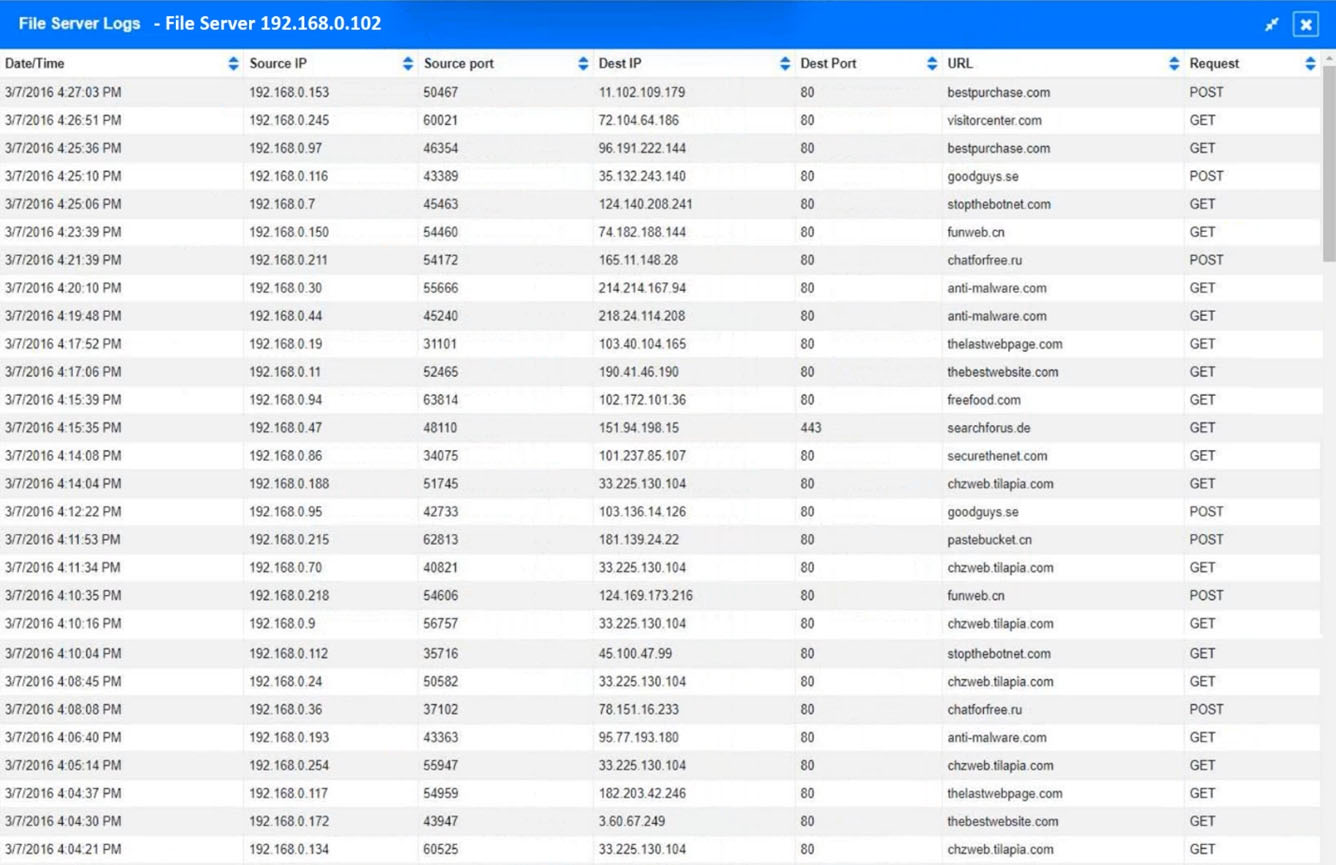
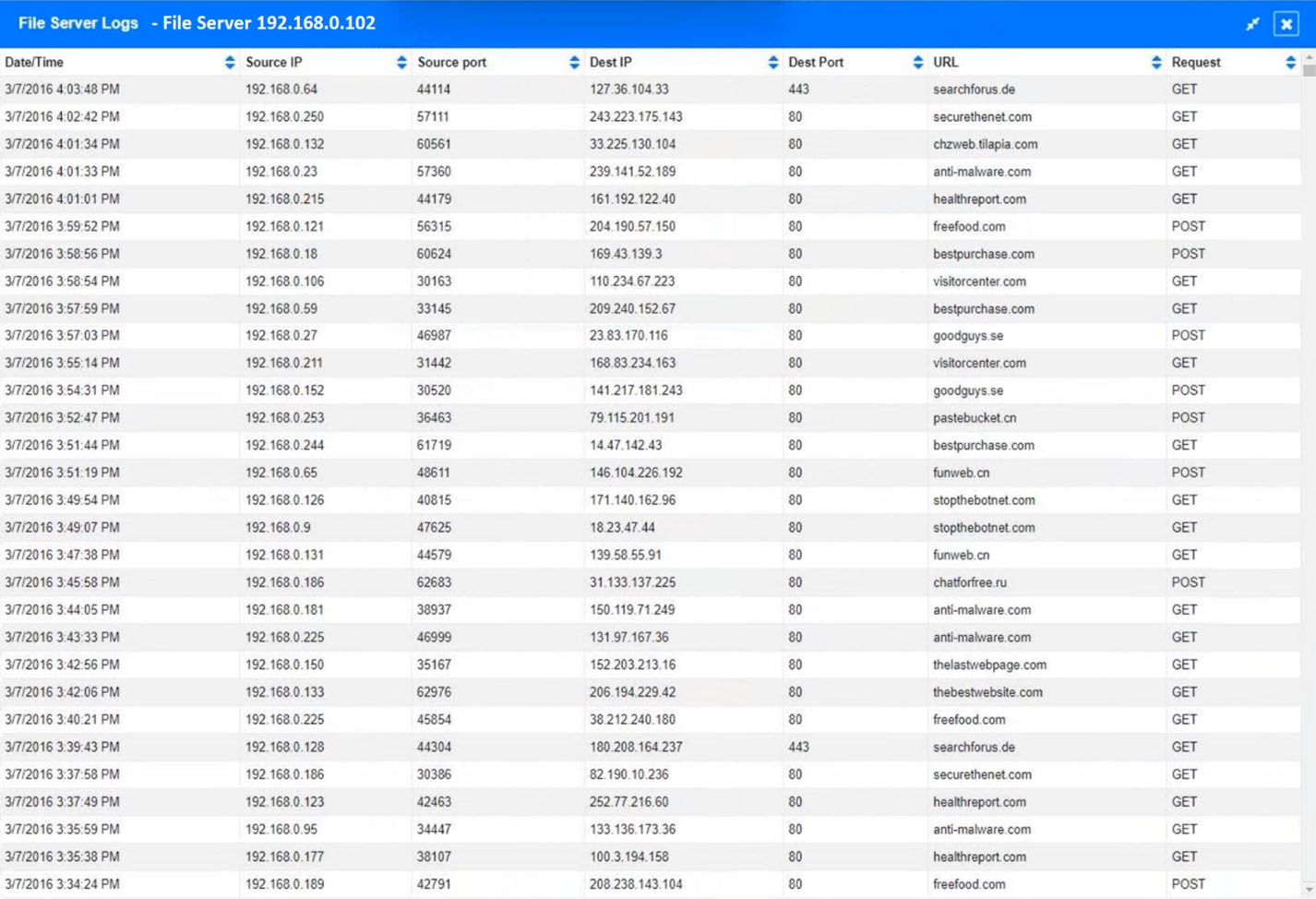
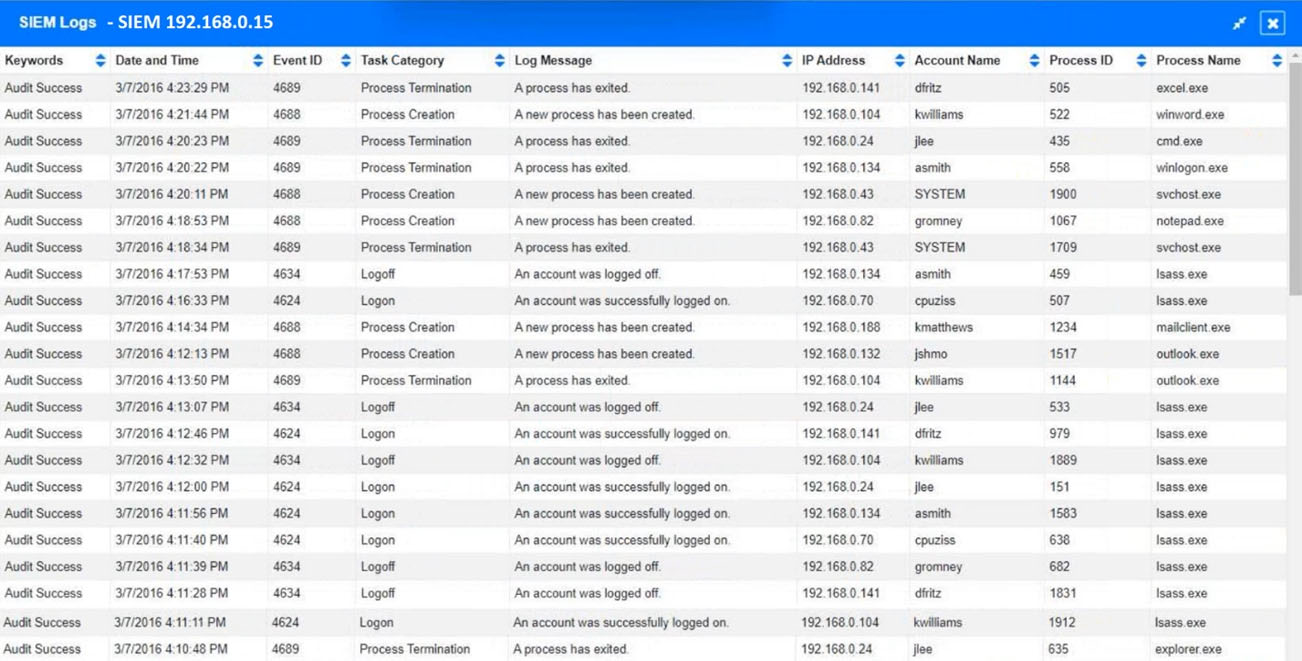
Approximately 100 employees at your company have received a phishing email. As a security analyst, you have been tasked with handling this situation.
INSTRUCTIONS -
Review the information provided and determine the following:
1. How many employees clicked on the link in the phishing email?
2. On how many workstations was the malware installed?
3. What is the executable file name of the malware?
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.











send
light_mode
delete
Question #29
A company is experiencing a malware attack within its network. A security engineer notices many of the impacted assets are connecting outbound to a number of remote destinations and exfiltrating data. The security engineer also sees that deployed, up-to-date antivirus signatures are ineffective. Which of the following is the BEST approach to prevent any impact to the company from similar attacks in the future?
- AIDS signatures
- BData loss prevention
- CPort security
- DSinkholingMost Voted
Correct Answer:
B
B
send
light_mode
delete
Question #30
The steering committee for information security management annually reviews the security incident register for the organization to look for trends and systematic issues. The steering committee wants to rank the risks based on past incidents to improve the security program for next year. Below is the incident register for the organization:
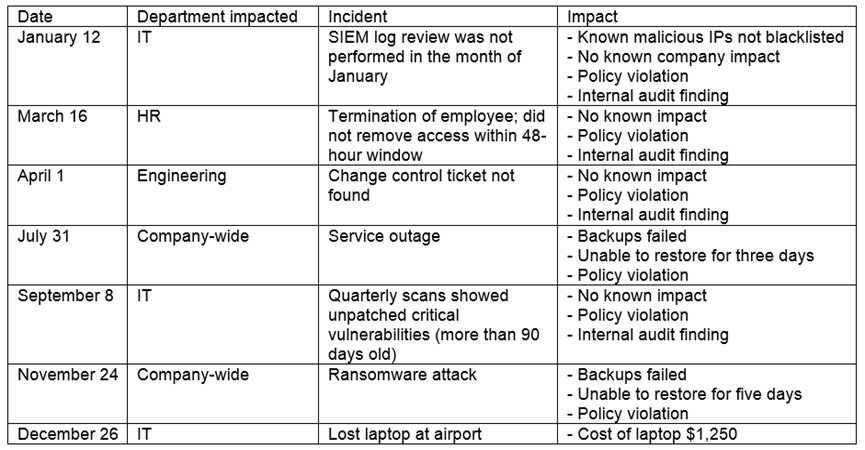
Which of the following should the organization consider investing in FIRST due to the potential impact of availability?

Which of the following should the organization consider investing in FIRST due to the potential impact of availability?
- AHire a managed service provider to help with vulnerability management
- BBuild a warm site in case of system outages
- CInvest in a failover and redundant system, as necessaryMost Voted
- DHire additional staff for the IT department to assist with vulnerability management and log review
Correct Answer:
C
C
send
light_mode
delete
All Pages