CompTIA CS0-002 Exam Practice Questions (P. 2)
- Full Access (422 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #11
Which of the following is a difference between SOAR and SCAP?
- ASOAR can be executed faster and with fewer false positives than SCAP because of advanced heuristics.
- BSOAR has a wider breadth of capability using orchestration and automation, while SCAP is more limited in scope.Most Voted
- CSOAR is less expensive because process and vulnerability remediation is more automated than what SCAP does.
- DSOAR eliminates the need for people to perform remediation, while SCAP relies heavily on security analysts.
Correct Answer:
B
B
 GPT-4o - Answer
GPT-4o - Answer
Absolutely, the distinction between SOAR and SCAP primarily lies in their scope and functionality. SOAR, standing for Security Orchestration, Automation, and Response, focuses on a broader set of capabilities like incident response and threat management through orchestrated automated processes. On the other hand, SCAP (Security Content Automation Protocol) is specialized for automating vulnerability management and ensuring compliance with standard configurations, making it a tool with a much narrower scope compared to SOAR. This understanding helps clarify how each tool fits into different segments of cybersecurity operations.
send
light_mode
delete
Question #12
An organization has a policy that requires servers to be dedicated to one function and unneeded services to be disabled. Given the following output from an Nmap scan of a web server:
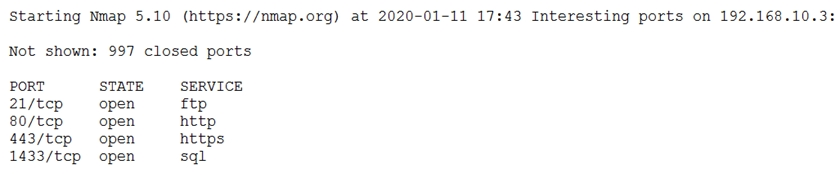
Which of the following ports should be closed?

Which of the following ports should be closed?
send
light_mode
delete
Question #13
An organization is upgrading its network and all of its workstations. The project will occur in phases, with infrastructure upgrades each month and workstation installs every other week. The schedule should accommodate the enterprise-wide changes, while minimizing the impact to the network. Which of the following schedules BEST addresses these requirements?
- AMonthly vulnerability scans, biweekly topology scans, daily host discovery scans
- BMonthly topology scans, biweekly host discovery scans, monthly vulnerability scansMost Voted
- CMonthly host discovery scans, biweekly vulnerability scans, monthly topology scans
- DMonthly topology scans, biweekly host discovery scans, weekly vulnerability scans
Correct Answer:
C
C
 GPT-4o - Answer
GPT-4o - Answer
Option C strategically aligns host discovery scans and vulnerability scans with the scheduled upgrades and installations—annual host discovery scans line up with monthly infrastructure updates, and biweekly vulnerability scans coincide with biweekly workstation installations. This schedule minimizes network disruption while ensuring all new additions and changes to the network structure are secured and incorporated efficiently. Monthly topology scans offer a consistent review of the network layout with minimal impact, adhering to best practices for handling large-scale updates within an enterprise environment.
send
light_mode
delete
Question #14
SIMULATION -
Malware is suspected on a server in the environment.
The analyst is provided with the output of commands from servers in the environment and needs to review all output files in order to determine which process running on one of the servers may be malware.
INSTRUCTIONS -
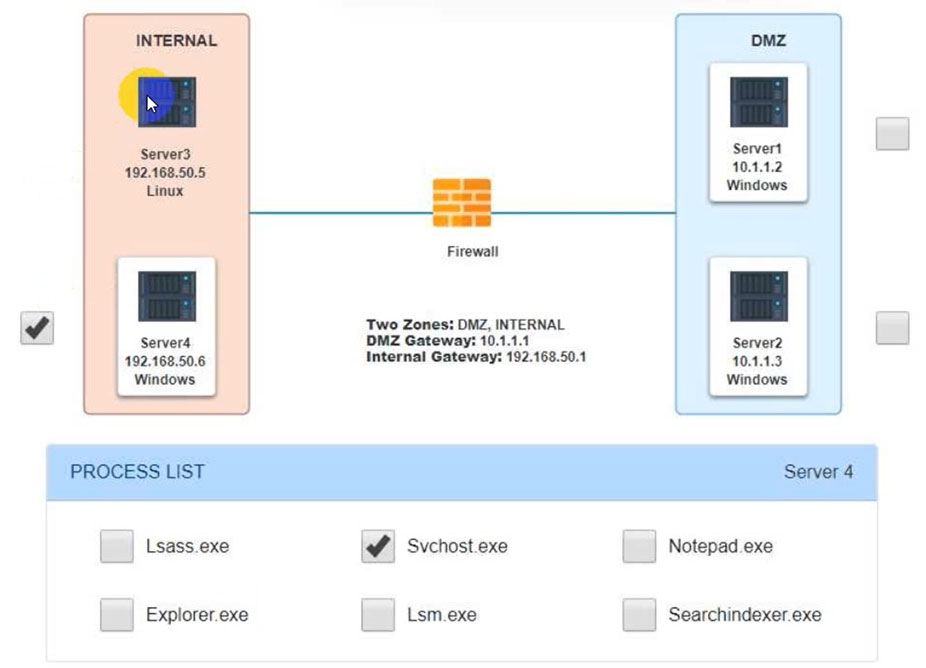
Servers 1, 2, and 4 are clickable. Select the Server and the process that host the malware.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
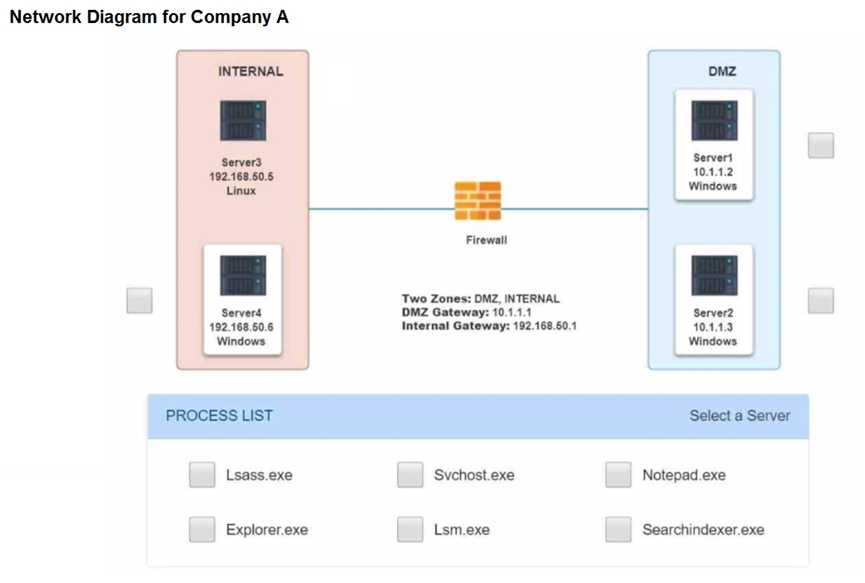
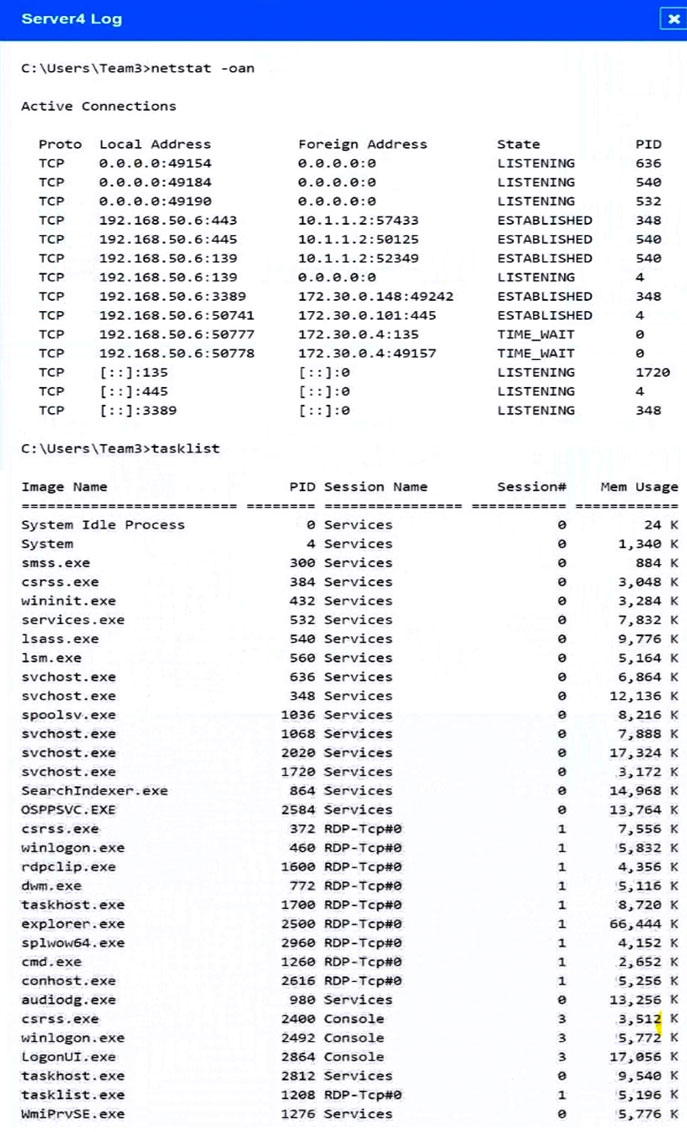
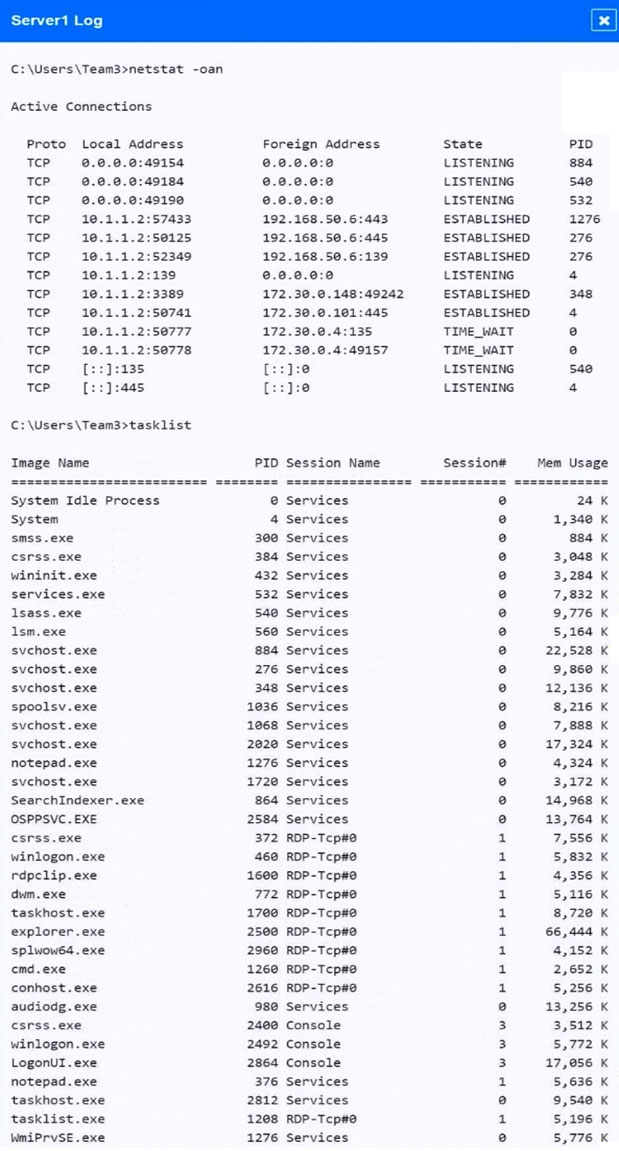
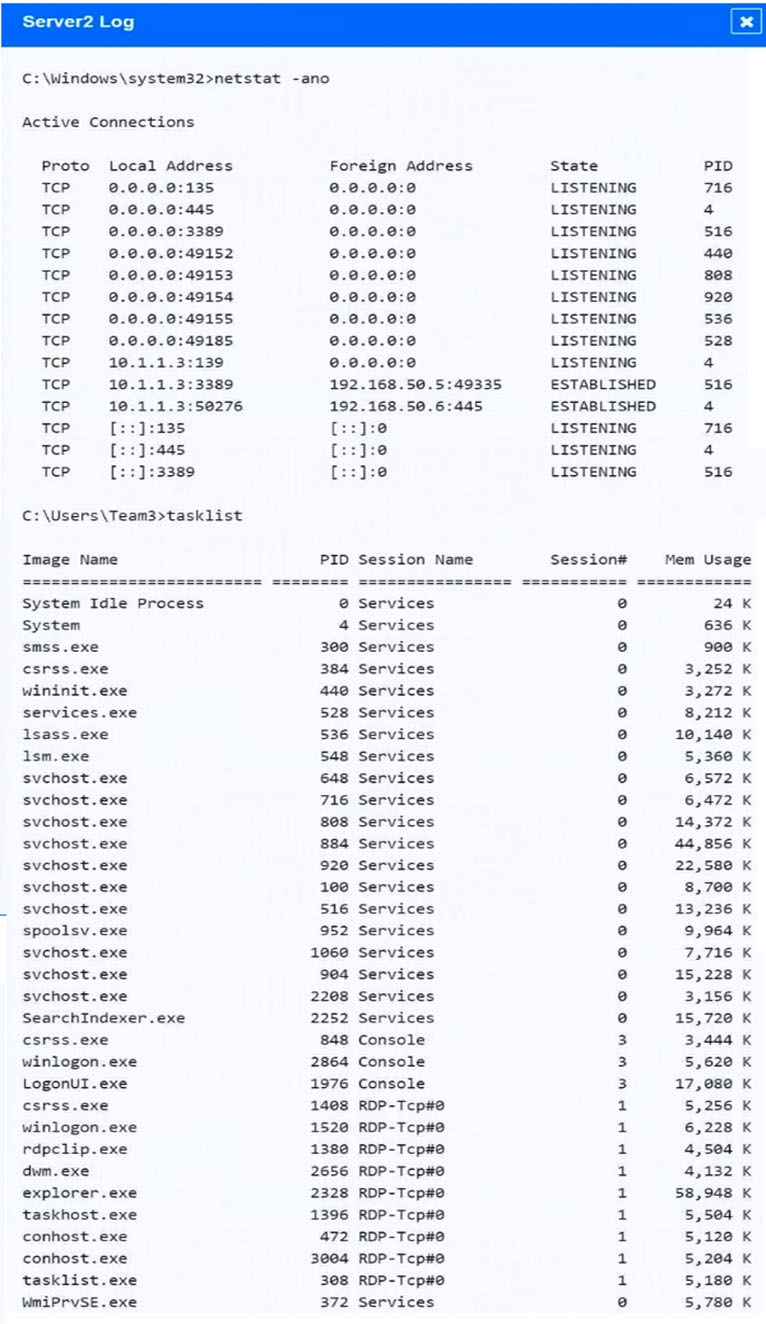
Malware is suspected on a server in the environment.
The analyst is provided with the output of commands from servers in the environment and needs to review all output files in order to determine which process running on one of the servers may be malware.
INSTRUCTIONS -
Servers 1, 2, and 4 are clickable. Select the Server and the process that host the malware.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.




send
light_mode
delete
Question #15
While reviewing incident reports from the previous night, a security analyst notices the corporate websites were defaced with political propaganda. Which of the following BEST describes this type of actor?
- AHacktivistMost Voted
- BNation-state
- CInsider threat
- DOrganized crime
Correct Answer:
A
A
 GPT-4o - Answer
GPT-4o - Answer
The term "hacktivist" aptly describes an actor who would deface websites with political propaganda, leveraging hacking to advance a political or philosophical cause. Such scenarios are typical of hacktivism where the primary motive is to promote a political message rather than financial gain or corporate espionage. It's crucial in cybersecurity analysis to recognize the motives behind security breaches, as they significantly influence the response and prevention strategies.
send
light_mode
delete
Question #16
A security analyst is performing a Diamond Model analysis of an incident the company had last quarter. A potential benefit of this activity is that it can identify:
- Adetection and prevention capabilities to improve.Most Voted
- Bwhich systems were exploited more frequently.
- Cpossible evidence that is missing during forensic analysis.
- Dwhich analysts require more training.
- Ethe time spent by analysts on each of the incidents.
Correct Answer:
A
Reference:
https://www.recordedfuture.com/diamond-model-intrusion-analysis/
A
Reference:
https://www.recordedfuture.com/diamond-model-intrusion-analysis/
send
light_mode
delete
Question #17
An IT security analyst has received an email alert regarding a vulnerability within the new fleet of vehicles the company recently purchased. Which of the following attack vectors is the vulnerability MOST likely targeting?
- ASCADA
- BCAN busMost Voted
- CModbus
- DIoT
Correct Answer:
B
B
 GPT-4o - Answer
GPT-4o - Answer
In the context of vehicle vulnerabilities, the Controller Area Network (CAN bus) is the primary vehicle network system facilitating communication between numerous electronic control units (ECUs) within the vehicle. CAN bus protocols define a standard car communication mode which can be susceptible to cyber-attacks, making it a highly probable attack vector for the vulnerabilities mentioned. This protocol is crucial in understanding automotive systems security and reflects the common configurations in modern vehicles to manage various electronic functions efficiently and reliably.
send
light_mode
delete
Question #18
An internally developed file-monitoring system identified the following excerpt as causing a program to crash often: char filedata[100]; fp = fopen(`access.log`, `r`); srtcopy (filedata, fp); printf (`%s\n`, filedata);
Which of the following should a security analyst recommend to fix the issue?
Which of the following should a security analyst recommend to fix the issue?
- AOpen the access.log file in read/write mode.
- BReplace the strcpy function.Most Voted
- CPerform input sanitization.
- DIncrease the size of the file data butter.
Correct Answer:
B
B
 GPT-4o - Answer
GPT-4o - Answer
Replacing the strcpy function is indeed the correct fix, as it can lead to buffer overflow attacks by copying data without validating the length, potentially exceeding the buffer's capacity. A more secure alternative which checks buffer limits, such as strncpy or memcpy, should be advised to mitigate risks of exploitable code vulnerabilities. This practice also aligns closely with the CySA+ exam objectives which emphasize secure coding practices and identifying weaknesses in software development processes.
send
light_mode
delete
Question #19
A company's legal and accounting teams have decided it would be more cost-effective to offload the risks of data storage to a third party. The IT management team has decided to implement a cloud model and has asked the security team for recommendations. Which of the following will allow all data to be kept on the third-party network?
- AVDI
- BSaaSMost Voted
- CCASB
- DFaaS
Correct Answer:
C
C
 GPT-4o - Answer
GPT-4o - Answer
The correct choice for ensuring all company data is managed and stored on a third-party network while maintaining policy compliance, user activity monitoring, and data residency laws adherence is CASB. The CASB functions as an intermediary that extends the company's security policies onto the cloud services used, allowing robust governance of data in the cloud, regardless of where the cloud provider is located or what type of data is being stored. This resolves any compliance issues related to data location and privacy concerns, ensuring all data can remain on the cloud provider’s network without breach of regulations.
send
light_mode
delete
Question #20
A security analyst discovers suspicious host activity while performing monitoring activities. The analyst pulls a packet capture for the activity and sees the following:

Follow TCP stream:
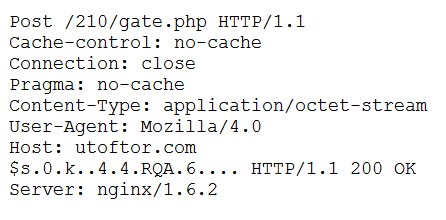
Which of the following describes what has occurred?

Follow TCP stream:

Which of the following describes what has occurred?
- AThe host attempted to download an application from utoftor.com.
- BThe host downloaded an application from utoftor.com.Most Voted
- CThe host attempted to make a secure connection to utoftor.com.
- DThe host rejected the connection from utoftor.com.
Correct Answer:
D
D
send
light_mode
delete
All Pages