CompTIA CAS-003 Exam Practice Questions (P. 4)
- Full Access (480 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #31
A Chief Information Officer (CIO) publicly announces the implementation of a new financial system. As part of a security assessment that includes a social engineering task, which of the following tasks should be conducted to demonstrate the BEST means to gain information to use for a report on social vulnerability details about the financial system?
- ACall the CIO and ask for an interview, posing as a job seeker interested in an open position
- BCompromise the email server to obtain a list of attendees who responded to the invitation who is on the IT staff
- CNotify the CIO that, through observation at events, malicious actors can identify individuals to befriend
- DUnderstand the CIO is a social drinker, and find the means to befriend the CIO at establishments the CIO frequents
Correct Answer:
D
D
send
light_mode
delete
Question #32
A recent assessment identified that several users' mobile devices are running outdated versions of endpoint security software that do not meet the company's security policy. Which of the following should be performed to ensure the users can access the network and meet the company's security requirements?
- AVulnerability assessment
- BRisk assessment
- CPatch management
- DDevice quarantine
- EIncident management
Correct Answer:
C
C
send
light_mode
delete
Question #33
A company suspects a web server may have been infiltrated by a rival corporation. The security engineer reviews the web server logs and finds the following: ls -l -a /usr/heinz/public; cat ./config/db.yml
The security engineer looks at the code with a developer, and they determine the log entry is created when the following line is run: system ("ls -l -a #{path}")
Which of the following is an appropriate security control the company should implement?
The security engineer looks at the code with a developer, and they determine the log entry is created when the following line is run: system ("ls -l -a #{path}")
Which of the following is an appropriate security control the company should implement?
- ARestrict directory permissions to read-only access.
- BUse server-side processing to avoid XSS vulnerabilities in path input.
- CSeparate the items in the system call to prevent command injection.
- DParameterize a query in the path variable to prevent SQL injection.
Correct Answer:
C
C
send
light_mode
delete
Question #34
A Chief Information Security Officer (CISO) is reviewing the results of a gap analysis with an outside cybersecurity consultant. The gap analysis reviewed all procedural and technical controls and found the following:
✑ High-impact controls implemented: 6 out of 10
✑ Medium-impact controls implemented: 409 out of 472
✑ Low-impact controls implemented: 97 out of 1000
The report includes a cost-benefit analysis for each control gap. The analysis yielded the following information:
✑ Average high-impact control implementation cost: $15,000; Probable ALE for each high-impact control gap: $95,000
✑ Average medium-impact control implementation cost: $6,250; Probable ALE for each medium-impact control gap: $11,000
Due to the technical construction and configuration of the corporate enterprise, slightly more than 50% of the medium-impact controls will take two years to fully implement. Which of the following conclusions could the CISO draw from the analysis?
✑ High-impact controls implemented: 6 out of 10
✑ Medium-impact controls implemented: 409 out of 472
✑ Low-impact controls implemented: 97 out of 1000
The report includes a cost-benefit analysis for each control gap. The analysis yielded the following information:
✑ Average high-impact control implementation cost: $15,000; Probable ALE for each high-impact control gap: $95,000
✑ Average medium-impact control implementation cost: $6,250; Probable ALE for each medium-impact control gap: $11,000
Due to the technical construction and configuration of the corporate enterprise, slightly more than 50% of the medium-impact controls will take two years to fully implement. Which of the following conclusions could the CISO draw from the analysis?
- AToo much emphasis has been placed on eliminating low-risk vulnerabilities in the past
- BThe enterprise security team has focused exclusively on mitigating high-level risks
- CBecause of the significant ALE for each high-risk vulnerability, efforts should be focused on those controls
- DThe cybersecurity team has balanced residual risk for both high and medium controls
Correct Answer:
C
C
send
light_mode
delete
Question #35
After investigating virus outbreaks that have cost the company $1000 per incident, the company's Chief Information Security Officer (CISO) has been researching new antivirus software solutions to use and be fully supported for the next two years. The CISO has narrowed down the potential solutions to four candidates that meet all the company's performance and capability requirements:
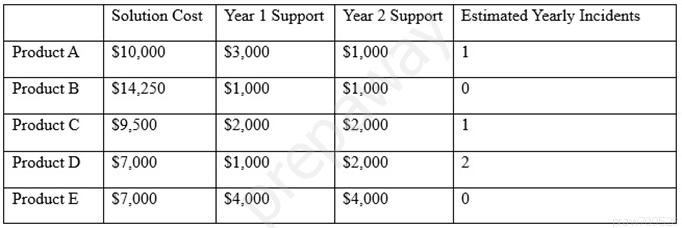
Using the table above, which of the following would be the BEST business-driven choice among the five possible solutions?

Using the table above, which of the following would be the BEST business-driven choice among the five possible solutions?
send
light_mode
delete
Question #36
A financial consulting firm recently recovered from some damaging incidents that were associated with malware installed via rootkit. Post-incident analysis is ongoing, and the incident responders and systems administrators are working to determine a strategy to reduce the risk of recurrence. The firm's systems are running modern operating systems and feature UEFI and TPMs. Which of the following technical options would provide the MOST preventive value?
- AUpdate and deploy GPOs
- BConfigure and use measured bootMost Voted
- CStrengthen the password complexity requirements
- DUpdate the antivirus software and definitions
Correct Answer:
D
D
send
light_mode
delete
Question #37
A company monitors the performance of all web servers using WMI. A network administrator informs the security engineer that web servers hosting the company's client-facing portal are running slowly today. After some investigation, the security engineer notices a large number of attempts at enumerating host information via
SNMP from multiple IP addresses. Which of the following would be the BEST technique for the security engineer to employ in an attempt to prevent reconnaissance activity?
SNMP from multiple IP addresses. Which of the following would be the BEST technique for the security engineer to employ in an attempt to prevent reconnaissance activity?
- AInstall a HIPS on the web servers
- BDisable inbound traffic from offending sources
- CDisable SNMP on the web servers
- DInstall anti-DDoS protection in the DMZ
Correct Answer:
A
A
send
light_mode
delete
Question #38
One of the objectives of a bank is to instill a security awareness culture. Which of the following are techniques that could help to achieve this? (Choose two.)
- ABlue teaming
- BPhishing simulations
- CLunch-and-learn
- DRandom audits
- EContinuous monitoring
- FSeparation of duties
Correct Answer:
BE
BE
send
light_mode
delete
Question #39
The risk subcommittee of a corporate board typically maintains a master register of the most prominent risks to the company. A centralized holistic view of risk is particularly important to the corporate Chief Information Security Officer (CISO) because:
- AIT systems are maintained in silos to minimize interconnected risks and provide clear risk boundaries used to implement compensating controls
- Brisks introduced by a system in one business unit can affect other business units in ways in which the individual business units have no awareness
- Ccorporate general counsel requires a single system boundary to determine overall corporate risk exposure
- Dmajor risks identified by the subcommittee merit the prioritized allocation of scare funding to address cybersecurity concerns
Correct Answer:
B
B
send
light_mode
delete
Question #40
An insurance company has two million customers and is researching the top transactions on its customer portal. It identifies that the top transaction is currently password reset. Due to users not remembering their secret questions, a large number of calls are consequently routed to the contact center for manual password resets. The business wants to develop a mobile application to improve customer engagement in the future, continue with a single factor of authentication, minimize management overhead of the solution, remove passwords, and eliminate to the contact center. Which of the following techniques would BEST meet the requirements? (Choose two.)
- AMagic link sent to an email address
- BCustomer ID sent via push notification
- CSMS with OTP sent to a mobile number
- DThird-party social login
- ECertificate sent to be installed on a device
- FHardware tokens sent to customers
Correct Answer:
CE
CE
send
light_mode
delete
All Pages
