CompTIA CAS-003 Exam Practice Questions (P. 1)
- Full Access (480 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #1
DRAG DROP -
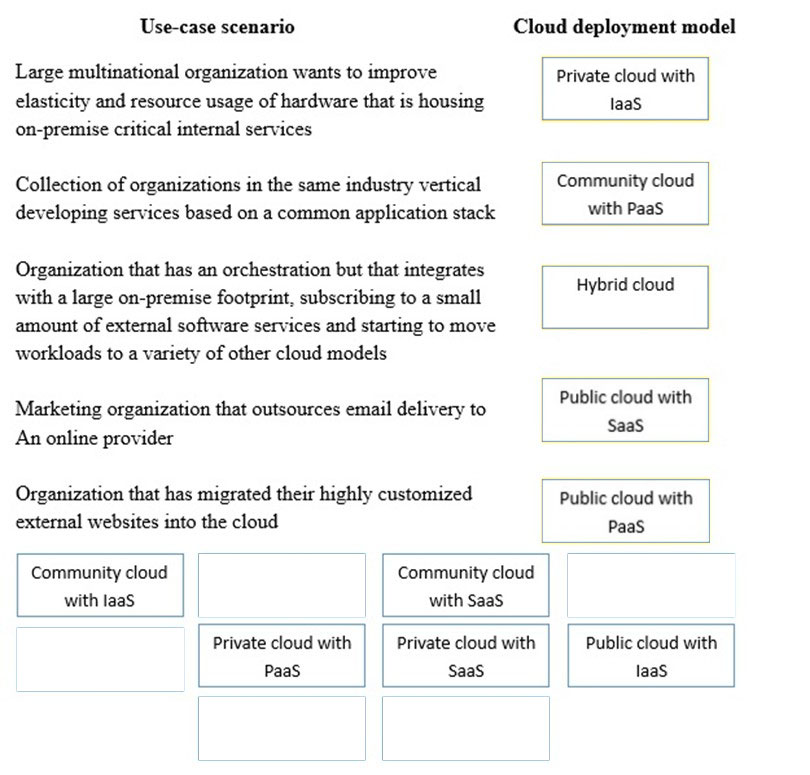
Drag and drop the cloud deployment model to the associated use-case scenario. Options may be used only once or not at all.
Select and Place:
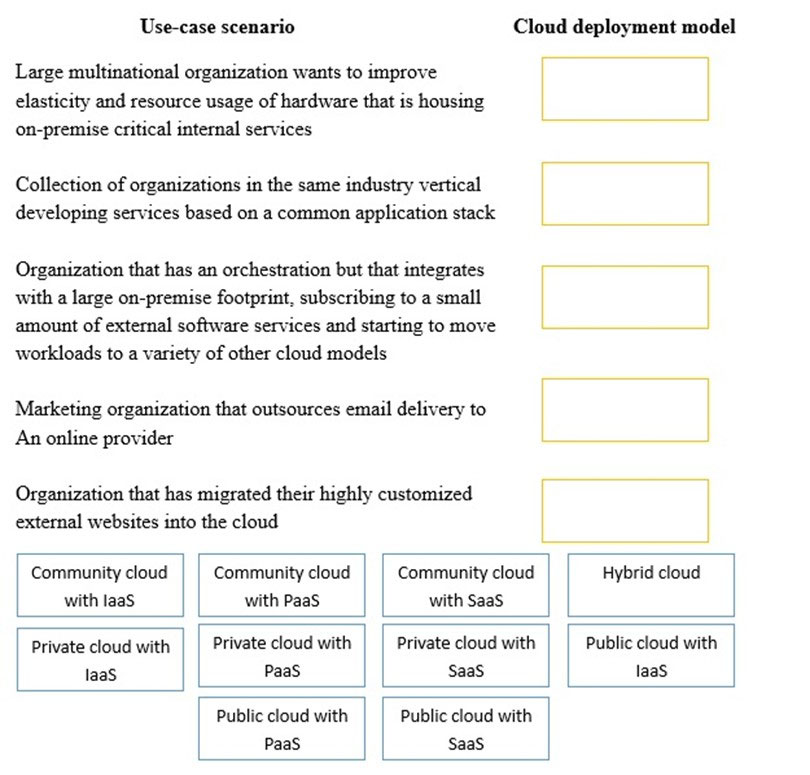
Drag and drop the cloud deployment model to the associated use-case scenario. Options may be used only once or not at all.
Select and Place:

send
light_mode
delete
Question #2
DRAG DROP -
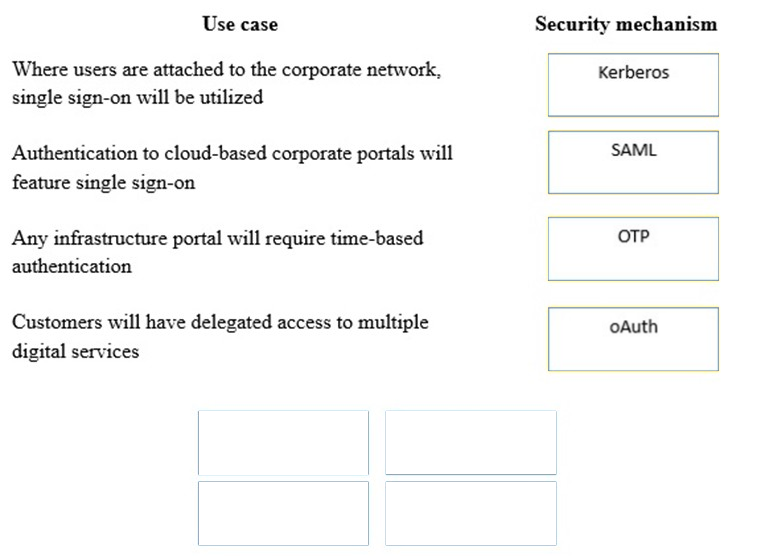
A security consultant is considering authentication options for a financial institution. The following authentication options are available. Drag and drop the security mechanism to the appropriate use case. Options may be used once.
Select and Place:
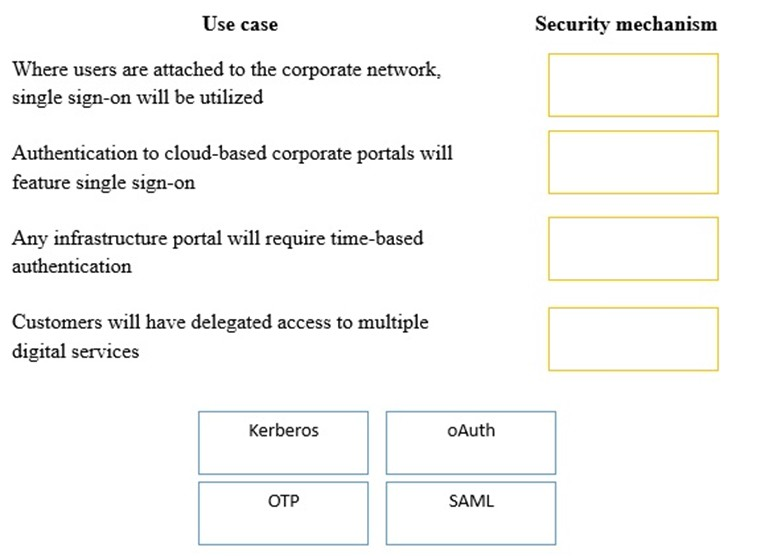
A security consultant is considering authentication options for a financial institution. The following authentication options are available. Drag and drop the security mechanism to the appropriate use case. Options may be used once.
Select and Place:

send
light_mode
delete
Question #3
A company's Chief Operating Officer (COO) is concerned about the potential for competitors to infer proprietary information gathered from employees' social media accounts.
Which of the following methods should the company use to gauge its own social media threat level without targeting individual employees?
Which of the following methods should the company use to gauge its own social media threat level without targeting individual employees?
- AUtilize insider threat consultants to provide expertise.
- BRequire that employees divulge social media accounts.
- CLeverage Big Data analytical algorithms.
- DPerform social engineering tests to evaluate employee awareness.
Correct Answer:
A
A
send
light_mode
delete
Question #4
DRAG DROP -
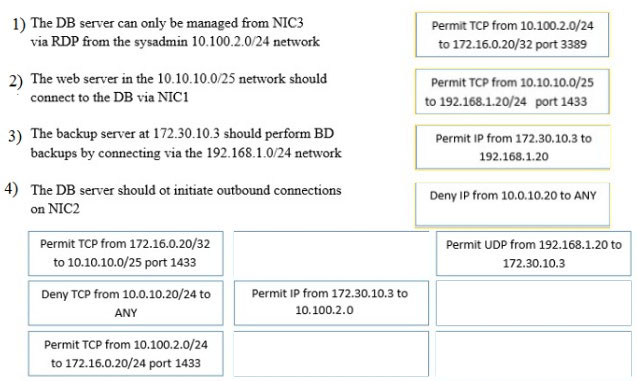
A security administrator must configure the database server shown below to comply with the four requirements listed. Drag and drop the appropriate ACL that should be configured on the database server to its corresponding requirement. Answer options may be used once or not at all.
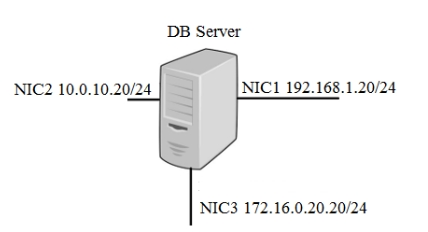
Select and Place:
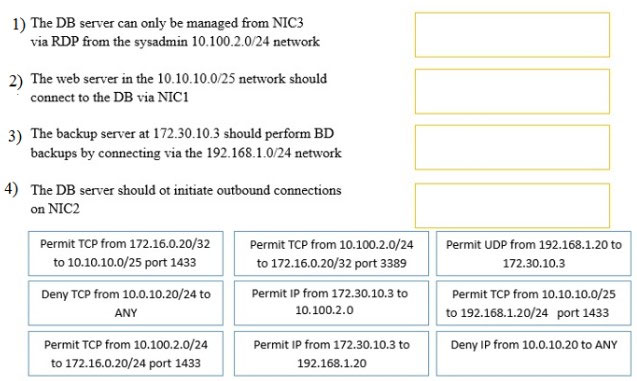
A security administrator must configure the database server shown below to comply with the four requirements listed. Drag and drop the appropriate ACL that should be configured on the database server to its corresponding requirement. Answer options may be used once or not at all.

Select and Place:

send
light_mode
delete
Question #5
A security administrator is hardening a TrustedSolaris server that processes sensitive data. The data owner has established the following security requirements:
✑ The data is for internal consumption only and shall not be distributed to outside individuals
✑ The systems administrator should not have access to the data processed by the server
✑ The integrity of the kernel image is maintained

Which of the following host-based security controls BEST enforce the data owner's requirements? (Choose three.)
✑ The data is for internal consumption only and shall not be distributed to outside individuals
✑ The systems administrator should not have access to the data processed by the server
✑ The integrity of the kernel image is maintained

Which of the following host-based security controls BEST enforce the data owner's requirements? (Choose three.)
- ASELinux
- BDLP
- CHIDS
- DHost-based firewall
- EMeasured boot
- FData encryption
- GWatermarking
Correct Answer:
CEF
CEF
send
light_mode
delete
Question #6
An SQL database is no longer accessible online due to a recent security breach. An investigation reveals that unauthorized access to the database was possible due to an SQL injection vulnerability. To prevent this type of breach in the future, which of the following security controls should be put in place before bringing the database back online? (Choose two.)
- ASecure storage policies
- BBrowser security updates
- CInput validation
- DWeb application firewall
- ESecure coding standards
- FDatabase activity monitoring
Correct Answer:
CF
CF
send
light_mode
delete
Question #7
A company has entered into a business agreement with a business partner for managed human resources services. The Chief Information Security Officer (CISO) has been asked to provide documentation that is required to set up a business-to-business VPN between the two organizations. Which of the following is required in this scenario?
send
light_mode
delete
Question #8
Given the following output from a local PC:
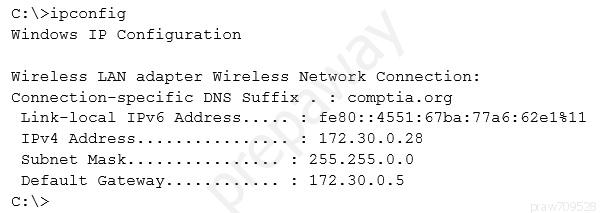
Which of the following ACLs on a stateful host-based firewall would allow the PC to serve an intranet website?

Which of the following ACLs on a stateful host-based firewall would allow the PC to serve an intranet website?
- AAllow 172.30.0.28:80 -> ANY
- BAllow 172.30.0.28:80 -> 172.30.0.0/16
- CAllow 172.30.0.28:80 -> 172.30.0.28:443
- DAllow 172.30.0.28:80 -> 172.30.0.28:53
Correct Answer:
B
B
send
light_mode
delete
Question #9
A penetration tester has been contracted to conduct a physical assessment of a site. Which of the following is the MOST plausible method of social engineering to be conducted during this engagement?
- ARandomly calling customer employees and posing as a help desk technician requiring user password to resolve issues
- BPosing as a copier service technician and indicating the equipment had ג€phoned homeג€ to alert the technician for a service callMost Voted
- CSimulating an illness while at a client location for a sales call and then recovering once listening devices are installed
- DObtaining fake government credentials and impersonating law enforcement to gain access to a company facility
Correct Answer:
A
A
send
light_mode
delete
Question #10
A penetration tester is conducting an assessment on Comptia.org and runs the following command from a coffee shop while connected to the public Internet:
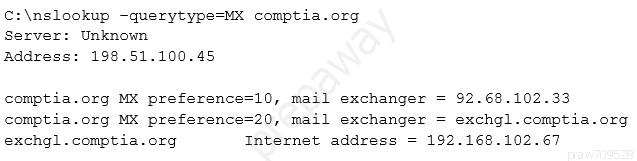
Which of the following should the penetration tester conclude about the command output?

Which of the following should the penetration tester conclude about the command output?
- AThe public/private views on the Comptia.org DNS servers are misconfiguredMost Voted
- BComptia.org is running an older mail server, which may be vulnerable to exploits
- CThe DNS SPF records have not been updated for Comptia.org
- D192.168.102.67 is a backup mail server that may be more vulnerable to attack
Correct Answer:
B
B
send
light_mode
delete
All Pages