Cisco® 350-601 Exam Practice Questions (P. 3)
- Full Access (526 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #21
What are two capabilities of the Cisco Network Assurance Engine? (Choose two.)
- AIt validates that devices comply with network security policies.Most Voted
- BIt predicts the impact of changes to the network.Most Voted
- CIt predicts the network load on a data center.
- DIt ensures that network performance meets an SLA.
- EIt verifies the speed of network packet flows by using telemetry.
Correct Answer:
AB
With Cisco Network Assurance Engine operators can:
ג— Predict the impact of network changes: Proactively verify changes made to the network for correctness to drive increased change agility while significantly reducing the risk of network failures induced by human error.
ג— Verify network-wide behavior: Continuously analyze and verify the dynamic state of the network against intent and policy to ensure connectivity and eliminate potential network outages and vulnerabilities before any business impact occurs.
ג— Ensure network security policy and compliance: Ensure network security policies and check for compliance against business rules to reduce security risk and achieve provable continuous compliance by policy and state.
Reference:
https://www.cisco.com/c/en/us/products/collateral/data-center-analytics/network-assurance-engine/at-a-glance-c45-740230.html
AB
With Cisco Network Assurance Engine operators can:
ג— Predict the impact of network changes: Proactively verify changes made to the network for correctness to drive increased change agility while significantly reducing the risk of network failures induced by human error.
ג— Verify network-wide behavior: Continuously analyze and verify the dynamic state of the network against intent and policy to ensure connectivity and eliminate potential network outages and vulnerabilities before any business impact occurs.
ג— Ensure network security policy and compliance: Ensure network security policies and check for compliance against business rules to reduce security risk and achieve provable continuous compliance by policy and state.
Reference:
https://www.cisco.com/c/en/us/products/collateral/data-center-analytics/network-assurance-engine/at-a-glance-c45-740230.html
send
light_mode
delete
Question #22
What is an advantage of streaming telemetry over SNMP?
- Aon-change traps sent to a receiver
- Bperiodic push-based subscription messagesMost Voted
- Cperiodic polling of the device status
- DMD5-based authentication on polling
Correct Answer:
B
A key difference between SNMP and streaming telemetry is the method of data collection.
SNMP polls network devices to collect information or set configuration properties. The approach, while generally reliable, can also lead to delays as long as five to
10 minutes before information is received from a deviceג€"veritable eons in today's networks. Streaming telemetry flips and streamlines the process. Instead of the pull model used by SNMP, streaming telemetry uses a push model to continuously stream data from network devices to one or more network monitoring systems.
Reference:
https://www.networkworld.com/article/3575837/streaming-telemetry-gains-interest-as-snmp-reliance-fades.html
B
A key difference between SNMP and streaming telemetry is the method of data collection.
SNMP polls network devices to collect information or set configuration properties. The approach, while generally reliable, can also lead to delays as long as five to
10 minutes before information is received from a deviceג€"veritable eons in today's networks. Streaming telemetry flips and streamlines the process. Instead of the pull model used by SNMP, streaming telemetry uses a push model to continuously stream data from network devices to one or more network monitoring systems.
Reference:
https://www.networkworld.com/article/3575837/streaming-telemetry-gains-interest-as-snmp-reliance-fades.html
send
light_mode
delete
Question #23
APIC EPG Resolution Immediacy is set to "Immediate".
Which statement is true about the Deployment Immediacy for VMM domains associated to EPGs?
Which statement is true about the Deployment Immediacy for VMM domains associated to EPGs?
- AIf "On demand" is selected, the policy is programmed in the hardware only when the first packet is received through the data path.Most Voted
- BIf "Immediate" is selected, the policy is programmed in the hardware as soon as the leaf is booted.
- CThe "Immediate" and "On demand" options require a port group to be created on the VDS.
- DIf "On demand" is selected, the policy is programmed in the hardware only when the APIC detects a VM created in the EPG.
Correct Answer:
A
It is important to understand what those options are and how are they going to impact during deployment. Following table lists these options, their description and recommendation for Cisco AVS.
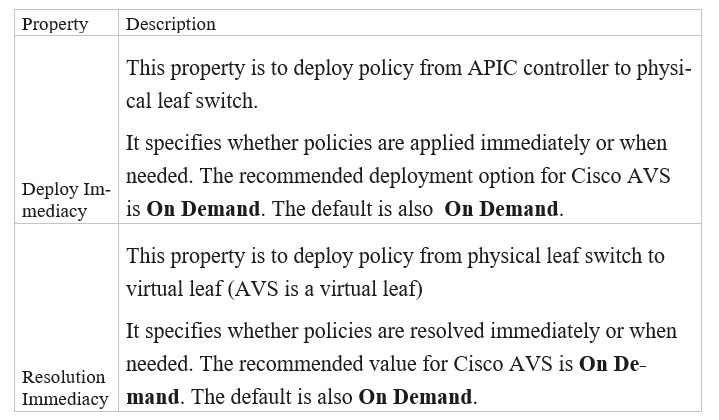
✑ Immediate ג€" Specifies that the policy is programmed in the hardware policy CAM as soon as the policy is downloaded in the leaf software.
✑ On Demand ג€" Specifies that the policy is programmed in the hardware policy CAM only when the first packet is received through the data path. This process helps to optimize the hardware space.
Reference:
https://community.cisco.com/t5/data-center-and-cloud-knowledge/apic-policy-deployment-and-resolution-immediacy-for-avs-vmm/ta-p/3134812
A
It is important to understand what those options are and how are they going to impact during deployment. Following table lists these options, their description and recommendation for Cisco AVS.

✑ Immediate ג€" Specifies that the policy is programmed in the hardware policy CAM as soon as the policy is downloaded in the leaf software.
✑ On Demand ג€" Specifies that the policy is programmed in the hardware policy CAM only when the first packet is received through the data path. This process helps to optimize the hardware space.
Reference:
https://community.cisco.com/t5/data-center-and-cloud-knowledge/apic-policy-deployment-and-resolution-immediacy-for-avs-vmm/ta-p/3134812
send
light_mode
delete
Question #24
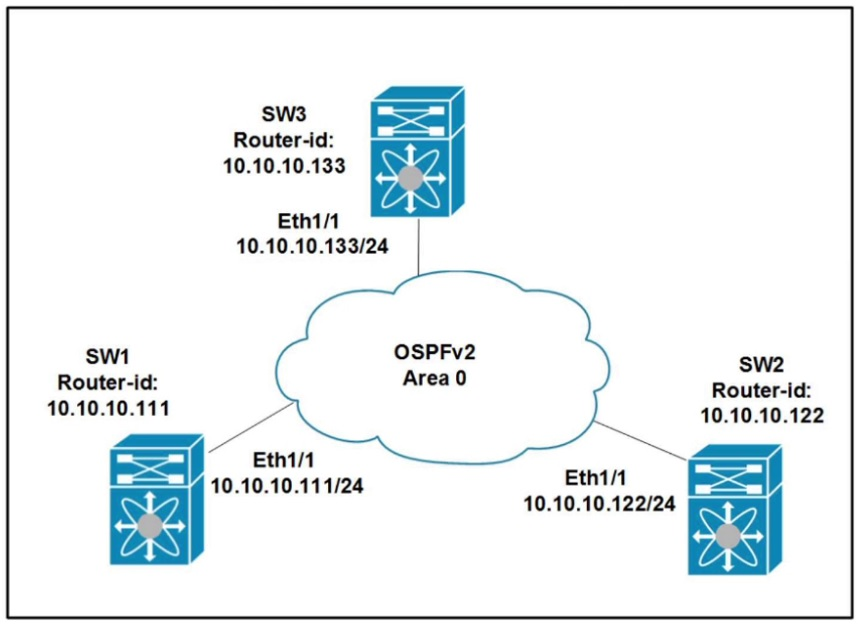
Refer to the exhibit. All switches are configured with the default OSPF priority. Which configuration should be applied to ensure that the SW2 Cisco Nexus switch controls the LSA floods and advertises the network to the remaining nodes in the OSPFv2 area?
- ASW2# configure terminal SW2 (config)# interface ethernet 1/1 SW2 (config-if)# ip ospf priority 255Most Voted
- BSW2# configure terminal SW2 (config)# interface ethernet 1/1 SW2 (config-if)# ip ospf priority 1
- CSW2# configure terminal SW2 (config)# router ospf 1 SW2 (config-router)# router-id 10.10.10.22
- DSW2# configure terminal SW2 (config)# interface ethernet 1/1 SW2 (config-if)# ip ospf priority 0
Correct Answer:
A
Reference:
https://www.cisco.com/c/m/en_us/techdoc/dc/reference/cli/nxos/commands/ospf/ip-ospf-priority.html
A
Reference:
https://www.cisco.com/c/m/en_us/techdoc/dc/reference/cli/nxos/commands/ospf/ip-ospf-priority.html
send
light_mode
delete
Question #25
DRAG DROP -
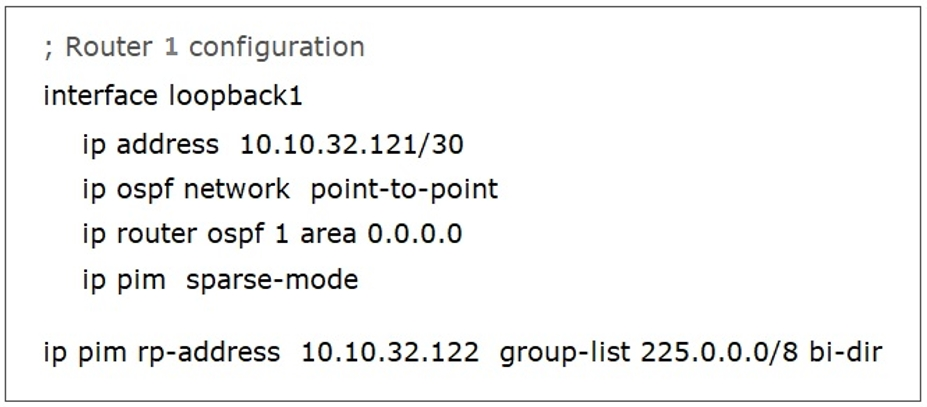
Refer to the exhibit. In a bidirectional PIM network using Phantom RP as an RP redundancy mechanism, two Cisco NX-OS routers have these requirements:
✑ R1 must be the active RP.
✑ R2 must be the backup RP that is used only if R1 is not reachable.
Drag and drop the configuration steps to complete the configuration for Router 2. Not all configuration steps are used.
Select and Place:
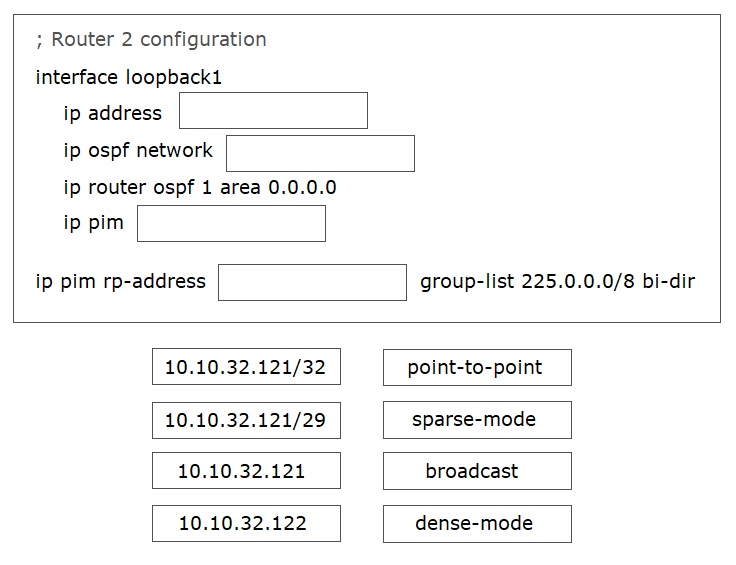

Refer to the exhibit. In a bidirectional PIM network using Phantom RP as an RP redundancy mechanism, two Cisco NX-OS routers have these requirements:
✑ R1 must be the active RP.
✑ R2 must be the backup RP that is used only if R1 is not reachable.
Drag and drop the configuration steps to complete the configuration for Router 2. Not all configuration steps are used.
Select and Place:

Correct Answer:
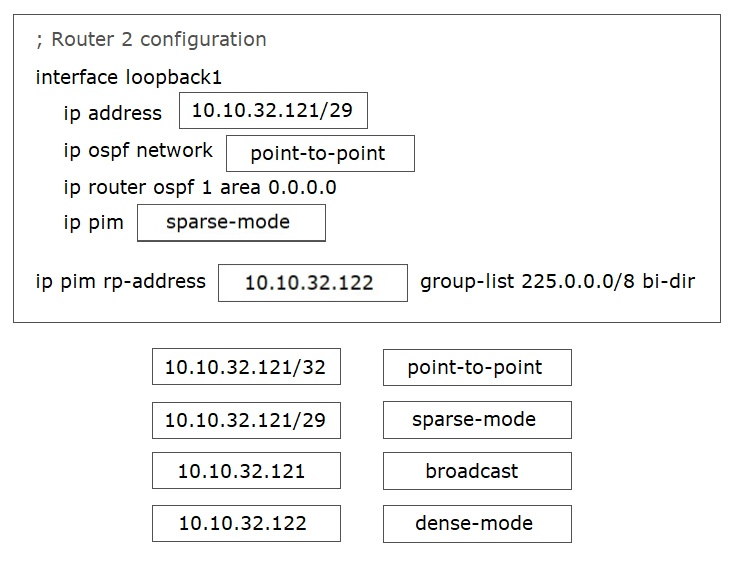
Reference:
https://community.cisco.com/t5/networking-documents/rp-redundancy-with-pim-bidir-phantom-rp/ta-p/3117191

Reference:
https://community.cisco.com/t5/networking-documents/rp-redundancy-with-pim-bidir-phantom-rp/ta-p/3117191
send
light_mode
delete
Question #26
An engineer must configure a Nexus 7000 series switch for HSRP on VLAN 100. When fully functional, the router must be the active master. Which set of commands must be used to implement the scenario?
- Afeature hsrp interface vlan100 ip address 10.1.1.2 255.255.255.0 priority 255 preempt hsrp version 2 hsrp 1000 ip 10.1.1.1Most Voted
- Bfeature-set hsrp interface vlan100 ip address 10.1.1.2 255.255.255.0 priority 20 preempt hsrp version 2 hsrp 1000 ip 10.1.1.1
- Cfeature-set hsrp interface vlan100 ip address 10.1.1.2 255.255.255.0 priority 80 preempt hsrp version 2 hsrp 1000 ip 10.1.1.1
- Dfeature hsrp interface vlan100 ip address 10.1.1.2 255.255.255.0 priority 240 preempt hsrp version 2 hsrp 1000 ip 10.1.1.1
Correct Answer:
A
Reference:
https://www.google.com/search?q=hsrp+priority&oq=hsrp+priority&aqs=chrome..69i57j0l2j0i20i263i395j0i395l6.5307j1j4&sourceid=chrome&ie=UTF-8
A
Reference:
https://www.google.com/search?q=hsrp+priority&oq=hsrp+priority&aqs=chrome..69i57j0l2j0i20i263i395j0i395l6.5307j1j4&sourceid=chrome&ie=UTF-8
send
light_mode
delete
Question #27
Which MAC address is an HSRP version 2?
- A3842.4250.0000
- B0000.0C07.AC1H
- C0000.0C9F.F0C8Most Voted
- D0100.5E7F.FFFF
Correct Answer:
C
Reference:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/ipapp_fhrp/configuration/xe-3s/fhp-xe-3s-book/fhp-hsrp-v2.html
C
Reference:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/ipapp_fhrp/configuration/xe-3s/fhp-xe-3s-book/fhp-hsrp-v2.html
send
light_mode
delete
Question #28
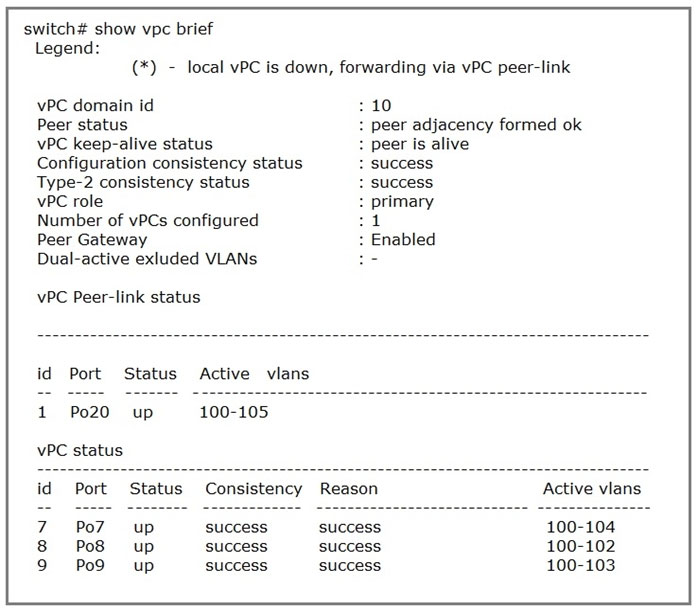
Refer to the exhibit. Which VLANs are capable to be assigned on vPC interfaces?
- A100-102
- B100-103
- C100-104
- D100-105Most Voted
Correct Answer:
D
Reference:
https://www.cisco.com/c/en/us/td/docs/switches/datacenter/nexus5000/sw/layer2/503_n2_1/503_n2_1nw/
Cisco_n5k_layer2_config_gd_rel_503_N2_1_chapter8.html
D
Reference:
https://www.cisco.com/c/en/us/td/docs/switches/datacenter/nexus5000/sw/layer2/503_n2_1/503_n2_1nw/
Cisco_n5k_layer2_config_gd_rel_503_N2_1_chapter8.html
send
light_mode
delete
Question #29
An engineer need to implement a solution that prevents loops from occurring accidentally by connecting a switch to interface Ethernet1/1. The port is designated to be used for host connectivity. Which configuration should be implemented?
- Aswitch# configure terminal switch(config)# interface Ethernet1/1 switch(config-if)# spanning-tree bpduguard enableMost Voted
- Bswitch# configure terminal switch(config)# interface Ethernet1/1 switch(config-if)# spanning-tree guard loop
- Cswitch# configure terminal switch(config)# interface Ethernet1/1 switch(config-if)# spanning-tree loopguard default
- Dswitch# configure terminal switch(config)# interface Ethernet1/1 switch(config-if)# spanning-tree bpdufilter enable
Correct Answer:
A
Reference:
https://www.cisco.com/c/m/en_us/techdoc/dc/reference/cli/nxos/commands/l2/spanning-tree-bpduguard.html#:~:text=To%20enable%20bridge%
20protocol%20data,no%20form%20of%20this%20command
.
A
Reference:
https://www.cisco.com/c/m/en_us/techdoc/dc/reference/cli/nxos/commands/l2/spanning-tree-bpduguard.html#:~:text=To%20enable%20bridge%
20protocol%20data,no%20form%20of%20this%20command
.
send
light_mode
delete
Question #30
A network engineer repeatedly saves a configuration on Catalyst switches to NVRAM using the write memory command. Which action should be taken to implement the same action on Nexus switches?
- AUse the alias command to use the write memory command.Most Voted
- BUse the wri command to use the copy running-config startup-config command.
- CUse the exit command to leave the configuration mode and save the configuration automatically.
- DUse the write memory command to save the configuration.
Correct Answer:
A
Reference:
https://community.cisco.com/t5/switching/write-command-on-nexus-switchs/td-p/1958386
A
Reference:
https://community.cisco.com/t5/switching/write-command-on-nexus-switchs/td-p/1958386
send
light_mode
delete
All Pages
