Cisco® 300-215 Exam Practice Questions (P. 5)
- Full Access (117 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #21
What is the goal of an incident response plan?
- Ato identify critical systems and resources in an organization
- Bto ensure systems are in place to prevent an attack
- Cto determine security weaknesses and recommend solutions
- Dto contain an attack and prevent it from spreading
Correct Answer:
D
Reference:
https://www.forcepoint.com/cyber-edu/incident-response
D
Reference:
https://www.forcepoint.com/cyber-edu/incident-response
send
light_mode
delete
Question #22
A security team received an alert of suspicious activity on a user's Internet browser. The user's anti-virus software indicated that the file attempted to create a fake recycle bin folder and connect to an external IP address. Which two actions should be taken by the security analyst with the executable file for further analysis?
(Choose two.)
(Choose two.)
- AEvaluate the process activity in Cisco Umbrella.
- BAnalyze the TCP/IP Streams in Cisco Secure Malware Analytics (Threat Grid).
- CEvaluate the behavioral indicators in Cisco Secure Malware Analytics (Threat Grid).
- DAnalyze the Magic File type in Cisco Umbrella.
- ENetwork Exit Localization in Cisco Secure Malware Analytics (Threat Grid).
Correct Answer:
BC
BC
send
light_mode
delete
Question #23
An employee receives an email from a "trusted" person containing a hyperlink that is malvertising. The employee clicks the link and the malware downloads. An information analyst observes an alert at the SIEM and engages the cybersecurity team to conduct an analysis of this incident in accordance with the incident response plan. Which event detail should be included in this root cause analysis?
- Aphishing email sent to the victim
- Balarm raised by the SIEM
- Cinformation from the email header
- Dalert identified by the cybersecurity team
Correct Answer:
B
B
send
light_mode
delete
Question #24
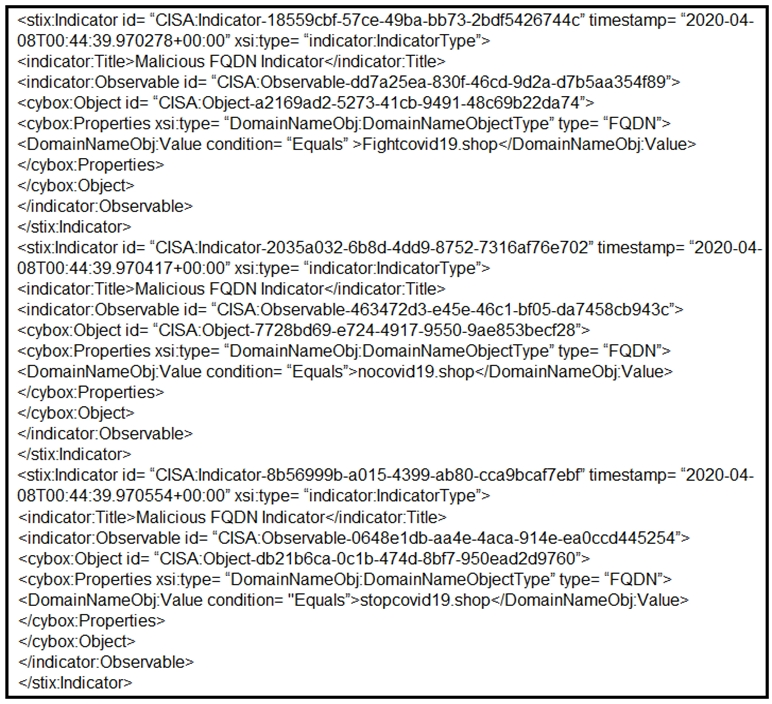
Refer to the exhibit. Which two actions should be taken based on the intelligence information? (Choose two.)
- ABlock network access to all .shop domains
- BAdd a SIEM rule to alert on connections to identified domains.
- CUse the DNS server to block hole all .shop requests.
- DBlock network access to identified domains.
- ERoute traffic from identified domains to block hole.
Correct Answer:
BD
BD
send
light_mode
delete
Question #25

Refer to the exhibit. Which two determinations should be made about the attack from the Apache access logs? (Choose two.)
- AThe attacker used r57 exploit to elevate their privilege.
- BThe attacker uploaded the word press file manager trojan.
- CThe attacker performed a brute force attack against word press and used sql injection against the backend database.
- DThe attacker used the word press file manager plugin to upoad r57.php.Most Voted
- EThe attacker logged on normally to word press admin page.Most Voted
Correct Answer:
CD
CD
send
light_mode
delete
All Pages
