Cisco® 300-215 Exam Practice Questions (P. 4)
- Full Access (117 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #16
What is the function of a disassembler?
- Aaids performing static malware analysis
- Baids viewing and changing the running state
- Caids transforming symbolic language into machine code
- Daids defining breakpoints in program execution
Correct Answer:
A
Reference:
https://scholar.google.co.in/scholar?q=disassembler+aids+performing+static+malware+analysis&hl=en&as_sdt=0&as_vis=1&oi=scholart
A
Reference:
https://scholar.google.co.in/scholar?q=disassembler+aids+performing+static+malware+analysis&hl=en&as_sdt=0&as_vis=1&oi=scholart
send
light_mode
delete
Question #17
An "unknown error code" is appearing on an ESXi host during authentication. An engineer checks the authentication logs but is unable to identify the issue.
Analysis of the vCenter agent logs shows no connectivity errors. What is the next log file the engineer should check to continue troubleshooting this error?
Analysis of the vCenter agent logs shows no connectivity errors. What is the next log file the engineer should check to continue troubleshooting this error?
- A/var/log/syslog.log
- B/var/log/vmksummary.log
- Cvar/log/shell.log
- Dvar/log/general/log
Correct Answer:
A
Reference:
https://docs.vmware.com/en/VMware-vSphere/6.7/com.vmware.vsphere.monitoring.doc/GUID-832A2618-6B11-4A28-9672-93296DA931D0.html
A
Reference:
https://docs.vmware.com/en/VMware-vSphere/6.7/com.vmware.vsphere.monitoring.doc/GUID-832A2618-6B11-4A28-9672-93296DA931D0.html
send
light_mode
delete
Question #18
Over the last year, an organization's HR department has accessed data from its legal department on the last day of each month to create a monthly activity report.
An engineer is analyzing suspicious activity alerted by a threat intelligence platform that an authorized user in the HR department has accessed legal data daily for the last week. The engineer pulled the network data from the legal department's shared folders and discovered above average-size data dumps. Which threat actor is implied from these artifacts?
An engineer is analyzing suspicious activity alerted by a threat intelligence platform that an authorized user in the HR department has accessed legal data daily for the last week. The engineer pulled the network data from the legal department's shared folders and discovered above average-size data dumps. Which threat actor is implied from these artifacts?
- Aprivilege escalation
- Binternal user errors
- Cmalicious insider
- Dexternal exfiltration
Correct Answer:
C
C
send
light_mode
delete
Question #19
A website administrator has an output of an FTP session that runs nightly to download and unzip files to a local staging server. The download includes thousands of files, and the manual process used to find how many files failed to download is time-consuming. The administrator is working on a PowerShell script that will parse a log file and summarize how many files were successfully downloaded versus ones that failed. Which script will read the contents of the file one line at a time and return a collection of objects?
- AGet-Content-Folder \\Server\FTPFolder\Logfiles\ftpfiles.log | Show-From "ERROR", "SUCCESS"
- BGet-Content ""ifmatch \\Server\FTPFolder\Logfiles\ftpfiles.log | Copy-Marked "ERROR", "SUCCESS"
- CGet-Content ""Directory \\Server\FTPFolder\Logfiles\ftpfiles.log | Export-Result "ERROR", "SUCCESS"
- DGet-Content ""Path \\Server\FTPFolder\Logfiles\ftpfiles.log | Select-String "ERROR", "SUCCESS"
Correct Answer:
D
D
send
light_mode
delete
Question #20
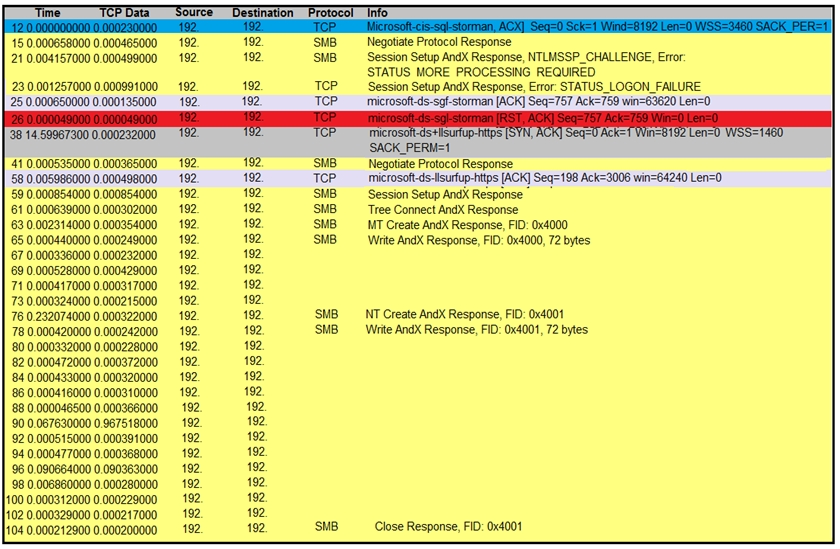
Refer to the exhibit. An engineer is analyzing a TCP stream in a Wireshark after a suspicious email with a URL. What should be determined about the SMB traffic from this stream?
- AIt is redirecting to a malicious phishing website,
- BIt is exploiting redirect vulnerability
- CIt is requesting authentication on the user site.
- DIt is sharing access to files and printers.Most Voted
Correct Answer:
B
B
send
light_mode
delete
All Pages
