Cisco® 300-215 Exam Practice Questions (P. 2)
- Full Access (117 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #6
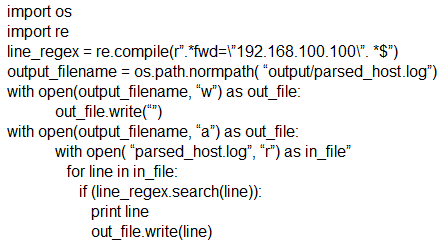
Which scripts will search a log file for the IP address of 192.168.100.100 and create an output file named parsed_host.log while printing results to the console?
A.
B.
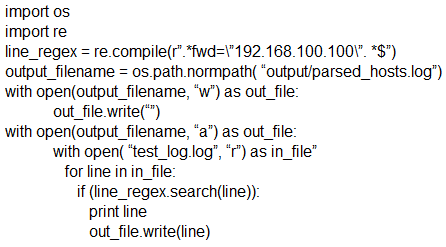
C.
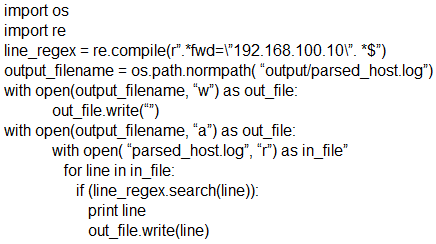
D.
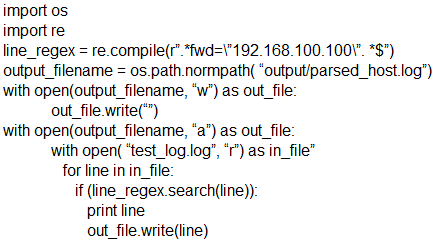
A.

B.

C.

D.

send
light_mode
delete
Question #7
What is the transmogrify anti-forensics technique?
- Ahiding a section of a malicious file in unused areas of a file
- Bsending malicious files over a public network by encapsulation
- Cconcealing malicious files in ordinary or unsuspecting places
- Dchanging the file header of a malicious file to another file type
Correct Answer:
D
Reference:
https://www.csoonline.com/article/2122329/the-rise-of-anti-forensics.html#:~:text=Transmogrify%20is%20similarly%20wise%20to,a%20file%20from%2C%20say%
2C%20
.
D
Reference:
https://www.csoonline.com/article/2122329/the-rise-of-anti-forensics.html#:~:text=Transmogrify%20is%20similarly%20wise%20to,a%20file%20from%2C%20say%
2C%20
.
send
light_mode
delete
Question #8
What is the steganography anti-forensics technique?
- Ahiding a section of a malicious file in unused areas of a file
- Bchanging the file header of a malicious file to another file type
- Csending malicious files over a public network by encapsulation
- Dconcealing malicious files in ordinary or unsuspecting places
Correct Answer:
A
https://blog.eccouncil.org/6-anti-forensic-techniques-that-every-cyber-investigator-dreads/
A
https://blog.eccouncil.org/6-anti-forensic-techniques-that-every-cyber-investigator-dreads/
send
light_mode
delete
Question #9
A security team receives reports of multiple files causing suspicious activity on users' workstations. The file attempted to access highly confidential information in a centralized file server. Which two actions should be taken by a security analyst to evaluate the file in a sandbox? (Choose two.)
- AInspect registry entries
- BInspect processes.
- CInspect file hash.
- DInspect file type.
- EInspect PE header.
Correct Answer:
BC
Reference:
https://medium.com/@Flying_glasses/top-5-ways-to-detect-malicious-file-manually-d02744f7c43a
BC
Reference:
https://medium.com/@Flying_glasses/top-5-ways-to-detect-malicious-file-manually-d02744f7c43a
send
light_mode
delete
Question #10
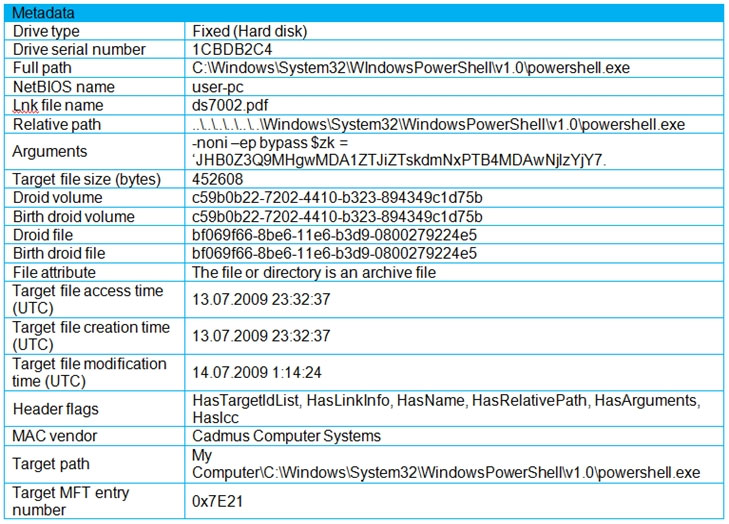
Refer to the exhibit. An engineer is analyzing a .LNK (shortcut) file recently received as an email attachment and blocked by email security as suspicious. What is the next step an engineer should take?
- ADelete the suspicious email with the attachment as the file is a shortcut extension and does not represent any threat.
- BUpload the file to a virus checking engine to compare with well-known viruses as the file is a virus disguised as a legitimate extension.
- CQuarantine the file within the endpoint antivirus solution as the file is a ransomware which will encrypt the documents of a victim.
- DOpen the file in a sandbox environment for further behavioral analysis as the file contains a malicious script that runs on execution.
Correct Answer:
D
D
send
light_mode
delete
All Pages
