Cisco® 200-310 Exam Practice Questions (P. 3)
- Full Access (776 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #21
Which of the following three options represents the components of the Teleworker Solution? (Choose three.)
- ACisco Unified IP Phone
- BCisco 880 Series Router
- CAironet Office Extend Access Point
- DCatalyst 3560 Series Switch
- ECisco 2900 Series Router
- FMPLS Layer 3 VPN
- GLeased lines
Correct Answer:
ABE
A Cisco ASR is used to terminate Teleworker solutions, not a 2900 series router.
Hybrid teleworker uses Aironet, Advanced teleworker uses 880, both use IP phones. google: "at_a_glance_c45-652500.pdf" for details
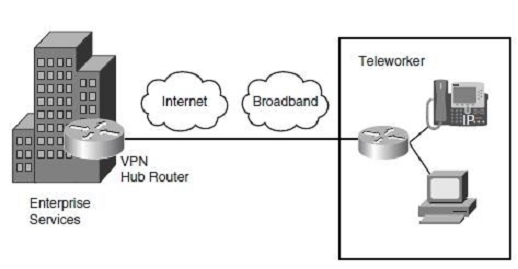
The Cisco Virtual Office Solution for the Enterprise Teleworker is implemented using the Cisco 800 series ISRs. Each ISR has integrated switch ports that then connect to the users broadband connection. The solution uses a permanent always-on IPsec VPN tunnel back to the corporate network. This architecture provides for centralized IT security management, corporate-pushed security policies, and integrated identity services. In addition, this solution supports the enterprise teleworker needs through advanced applications such as voice and video. For example, the enterprise teleworker can take advantage of toll bypass, voicemail, and advanced IP phone features not available in the PSTN.
Enterprise Teleworker Module -
The enterprise teleworker module consists of a small office or a mobile user who needs to access services of the enterprise campus. As shown in Figure 2-14, mobile users connect from their homes, hotels, or other locations using dialup or Internet access lines. VPN clients are used to allow mobile users to securely access enterprise applications. The Cisco Virtual Office solution provides a solution for teleworkers that is centrally managed using small integrated service routers
(ISR) in the VPN solution. IP phone capabilities are also provided in the Cisco Virtual Office solution, providing corporate voice services for mobile users.
ABE
A Cisco ASR is used to terminate Teleworker solutions, not a 2900 series router.
Hybrid teleworker uses Aironet, Advanced teleworker uses 880, both use IP phones. google: "at_a_glance_c45-652500.pdf" for details
The Cisco Virtual Office Solution for the Enterprise Teleworker is implemented using the Cisco 800 series ISRs. Each ISR has integrated switch ports that then connect to the users broadband connection. The solution uses a permanent always-on IPsec VPN tunnel back to the corporate network. This architecture provides for centralized IT security management, corporate-pushed security policies, and integrated identity services. In addition, this solution supports the enterprise teleworker needs through advanced applications such as voice and video. For example, the enterprise teleworker can take advantage of toll bypass, voicemail, and advanced IP phone features not available in the PSTN.
Enterprise Teleworker Module -
The enterprise teleworker module consists of a small office or a mobile user who needs to access services of the enterprise campus. As shown in Figure 2-14, mobile users connect from their homes, hotels, or other locations using dialup or Internet access lines. VPN clients are used to allow mobile users to securely access enterprise applications. The Cisco Virtual Office solution provides a solution for teleworkers that is centrally managed using small integrated service routers
(ISR) in the VPN solution. IP phone capabilities are also provided in the Cisco Virtual Office solution, providing corporate voice services for mobile users.

send
light_mode
delete
Question #22
Which three types of WAN topologies can be deployed in the Service Provider Module? (Choose three.)
send
light_mode
delete
Question #23
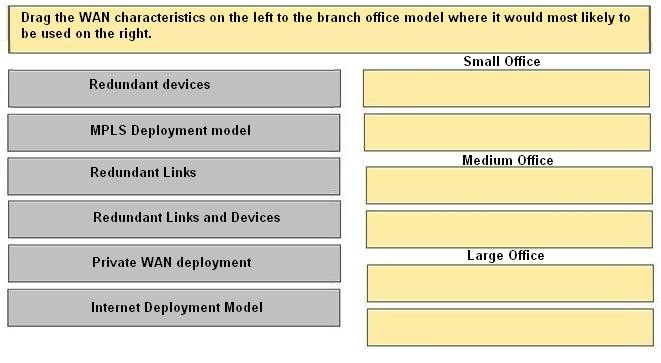
DRAG DROP -
Drag the WAN characteristics on the left to the branch office model where it would most likely to be used on the right.
Select and Place:
Drag the WAN characteristics on the left to the branch office model where it would most likely to be used on the right.
Select and Place:

Correct Answer:
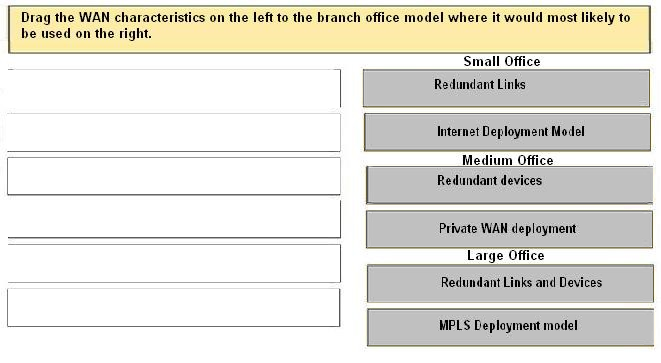
Small Branch Design -
is recommended for branch offices that do not require hardware redundancy and that have a small user base supporting up to 50 users.
This profile consists of an access router providing WAN services and connections for the LAN services.
The Layer 3 WAN services are based on the WAN and Internet deployment model. A T1 is used for the primary link, and an ADSL secondary link is used for backup. Other network fundamentals are supported, such as EIGRP, floating static routes, and QoS for bandwidth protection.
Medium Branch Design -
is recommended for branch offices of 50 to 100 users, which is similar to the small branch but with an additional access router in the
WAN edge (slightly larger) allowing for redundancy services.
Large Branch Design -
is the largest of the branch profiles, supporting between 100 and 1000 users. This design profile is similar to the medium branch design in that it also provides dual access routers in the WAN edge. In addition, dual Adaptive Security Appliances (ASA) are used for stateful firewall filtering, and dual distribution switches provide the multilayer switching component. The WAN services use an MPLS deployment model with dual WAN links into the WAN cloud.
Cisco Press CCDA 640-864 Official Certification Guide Fourth Edition, Chapter 7

Small Branch Design -
is recommended for branch offices that do not require hardware redundancy and that have a small user base supporting up to 50 users.
This profile consists of an access router providing WAN services and connections for the LAN services.
The Layer 3 WAN services are based on the WAN and Internet deployment model. A T1 is used for the primary link, and an ADSL secondary link is used for backup. Other network fundamentals are supported, such as EIGRP, floating static routes, and QoS for bandwidth protection.
Medium Branch Design -
is recommended for branch offices of 50 to 100 users, which is similar to the small branch but with an additional access router in the
WAN edge (slightly larger) allowing for redundancy services.
Large Branch Design -
is the largest of the branch profiles, supporting between 100 and 1000 users. This design profile is similar to the medium branch design in that it also provides dual access routers in the WAN edge. In addition, dual Adaptive Security Appliances (ASA) are used for stateful firewall filtering, and dual distribution switches provide the multilayer switching component. The WAN services use an MPLS deployment model with dual WAN links into the WAN cloud.
Cisco Press CCDA 640-864 Official Certification Guide Fourth Edition, Chapter 7
send
light_mode
delete
Question #24
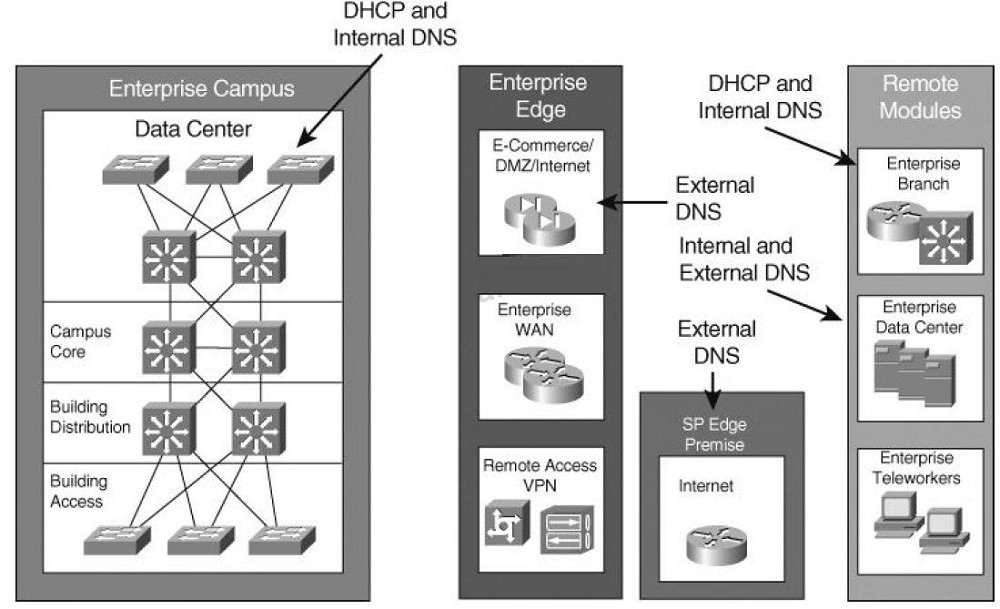
Which statement describes the recommended deployment of DNS and DHCP servers in the Cisco Network Architecture for the Enterprise?
- APlace the DHCP and DNS servers in the Enterprise Campus Access layer and Enterprise branch.
- BPlace the DHCP and DNS servers in the Enterprise Campus Server Farm layer and Enterprise branch.
- CPlace the DHCP server in the Enterprise Campus Core layer and Remote Access_VPN module with the DNS server in the Internet Connectivity module.
- DPlace the DHCP server in the Enterprise Campus Distribution layer with the DNS server in the Internet Connectivity module.
Correct Answer:
B
For the Enterprise Campus, DHCP and internal DNS servers should be located in the Server Farm and they should be redundant. External DNS servers can be placed redundantly at the service provider facility and at the Enterprise branch.
B
For the Enterprise Campus, DHCP and internal DNS servers should be located in the Server Farm and they should be redundant. External DNS servers can be placed redundantly at the service provider facility and at the Enterprise branch.

send
light_mode
delete
Question #25
Your company's Cisco routers are operating with EIGRP. You need to join networks with an acquisition's heterogeneous routers at 3 sites, operating with EIGRP and OSPF. Which describes the best practice for routing protocol deployment?
- AApply OSPF throughout both networks
- BApply one-way redistribution exclusively at each location
- CApply two-way redistribution exclusively at each location
- DApply two-way redistribution at each location with a route filter at only one location
- EApply two-way redistribution at each location with a route filter at each location
- FApply EIGRP with the same autonomous system throughout both networks E
Correct Answer:
Explanation
Without filters there is possibility of routing loops.
Link: http://www.cisco.com/en/US/tech/tk365/technologies_tech_note09186a008009487e.shtml
Explanation
Without filters there is possibility of routing loops.
Link: http://www.cisco.com/en/US/tech/tk365/technologies_tech_note09186a008009487e.shtml
send
light_mode
delete
Question #26
Which two routing protocols converge most quickly? (Choose two.)
send
light_mode
delete
Question #27
Which of these is the equation used to derive a 64 Kbps bit rate?
- A2 x 8 kHz x 4-bit code words
- B8 kHz x 8-bit code words
- C2 x 4-bit code words x 8 kHz
- D2 x 4 kHz x 8-bit code words
Correct Answer:
D
While the human ear can sense sounds from 20 to 20, 000 Hz, and speech encompasses sounds from about 200 to 9000 Hz, the telephone channel was designed to operate at about 300 to 3400 Hz. This economical range carries enough fidelity to allow callers to identify the party at the far end and sense their mood. Nyquist decided to extend the digitization to 4000 Hz, to capture higher-frequency sounds that the telephone channel may deliver. Therefore, the highest frequency for voice is 4000 Hz. According to Nyquist theory, we must double the highest frequency, so 2x4kHz = 8kHz.
Each sample will be encoded into a 8-bit code. Therefore 8kHz x 8-bit code = 64 Kbps (notice about the unit Kbps: 8kHz = 8000 samples per second so 8000 x 8- bit = 64000 bit per second = 64 Kilobit per second = 64 Kbps)
Link: http://encyclopedia2.thefreedictionary.com/Nyquist+theorem
Note:
Nyquist theory:
"When sampling a signal (e.g., converting from an analog signal to digital), the sampling frequency must be greater than twice the bandwidth of the input signal in order to be able to reconstruct the original perfectly from the sampled version."
D
While the human ear can sense sounds from 20 to 20, 000 Hz, and speech encompasses sounds from about 200 to 9000 Hz, the telephone channel was designed to operate at about 300 to 3400 Hz. This economical range carries enough fidelity to allow callers to identify the party at the far end and sense their mood. Nyquist decided to extend the digitization to 4000 Hz, to capture higher-frequency sounds that the telephone channel may deliver. Therefore, the highest frequency for voice is 4000 Hz. According to Nyquist theory, we must double the highest frequency, so 2x4kHz = 8kHz.
Each sample will be encoded into a 8-bit code. Therefore 8kHz x 8-bit code = 64 Kbps (notice about the unit Kbps: 8kHz = 8000 samples per second so 8000 x 8- bit = 64000 bit per second = 64 Kilobit per second = 64 Kbps)
Link: http://encyclopedia2.thefreedictionary.com/Nyquist+theorem
Note:
Nyquist theory:
"When sampling a signal (e.g., converting from an analog signal to digital), the sampling frequency must be greater than twice the bandwidth of the input signal in order to be able to reconstruct the original perfectly from the sampled version."
send
light_mode
delete
Question #28
Which one of these statements is an example of how trust and identity management solutions should be deployed in the enterprise campus network?
- AAuthentication validation should be deployed as close to the data center as possible.
- BUse the principle of top-down privilege, which means that each subject should have the privileges that are necessary to perform their defined tasks, as well as all the tasks for those roles below them.
- CMixed ACL rules, using combinations of specific sources and destinations, should be applied as close to the source as possible.
- DFor ease of management, practice defense in isolation - security mechanisms should be in place one time, in one place.
Correct Answer:
C
Validating user authentication should be implemented as close to the source as possible, with an emphasis on strong authentication for access from untrusted networks. Access rules should enforce policy deployed throughout the network with the following guidelines:
✑ Source-specific rules with any type destinations should be applied as close to the source as possible.
✑ Destination-specific rules with any type sources should be applied as close to the destination as possible.
✑ Mixed rules integrating both source and destination should be used as close to the source as possible.
An integral part of identity and access control deployments is to allow only the necessary access. Highly distributed rules allow for greater granularity and scalability but, unfortunately, increase the management complexity. On the other hand, centralized rule deployment eases management but lacks flexibility and scalability.
Practicing "defense in depth" by using security mechanisms that back each other up is an important concept to understand. For example, the perimeter Internet routers should use ACLs to filter packets in addition to the firewall inspecting packets at a deeper level.
Cisco Press CCDA 640-864 Official Certification Guide Fourth Edition, Chapter 13
C
Validating user authentication should be implemented as close to the source as possible, with an emphasis on strong authentication for access from untrusted networks. Access rules should enforce policy deployed throughout the network with the following guidelines:
✑ Source-specific rules with any type destinations should be applied as close to the source as possible.
✑ Destination-specific rules with any type sources should be applied as close to the destination as possible.
✑ Mixed rules integrating both source and destination should be used as close to the source as possible.
An integral part of identity and access control deployments is to allow only the necessary access. Highly distributed rules allow for greater granularity and scalability but, unfortunately, increase the management complexity. On the other hand, centralized rule deployment eases management but lacks flexibility and scalability.
Practicing "defense in depth" by using security mechanisms that back each other up is an important concept to understand. For example, the perimeter Internet routers should use ACLs to filter packets in addition to the firewall inspecting packets at a deeper level.
Cisco Press CCDA 640-864 Official Certification Guide Fourth Edition, Chapter 13
send
light_mode
delete
Question #29
With deterministic Wireless LAN Controller redundancy design, the different options available to the designer have their own strengths. Which one of these statements is an example of such a strength?
- ADynamic load balancing, or salt-and-pepper access point design, avoids the potential impact of oversubscription on aggregate network performance.
- BN+N redundancy configuration allows logically grouping access points on controllers to minimize intercontroller roaming events.
- CN+N+1 redundancy configuration has the least impact to system management because all of the controllers are colocated in an NOC or data center.
- DN+1 redundancy configuration uses Layer 3 intercontroller roaming, maintaining traffic on the same subnet for more efficiency.
Correct Answer:
B
With such an arrangement there is no complex mesh of access points & controllers.
Link: http://www.cisco.com/web/learning/le31/le46/cln/qlm/CCDA/design/understanding-wireless-network-controller-technology-3/player.html
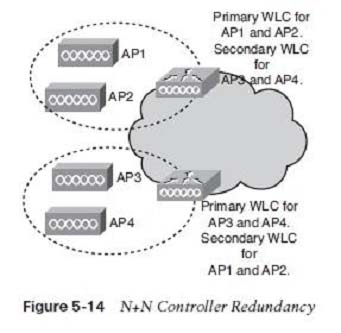
N+N WLC Redundancy -
With N+N redundancy, shown in Figure 5-14, an equal number of controllers hack up each other. For example, a pair of WLCs on one floor serves as a backup to a second pair on another floor. The top WLC is primary for API and AP2 and secondary for AP3 and AP4. The bottom WLC is primary for AP3 and AP4 and secondary for API and AP2. There should be enough capacity on each controller to manage a failover situation.
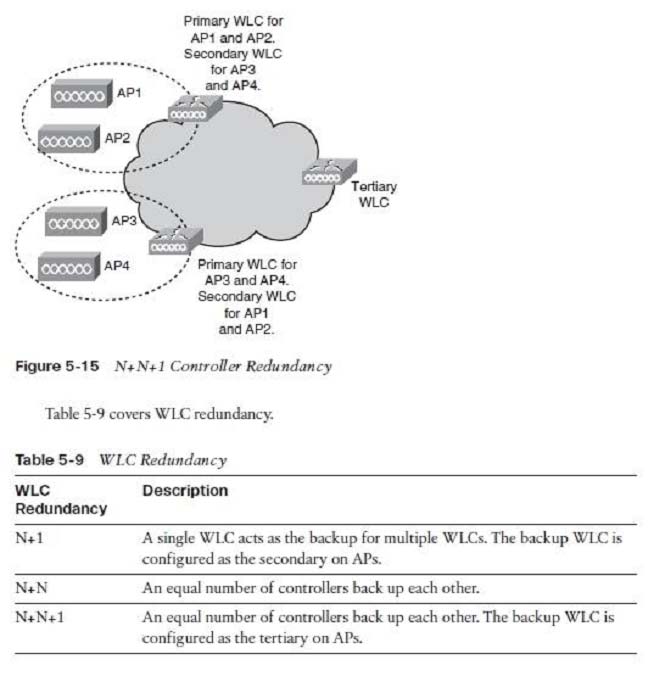
N+N+1 WLC Redundancy -
With N+N+1 redundancy, shown in Figure 5-15, an equal number of controllers back up each other (as with N+N), plus a backup WLC is configured as the tertiary
WLC for the APs. N+N+1 redundancy functions the same as N+N redundancy plus a tertiary controller that backs up the secondary controllers. The tertiary WLC is placed in the data center or network operations center
B
With such an arrangement there is no complex mesh of access points & controllers.
Link: http://www.cisco.com/web/learning/le31/le46/cln/qlm/CCDA/design/understanding-wireless-network-controller-technology-3/player.html
N+N WLC Redundancy -
With N+N redundancy, shown in Figure 5-14, an equal number of controllers hack up each other. For example, a pair of WLCs on one floor serves as a backup to a second pair on another floor. The top WLC is primary for API and AP2 and secondary for AP3 and AP4. The bottom WLC is primary for AP3 and AP4 and secondary for API and AP2. There should be enough capacity on each controller to manage a failover situation.

N+N+1 WLC Redundancy -
With N+N+1 redundancy, shown in Figure 5-15, an equal number of controllers back up each other (as with N+N), plus a backup WLC is configured as the tertiary
WLC for the APs. N+N+1 redundancy functions the same as N+N redundancy plus a tertiary controller that backs up the secondary controllers. The tertiary WLC is placed in the data center or network operations center

send
light_mode
delete
Question #30
When designing the threat detection and mitigation portion for the enterprise data center network, which of the following would be the most appropriate solution to consider?
- A802.1X
- BACLs in the core layer
- CCisco Security MARS
- DCisco Firewall Services Module
Correct Answer:
C
C
send
light_mode
delete
All Pages
