Cisco® 100-105 Exam Practice Questions (P. 5)
- Full Access (724 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #41
Which statement about unicast frame forwarding on a switch is true?
- AThe TCAM table stores destination MAC addresses.
- BIf the destination MAC address is unknown, the frame is flooded to every port that is configured in the same VLAN except on the port that it was received on.
- CThe CAM table is used to determine whether traffic is permitted or denied on a switch.
- DThe source address is used to determine the switch port to which a frame is forwarded.
Correct Answer:
B
B
send
light_mode
delete
Question #42
By default, how many MAC addresses are permitted to be learned on a switch port with port-security enabled?
- A8
- B2
- C1
- D0
Correct Answer:
C
Reference: http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst6500/ios/12-2SX/configuration/guide/book/port_sec.pdf
C
Reference: http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst6500/ios/12-2SX/configuration/guide/book/port_sec.pdf
send
light_mode
delete
Question #43
Which dynamic routing protocol uses only the hop count to determine the best path to a destination?
- AIGRP
- BRIP
- CEIGRP
- DOSPF
Correct Answer:
B
Determining the best path involves the evaluation of multiple paths to the same destination network and selecting the optimum or shortest path to reach that network. Whenever multiple paths to the same network exist, each path uses a different exit interface on the router to reach that network.
The best path is selected by a routing protocol based on the value or metric it uses to determine the distance to reach a network. A metric is the quantitative value used to measure the distance to a given network. The best path to a network is the path with the lowest metric.
Dynamic routing protocols typically use their own rules and metrics to build and update routing tables. The routing algorithm generates a value, or a metric, for each path through the network. Metrics can be based on either a single characteristic or several characteristics of a path. Some routing protocols can base route selection on multiple metrics, combining them into a single metric. The following lists some dynamic protocols and the metrics they use:
Routing Information Protocol (RIP): Hop count
Open Shortest Path First (OSPF): Cisco routers use a cost based on cumulative bandwidth from source to destination
Enhanced Interior Gateway Routing Protocol (EIGRP): Bandwidth, delay, load, reliability
B
Determining the best path involves the evaluation of multiple paths to the same destination network and selecting the optimum or shortest path to reach that network. Whenever multiple paths to the same network exist, each path uses a different exit interface on the router to reach that network.
The best path is selected by a routing protocol based on the value or metric it uses to determine the distance to reach a network. A metric is the quantitative value used to measure the distance to a given network. The best path to a network is the path with the lowest metric.
Dynamic routing protocols typically use their own rules and metrics to build and update routing tables. The routing algorithm generates a value, or a metric, for each path through the network. Metrics can be based on either a single characteristic or several characteristics of a path. Some routing protocols can base route selection on multiple metrics, combining them into a single metric. The following lists some dynamic protocols and the metrics they use:
Routing Information Protocol (RIP): Hop count
Open Shortest Path First (OSPF): Cisco routers use a cost based on cumulative bandwidth from source to destination
Enhanced Interior Gateway Routing Protocol (EIGRP): Bandwidth, delay, load, reliability
send
light_mode
delete
Question #44
Refer to the exhibit.
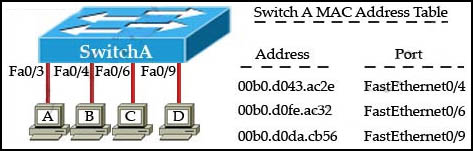
The exhibit is showing the topology and the MAC address table. Host A sends a data frame to host D. Which option describes what the switch will do when it receives the frame from host A?

The exhibit is showing the topology and the MAC address table. Host A sends a data frame to host D. Which option describes what the switch will do when it receives the frame from host A?
- AThe switch will flood the frame out of all ports except for port Fa0/3.
- BThe switch will add the destination address of the frame to the MAC address table and forward the frame to host D.
- CThe switch will add the source address and port to the MAC address table and forward the frame to host D.
- DThe switch will discard the frame and send an error message back to host A.
Correct Answer:
C
When switch receives the data frame from the host not having the MAC address already on the MAC table, it will add the MAC address to source port on MAC address table and sends the data frame.
C
When switch receives the data frame from the host not having the MAC address already on the MAC table, it will add the MAC address to source port on MAC address table and sends the data frame.
send
light_mode
delete
Question #45
Refer to the exhibit.
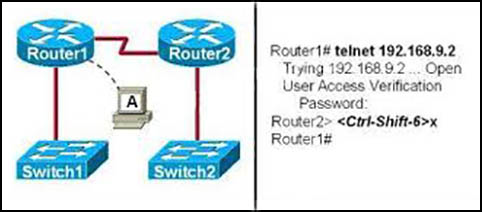
If the resume command is entered after the sequence that is shown in the exhibit, which router prompt will be displayed?

If the resume command is entered after the sequence that is shown in the exhibit, which router prompt will be displayed?
- ARouter2#
- BRouter2>
- CRouter1#
- DRouter1>
Correct Answer:
B
If the enter command is issued the session will resume back to what it was, which is the Router2> prompt.
B
If the enter command is issued the session will resume back to what it was, which is the Router2> prompt.
send
light_mode
delete
Question #46
Which feature allows a device to use a switch port that is configured for half-duplex to access the network?
- ACSMA/CD
- BIGMP
- Cport security
- Dsplit horizon
Correct Answer:
A
Ethernet began as a local area network technology that provided a half-duplex shared channel for stations connected to coaxial cable segments linked with signal repeaters. In this appendix, we take a detailed look at the half-duplex shared- channel mode of operation, and at the CSMA/CD mechanism that makes it work. In the original half-duplex mode, the CSMA/CD protocol allows a set of stations to compete for access to a shared Ethernet channel in a fair and equitable manner.
The protocol's rules determine the behavior of Ethernet stations, including when they are allowed to transmit a frame onto a shared Ethernet channel, and what to do when a collision occurs. Today, virtually all devices are connected to Ethernet switch ports over full-duplex media, such as twisted-pair cables. On this type of connection, assuming that both devices can support the full-duplex mode of operation and that Auto-Negotiation (AN) is enabled, the AN protocol will automatically select the highest-performance mode of operation supported by the devices at each end of the link. That will result in full-duplex mode for the vast majority of
Ethernet connections with modern interfaces that support full duplex and AN.
A
Ethernet began as a local area network technology that provided a half-duplex shared channel for stations connected to coaxial cable segments linked with signal repeaters. In this appendix, we take a detailed look at the half-duplex shared- channel mode of operation, and at the CSMA/CD mechanism that makes it work. In the original half-duplex mode, the CSMA/CD protocol allows a set of stations to compete for access to a shared Ethernet channel in a fair and equitable manner.
The protocol's rules determine the behavior of Ethernet stations, including when they are allowed to transmit a frame onto a shared Ethernet channel, and what to do when a collision occurs. Today, virtually all devices are connected to Ethernet switch ports over full-duplex media, such as twisted-pair cables. On this type of connection, assuming that both devices can support the full-duplex mode of operation and that Auto-Negotiation (AN) is enabled, the AN protocol will automatically select the highest-performance mode of operation supported by the devices at each end of the link. That will result in full-duplex mode for the vast majority of
Ethernet connections with modern interfaces that support full duplex and AN.
send
light_mode
delete
Question #47
Which component of a routing table entry represents the subnet mask?
- Arouting protocol code
- Bprefix
- Cmetric
- Dnetwork mask
Correct Answer:
D
IP Routing Table Entry Types -
An entry in the IP routing table contains the following information in the order presented:
Network ID. The network ID or destination corresponding to the route. The network ID can be class-based, subnet, or supernet network ID, or an IP address for a host route.
Network Mask. The mask that is used to match a destination IP address to the network ID.
Next Hop. The IP address of the next hop.
Interface. An indication of which network interface is used to forward the IP packet.
Metric. A number used to indicate the cost of the route so the best route among possible multiple routes to the same destination can be selected. A common use of the metric is to indicate the number of hops (routers crossed) to the network ID.
Routing table entries can be used to store the following types of routes:
Directly Attached Network IDs.
Routes for network IDs that are directly attached. For directly attached networks, the Next Hop field can be blank or contain the IP address of the interface on that network.
Remote Network IDs.
Routes for network IDs that are not directly attached but are available across other routers. For remote networks, the Next Hop field is the IP address of a local router in between the forwarding node and the remote network.
Host Routes.
A route to a specific IP address.
Host routes allow routing to occur on a per- IP address basis. For host routes, the network ID is the IP address of the specified host and the network mask is
255.255.255.255.
Default Route.
The default route is designed to be used when a more specific network ID or host route is not found. The default route network ID is 0.0.0.0 with the network mask of 0.0.0.0.
D
IP Routing Table Entry Types -
An entry in the IP routing table contains the following information in the order presented:
Network ID. The network ID or destination corresponding to the route. The network ID can be class-based, subnet, or supernet network ID, or an IP address for a host route.
Network Mask. The mask that is used to match a destination IP address to the network ID.
Next Hop. The IP address of the next hop.
Interface. An indication of which network interface is used to forward the IP packet.
Metric. A number used to indicate the cost of the route so the best route among possible multiple routes to the same destination can be selected. A common use of the metric is to indicate the number of hops (routers crossed) to the network ID.
Routing table entries can be used to store the following types of routes:
Directly Attached Network IDs.
Routes for network IDs that are directly attached. For directly attached networks, the Next Hop field can be blank or contain the IP address of the interface on that network.
Remote Network IDs.
Routes for network IDs that are not directly attached but are available across other routers. For remote networks, the Next Hop field is the IP address of a local router in between the forwarding node and the remote network.
Host Routes.
A route to a specific IP address.
Host routes allow routing to occur on a per- IP address basis. For host routes, the network ID is the IP address of the specified host and the network mask is
255.255.255.255.
Default Route.
The default route is designed to be used when a more specific network ID or host route is not found. The default route network ID is 0.0.0.0 with the network mask of 0.0.0.0.
send
light_mode
delete
Question #48
Which technology supports the stateless assignment of IPv6 addresses?
- ADNS
- BDHCPv6
- CDHCP
- Dautoconfiguration D
Correct Answer:
Explanation
Stateless Auto Configuration is an important feature offered by the IPv6 protocol. It allows the various devices attached to an IPv6 network to connect to the
Internet using the Stateless Auto Configuration without requiring any intermediate IP support in the form of a Dynamic Host Configuration Protocol (DHCP) server. http://ipv6.com/articles/general/Stateless-Auto-Configuration.htm
Explanation
Stateless Auto Configuration is an important feature offered by the IPv6 protocol. It allows the various devices attached to an IPv6 network to connect to the
Internet using the Stateless Auto Configuration without requiring any intermediate IP support in the form of a Dynamic Host Configuration Protocol (DHCP) server. http://ipv6.com/articles/general/Stateless-Auto-Configuration.htm
send
light_mode
delete
Question #49
When enabled, which feature prevents routing protocols from sending hello messages on an interface?
- Avirtual links
- Bpassive-interface
- Cdirected neighbors
- DOSPF areas
Correct Answer:
B
You can use the passive-interface command in order to control the advertisement of routing information. The command enables the suppression of routing updates over some interfaces while it allows updates to be exchanged normally over other interfaces. With most routing protocols, the passive-interface command restricts outgoing advertisements only. But, when used with Enhanced Interior Gateway Routing Protocol (EIGRP), the effect is slightly different. This document demonstrates that use of the passive-interface command in EIGRP suppresses the exchange of hello packets between two routers, which results in the loss of their neighbor relationship. This stops not only routing updates from being advertised, but it also suppresses incoming routing updates. This document also discusses the configuration required in order to allow the suppression of outgoing routing updates, while it also allows incoming routing updates to be learned normally from the neighbor.
B
You can use the passive-interface command in order to control the advertisement of routing information. The command enables the suppression of routing updates over some interfaces while it allows updates to be exchanged normally over other interfaces. With most routing protocols, the passive-interface command restricts outgoing advertisements only. But, when used with Enhanced Interior Gateway Routing Protocol (EIGRP), the effect is slightly different. This document demonstrates that use of the passive-interface command in EIGRP suppresses the exchange of hello packets between two routers, which results in the loss of their neighbor relationship. This stops not only routing updates from being advertised, but it also suppresses incoming routing updates. This document also discusses the configuration required in order to allow the suppression of outgoing routing updates, while it also allows incoming routing updates to be learned normally from the neighbor.
send
light_mode
delete
Question #50
Refer to the exhibit.
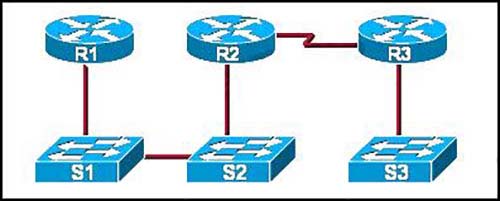
If CDP is enabled on all devices and interfaces, which devices will appear in the output of a show cdp neighbors command issued from R2?

If CDP is enabled on all devices and interfaces, which devices will appear in the output of a show cdp neighbors command issued from R2?
- AR1, S1, S2, R3 and S3
- BR2 and R3
- CR3 and S2
- DR1 and R3
- ER1, S1, S2, and R3
Correct Answer:
C
A Cisco device enabled with CDP sends out periodic interface updates to a multicast address in order to make itself known to neighbors. Since it is a layer two protocol, these packets are not routed. So the devices detected would be immediate connected neighbors.
C
A Cisco device enabled with CDP sends out periodic interface updates to a multicast address in order to make itself known to neighbors. Since it is a layer two protocol, these packets are not routed. So the devices detected would be immediate connected neighbors.
send
light_mode
delete
All Pages
