Cisco® 100-105 Exam Practice Questions (P. 4)
- Full Access (724 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #31
Which network topology allows all traffic to flow through a central hub?
- Abus
- Bstar
- Cmesh
- Dring
Correct Answer:
B
Star topology is the arrangement of the computers in such a way that all the terminals or work stations are connected to the main central hub. The terminals are referred to as the clients and the main central hub is referred to as the switch. It is the easiest way of arranging a network topology with one central main computer connected to several other functioning terminals. All the network traffic passes through the central device and all the data transmission occurs through the main switch as well as all the hub acts as the signal repeater. One advantage of such an arrangement is the simplicity and the ease with which you can add additional nodes. The disadvantage is that if an error occurs in the central hub the whole network shuts down.
Reference: http://www.certiology.com/computing/computer-networking/network-topology.html
B
Star topology is the arrangement of the computers in such a way that all the terminals or work stations are connected to the main central hub. The terminals are referred to as the clients and the main central hub is referred to as the switch. It is the easiest way of arranging a network topology with one central main computer connected to several other functioning terminals. All the network traffic passes through the central device and all the data transmission occurs through the main switch as well as all the hub acts as the signal repeater. One advantage of such an arrangement is the simplicity and the ease with which you can add additional nodes. The disadvantage is that if an error occurs in the central hub the whole network shuts down.

Reference: http://www.certiology.com/computing/computer-networking/network-topology.html
send
light_mode
delete
Question #32
Which two statements are true regarding ICMP packets? (Choose two.)
- AThey are encapsulated within IP datagrams.
- BThey guarantee datagram delivery.
- CTRACERT uses ICMP packets.
- DThey acknowledge receipt of TCP segments.
- EThey are encapsulated within UDP datagrams.
Correct Answer:
AC
Ping may be used to find out whether the local machines are connected to the network or whether a remote site is reachable. This tool is a common network tool for determining the network connectivity which uses ICMP protocol instead of TCP/IP and UDP/IP. This protocol is usually associated with the network management tools which provide network information to network administrators, such as ping and traceroute (the later also uses the UDP/IP protocol).
ICMP is quite different from the TCP/IP and UDP/IP protocols. No source and destination ports are included in its packets. Therefore, usual packet-filtering rules for TCP/IP and UDP/IP are not applicable. Fortunately, a special "signature" known as the packet's Message type is included for denoting the purposes of the
ICMP packet. Most commonly used message types are namely, 0, 3, 4, 5, 8, 11, and 12 which represent echo reply, destination unreachable, source quench, redirect, echo request, time exceeded, and parameter problem respectively.
In the ping service, after receiving the ICMP "echo request" packet from the source location, the destination.
AC
Ping may be used to find out whether the local machines are connected to the network or whether a remote site is reachable. This tool is a common network tool for determining the network connectivity which uses ICMP protocol instead of TCP/IP and UDP/IP. This protocol is usually associated with the network management tools which provide network information to network administrators, such as ping and traceroute (the later also uses the UDP/IP protocol).
ICMP is quite different from the TCP/IP and UDP/IP protocols. No source and destination ports are included in its packets. Therefore, usual packet-filtering rules for TCP/IP and UDP/IP are not applicable. Fortunately, a special "signature" known as the packet's Message type is included for denoting the purposes of the
ICMP packet. Most commonly used message types are namely, 0, 3, 4, 5, 8, 11, and 12 which represent echo reply, destination unreachable, source quench, redirect, echo request, time exceeded, and parameter problem respectively.
In the ping service, after receiving the ICMP "echo request" packet from the source location, the destination.
send
light_mode
delete
Question #33
Which method does a connected trunk port use to tag VLAN traffic?
- AIEEE 802.1w
- BIEEE 802.1D
- CIEEE 802.1Q
- DIEEE 802.1p
Correct Answer:
C
IEEE 802.1Q is the networking standard that supports virtual LANs (VLANs) on an Ethernet network. When a frame enters the VLAN-aware portion of the network
(a trunk link, for example), a VLAN ID tag is added to represent the VLAN membership of that frame. The picture below shows how VLAN tag is added and removed while going through the network. http://www.cisco.com/c/en/us/support/docs/lan-switching/8021q/17056-741-4.html
C
IEEE 802.1Q is the networking standard that supports virtual LANs (VLANs) on an Ethernet network. When a frame enters the VLAN-aware portion of the network
(a trunk link, for example), a VLAN ID tag is added to represent the VLAN membership of that frame. The picture below shows how VLAN tag is added and removed while going through the network. http://www.cisco.com/c/en/us/support/docs/lan-switching/8021q/17056-741-4.html
send
light_mode
delete
Question #34
On which type of device is every port in the same collision domain?
- Aa router
- Ba Layer 2 switch
- Cswitch
- Da hub
- Ea Layer 3 switch
Correct Answer:
D
The definition of a collision domain is a set of LAN devices whose frames could collide with one another. This happens with hubs, bridges, repeaters and wireless access points as only one device can send and receive. If more than one device tries sending or receiving, the information is lost and irrecoverable it will need to be resent. This can slow down network performance along with making it a security threat.
D
The definition of a collision domain is a set of LAN devices whose frames could collide with one another. This happens with hubs, bridges, repeaters and wireless access points as only one device can send and receive. If more than one device tries sending or receiving, the information is lost and irrecoverable it will need to be resent. This can slow down network performance along with making it a security threat.
send
light_mode
delete
Question #35
Which option is the default switch port port-security violation mode?
- Ashutdown
- Bprotect
- Cshutdown vlan
- Drestrict
Correct Answer:
A
Shutdown - This mode is the default violation mode; when in this mode, the switch will automatically force the switchport into an error disabled (err-disable) state when a violation occurs. While in this state, the switchport forwards no traffic. The switchport can be brought out of this error disabled state by issuing the errdisable recovery cause CLI command or by disabling and reenabling the switchport.
Shutdown VLAN - This mode mimics the behavior of the shutdown mode but limits the error disabled state the specific violating VLAN.
A
Shutdown - This mode is the default violation mode; when in this mode, the switch will automatically force the switchport into an error disabled (err-disable) state when a violation occurs. While in this state, the switchport forwards no traffic. The switchport can be brought out of this error disabled state by issuing the errdisable recovery cause CLI command or by disabling and reenabling the switchport.
Shutdown VLAN - This mode mimics the behavior of the shutdown mode but limits the error disabled state the specific violating VLAN.
send
light_mode
delete
Question #36
Refer to the exhibit.
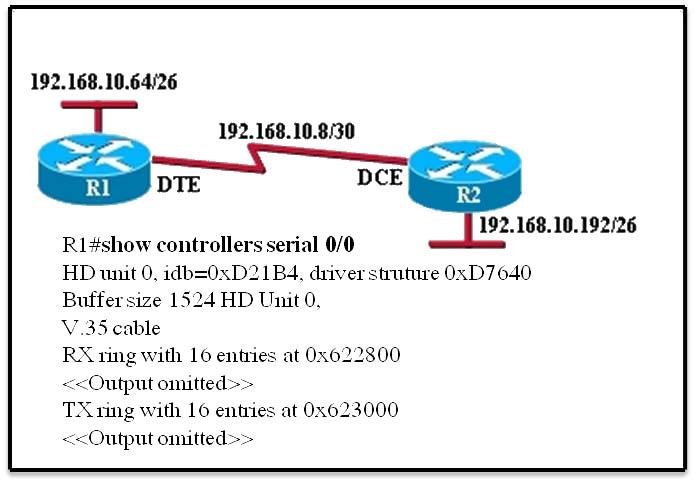
An administrator cannot connect from R1 to R2. To troubleshoot this problem, the administrator has entered the command shown in the exhibit. Based on the output shown, what could be the problem?

An administrator cannot connect from R1 to R2. To troubleshoot this problem, the administrator has entered the command shown in the exhibit. Based on the output shown, what could be the problem?
- AThe serial interface is configured for the wrong frame size.
- BThe serial interface does not have a cable attached.
- CThe serial interface has the wrong type of cable attached.
- DThe serial interface has a full buffer.
- EThe serial interface is configured for half duplex.
Correct Answer:
C
Since the output is not forthcoming it shows that the type of cable attached is wrong, though the cable is connected since it shows the cable type. According to the figure DTE cable should connect to R1 on interface but while examining using show controllers serial 0/0 command it showing that a DCE is connected so the wrong type of cable is being used.
C
Since the output is not forthcoming it shows that the type of cable attached is wrong, though the cable is connected since it shows the cable type. According to the figure DTE cable should connect to R1 on interface but while examining using show controllers serial 0/0 command it showing that a DCE is connected so the wrong type of cable is being used.
send
light_mode
delete
Question #37
Which statement about native VLAN traffic is true?
- ACisco Discovery Protocol traffic travels on the native VLAN by default.
- BTraffic on the native VLAN is tagged with 1 by default.
- CControl plane traffic is blocked on the native VLAN.
- DThe native VLAN is typically disabled for security reasons.
Correct Answer:
A
The native VLAN is the VLAN that is configured for packets that dont have a tag. The default native VLAN on all Cisco Switches is VLAN 1. It is always enabled by default. These settings can all be changed: That is: you can designate a different VLAN as the native VLAN, disable VLAN 1, etc. Knowing that, we can eliminate
D) as the correct answer because it is enabled by default. We can also eliminate B) because Native VLAN packets dont get tags by default (you can change this).
Finally, Control Plane traffic is never blocked on Native VLAN 1, and even if you change the Native VLAN, the control plane traffic still comes across VLAN 1.
A
The native VLAN is the VLAN that is configured for packets that dont have a tag. The default native VLAN on all Cisco Switches is VLAN 1. It is always enabled by default. These settings can all be changed: That is: you can designate a different VLAN as the native VLAN, disable VLAN 1, etc. Knowing that, we can eliminate
D) as the correct answer because it is enabled by default. We can also eliminate B) because Native VLAN packets dont get tags by default (you can change this).
Finally, Control Plane traffic is never blocked on Native VLAN 1, and even if you change the Native VLAN, the control plane traffic still comes across VLAN 1.
send
light_mode
delete
Question #38
Which value is indicated by the next hop in a routing table?
- Apreference of the route source
- BIP address of the remote router for forwarding the packets
- Chow the route was learned
- Dexit interface IP address for forwarding the packets
Correct Answer:
B
From official Odom cisco book is Routes for remote subnets typically list both an outgoing interface and next-hop router IP address. Routes for subnets that connect directly to the router list only the outgoing interface, because packets to these destinations do not need to be sent to another router.
B
From official Odom cisco book is Routes for remote subnets typically list both an outgoing interface and next-hop router IP address. Routes for subnets that connect directly to the router list only the outgoing interface, because packets to these destinations do not need to be sent to another router.
send
light_mode
delete
Question #39
Which component of the routing table ranks routing protocols according to their preferences?
- Aadministrative distance
- Bnext hop
- Cmetric
- Drouting protocol code
Correct Answer:
A
Administrative distance - This is the measure of trustworthiness of the source of the route. If a router learns about a destination from more than one routing protocol, administrative distance is compared and the preference is given to the routes with lower administrative distance. In other words, it is the believability of the source of the route.
A
Administrative distance - This is the measure of trustworthiness of the source of the route. If a router learns about a destination from more than one routing protocol, administrative distance is compared and the preference is given to the routes with lower administrative distance. In other words, it is the believability of the source of the route.
send
light_mode
delete
Question #40
At which layer of the OSI model does the protocol that provides the information that is displayed by the show cdp neighbors command operate?
- Adata link
- Bapplication
- Cnetwork
- Dtransport
- Ephysical
Correct Answer:
A
CDP is a device discovery protocol that runs over Layer 2 (the data link layer) on all Cisco-manufactured devices (routers, bridges, access servers, and switches) and allows network management applications to discover Cisco devices that are neighbors of already known devices.
With CDP, network management applications can learn the device type and the Simple Network Management Protocol (SNMP) agent address of neighboring devices running lower-layer, transparent protocols.
A
CDP is a device discovery protocol that runs over Layer 2 (the data link layer) on all Cisco-manufactured devices (routers, bridges, access servers, and switches) and allows network management applications to discover Cisco devices that are neighbors of already known devices.
With CDP, network management applications can learn the device type and the Simple Network Management Protocol (SNMP) agent address of neighboring devices running lower-layer, transparent protocols.
send
light_mode
delete
All Pages
