Checkpoint 156-215.80 Exam Practice Questions (P. 5)
- Full Access (536 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #41
Which options are given on features, when editing a Role on Gaia Platform?
- ARead/Write, Read OnlyMost Voted
- BRead/Write, Read Only, None
- CRead/Write, None
- DRead Only, None
Correct Answer:
B
Roles -
Role-based administration (RBA) lets you create administrative roles for users. With RBA, an administrator can allow Gaia users to access specified features by including those features in a role and assigning that role to users. Each role can include a combination of administrative (read/write) access to some features, monitoring (read-only) access to other features, and no access to other features.
You can also specify which access mechanisms (WebUI or the CLI) are available to the user.

Note - When users log in to the WebUI, they see only those features that they have read-only or read/write access to. If they have read-only access to a feature, they can see the settings pages, but cannot change the settings.
Gaia includes these predefined roles:
✑ adminRole - Gives the user read/write access to all features.
✑ monitorRole- Gives the user read-only access to all features.
You cannot delete or change the predefined roles.

Note - Do not define a new user for external users. An external user is one that is defined on an authentication server (such as RADIUS or TACACS) and not on the local Gaia system.
Reference:
https://sc1.checkpoint.com/documents/R77/CP_R77_Gaia_AdminWebAdminGuide/html_frameset.htm?topic=documents/R77/
CP_R77_Gaia_AdminWebAdminGuide/75930
B
Roles -
Role-based administration (RBA) lets you create administrative roles for users. With RBA, an administrator can allow Gaia users to access specified features by including those features in a role and assigning that role to users. Each role can include a combination of administrative (read/write) access to some features, monitoring (read-only) access to other features, and no access to other features.
You can also specify which access mechanisms (WebUI or the CLI) are available to the user.

Note - When users log in to the WebUI, they see only those features that they have read-only or read/write access to. If they have read-only access to a feature, they can see the settings pages, but cannot change the settings.
Gaia includes these predefined roles:
✑ adminRole - Gives the user read/write access to all features.
✑ monitorRole- Gives the user read-only access to all features.
You cannot delete or change the predefined roles.

Note - Do not define a new user for external users. An external user is one that is defined on an authentication server (such as RADIUS or TACACS) and not on the local Gaia system.
Reference:
https://sc1.checkpoint.com/documents/R77/CP_R77_Gaia_AdminWebAdminGuide/html_frameset.htm?topic=documents/R77/
CP_R77_Gaia_AdminWebAdminGuide/75930
send
light_mode
delete
Question #42
What is the default time length that Hit Count Data is kept?
- A3 monthMost Voted
- B4 weeks
- C12 months
- D1 week
Correct Answer:
A
Reference:
https://community.checkpoint.com/t5/General-Topics/What-is-the-default-time-that-HIT-count-data-is-kept-in-R80/td-p/33636
A
Reference:
https://community.checkpoint.com/t5/General-Topics/What-is-the-default-time-that-HIT-count-data-is-kept-in-R80/td-p/33636
send
light_mode
delete
Question #43
Choose the Best place to find a Security Management Server backup file named backup_fw, on a Check Point Appliance.
- A/var/log/Cpbackup/backups/backup/backup_fw.tgs
- B/var/log/Cpbackup/backups/backup/backup_fw.tar
- C/var/log/Cpbackup/backups/backups/backup_fw.tar
- D/var/log/Cpbackup/backups/backup_fw.tgz
Correct Answer:
D
Gaia's Backup feature allows backing up the configuration of the Gaia OS and of the Security Management server database, or restoring a previously saved configuration.
The configuration is saved to a .tgz file in the following directory:
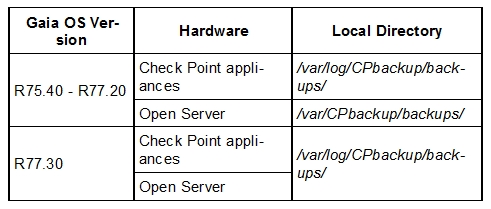
Reference:
https://supportcenter.checkpoint.com/supportcenter/portal?
action=portlets.SearchResultMainAction&eventSubmit_doGoviewsolutiondetails=&solutionid=sk91400
D
Gaia's Backup feature allows backing up the configuration of the Gaia OS and of the Security Management server database, or restoring a previously saved configuration.
The configuration is saved to a .tgz file in the following directory:

Reference:
https://supportcenter.checkpoint.com/supportcenter/portal?
action=portlets.SearchResultMainAction&eventSubmit_doGoviewsolutiondetails=&solutionid=sk91400
send
light_mode
delete
Question #44
With which command can you view the running configuration of Gaia Operating system?
- Ashow conf-active
- Bshow configuration active
- Cshow configuration
- Dshow running-configuration
Correct Answer:
C
C
send
light_mode
delete
Question #45
Which of the following is TRUE regarding Gaia command line?
- AConfiguration changes should be done in mgmt_cli and use CLISH for monitoring. Expert mode is used only for OS level tasks.
- BConfiguration changes should be done in expert-mode and CLISH is used for monitoring.
- CConfiguration changes should be done in mgmt_cli and use expert-mode for OS-level tasks.
- DAll configuration changes should be made in CLISH and expert-mode should be used for OS-level tasks.
Correct Answer:
D
D
send
light_mode
delete
Question #46
If there are two administrators logged in at the same time to the SmartConsole, and there are objects locked for editing, what must be done to make them available to other administrators? Choose the BEST answer.
- APublish or discard the session.Most Voted
- BRevert the session.
- CSave and install the Policy.
- DDelete older versions of database.
Correct Answer:
A
To make changes available to all administrators, and to unlock the objects and rules that are being edited, the administrator must publish the session.
To make your changes available to other administrators, and to save the database before installing a policy, you must publish the session. When you publish a session, a new database version is created.
When you select Install Policy, you are prompted to publish all unpublished changes. You cannot install a policy if the included changes are not published.
Reference:
https://sc1.checkpoint.com/documents/R80/CP_R80_SecMGMT/html_frameset.htm?topic=documents/R80/CP_R80_SecMGMT/126197
A
To make changes available to all administrators, and to unlock the objects and rules that are being edited, the administrator must publish the session.
To make your changes available to other administrators, and to save the database before installing a policy, you must publish the session. When you publish a session, a new database version is created.
When you select Install Policy, you are prompted to publish all unpublished changes. You cannot install a policy if the included changes are not published.
Reference:
https://sc1.checkpoint.com/documents/R80/CP_R80_SecMGMT/html_frameset.htm?topic=documents/R80/CP_R80_SecMGMT/126197
send
light_mode
delete
Question #47
Which one of the following is the preferred licensing model? Choose the BEST answer.
- ALocal licensing because it ties the package license to the IP-address of the gateway and has no dependency of the Security Management Server.
- BCentral licensing because it ties the package license to the IP-address of the Security Management Server and has no dependency on the gateway.
- CLocal licensing because it ties the package license to the MAC-address of the gateway management interface and has no Security Management Server dependency.
- DCentral licensing because it ties the package license to the MAC-address of the Security Management Server's Mgmt-interface and has no dependency on the gateway.
Correct Answer:
B
Central License -
A Central License is a license attached to the Security Management server IP address, rather than the gateway IP address. The benefits of a Central
License are:
✑ Only one IP address is needed for all licenses.
✑ A license can be taken from one gateway and given to another.
✑ The new license remains valid when changing the gateway IP address. There is no need to create and install a new license.
Reference:
https://sc1.checkpoint.com/documents/R76/CP_R76_Installation_and_Upgrade_Guide-webAdmin/13128.htm#o13527
B
Central License -
A Central License is a license attached to the Security Management server IP address, rather than the gateway IP address. The benefits of a Central
License are:
✑ Only one IP address is needed for all licenses.
✑ A license can be taken from one gateway and given to another.
✑ The new license remains valid when changing the gateway IP address. There is no need to create and install a new license.
Reference:
https://sc1.checkpoint.com/documents/R76/CP_R76_Installation_and_Upgrade_Guide-webAdmin/13128.htm#o13527
send
light_mode
delete
Question #48
Tom has been tasked to install Check Point R80 in a distributed deployment. Before Tom installs the systems this way, how many machines will he need if he does NOT include a SmartConsole machine in his calculations?
- AOne machine, but it needs to be installed using SecurePlatform for compatibility purposes.
- BOne machine
- CTwo machines
- DThree machines
Correct Answer:
C
One for Security Management Server and the other one for the Security Gateway.
C
One for Security Management Server and the other one for the Security Gateway.
send
light_mode
delete
Question #49
A new license should be generated and installed in all of the following situations EXCEPT when ________ .
- AThe license is attached to the wrong Security Gateway
- BThe existing license expires
- CThe license is upgraded
- DThe IP address of the Security Management or Security Gateway has changed
Correct Answer:
A
There is no need to generate new license in this situation, just need to detach license from wrong Security Gateway and attach it to the right one.
A
There is no need to generate new license in this situation, just need to detach license from wrong Security Gateway and attach it to the right one.
send
light_mode
delete
Question #50
What is the default shell for the command line interface?
- AExpert
- BClishMost Voted
- CAdmin
- DNormal
Correct Answer:
B
The default shell of the CLI is called clish
https://sc1.checkpoint.com/documents/R76/CP_R76_Gaia_WebAdmin/75697.htm
Reference:
B
The default shell of the CLI is called clish
https://sc1.checkpoint.com/documents/R76/CP_R76_Gaia_WebAdmin/75697.htm
Reference:
send
light_mode
delete
All Pages
