Checkpoint 156-215.80 Exam Practice Questions (P. 2)
- Full Access (536 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #11
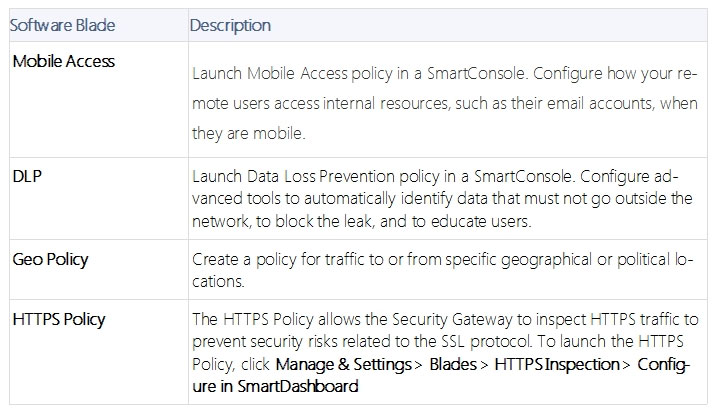
DLP and Geo Policy are examples of what type of Policy?
- AStandard Policies
- BShared Policies
- CInspection Policies
- DUnified Policies
Correct Answer:
B
The Shared policies are installed with the Access Control Policy.
Reference:
https://sc1.checkpoint.com/documents/R80/CP_R80_SecMGMT/html_frameset.htm?topic=documents/R80/CP_R80_SecMGMT/126197
B
The Shared policies are installed with the Access Control Policy.

Reference:
https://sc1.checkpoint.com/documents/R80/CP_R80_SecMGMT/html_frameset.htm?topic=documents/R80/CP_R80_SecMGMT/126197
send
light_mode
delete
Question #12
In which deployment is the security management server and Security Gateway installed on the same appliance?
- ABridge Mode
- BRemote
- CStandalone
- DDistributed
Correct Answer:
C
Installing Standalone -
Standalone Deployment - The Security Management Server and the Security Gateway are installed on the same computer or appliance.
Reference:
https://sc1.checkpoint.com/documents/R76/CP_R76_Installation_and_Upgrade_Guide-webAdmin/89230.htm#o98246
C
Installing Standalone -
Standalone Deployment - The Security Management Server and the Security Gateway are installed on the same computer or appliance.

Reference:
https://sc1.checkpoint.com/documents/R76/CP_R76_Installation_and_Upgrade_Guide-webAdmin/89230.htm#o98246
send
light_mode
delete
Question #13
A _________ VPN deployment is used to provide remote users with secure access to internal corporate resources by authenticating the user through an internet browser.
- AClientless remote access
- BClientless direct access
- CClient-based remote access
- DDirect access
Correct Answer:
A
Clientless - Users connect through a web browser and use HTTPS connections. Clientless solutions usually supply access to web-based corporate resources.
Reference:
https://sc1.checkpoint.com/documents/R80/CP_R80BC_Firewall/html_frameset.htm?topic=documents/R80/CP_R80BC_Firewall/92704
A
Clientless - Users connect through a web browser and use HTTPS connections. Clientless solutions usually supply access to web-based corporate resources.
Reference:
https://sc1.checkpoint.com/documents/R80/CP_R80BC_Firewall/html_frameset.htm?topic=documents/R80/CP_R80BC_Firewall/92704
send
light_mode
delete
Question #14
Which of the following statements is TRUE about R80 management plug-ins?
- AThe plug-in is a package installed on the Security Gateway.
- BInstalling a management plug-in requires a Snapshot, just like any upgrade process.
- CA management plug-in interacts with a Security Management Server to provide new features and support for new products.
- DUsing a plug-in offers full central management only if special licensing is applied to specific features of the plug-in.
Correct Answer:
C
C
send
light_mode
delete
Question #15
Gaia can be configured using the _______ or ______ .
- AGaiaUI; command line interfaceMost Voted
- BWebUI; Gaia Interface
- CCommand line interface; WebUI
- DGaia Interface; GaiaUI
Correct Answer:
C
Configuring Gaia for the First Time
In This Section:
Running the First Time Configuration Wizard in WebUI
Running the First Time Configuration Wizard in CLI
After you install Gaia for the first time, use the First Time Configuration Wizard to configure the system and the Check Point products on it.
Reference:
https://sc1.checkpoint.com/documents/R77/CP_R77_Gaia_AdminWebAdminGuide/html_frameset.htm?topic=documents/R77/
CP_R77_Gaia_AdminWebAdminGuide/112568
C
Configuring Gaia for the First Time
In This Section:
Running the First Time Configuration Wizard in WebUI
Running the First Time Configuration Wizard in CLI
After you install Gaia for the first time, use the First Time Configuration Wizard to configure the system and the Check Point products on it.
Reference:
https://sc1.checkpoint.com/documents/R77/CP_R77_Gaia_AdminWebAdminGuide/html_frameset.htm?topic=documents/R77/
CP_R77_Gaia_AdminWebAdminGuide/112568
send
light_mode
delete
Question #16
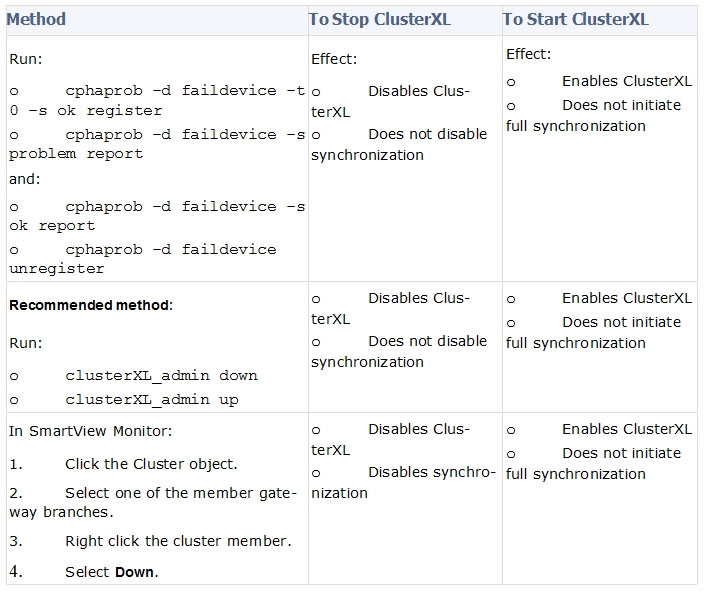
Where can you trigger a failover of the cluster members?
1. Log in to Security Gateway CLI and run command clusterXL_admin down.
2. In SmartView Monitor right-click the Security Gateway member and select Cluster member stop.
3. Log into Security Gateway CLI and run command cphaprob down.
1. Log in to Security Gateway CLI and run command clusterXL_admin down.
2. In SmartView Monitor right-click the Security Gateway member and select Cluster member stop.
3. Log into Security Gateway CLI and run command cphaprob down.
- A1, 2, and 3
- B2 and 3
- C1 and 2
- D1 and 3
Correct Answer:
C
How to Initiate Failover -
Reference:
https://sc1.checkpoint.com/documents/R76/CP_R76_ClusterXL_AdminGuide/7298.htm
C
How to Initiate Failover -

Reference:
https://sc1.checkpoint.com/documents/R76/CP_R76_ClusterXL_AdminGuide/7298.htm
send
light_mode
delete
Question #17
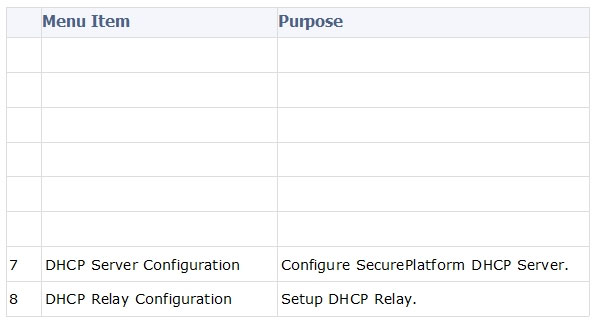
Which utility allows you to configure the DHCP service on GAIA from the command line?
- Aifconfig
- Bdhcp_cfg
- Csysconfig
- Dcpconfig
Correct Answer:
C
Sysconfig Configuration Options -
Refrence:
https://sc1.checkpoint.com/documents/R76/CP_R76_Splat_AdminGuide/51548.htm
NOTE:Question must be wrong because no answer is possible for GAIA system, this must be SPLAT version.
DHCP CLI configuration for GAIA reference:
https://sc1.checkpoint.com/documents/R76/CP_R76_Gaia_WebAdmin/73181.htm#o80096
C
Sysconfig Configuration Options -

Refrence:
https://sc1.checkpoint.com/documents/R76/CP_R76_Splat_AdminGuide/51548.htm
NOTE:Question must be wrong because no answer is possible for GAIA system, this must be SPLAT version.
DHCP CLI configuration for GAIA reference:
https://sc1.checkpoint.com/documents/R76/CP_R76_Gaia_WebAdmin/73181.htm#o80096
send
light_mode
delete
Question #18
Which VPN routing option uses VPN routing for every connection a satellite gateway handles?
- ATo satellites through center only
- BTo center only
- CTo center and to other satellites through center
- DTo center, or through the center to other satellites, to internet and other VPN targets
Correct Answer:
D
On the VPN Routing page, enable the VPN routing for satellites section, by selecting one of these options:
✑ To center and to other Satellites through center; this allows connectivity between Gateways; for example, if the spoke Gateways are DAIP Gateways, and the hub is a Gateway with a static IP address
✑ To center, or through the center to other satellites, to Internet and other VPN targets; this allows connectivity between the Gateways, as well as the ability to inspect all communication passing through the hub to the Internet.
Reference:
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk31021
D
On the VPN Routing page, enable the VPN routing for satellites section, by selecting one of these options:
✑ To center and to other Satellites through center; this allows connectivity between Gateways; for example, if the spoke Gateways are DAIP Gateways, and the hub is a Gateway with a static IP address
✑ To center, or through the center to other satellites, to Internet and other VPN targets; this allows connectivity between the Gateways, as well as the ability to inspect all communication passing through the hub to the Internet.
Reference:
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk31021
send
light_mode
delete
Question #19
Which product correlates logs and detects security threats, providing a centralized display of potential attack patterns from all network devices?
- ASmartView Monitor
- BSmartEvent
- CSmartUpdate
- DSmartDashboard
Correct Answer:
B
SmartEvent correlates logs from all Check Point enforcement points, including end-points, to identify suspicious activity from the clutter. Rapid data analysis and custom event logs immediately alert administrators to anomalous behavior such as someone attempting to use the same credential in multiple geographies simultaneously.
Reference:
https://www.checkpoint.com/products/smartevent/
B
SmartEvent correlates logs from all Check Point enforcement points, including end-points, to identify suspicious activity from the clutter. Rapid data analysis and custom event logs immediately alert administrators to anomalous behavior such as someone attempting to use the same credential in multiple geographies simultaneously.
Reference:
https://www.checkpoint.com/products/smartevent/
send
light_mode
delete
Question #20
Assuming you have a Distributed Deployment, what will be the effect of running the following command on the Security Management Server?
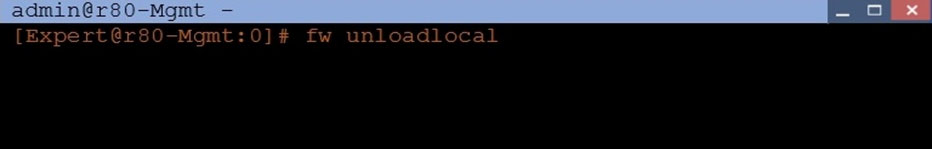

- ARemove the installed Security Policy.Most Voted
- BRemove the local ACL lists.
- CNo effect.
- DReset SIC on all gateways.
Correct Answer:
A
This command uninstall actual security policy (already installed)
Reference:
https://sc1.checkpoint.com/documents/R77/CP_R77_SecurityGatewayTech_WebAdmin/6751.htm
A
This command uninstall actual security policy (already installed)
Reference:
https://sc1.checkpoint.com/documents/R77/CP_R77_SecurityGatewayTech_WebAdmin/6751.htm
send
light_mode
delete
All Pages
