Checkpoint 156-215.80 Exam Practice Questions (P. 3)
- Full Access (536 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #21
An administrator is creating an IPsec site-to-site VPN between his corporate office and branch office. Both offices are protected by Check Point Security Gateway managed by the same Security Management Server. While configuring the VPN community to specify the pre-shared secret, the administrator found that the check box to enable pre-shared secret is shared and cannot be enabled. Why does it not allow him to specify the pre-shared secret?
- AIPsec VPN blade should be enabled on both Security Gateway.
- BPre-shared can only be used while creating a VPN between a third party vendor and Check Point Security Gateway.
- CCertificate based Authentication is the only authentication method available between two Security Gateway managed by the same SMS.
- DThe Security Gateways are pre-R75.40.
Correct Answer:
C
C
send
light_mode
delete
Question #22
You are the senior Firewall administrator for Alpha Corp, and have recently returned from a training course on Check Point's new advanced management platform.
You are presenting an in-house overview of the new features of Check Point Management to the other administrators in Alpha Corp.
How will you describe the new `Publish` button in Management Console?
You are presenting an in-house overview of the new features of Check Point Management to the other administrators in Alpha Corp.

How will you describe the new `Publish` button in Management Console?
- AThe Publish button takes any changes an administrator has made in their management session, publishes a copy to the Check Point Cloud, and then saves it to the database.
- BThe Publish button takes any changes an administrator has made in their management session and publishes a copy to the Check Point Cloud but does not save it to the database.
- CThe Publish button saves any changes an administrator has made in their management session. After saving to the database, any changes are now visible to all other administrator sessions.
- DThe Publish button saves any changes an administrator has made in their management session. After saving to the database, any changes are now visible to any new Unified Policy sessions.
Correct Answer:
C
To make your changes available to other administrators, and to save the database before installing a policy, you must publish the session. When you publish a session, a new database version is created.
Reference:
https://sc1.checkpoint.com/documents/R80/CP_R80_SecMGMT/html_frameset.htm?topic=documents/R80/CP_R80_SecMGMT/126197
C
To make your changes available to other administrators, and to save the database before installing a policy, you must publish the session. When you publish a session, a new database version is created.
Reference:
https://sc1.checkpoint.com/documents/R80/CP_R80_SecMGMT/html_frameset.htm?topic=documents/R80/CP_R80_SecMGMT/126197
send
light_mode
delete
Question #23
Which of the following ClusterXL modes uses a non-unicast MAC address for the cluster IP address.
- AHigh Availability
- BLoad Sharing Multicast
- CLoad Sharing Pivot
- DMaster/Backup
Correct Answer:
B
Explanation :
ClusterXL uses the Multicast mechanism to associate the virtual cluster IP addresses with all cluster members. By binding these IP addresses to a Multicast MAC address, it ensures that all packets sent to the cluster, acting as a gateway, will reach all members in the cluster.
Reference:
https://sc1.checkpoint.com/documents/R76/CP_R76_ClusterXL_AdminGuide/7292.htm
B
Explanation :
ClusterXL uses the Multicast mechanism to associate the virtual cluster IP addresses with all cluster members. By binding these IP addresses to a Multicast MAC address, it ensures that all packets sent to the cluster, acting as a gateway, will reach all members in the cluster.
Reference:
https://sc1.checkpoint.com/documents/R76/CP_R76_ClusterXL_AdminGuide/7292.htm
send
light_mode
delete
Question #24
With the User Directory Software Blade, you can create user definitions on a(an) ___________ Server.
- ANT domain
- BSMTP
- CLDAP
- DSecurID
Correct Answer:
C
Reference:
https://sc1.checkpoint.com/documents/R80/CP_R80_SecMGMT/html_frameset.htm?topic=documents/R80/CP_R80_SecMGMT/126197
C
Reference:
https://sc1.checkpoint.com/documents/R80/CP_R80_SecMGMT/html_frameset.htm?topic=documents/R80/CP_R80_SecMGMT/126197
send
light_mode
delete
Question #25
Which of the following is NOT a component of a Distinguished Name?
- AOrganizational Unit
- BCountry
- CCommon Name
- DUser container
Correct Answer:
D
Distinguished Name Components -
CN=common name, OU=organizational unit, O=organization, L=locality, ST=state or province, C=country name
Reference:
https://sc1.checkpoint.com/documents/R76/CP_R76_SecMan_WebAdmin/html_frameset.htm?topic=documents/R76/
CP_R76_SecMan_WebAdmin/71950
D
Distinguished Name Components -
CN=common name, OU=organizational unit, O=organization, L=locality, ST=state or province, C=country name
Reference:
https://sc1.checkpoint.com/documents/R76/CP_R76_SecMan_WebAdmin/html_frameset.htm?topic=documents/R76/
CP_R76_SecMan_WebAdmin/71950
send
light_mode
delete
Question #26
What are the three authentication methods for SIC?
- APasswords, Users, and standards-based SSL for the creation of secure channels
- BCertificates, standards-based SSL for the creation of secure channels, and 3DES or AES128 for encryptionMost Voted
- CPacket Filtering, certificates, and 3DES or AES128 for encryption
- DCertificates, Passwords, and Tokens
Correct Answer:
B
Secure Internal Communication (SIC)
Secure Internal Communication (SIC) lets Check Point platforms and products authenticate with each other. The SIC procedure creates a trusted status between gateways, management servers and other Check Point components. SIC is required to install polices on gateways and to send logs between gateways and management servers.
These security measures make sure of the safety of SIC:
✑ Certificates for authentication
✑ Standards-based SSL for the creation of the secure channel
✑ 3DES for encryption
Reference:
https://sc1.checkpoint.com/documents/R76/CP_R76_SecMan_WebAdmin/html_frameset.htm?topic=documents/R76/
CP_R76_SecMan_WebAdmin/71950
B
Secure Internal Communication (SIC)
Secure Internal Communication (SIC) lets Check Point platforms and products authenticate with each other. The SIC procedure creates a trusted status between gateways, management servers and other Check Point components. SIC is required to install polices on gateways and to send logs between gateways and management servers.
These security measures make sure of the safety of SIC:
✑ Certificates for authentication
✑ Standards-based SSL for the creation of the secure channel
✑ 3DES for encryption
Reference:
https://sc1.checkpoint.com/documents/R76/CP_R76_SecMan_WebAdmin/html_frameset.htm?topic=documents/R76/
CP_R76_SecMan_WebAdmin/71950
send
light_mode
delete
Question #27
You have enabled `Extended Log` as a tracking option to a security rule. However, you are still not seeing any data type information. What is the MOST likely reason?
- ALogging has disk space issues.
- BContent Awareness is not enabled.
- CIdentity Awareness is not enabled.
- DLog Trimming is enabled.
Correct Answer:
A
The most likely reason for the logs data to stop is the low disk space on the logging device, which can be the Management Server or the Gateway Server.
A
The most likely reason for the logs data to stop is the low disk space on the logging device, which can be the Management Server or the Gateway Server.
send
light_mode
delete
Question #28
What is the order of NAT priorities?
- AStatic NAT, IP pool NAT, hide NATMost Voted
- BIP pool NAT, static NAT, hide NAT
- CStatic NAT, automatic NAT, hide NAT
- DStatic NAT, hide NAT, IP pool NAT
Correct Answer:
A
The order of NAT priorities is:
1. Static NAT
2. IP Pool NAT
3. Hide NAT
Since Static NAT has all of the advantages of IP Pool NAT and more, it has a higher priority than the other NAT methods.
Reference:
https://sc1.checkpoint.com/documents/R77/CP_R77_Firewall_WebAdmin/6724.htm#o6919
A
The order of NAT priorities is:
1. Static NAT
2. IP Pool NAT
3. Hide NAT
Since Static NAT has all of the advantages of IP Pool NAT and more, it has a higher priority than the other NAT methods.
Reference:
https://sc1.checkpoint.com/documents/R77/CP_R77_Firewall_WebAdmin/6724.htm#o6919
send
light_mode
delete
Question #29
Which of the following is an identity acquisition method that allows a Security Gateway to identify Active Directory users and computers?
- AUserCheck
- BActive Directory Query
- CAccount Unit Query
- DUser Directory Query
Correct Answer:
B
Explanation :
AD Query extracts user and computer identity information from the Active Directory Security Event Logs. The system generates a Security Event log entry when a user or computer accesses a network resource. For example, this occurs when a user logs in, unlocks a screen, or accesses a network drive.
Reference :
https://sc1.checkpoint.com/documents/R76/CP_R76_IdentityAwareness_AdminGuide/62402.htm
B
Explanation :
AD Query extracts user and computer identity information from the Active Directory Security Event Logs. The system generates a Security Event log entry when a user or computer accesses a network resource. For example, this occurs when a user logs in, unlocks a screen, or accesses a network drive.
Reference :
https://sc1.checkpoint.com/documents/R76/CP_R76_IdentityAwareness_AdminGuide/62402.htm
send
light_mode
delete
Question #30
Ken wants to obtain a configuration lock from other administrator on R80 Security Management Server Operating System. He can do this via WebUI or via CLI.
Which command should he use in CLI?
Which command should he use in CLI?
- Aremove database lock
- BThe database feature has one command: lock database override.
- Coverride database lock
- DThe database feature has two commands: lock database override and unlock database. Both will work.Most Voted
Correct Answer:
D
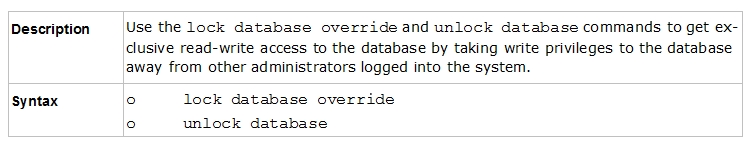
Use the database feature to obtain the configuration lock. The database feature has two commands:
✑ lock database [override].
✑ unlock database
The commands do the same thing: obtain the configuration lock from another administrator.
Reference:
https://sc1.checkpoint.com/documents/R76/CP_R76_Gaia_WebAdmin/75697.htm#o73091
D
Use the database feature to obtain the configuration lock. The database feature has two commands:
✑ lock database [override].
✑ unlock database
The commands do the same thing: obtain the configuration lock from another administrator.

Reference:
https://sc1.checkpoint.com/documents/R76/CP_R76_Gaia_WebAdmin/75697.htm#o73091
send
light_mode
delete
All Pages
