Palo Alto Networks PCNSA Exam Practice Questions (P. 5)
- Full Access (420 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #41
Given the image, which two options are true about the Security policy rules. (Choose two.)
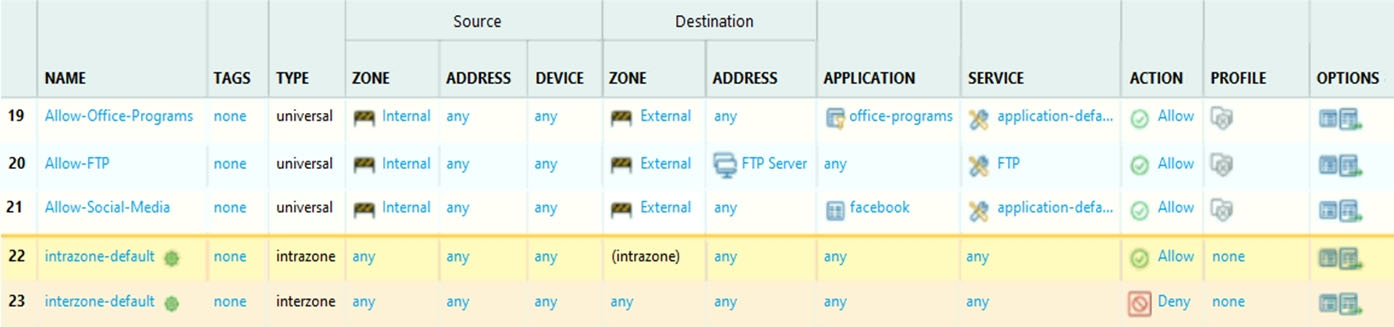

- AThe Allow-Office-Programs rule is using an Application Filter.Most Voted
- BIn the Allow-FTP policy, FTP is allowed using App-ID.
- CThe Allow-Office-Programs rule is using an Application Group.
- DThe Allow-Social-Media rule allows all of Facebook's functions.Most Voted
Correct Answer:
BC
BC
send
light_mode
delete
Question #42
Which type of Security policy rule would match traffic flowing between the Inside zone and Outside zone, within the Inside zone, and within the Outside zone?
- Aglobal
- Bintrazone
- Cinterzone
- DuniversalMost Voted
Correct Answer:
D
Reference:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClomCAC
D
Reference:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClomCAC
send
light_mode
delete
Question #43
Which Palo Alto Networks firewall security platform provides network security for mobile endpoints by inspecting traffic deployed as internet gateways?
send
light_mode
delete
Question #44
Which two statements are correct regarding multiple static default routes when they are configured as shown in the image? (Choose two.)
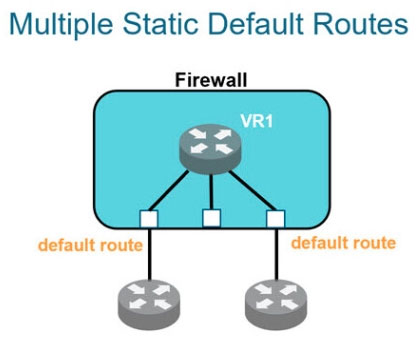

- APath monitoring does not determine if route is useable.
- BRoute with highest metric is actively used.
- CPath monitoring determines if route is useable.Most Voted
- DRoute with lowest metric is actively used.Most Voted
Correct Answer:
CD
CD
send
light_mode
delete
Question #45
Given the Cyber-Attack Lifecycle diagram, identify the stage in which the attacker can run malicious code against a targeted machine.
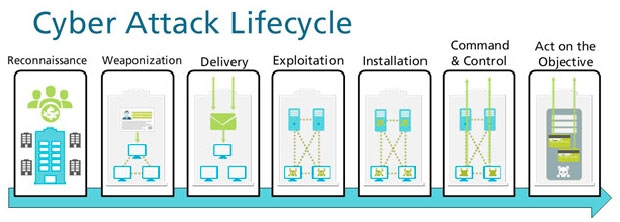

- AExploitationMost Voted
- BInstallation
- CReconnaissance
- DAct on Objective
Correct Answer:
A
A
send
light_mode
delete
Question #46
Which file is used to save the running configuration with a Palo Alto Networks firewall?
- Arunning-config.xmlMost Voted
- Brun-config.xml
- Crunning-configuration.xml
- Drun-configuration.xml
Correct Answer:
A
A
send
light_mode
delete
Question #47
In the example security policy shown, which two websites would be blocked? (Choose two.)
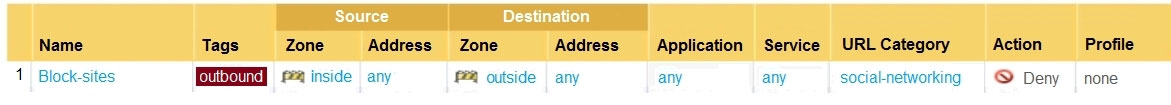

send
light_mode
delete
Question #48
Which Palo Alto Networks component provides consolidated policy creation and centralized management?
- AGlobalProtect
- BPanoramaMost Voted
- CPrisma SaaS
- DAutoFocus
Correct Answer:
B
Reference:
https://www.paloaltonetworks.com/resources/datasheets/panorama-centralized-management-datasheet
B
Reference:
https://www.paloaltonetworks.com/resources/datasheets/panorama-centralized-management-datasheet
send
light_mode
delete
Question #49
Which statement is true regarding a Prevention Posture Assessment?
- AThe Security Policy Adoption Heatmap component filters the information by device groups, serial numbers, zones, areas of architecture, and other categories
- BIt provides a set of questionnaires that help uncover security risk prevention gaps across all areas of network and security architectureMost Voted
- CIt provides a percentage of adoption for each assessment area
- DIt performs over 200 security checks on Panorama/firewall for the assessment
Correct Answer:
B
Reference:
https://docs.paloaltonetworks.com/best-practices/8-1/data-center-best-practices/data-center-best-practice-security-policy/use-palo-alto-networks- assessment-and-review-tools
B
Reference:
https://docs.paloaltonetworks.com/best-practices/8-1/data-center-best-practices/data-center-best-practice-security-policy/use-palo-alto-networks- assessment-and-review-tools
send
light_mode
delete
Question #50
Which five Zero Trust concepts does a Palo Alto Networks firewall apply to achieve an integrated approach to prevent threats? (Choose five.)
- AUser identificationMost Voted
- BFiltration protection
- CVulnerability protectionMost Voted
- DAntivirusMost Voted
- EApplication identificationMost Voted
- FAnti-spywareMost Voted
Correct Answer:
ACDEF
ACDEF
send
light_mode
delete
All Pages
