Palo Alto Networks PCNSA Exam Practice Questions (P. 4)
- Full Access (420 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #31
An administrator notices that protection is needed for traffic within the network due to malicious lateral movement activity. Based on the image shown, which traffic would the administrator need to monitor and block to mitigate the malicious activity?
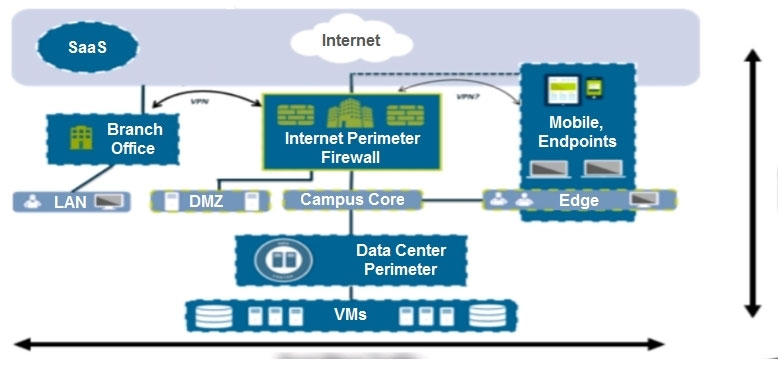

- Abranch office traffic
- Bnorth-south traffic
- Cperimeter traffic
- Deast-west trafficMost Voted
Correct Answer:
D
D
send
light_mode
delete
Question #32
Given the topology, which zone type should zone A and zone B to be configured with?
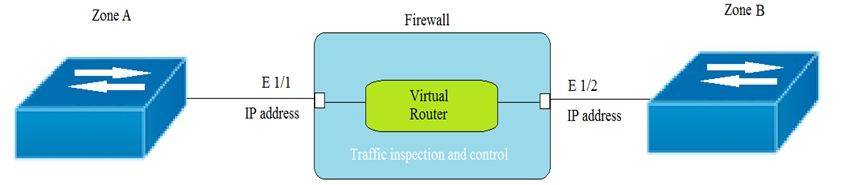

send
light_mode
delete
Question #33
To use Active Directory to authenticate administrators, which server profile is required in the authentication profile?
- Adomain controller
- BTACACS+
- CLDAPMost Voted
- DRADIUS
Correct Answer:
C
C
 GPT-4o - Answer
GPT-4o - Answer
Alright, here’s the deal: LDAP (Lightweight Directory Access Protocol) is the way to go when we’re setting up authentication for administrators via Active Directory. This isn’t just because it’s in the options list; it’s because LDAP is directly supported by Active Directory for authentication purposes. Kerberos is another protocol supported by Active Directory, but since it’s not an available option in your question, LDAP stands out as the straightforward choice. This ensures a seamless integration emphasizing security and administrative ease.
send
light_mode
delete
Question #34
Which interface type is used to monitor traffic and cannot be used to perform traffic shaping?
- ALayer 2
- BTapMost Voted
- CLayer 3
- DVirtual Wire
Correct Answer:
B
B
 GPT-4o - Answer
GPT-4o - Answer
The most accurate choice for monitoring traffic without having the capability to perform traffic shaping is the Tap interface. Specifically designed in the context of network security and administration in Palo Alto Networks platforms, Tap interfaces strictly facilitate traffic monitoring by passively listening to network traffic; they do not participate in traffic flow, hence cannot shape or modify traffic. This distinction is crucial for network admins especially when deploying network monitoring tools while ensuring existing traffic flows remain unaffected.
send
light_mode
delete
Question #35
Which administrator type provides more granular options to determine what the administrator can view and modify when creating an administrator account?
send
light_mode
delete
Question #36
Which administrator type utilizes predefined roles for a local administrator account?
- ASuperuser
- BRole-based
- CDynamicMost Voted
- DDevice administrator
Correct Answer:
C
Reference:
https://docs.paloaltonetworks.com/pan-os/8-0/pan-os-cli-quick-start/get-started-with-the-cli/give-administrators-access-to-the-cli/administrative- privileges?PageSpeed=noscript
C
Reference:
https://docs.paloaltonetworks.com/pan-os/8-0/pan-os-cli-quick-start/get-started-with-the-cli/give-administrators-access-to-the-cli/administrative- privileges?PageSpeed=noscript
send
light_mode
delete
Question #37
Which two security profile types can be attached to a security policy? (Choose two.)
- AantivirusMost Voted
- BDDoS protection
- Cthreat
- DvulnerabilityMost Voted
Correct Answer:
AD
Reference:
https://docs.paloaltonetworks.com/pan-os/8-0/pan-os-admin/policy/security-profiles
AD
Reference:
https://docs.paloaltonetworks.com/pan-os/8-0/pan-os-admin/policy/security-profiles
send
light_mode
delete
Question #38
The CFO found a USB drive in the parking lot and decide to plug it into their corporate laptop. The USB drive had malware on it that loaded onto their computer and then contacted a known command and control (CnC) server, which ordered the infected machine to begin Exfiltrating data from the laptop.
Which security profile feature could have been used to prevent the communication with the CnC server?
Which security profile feature could have been used to prevent the communication with the CnC server?
- ACreate an anti-spyware profile and enable DNS SinkholeMost Voted
- BCreate an antivirus profile and enable DNS Sinkhole
- CCreate a URL filtering profile and block the DNS Sinkhole category
- DCreate a security policy and enable DNS Sinkhole
Correct Answer:
A
Reference:
https://docs.paloaltonetworks.com/pan-os/7-1/pan-os-web-interface-help/objects/objects-security-profiles-anti-spyware-profile
A
Reference:
https://docs.paloaltonetworks.com/pan-os/7-1/pan-os-web-interface-help/objects/objects-security-profiles-anti-spyware-profile
send
light_mode
delete
Question #39
Which user mapping method could be used to discover user IDs in an environment with multiple Windows domain controllers?
- AActive Directory monitoring
- BWindows session monitoring
- CWindows client probing
- Ddomain controller monitoringMost Voted
Correct Answer:
A
A
send
light_mode
delete
Question #40
Which three statements describe the operation of Security policy rules and Security Profiles? (Choose three.)
- ASecurity policy rules are attached to Security Profiles.
- BSecurity Profiles are attached to Security policy rules.Most Voted
- CSecurity Profiles should be used only on allowed traffic.Most Voted
- DSecurity policy rules inspect but do not block traffic.
- ESecurity policy rules can block or allow traffic.Most Voted
Correct Answer:
ABC
ABC
send
light_mode
delete
All Pages
