Microsoft SC-400 Exam Practice Questions (P. 4)
- Full Access (387 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
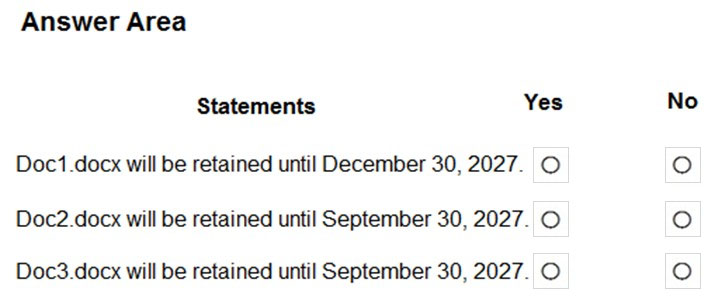
Question #31
HOTSPOT -
You have the retention label policy shown in the Policy exhibit. (Click the Policy tab.)
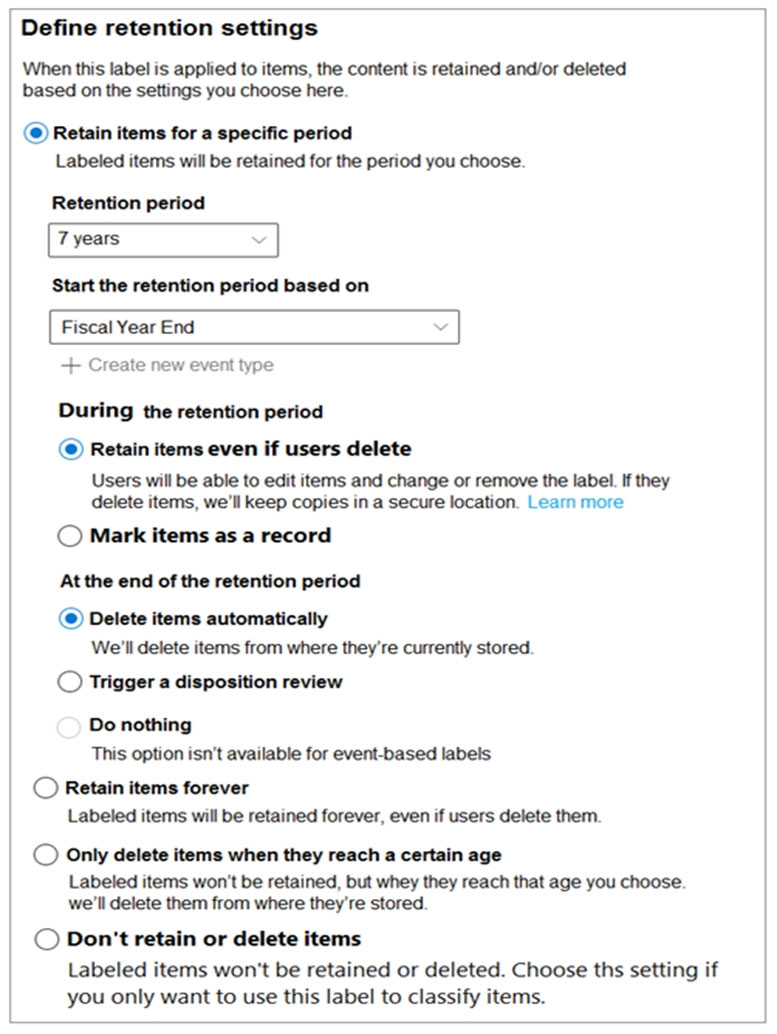
Users apply the retention label policy to files and set the asset ID as shown in the following table.
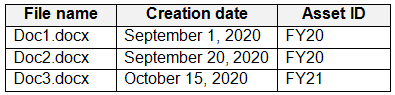
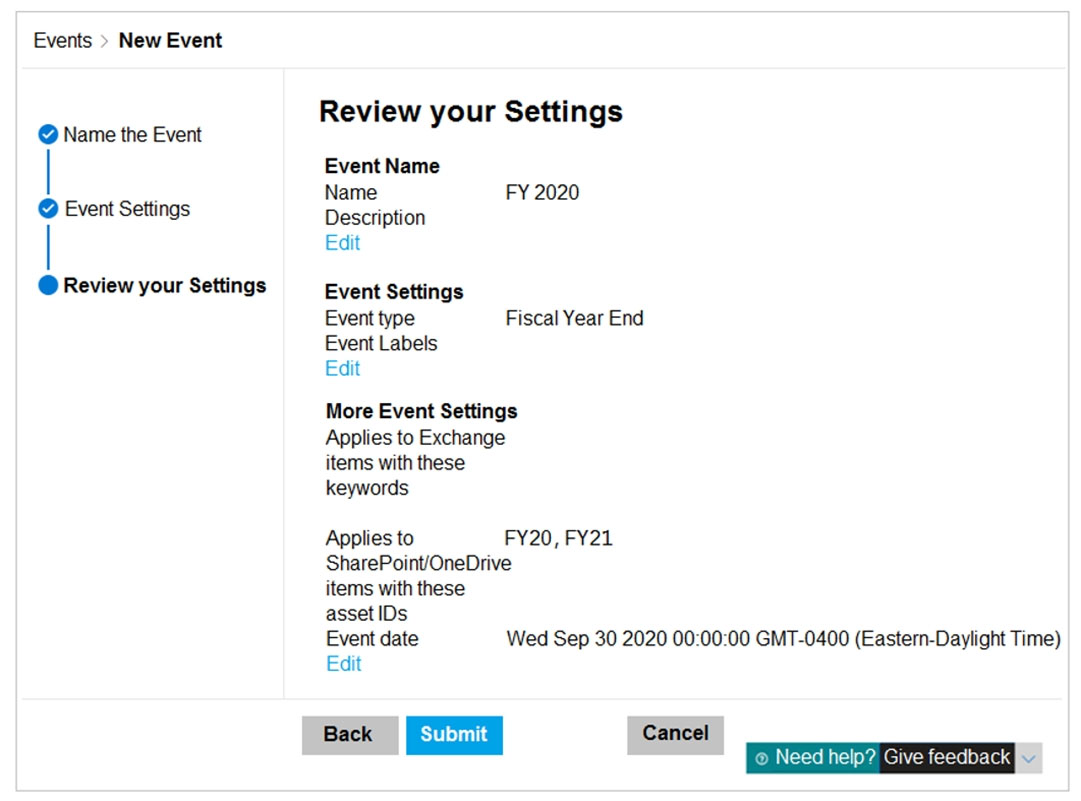
On December 1, 2020, you create the event shown in the Event exhibit. (Click the Event tab.)
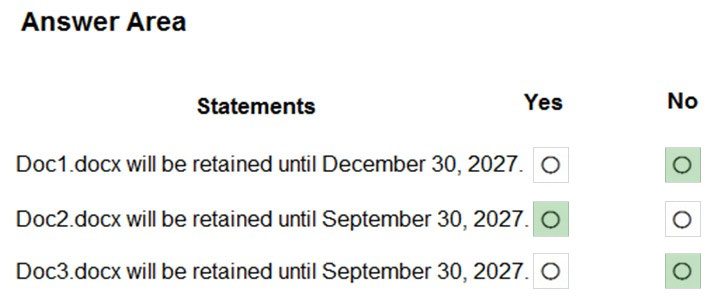
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
You have the retention label policy shown in the Policy exhibit. (Click the Policy tab.)

Users apply the retention label policy to files and set the asset ID as shown in the following table.

On December 1, 2020, you create the event shown in the Event exhibit. (Click the Event tab.)

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:

send
light_mode
delete
Question #32
You have a sensitive information type based on a trainable classifier.
You are unsatisfied with the result of the result of trainable classifier.
You need to retrain the classifier.
What should you use in the Microsoft 365 compliance center?
You are unsatisfied with the result of the result of trainable classifier.
You need to retrain the classifier.
What should you use in the Microsoft 365 compliance center?
- ALabels from Information protection
- BLabels from Information governance
- CContent explorer from Data classificationMost Voted
- DContent search
Correct Answer:
C
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/classifier-how-to-retrain-content-explorer?view=o365-worldwide
C
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/classifier-how-to-retrain-content-explorer?view=o365-worldwide
send
light_mode
delete
Question #33
You receive an email that contains a list of words that will be used for a sensitive information type.
You need to create a file that can be used as the source of a keyword dictionary.
In which format should you save the list?
You need to create a file that can be used as the source of a keyword dictionary.
In which format should you save the list?
- Aa JSON file that has an element for each word
- Ban ACCDB database file that contains a table named Dictionary
- Can XLSX file that contains one word in each cell of the first row
- Da text file that has one word on each lineMost Voted
Correct Answer:
D
Keyword dictionaries can be created either from a text file or from csv file.
Note:
There are several versions of this question in the exam. The question has two possible correct answers:
1. a CSV file that contains words separated by commas
2. a text file that has one word on each line
Other incorrect answer options you may see on the exam include the following:
✑ a TSV file that contains words separated by tabs
✑ a DOCX file that has one word on each line
✑ an XML file that contains a keyword tag for each word
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/create-a-keyword-dictionary?view=o365-worldwide
D
Keyword dictionaries can be created either from a text file or from csv file.
Note:
There are several versions of this question in the exam. The question has two possible correct answers:
1. a CSV file that contains words separated by commas
2. a text file that has one word on each line
Other incorrect answer options you may see on the exam include the following:
✑ a TSV file that contains words separated by tabs
✑ a DOCX file that has one word on each line
✑ an XML file that contains a keyword tag for each word
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/create-a-keyword-dictionary?view=o365-worldwide
send
light_mode
delete
Question #34
HOTSPOT -
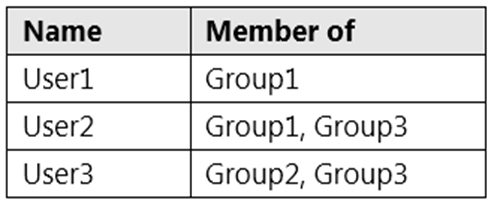
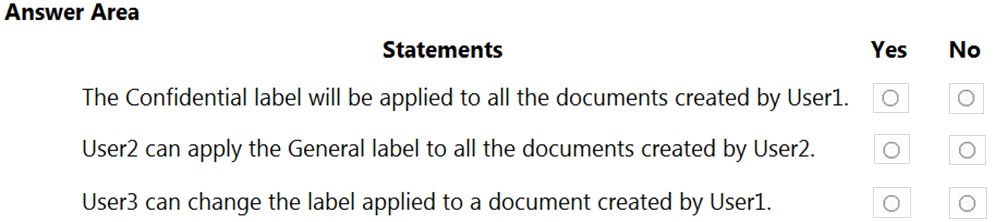
You have a Microsoft 365 E5 tenant that contains three groups named Group1, Group2, and Group3.
You have the users shown in the following table.
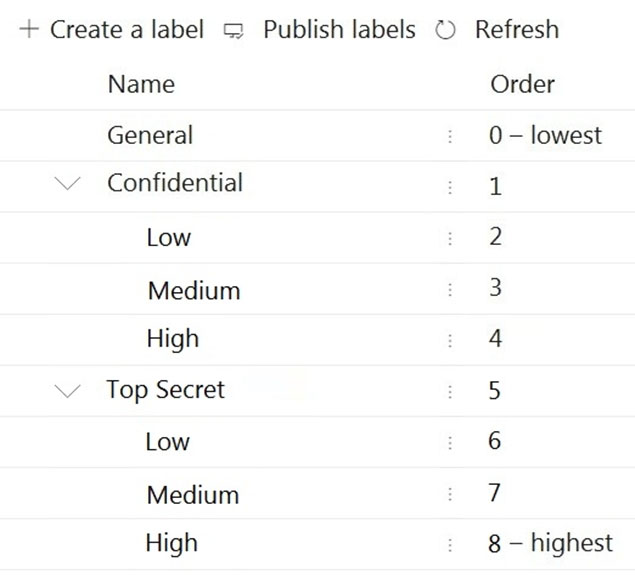
You have the sensitivity labels shown in the following exhibit.
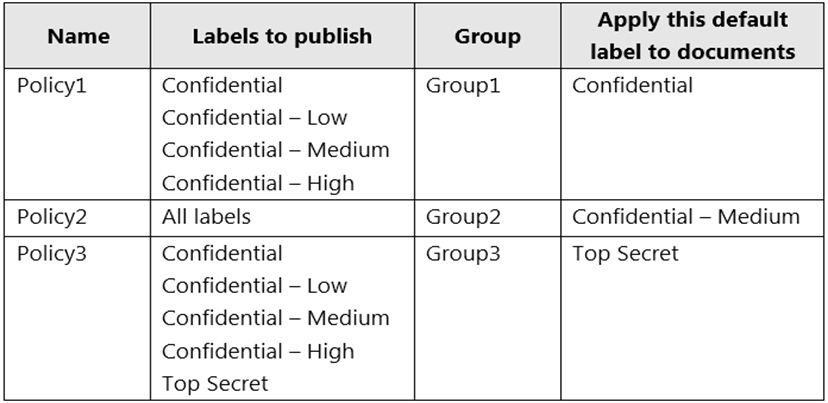
You have the label policies shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
You have a Microsoft 365 E5 tenant that contains three groups named Group1, Group2, and Group3.
You have the users shown in the following table.

You have the sensitivity labels shown in the following exhibit.

You have the label policies shown in the following table.

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:
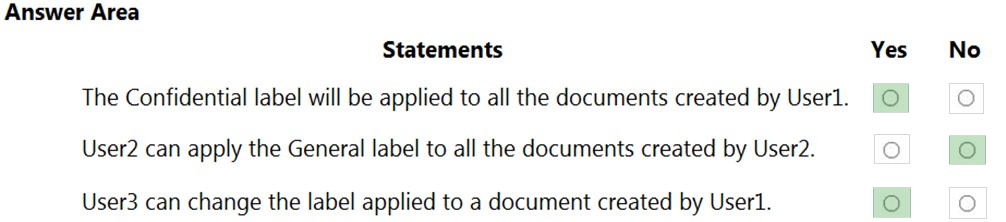
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels?view=o365-worldwide

Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels?view=o365-worldwide
send
light_mode
delete
Question #35
HOTSPOT -
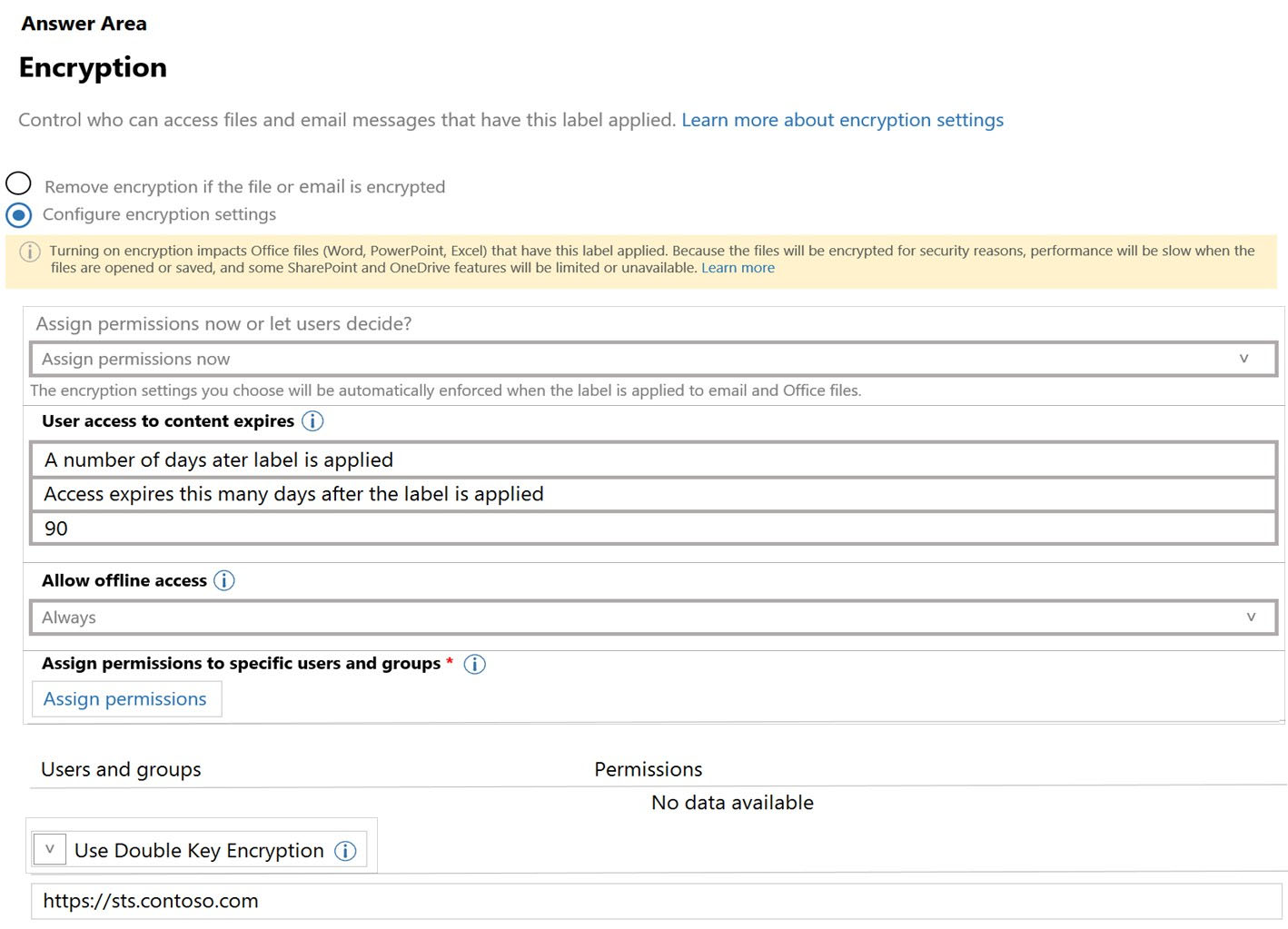
You have a Microsoft 365 E5 tenant that contains a sensitivity label named label1.
You plan to enable co-authoring for encrypted files.
You need to ensure that files that have label1 applied support co-authoring.
Which two settings should you modify? To answer, select the settings in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
You have a Microsoft 365 E5 tenant that contains a sensitivity label named label1.
You plan to enable co-authoring for encrypted files.
You need to ensure that files that have label1 applied support co-authoring.
Which two settings should you modify? To answer, select the settings in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:
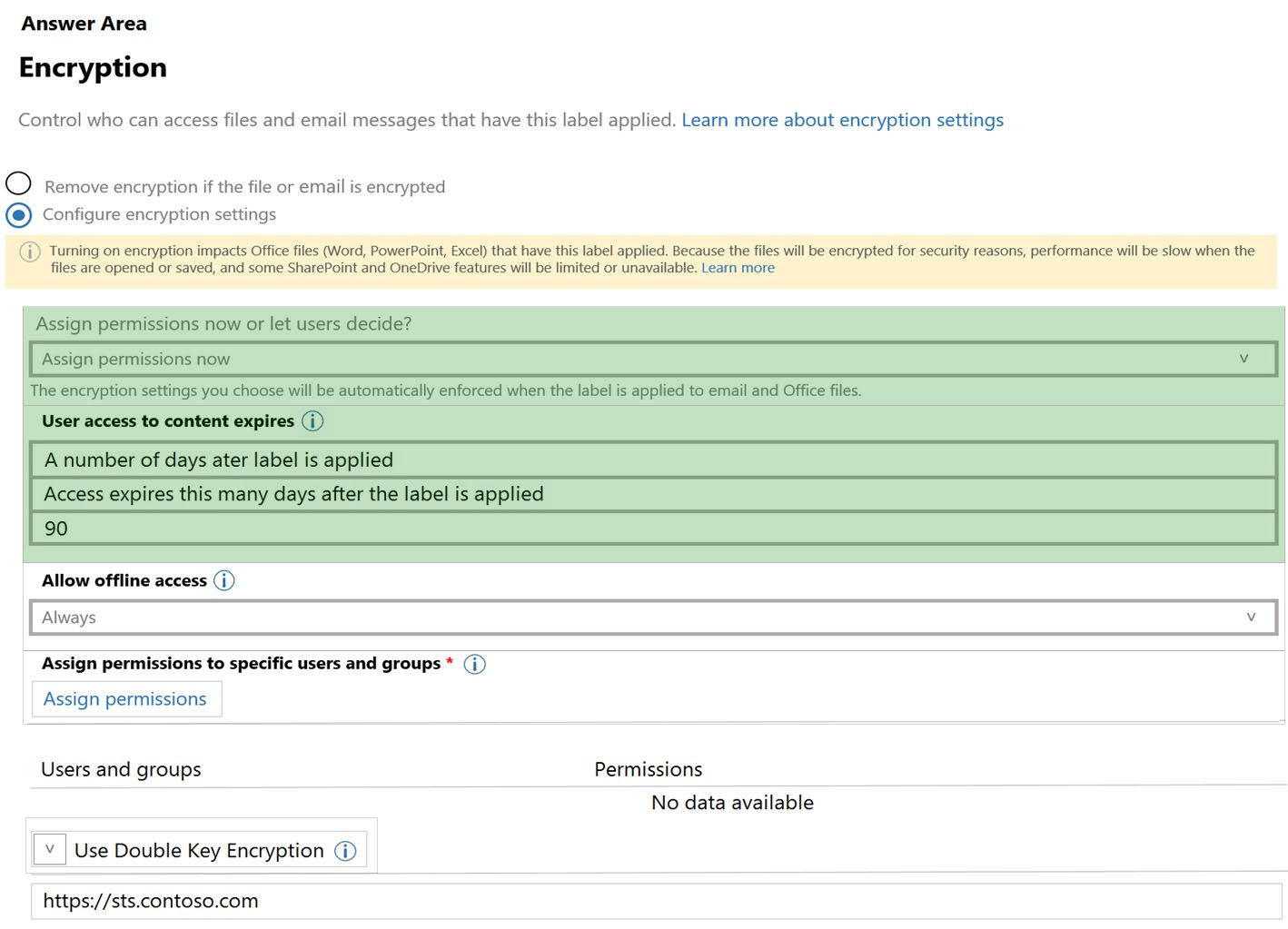
Co-authoring and AutoSave aren't supported and don't work for labeled and encrypted Office documents that use any of the following configurations for encryption:
✑ Let users assign permissions when they apply the label and the checkbox In Word, PowerPoint, and Excel, prompt users to specify permissions is selected.
This configuration is sometimes referred to as "user-defined permissions".
✑ User access to content expires is set to a value other than Never.
Double Key Encryption is selected.

Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels-coauthoring?view=o365-worldwide https://techcommunity.microsoft.com/t5/security-compliance-and-identity/co-authoring-files-with-sensitivity-labels/ba-p/3029768

Co-authoring and AutoSave aren't supported and don't work for labeled and encrypted Office documents that use any of the following configurations for encryption:
✑ Let users assign permissions when they apply the label and the checkbox In Word, PowerPoint, and Excel, prompt users to specify permissions is selected.
This configuration is sometimes referred to as "user-defined permissions".
✑ User access to content expires is set to a value other than Never.
Double Key Encryption is selected.

Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels-coauthoring?view=o365-worldwide https://techcommunity.microsoft.com/t5/security-compliance-and-identity/co-authoring-files-with-sensitivity-labels/ba-p/3029768
send
light_mode
delete
Question #36
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You implement Microsoft 365 Endpoint data loss prevention (Endpoint DLP).
You have computers that run Windows 10 and have Microsoft 365 Apps installed. The computers are joined to Azure Active Directory (Azure AD).
You need to ensure that Endpoint DLP policies can protect content on the computers.
Solution: You onboard the computers to Microsoft Defender for Endpoint.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You implement Microsoft 365 Endpoint data loss prevention (Endpoint DLP).
You have computers that run Windows 10 and have Microsoft 365 Apps installed. The computers are joined to Azure Active Directory (Azure AD).
You need to ensure that Endpoint DLP policies can protect content on the computers.
Solution: You onboard the computers to Microsoft Defender for Endpoint.
Does this meet the goal?
- AYesMost Voted
- BNo
Correct Answer:
A
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/endpoint-dlp-getting-started?view=o365-worldwide
A
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/endpoint-dlp-getting-started?view=o365-worldwide
send
light_mode
delete
Question #37
You have a Microsoft 365 tenant that uses 100 data loss prevention (DLP) policies.
A Microsoft Exchange administrator frequently investigates emails that were blocked due to DLP policy violations.
You need recommend which DLP report the Exchange administrator can use to identify how many messages were blocked based on each DLP policy.
Which report should you recommend?
A Microsoft Exchange administrator frequently investigates emails that were blocked due to DLP policy violations.
You need recommend which DLP report the Exchange administrator can use to identify how many messages were blocked based on each DLP policy.
Which report should you recommend?
- AThird-party DLP policy matches
- BDLP policy matchesMost Voted
- CDLP incidents
- DFalse positive and override
Correct Answer:
B
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/dlp-learn-about-dlp?view=o365-worldwide
B
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/dlp-learn-about-dlp?view=o365-worldwide
send
light_mode
delete
Question #38
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are configuring a file policy in Microsoft Cloud App Security.
You need to configure the policy to apply to all files. Alerts must be sent to every file owner who is affected by the policy. The policy must scan for credit card numbers, and alerts must be sent to the Microsoft Teams site of the affected department.
Solution: You use the Data Classification service inspection method and send alerts to Microsoft Power Automate.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are configuring a file policy in Microsoft Cloud App Security.
You need to configure the policy to apply to all files. Alerts must be sent to every file owner who is affected by the policy. The policy must scan for credit card numbers, and alerts must be sent to the Microsoft Teams site of the affected department.
Solution: You use the Data Classification service inspection method and send alerts to Microsoft Power Automate.
Does this meet the goal?
send
light_mode
delete
Question #39
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are configuring a file policy in Microsoft Cloud App Security.
You need to configure the policy to apply to all files. Alerts must be sent to every file owner who is affected by the policy. The policy must scan for credit card numbers, and alerts must be sent to the Microsoft Teams site of the affected department.
Solution: You use the Build-in DLP inspection method and send alerts to Microsoft Power Automate.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are configuring a file policy in Microsoft Cloud App Security.
You need to configure the policy to apply to all files. Alerts must be sent to every file owner who is affected by the policy. The policy must scan for credit card numbers, and alerts must be sent to the Microsoft Teams site of the affected department.
Solution: You use the Build-in DLP inspection method and send alerts to Microsoft Power Automate.
Does this meet the goal?
- AYes
- BNoMost Voted
Correct Answer:
B
Reference:
https://docs.microsoft.com/en-us/cloud-app-security/dcs-inspection https://docs.microsoft.com/en-us/cloud-app-security/data-protection-policies
B
Reference:
https://docs.microsoft.com/en-us/cloud-app-security/dcs-inspection https://docs.microsoft.com/en-us/cloud-app-security/data-protection-policies
send
light_mode
delete
Question #40
Your company has a Microsoft 365 tenant that uses a domain named contoso.com.
You are implementing data loss prevention (DLP).
The company's default browser is Microsoft Edge.
During a recent audit, you discover that some users use Firefox and Google Chrome browsers to upload files labeled as Confidential to a third-party Microsoft
SharePoint Online site that has a URL of https://m365x076709.sharepoint.com. Users are blocked from uploading the confidential files to the site from Microsoft
Edge.
You need to ensure that the users cannot upload files labeled as Confidential from Firefox and Google Chrome to any cloud services.
Which two actions should you perform? Each correct answer presents part of the solution. (Choose two.)
NOTE: Each correct selection is worth one point.
You are implementing data loss prevention (DLP).
The company's default browser is Microsoft Edge.
During a recent audit, you discover that some users use Firefox and Google Chrome browsers to upload files labeled as Confidential to a third-party Microsoft
SharePoint Online site that has a URL of https://m365x076709.sharepoint.com. Users are blocked from uploading the confidential files to the site from Microsoft
Edge.
You need to ensure that the users cannot upload files labeled as Confidential from Firefox and Google Chrome to any cloud services.
Which two actions should you perform? Each correct answer presents part of the solution. (Choose two.)
NOTE: Each correct selection is worth one point.
- AFrom the Microsoft 365 Endpoint data loss prevention (Endpoint) DLP settings, add m365x076709.sharepoint.com as a blocked service domain.
- BCreate a DLP policy that applies to the Devices location.
- CFrom the Microsoft 365 Endpoint data loss prevention (Endpoint DLP) settings, add Firefox and Google Chrome to the unallowed browsers list.Most Voted
- DFrom the Microsoft 365 compliance center, onboard the devices.Most Voted
- EFrom the Microsoft 365 Endpoint data loss prevention (Endpoint) DLP settings, add contoso.com as an allowed service domain.
Correct Answer:
CD
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/endpoint-dlp-learn-about?view=o365-worldwide
CD
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/endpoint-dlp-learn-about?view=o365-worldwide
send
light_mode
delete
All Pages