Microsoft SC-200 Exam Practice Questions (P. 5)
- Full Access (411 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #41
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You use Azure Security Center.
You receive a security alert in Security Center.
You need to view recommendations to resolve the alert in Security Center.
Solution: From Regulatory compliance, you download the report.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You use Azure Security Center.
You receive a security alert in Security Center.
You need to view recommendations to resolve the alert in Security Center.
Solution: From Regulatory compliance, you download the report.
Does this meet the goal?
- AYes
- BNoMost Voted
Correct Answer:
B
Reference:
https://docs.microsoft.com/en-us/azure/security-center/security-center-managing-and-responding-alerts
B
Reference:
https://docs.microsoft.com/en-us/azure/security-center/security-center-managing-and-responding-alerts
send
light_mode
delete
Question #42
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You use Azure Security Center.
You receive a security alert in Security Center.
You need to view recommendations to resolve the alert in Security Center.
Solution: From Security alerts, you select the alert, select Take Action, and then expand the Mitigate the threat section.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You use Azure Security Center.
You receive a security alert in Security Center.
You need to view recommendations to resolve the alert in Security Center.
Solution: From Security alerts, you select the alert, select Take Action, and then expand the Mitigate the threat section.
Does this meet the goal?
- AYesMost Voted
- BNo
Correct Answer:
A
Reference:
https://docs.microsoft.com/en-us/azure/security-center/security-center-managing-and-responding-alerts
A
Reference:
https://docs.microsoft.com/en-us/azure/security-center/security-center-managing-and-responding-alerts
send
light_mode
delete
Question #43
You have an Azure subscription that has Azure Defender enabled for all supported resource types.
You need to configure the continuous export of high-severity alerts to enable their retrieval from a third-party security information and event management (SIEM) solution.
To which service should you export the alerts?
You need to configure the continuous export of high-severity alerts to enable their retrieval from a third-party security information and event management (SIEM) solution.
To which service should you export the alerts?
- AAzure Cosmos DB
- BAzure Event Grid
- CAzure Event HubsMost Voted
- DAzure Data Lake
Correct Answer:
C
Reference:
https://docs.microsoft.com/en-us/azure/security-center/continuous-export?tabs=azure-portal
C
Reference:
https://docs.microsoft.com/en-us/azure/security-center/continuous-export?tabs=azure-portal
send
light_mode
delete
Question #44
You are responsible for responding to Azure Defender for Key Vault alerts.
During an investigation of an alert, you discover unauthorized attempts to access a key vault from a Tor exit node.
What should you configure to mitigate the threat?
During an investigation of an alert, you discover unauthorized attempts to access a key vault from a Tor exit node.
What should you configure to mitigate the threat?
- AKey Vault firewalls and virtual networksMost Voted
- BAzure Active Directory (Azure AD) permissions
- Crole-based access control (RBAC) for the key vault
- Dthe access policy settings of the key vault
Correct Answer:
A
Reference:
https://docs.microsoft.com/en-us/azure/key-vault/general/network-security
A
Reference:
https://docs.microsoft.com/en-us/azure/key-vault/general/network-security
send
light_mode
delete
Question #45
HOTSPOT -
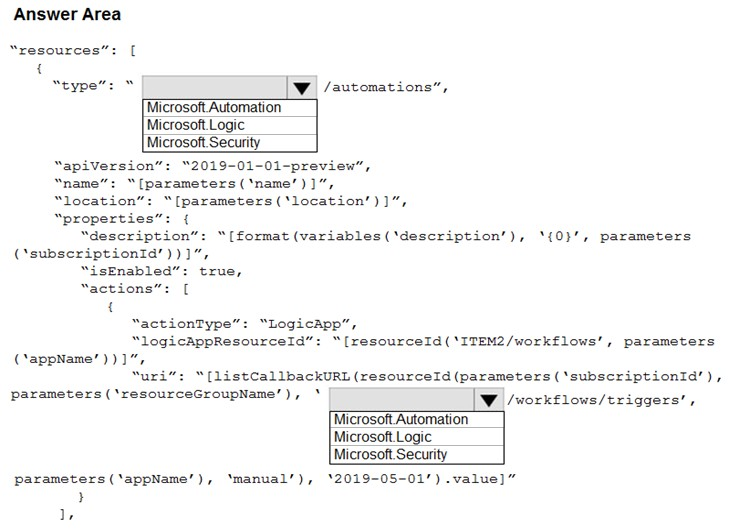
You need to use an Azure Resource Manager template to create a workflow automation that will trigger an automatic remediation when specific security alerts are received by Azure Security Center.
How should you complete the portion of the template that will provision the required Azure resources? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
You need to use an Azure Resource Manager template to create a workflow automation that will trigger an automatic remediation when specific security alerts are received by Azure Security Center.
How should you complete the portion of the template that will provision the required Azure resources? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:
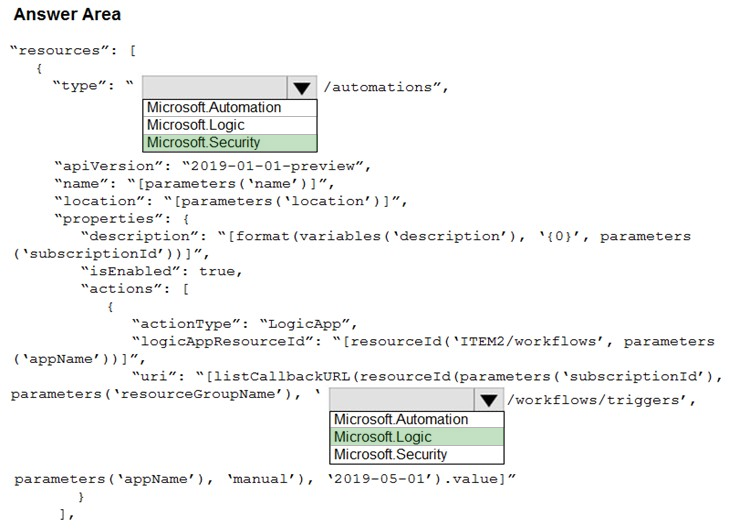
Reference:
https://docs.microsoft.com/en-us/azure/security-center/quickstart-automation-alert

Reference:
https://docs.microsoft.com/en-us/azure/security-center/quickstart-automation-alert
send
light_mode
delete
Question #46
You have an Azure subscription that contains a Log Analytics workspace.
You need to enable just-in-time (JIT) VM access and network detections for Azure resources.
Where should you enable Azure Defender?
You need to enable just-in-time (JIT) VM access and network detections for Azure resources.
Where should you enable Azure Defender?
- Aat the subscription levelMost Voted
- Bat the workspace level
- Cat the resource level
Correct Answer:
A
Reference:
https://docs.microsoft.com/en-us/azure/security-center/enable-azure-defender
A
Reference:
https://docs.microsoft.com/en-us/azure/security-center/enable-azure-defender
send
light_mode
delete
Question #47
You use Azure Defender.
You have an Azure Storage account that contains sensitive information.
You need to run a PowerShell script if someone accesses the storage account from a suspicious IP address.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You have an Azure Storage account that contains sensitive information.
You need to run a PowerShell script if someone accesses the storage account from a suspicious IP address.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- AFrom Azure Security Center, enable workflow automation.Most Voted
- BCreate an Azure logic app that has a manual trigger.
- CCreate an Azure logic app that has an Azure Security Center alert trigger.Most Voted
- DCreate an Azure logic app that has an HTTP trigger.
- EFrom Azure Active Directory (Azure AD), add an app registration.
Correct Answer:
AC
Reference:
https://docs.microsoft.com/en-us/azure/storage/common/azure-defender-storage-configure?tabs=azure-security-center https://docs.microsoft.com/en-us/azure/security-center/workflow-automation
AC
Reference:
https://docs.microsoft.com/en-us/azure/storage/common/azure-defender-storage-configure?tabs=azure-security-center https://docs.microsoft.com/en-us/azure/security-center/workflow-automation
send
light_mode
delete
Question #48
HOTSPOT -
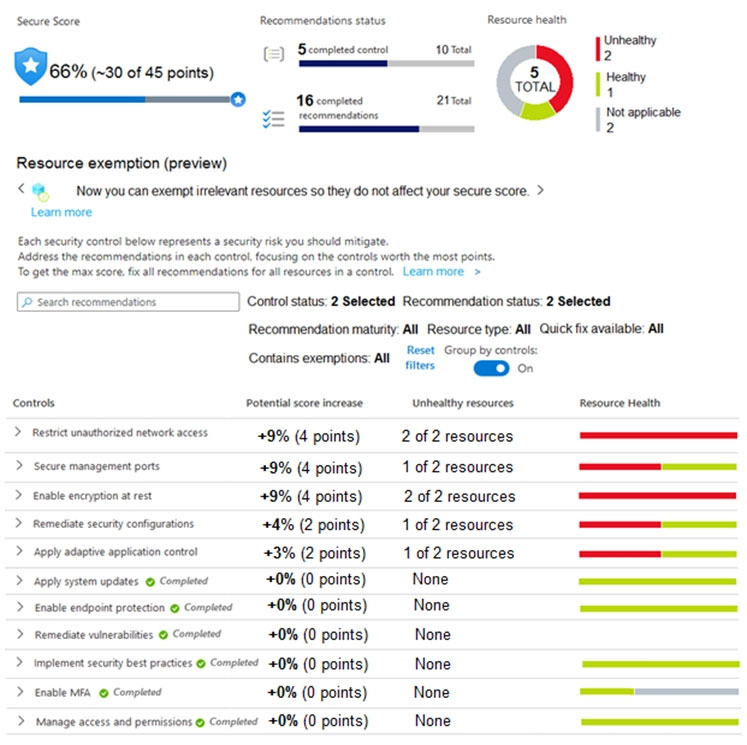
You manage the security posture of an Azure subscription that contains two virtual machines name vm1 and vm2.
The secure score in Azure Security Center is shown in the Security Center exhibit. (Click the Security Center tab.)
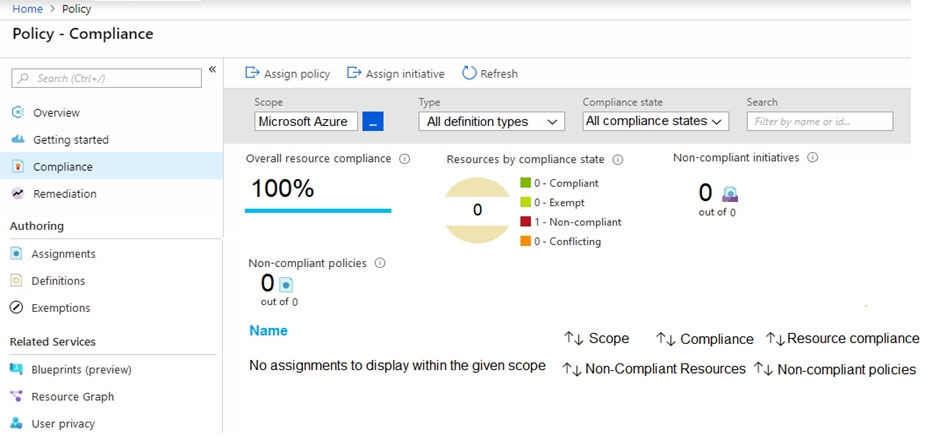
Azure Policy assignments are configured as shown in the Policies exhibit. (Click the Policies tab.)
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
You manage the security posture of an Azure subscription that contains two virtual machines name vm1 and vm2.
The secure score in Azure Security Center is shown in the Security Center exhibit. (Click the Security Center tab.)

Azure Policy assignments are configured as shown in the Policies exhibit. (Click the Policies tab.)

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:
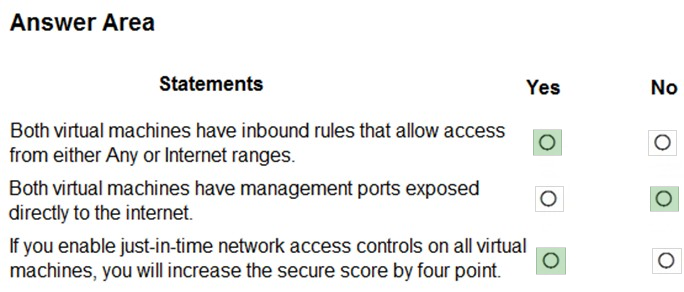
Reference:
https://techcommunity.microsoft.com/t5/azure-security-center/security-control-restrict-unauthorized-network-access/ba-p/1593833 https://techcommunity.microsoft.com/t5/azure-security-center/security-control-secure-management-ports/ba-p/1505770

Reference:
https://techcommunity.microsoft.com/t5/azure-security-center/security-control-restrict-unauthorized-network-access/ba-p/1593833 https://techcommunity.microsoft.com/t5/azure-security-center/security-control-secure-management-ports/ba-p/1505770
send
light_mode
delete
Question #49
DRAG DROP -
You are informed of a new common vulnerabilities and exposures (CVE) vulnerability that affects your environment.
You need to use Microsoft Defender Security Center to request remediation from the team responsible for the affected systems if there is a documented active exploit available.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:
You are informed of a new common vulnerabilities and exposures (CVE) vulnerability that affects your environment.
You need to use Microsoft Defender Security Center to request remediation from the team responsible for the affected systems if there is a documented active exploit available.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:

Correct Answer:
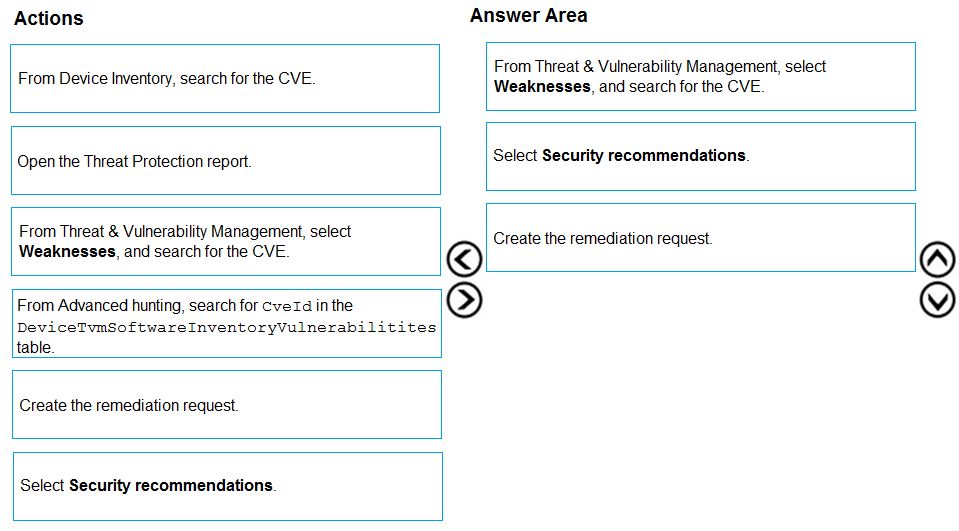
Reference:
https://techcommunity.microsoft.com/t5/core-infrastructure-and-security/microsoft-defender-atp-remediate-apps-using-mem/ba-p/1599271

Reference:
https://techcommunity.microsoft.com/t5/core-infrastructure-and-security/microsoft-defender-atp-remediate-apps-using-mem/ba-p/1599271
send
light_mode
delete
Question #50
You use Azure Security Center.
You receive a security alert in Security Center.
You need to view recommendations to resolve the alert in Security Center.
What should you do?
You receive a security alert in Security Center.
You need to view recommendations to resolve the alert in Security Center.
What should you do?
- AFrom Security alerts, select the alert, select Take Action, and then expand the Prevent future attacks section.
- BFrom Security alerts, select Take Action, and then expand the Mitigate the threat section.Most Voted
- CFrom Regulatory compliance, download the report.
- DFrom Recommendations, download the CSV report.
Correct Answer:
B
Reference:
https://docs.microsoft.com/en-us/azure/security-center/security-center-managing-and-responding-alerts
B
Reference:
https://docs.microsoft.com/en-us/azure/security-center/security-center-managing-and-responding-alerts
send
light_mode
delete
All Pages
