Microsoft SC-200 Exam Practice Questions (P. 4)
- Full Access (411 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #31
You have a Microsoft 365 subscription that uses Microsoft 365 Defender.
You need to identify all the entities affected by an incident.
Which tab should you use in the Microsoft 365 Defender portal?
You need to identify all the entities affected by an incident.
Which tab should you use in the Microsoft 365 Defender portal?
- AInvestigations
- BDevices
- CEvidence and ResponseMost Voted
- DAlerts
Correct Answer:
C
The Evidence and Response tab shows all the supported events and suspicious entities in the alerts in the incident.
Incorrect:
* The Investigations tab lists all the automated investigations triggered by alerts in this incident. Automated investigations will perform remediation actions or wait for analyst approval of actions, depending on how you configured your automated investigations to run in Defender for Endpoint and Defender for Office 365.
* Devices
The Devices tab lists all the devices related to the incident.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender/investigate-incidents
C
The Evidence and Response tab shows all the supported events and suspicious entities in the alerts in the incident.
Incorrect:
* The Investigations tab lists all the automated investigations triggered by alerts in this incident. Automated investigations will perform remediation actions or wait for analyst approval of actions, depending on how you configured your automated investigations to run in Defender for Endpoint and Defender for Office 365.
* Devices
The Devices tab lists all the devices related to the incident.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender/investigate-incidents
send
light_mode
delete
Question #32
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You use Azure Security Center.
You receive a security alert in Security Center.
You need to view recommendations to resolve the alert in Security Center.
Solution: From Security alerts, you select the alert, select Take Action, and then expand the Prevent future attacks section.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You use Azure Security Center.
You receive a security alert in Security Center.
You need to view recommendations to resolve the alert in Security Center.
Solution: From Security alerts, you select the alert, select Take Action, and then expand the Prevent future attacks section.
Does this meet the goal?
- AYes
- BNoMost Voted
Correct Answer:
B
You need to resolve the existing alert, not prevent future alerts. Therefore, you need to select the 'Mitigate the threat' option.
Reference:
https://docs.microsoft.com/en-us/azure/security-center/security-center-managing-and-responding-alerts
B
You need to resolve the existing alert, not prevent future alerts. Therefore, you need to select the 'Mitigate the threat' option.
Reference:
https://docs.microsoft.com/en-us/azure/security-center/security-center-managing-and-responding-alerts
send
light_mode
delete
Question #33
You receive an alert from Azure Defender for Key Vault.
You discover that the alert is generated from multiple suspicious IP addresses.
You need to reduce the potential of Key Vault secrets being leaked while you investigate the issue. The solution must be implemented as soon as possible and must minimize the impact on legitimate users.
What should you do first?
You discover that the alert is generated from multiple suspicious IP addresses.
You need to reduce the potential of Key Vault secrets being leaked while you investigate the issue. The solution must be implemented as soon as possible and must minimize the impact on legitimate users.
What should you do first?
- AModify the access control settings for the key vault.
- BEnable the Key Vault firewall.Most Voted
- CCreate an application security group.
- DModify the access policy for the key vault.
Correct Answer:
B
Reference:
https://docs.microsoft.com/en-us/azure/security-center/defender-for-key-vault-usage
B
Reference:
https://docs.microsoft.com/en-us/azure/security-center/defender-for-key-vault-usage
send
light_mode
delete
Question #34
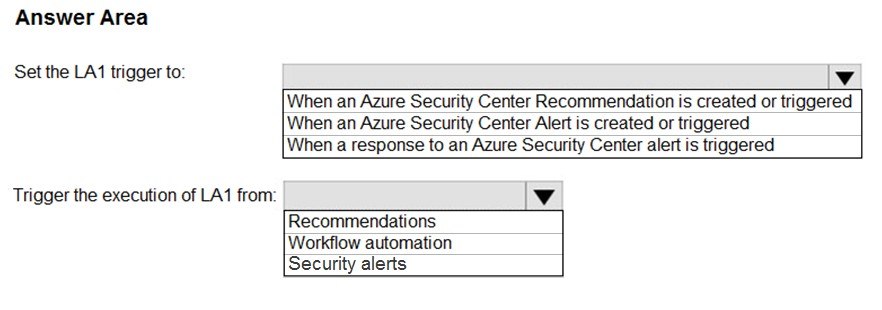
HOTSPOT -
You have an Azure subscription that has Azure Defender enabled for all supported resource types.
You create an Azure logic app named LA1.
You plan to use LA1 to automatically remediate security risks detected in Azure Security Center.
You need to test LA1 in Security Center.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
You have an Azure subscription that has Azure Defender enabled for all supported resource types.
You create an Azure logic app named LA1.
You plan to use LA1 to automatically remediate security risks detected in Azure Security Center.
You need to test LA1 in Security Center.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:
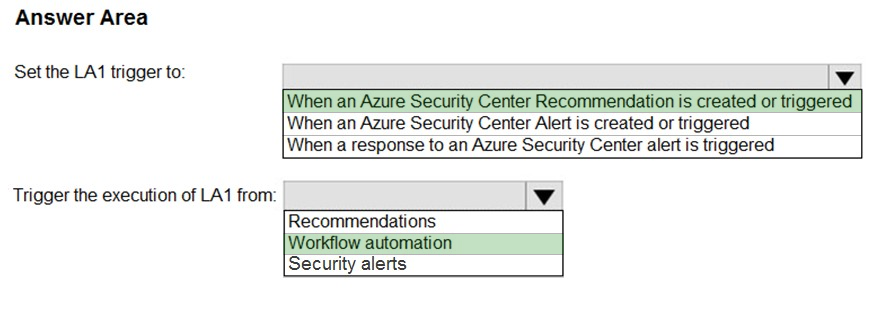
Reference:
https://docs.microsoft.com/en-us/azure/security-center/workflow-automation#create-a-logic-app-and-define-when-it-should-automatically-run

Reference:
https://docs.microsoft.com/en-us/azure/security-center/workflow-automation#create-a-logic-app-and-define-when-it-should-automatically-run
send
light_mode
delete
Question #35
You have a Microsoft 365 subscription that uses Azure Defender.
You have 100 virtual machines in a resource group named RG1.
You assign the Security Admin roles to a new user named SecAdmin1.
You need to ensure that SecAdmin1 can apply quick fixes to the virtual machines by using Azure Defender. The solution must use the principle of least privilege.
Which role should you assign to SecAdmin1?
You have 100 virtual machines in a resource group named RG1.
You assign the Security Admin roles to a new user named SecAdmin1.
You need to ensure that SecAdmin1 can apply quick fixes to the virtual machines by using Azure Defender. The solution must use the principle of least privilege.
Which role should you assign to SecAdmin1?
- Athe Security Reader role for the subscription
- Bthe Contributor for the subscription
- Cthe Contributor role for RG1Most Voted
- Dthe Owner role for RG1
Correct Answer:
C
C
 GPT-4o - Answer
GPT-4o - Answer
Indeed, granting the Contributor role for RG1 to SecAdmin1 is the best course of action to ensure the ability to apply quick fixes to the virtual machines using Azure Defender, while still sticking strictly to the principle of least privilege. This role provides SecAdmin1 with necessary permissions like deploying resources and editing properties specifically within RG1. However, it cleverly avoids overextending privileges that could potentially compromise broader security measures by not granting admin rights at the subscription level. This tailored permission approach supports efficient and secure management without unnecessary access.
send
light_mode
delete
Question #36
You provision a Linux virtual machine in a new Azure subscription.
You enable Azure Defender and onboard the virtual machine to Azure Defender.
You need to verify that an attack on the virtual machine triggers an alert in Azure Defender.
Which two Bash commands should you run on the virtual machine? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You enable Azure Defender and onboard the virtual machine to Azure Defender.
You need to verify that an attack on the virtual machine triggers an alert in Azure Defender.
Which two Bash commands should you run on the virtual machine? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Acp /bin/echo ./asc_alerttest_662jfi039n
- B./alerttest testing eicar pipe
- Ccp /bin/echo ./alerttestMost Voted
- D./asc_alerttest_662jfi039n testing eicar pipeMost Voted
Correct Answer:
AD
Reference:
https://docs.microsoft.com/en-us/azure/security-center/security-center-alert-validation#simulate-alerts-on-your-azure-vms-linux-
AD
Reference:
https://docs.microsoft.com/en-us/azure/security-center/security-center-alert-validation#simulate-alerts-on-your-azure-vms-linux-
send
light_mode
delete
Question #37
You create an Azure subscription named sub1.
In sub1, you create a Log Analytics workspace named workspace1.
You enable Azure Security Center and configure Security Center to use workspace1.
You need to collect security event logs from the Azure virtual machines that report to workspace1.
What should you do?
In sub1, you create a Log Analytics workspace named workspace1.
You enable Azure Security Center and configure Security Center to use workspace1.
You need to collect security event logs from the Azure virtual machines that report to workspace1.
What should you do?
- AFrom Security Center, enable data collectionMost Voted
- BIn sub1, register a provider.
- CFrom Security Center, create a Workflow automation.
- DIn workspace1, create a workbook.
Correct Answer:
A
Reference:
https://docs.microsoft.com/en-us/azure/security-center/security-center-enable-data-collection
A
Reference:
https://docs.microsoft.com/en-us/azure/security-center/security-center-enable-data-collection
send
light_mode
delete
Question #38
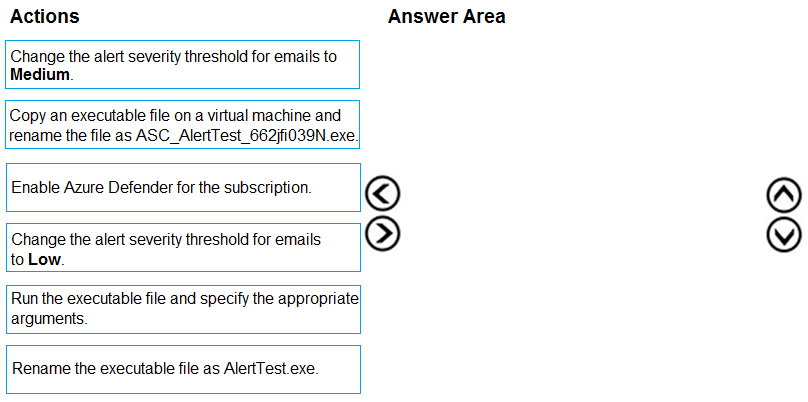
DRAG DROP -
You create a new Azure subscription and start collecting logs for Azure Monitor.
You need to configure Azure Security Center to detect possible threats related to sign-ins from suspicious IP addresses to Azure virtual machines. The solution must validate the configuration.
Which three actions should you perform in a sequence? To answer, move the appropriate actions from the list of action to the answer area and arrange them in the correct order.
Select and Place:
You create a new Azure subscription and start collecting logs for Azure Monitor.
You need to configure Azure Security Center to detect possible threats related to sign-ins from suspicious IP addresses to Azure virtual machines. The solution must validate the configuration.
Which three actions should you perform in a sequence? To answer, move the appropriate actions from the list of action to the answer area and arrange them in the correct order.
Select and Place:

Correct Answer:
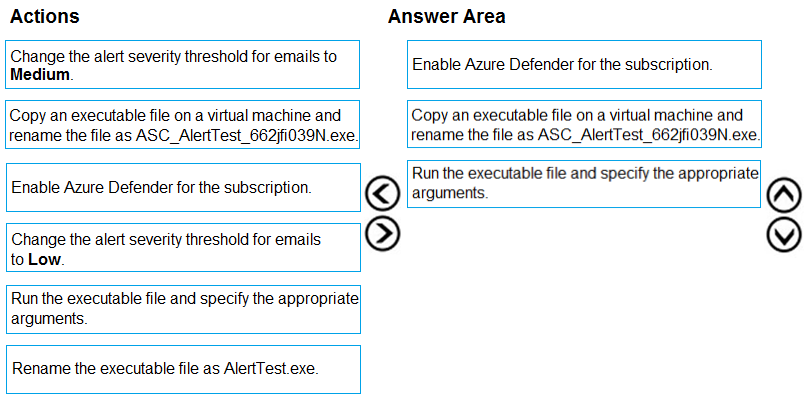
Reference:
https://docs.microsoft.com/en-us/azure/security-center/security-center-alert-validation

Reference:
https://docs.microsoft.com/en-us/azure/security-center/security-center-alert-validation
send
light_mode
delete
Question #39
Your company uses Azure Security Center and Azure Defender.
The security operations team at the company informs you that it does NOT receive email notifications for security alerts.
What should you configure in Security Center to enable the email notifications?
The security operations team at the company informs you that it does NOT receive email notifications for security alerts.
What should you configure in Security Center to enable the email notifications?
- ASecurity solutions
- BSecurity policy
- CPricing & settingsMost Voted
- DSecurity alerts
- EAzure Defender
Correct Answer:
C
Reference:
https://docs.microsoft.com/en-us/azure/security-center/security-center-provide-security-contact-details
C
Reference:
https://docs.microsoft.com/en-us/azure/security-center/security-center-provide-security-contact-details
send
light_mode
delete
Question #40
DRAG DROP -
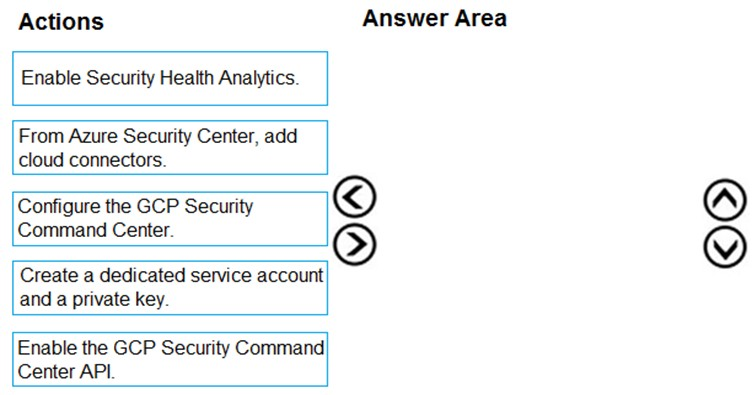
You have resources in Azure and Google cloud.
You need to ingest Google Cloud Platform (GCP) data into Azure Defender.
In which order should you perform the actions? To answer, move all actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:
You have resources in Azure and Google cloud.
You need to ingest Google Cloud Platform (GCP) data into Azure Defender.
In which order should you perform the actions? To answer, move all actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:

Correct Answer:
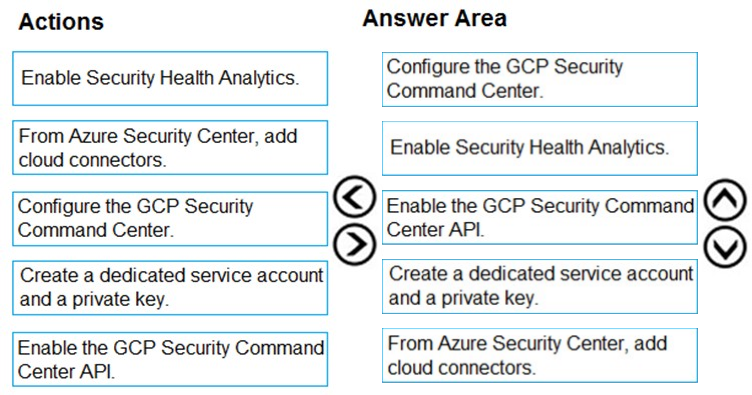
Reference:
https://docs.microsoft.com/en-us/azure/security-center/quickstart-onboard-gcp

Reference:
https://docs.microsoft.com/en-us/azure/security-center/quickstart-onboard-gcp
send
light_mode
delete
All Pages
