Microsoft 70-743 Exam Practice Questions (P. 4)
- Full Access (231 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #16
You have a Hyper-V host named Server1 that runs Windows Server 2016.
Server1 has a virtual machine named VM1. VM1 is configured to run the Docker daemon.
On VM1, you have a container network that uses transparent mode.
You need to ensure that containers that run on VM1 can obtain IP addresses from DHCP.
What should you do?
Server1 has a virtual machine named VM1. VM1 is configured to run the Docker daemon.
On VM1, you have a container network that uses transparent mode.
You need to ensure that containers that run on VM1 can obtain IP addresses from DHCP.
What should you do?
- AOn VM1, run docker network connect.
- BOn Server1, run docker network connect.
- COn VM1, run Get-VMNetworkAdapter –VMName VM1 | Set-VMNetworkAdapter –MacAddressSpoofing On.
- DOn Server1, run Get-VMNetworkAdapter –VMName VM1 | Set-VMNetworkAdapter – MacAddressSpoofing On.
Correct Answer:
D
If the container host is virtualized, and you wish to use DHCP for IP assignment, you must enable MACAddressSpoofing.
PS C:\> Get-VMNetworkAdapter -VMName ContainerHostVM | Set-VMNetworkAdapter -MacAddressSpoofing On
The command needs to be run on the Hyper-V host.
References: https://msdn.microsoft.com/en-us/virtualization/windowscontainers/management/container_networking
D
If the container host is virtualized, and you wish to use DHCP for IP assignment, you must enable MACAddressSpoofing.
PS C:\> Get-VMNetworkAdapter -VMName ContainerHostVM | Set-VMNetworkAdapter -MacAddressSpoofing On
The command needs to be run on the Hyper-V host.
References: https://msdn.microsoft.com/en-us/virtualization/windowscontainers/management/container_networking
send
light_mode
delete
Question #17
You have a server named Server1 that runs Windows Server 2016. You install the Docker daemon on Server1.
You need to configure the Docker daemon to accept connections only on TCP port 64500.
What should you do?
You need to configure the Docker daemon to accept connections only on TCP port 64500.
What should you do?
- AEdit the configuration.json file.
- BRun the Set-ServiceWindows PowerShell cmdlet.
- CEdit the daemon.json file.
- DRun the New-NetFirewallRule cmdlet
Correct Answer:
C
Configure Docker with Configuration File
The preferred method for configuring the Docker Engine on Windows is using a configuration file. The configuration file can be found at 'c:\ProgramData\docker
\config\daemon.json'.
Only the desired configuration changes need to be added to the configuration file. For example, this sample configures the Docker Engine to accept incoming connections on port 64500. All other configuration options will use default values.
{
"hosts": ["tcp://0.0.0.0:64500"]
}
References:
https://msdn.microsoft.com/en-us/virtualization/windowscontainers/docker/configure_docker_daemon
C
Configure Docker with Configuration File
The preferred method for configuring the Docker Engine on Windows is using a configuration file. The configuration file can be found at 'c:\ProgramData\docker
\config\daemon.json'.
Only the desired configuration changes need to be added to the configuration file. For example, this sample configures the Docker Engine to accept incoming connections on port 64500. All other configuration options will use default values.
{
"hosts": ["tcp://0.0.0.0:64500"]
}
References:
https://msdn.microsoft.com/en-us/virtualization/windowscontainers/docker/configure_docker_daemon
send
light_mode
delete
Question #18
You have a failover cluster named Cluster1.
A virtual machine named VM1 is a highly available virtual machine that runs on Cluster1. A custom application named App1 runs on VM1.
You need to configure monitoring on VM1. If App1 adds an error entry to the Application even log, VM1 should be automatically rebooted and moved to another cluster node.
Which tool should you use?
A virtual machine named VM1 is a highly available virtual machine that runs on Cluster1. A custom application named App1 runs on VM1.
You need to configure monitoring on VM1. If App1 adds an error entry to the Application even log, VM1 should be automatically rebooted and moved to another cluster node.
Which tool should you use?
- AResource Monitor
- BFailover Cluster Manager
- CServer Manager
- DHyper-V Manager
Correct Answer:
B
Do you have a large number of virtualized workloads in your cluster? Have you been looking for a solution that allows you to detect if any of the virtualized workloads in your cluster are behaving abnormally? Would you like the cluster service to take recovery actions when these workloads are in an unhealthy state? In
Windows Server 2012/2016, there is a great new feature, in Failover Clustering called "VM Monitoring", which does exactly that – it allows you monitor the health state of applications that are running within a virtual machine and then reports that to the host level so that it can take recovery actions.
VM Monitoring can be easily configured using the Failover Cluster Manager through the following steps:
✑ Right click on the Virtual Machine role on which you want to configure monitoring
✑ Select "More Actions" and then the "Configure Monitoring" options
✑ You will then see a list of services that can be configured for monitoring using the Failover Cluster Manager.
References: https://blogs.msdn.microsoft.com/clustering/2012/04/18/how-to-configure-vm-monitoring-in-windows-server-2012/
B
Do you have a large number of virtualized workloads in your cluster? Have you been looking for a solution that allows you to detect if any of the virtualized workloads in your cluster are behaving abnormally? Would you like the cluster service to take recovery actions when these workloads are in an unhealthy state? In
Windows Server 2012/2016, there is a great new feature, in Failover Clustering called "VM Monitoring", which does exactly that – it allows you monitor the health state of applications that are running within a virtual machine and then reports that to the host level so that it can take recovery actions.
VM Monitoring can be easily configured using the Failover Cluster Manager through the following steps:
✑ Right click on the Virtual Machine role on which you want to configure monitoring
✑ Select "More Actions" and then the "Configure Monitoring" options
✑ You will then see a list of services that can be configured for monitoring using the Failover Cluster Manager.
References: https://blogs.msdn.microsoft.com/clustering/2012/04/18/how-to-configure-vm-monitoring-in-windows-server-2012/
send
light_mode
delete
Question #19
You have a server named Server1 that runs Windows Server 2016.
The disk configuration for Server1 is shown in the exhibit. (Click the Exhibit button.)
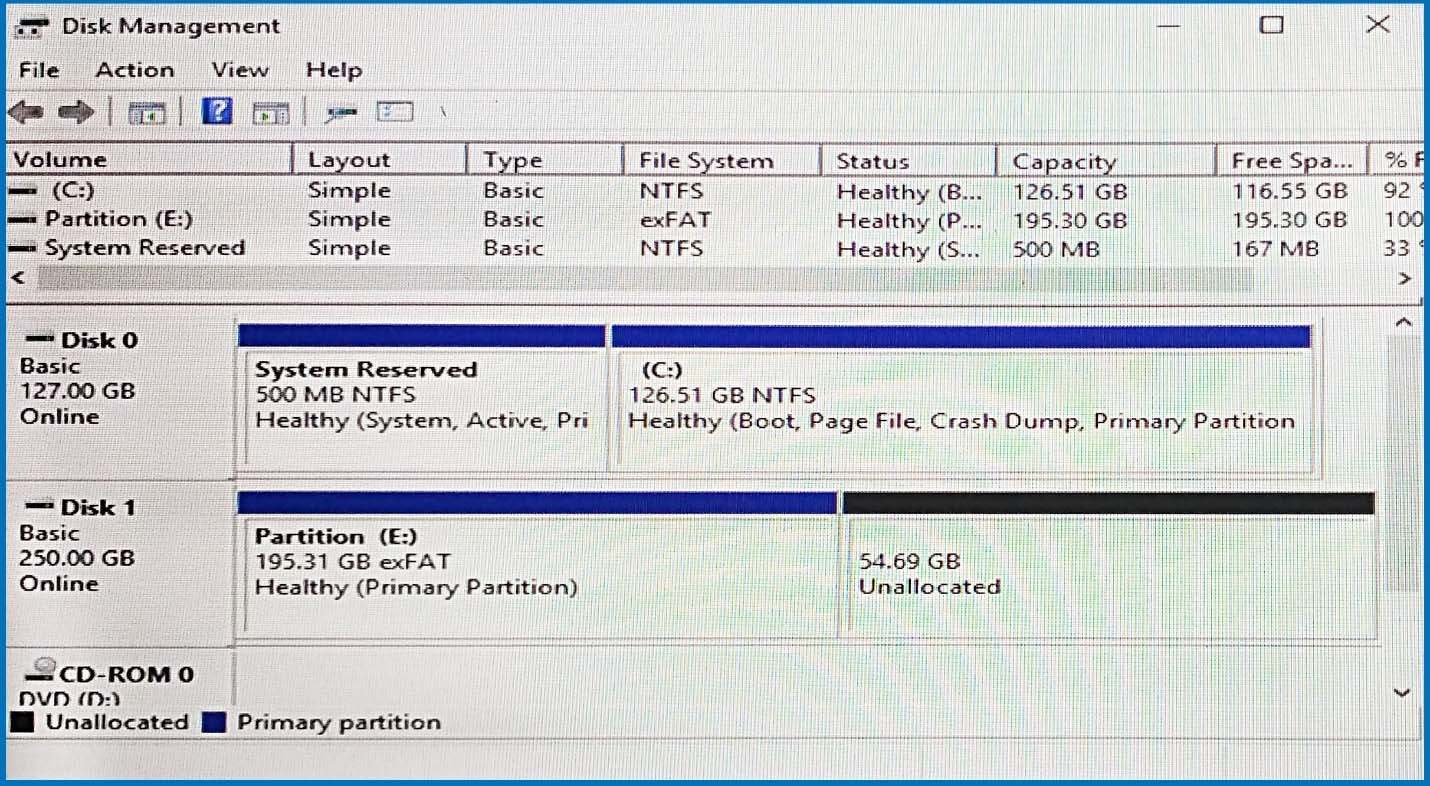
You add Server1 to a cluster.
You need to ensure that you can use Disk 1 for Storage Spaces Direct.
What should you do first?
The disk configuration for Server1 is shown in the exhibit. (Click the Exhibit button.)

You add Server1 to a cluster.
You need to ensure that you can use Disk 1 for Storage Spaces Direct.
What should you do first?
- ASet Disk 1 to offline.
- BConvert Partition (E:) to ReFS.
- CConvert Disk 1 to a dynamic disk.
- DDelete Partition (E:).
Correct Answer:
D
The disks used in Storage Spaces Direct cannot contain existing partitions.
D
The disks used in Storage Spaces Direct cannot contain existing partitions.
send
light_mode
delete
Question #20
Your network contains an Active Directory domain. The domain contains two Hyper-V hosts.
You plan to perform live migrations between the hosts.
You need to ensure that the live migration traffic is authenticated by using Kerberos.
What should you do first?
You plan to perform live migrations between the hosts.
You need to ensure that the live migration traffic is authenticated by using Kerberos.
What should you do first?
- AFrom Server Manager, install the Host Guardian Service server role on a domain controller.
- BFrom Active Directory Users and Computers, add the computer accounts for both servers to the Cryptographic Operators group.
- CFrom Active Directory Users and Computers, modify the Delegation properties of the computer accounts for both servers.
- DFrom Server Manager, install the Host Guardian Service server role on both servers.
Correct Answer:
C
If you have decided to use Kerberos to authenticate live migration traffic, configure constrained delegation before you proceed to the rest of the steps.
To configure constrained delegation
✑ Open the Active Directory Users and Computers snap-in.
From the navigation pane, select the domain and double-click the Computers folder.

✑ From the Computers folder, right-click the computer account of the source server and then click Properties.
✑ In the Properties dialog box, click the Delegation tab.
✑ On the delegation tab, select Trust this computer for delegation to the specified services only. Under that option, select Use Kerberos only.
C
If you have decided to use Kerberos to authenticate live migration traffic, configure constrained delegation before you proceed to the rest of the steps.
To configure constrained delegation
✑ Open the Active Directory Users and Computers snap-in.
From the navigation pane, select the domain and double-click the Computers folder.

✑ From the Computers folder, right-click the computer account of the source server and then click Properties.
✑ In the Properties dialog box, click the Delegation tab.
✑ On the delegation tab, select Trust this computer for delegation to the specified services only. Under that option, select Use Kerberos only.
send
light_mode
delete
All Pages
