Microsoft 70-686 Exam Practice Questions (P. 4)
- Full Access (183 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #16
Your company infrastructure includes a Windows Server 2008 R2 file server and 1,000 Windows 7 Enterprise client computers.
The company wants to require a secure connection between client computers and the file server.
You need to create and deploy a Group Policy object (GPO) that includes a rule for Windows Firewall with Advanced Security.
What should you do?
The company wants to require a secure connection between client computers and the file server.
You need to create and deploy a Group Policy object (GPO) that includes a rule for Windows Firewall with Advanced Security.
What should you do?
- ACreate an Isolation rule and specify Request authentication for inbound and outbound connections.
- BCreate a Tunnel rule and specify Gateway-to-client as the tunnel type.
- CCreate a Server-to-server rule and specify the endpoints as Any IP address and the file server IP address.
- DCreate an Authentication exemption rule and add the file server IP address to the Exempt Computers list.
Correct Answer:
C
The PDC emulator master also serves as the machine to which all domain controllers in the domain will synchronise their clocks. It, in turn, should be configured to synchronise to an external NTP time source http://en.wikipedia.org/wiki/Primary_Domain_Controller
C
The PDC emulator master also serves as the machine to which all domain controllers in the domain will synchronise their clocks. It, in turn, should be configured to synchronise to an external NTP time source http://en.wikipedia.org/wiki/Primary_Domain_Controller
send
light_mode
delete
Question #17
You deploy Windows 7 to the computers that are used by your companys Web developers. All Web developer user accounts are in a single organizational unit
(OU).
Internet Explorer is blocking pop-up windows for multiple internal Web applications that are hosted on different servers.
You need to use Group Policy to ensure that Internet Explorer does not block pop-up windows for internal Web applications.
What should you do?
(OU).
Internet Explorer is blocking pop-up windows for multiple internal Web applications that are hosted on different servers.
You need to use Group Policy to ensure that Internet Explorer does not block pop-up windows for internal Web applications.
What should you do?
- AEnable Compatibility View in Internet Explorer.
- BAdd each server to the Intranet zone.
- CAdd each server to the Trusted Sites zone.
- DSet the default security setting in Internet Explorer to Medium.
Correct Answer:
B
Pop-up Blocker features -
Pop-up Blocker is turned on by default. There are restrictions on the size and position of pop-up windows, regardless of the Pop-up Blocker setting. Pop-up windows cannot be opened larger than or outside the viewable desktop area. For more information, see "Windows Restrictions" in this document.
When this functionality is enabled, automatic and background pop-up windows are blocked, but windows that are opened by a user click will still open in the usual manner. Note that sites in the
Trusted Sites and Local -
Intranet zones do not have their pop-up windows blocked by default, as they are considered safe. This setting can be configured in the Security tab in Internet
Options.
http://technet.microsoft.com/en-us/library/cc784600(v=ws.10).aspx hints: internal web , so i choose intranet zones.
Local Intranet Zone -
By default, the Local Intranet zone contains all network connections that were established by using a Universal
Naming Convention (UNC) path, and Web sites that bypass the proxy server or have names that do not include periods (for example, http://local), as long as they are not assigned to either the Restricted Sites or Trusted Sites zone. The default security level for the Local Intranet zone is set to Medium (Internet Explorer 4) or
Medium-low (Internet Explorer 5 and 6). Be aware that when you access a local area network (LAN) or an intranet share, or an intranet Web site by using an
Internet Protocol (IP) address or by using a fully qualified domain name (FQDN), the share or Web site is identified as being in the Internet zone instead of in the
Local intranet zone.
Trusted Sites Zone -
This zone contains Web sites that you trust as safe (such as Web sites that are on your organization's intranet or that come from established companies in whom you have confidence). When you add a Web site to the Trusted Sites zone, you believe that files you download or that you run from the Web site will not damage your computer or data. By default, there are no Web sites that are assigned to the Trusted Sites zone, and the security level is set to Low. http://support.microsoft.com/kb/174360
B
Pop-up Blocker features -
Pop-up Blocker is turned on by default. There are restrictions on the size and position of pop-up windows, regardless of the Pop-up Blocker setting. Pop-up windows cannot be opened larger than or outside the viewable desktop area. For more information, see "Windows Restrictions" in this document.
When this functionality is enabled, automatic and background pop-up windows are blocked, but windows that are opened by a user click will still open in the usual manner. Note that sites in the
Trusted Sites and Local -
Intranet zones do not have their pop-up windows blocked by default, as they are considered safe. This setting can be configured in the Security tab in Internet
Options.
http://technet.microsoft.com/en-us/library/cc784600(v=ws.10).aspx hints: internal web , so i choose intranet zones.
Local Intranet Zone -
By default, the Local Intranet zone contains all network connections that were established by using a Universal
Naming Convention (UNC) path, and Web sites that bypass the proxy server or have names that do not include periods (for example, http://local), as long as they are not assigned to either the Restricted Sites or Trusted Sites zone. The default security level for the Local Intranet zone is set to Medium (Internet Explorer 4) or
Medium-low (Internet Explorer 5 and 6). Be aware that when you access a local area network (LAN) or an intranet share, or an intranet Web site by using an
Internet Protocol (IP) address or by using a fully qualified domain name (FQDN), the share or Web site is identified as being in the Internet zone instead of in the
Local intranet zone.
Trusted Sites Zone -
This zone contains Web sites that you trust as safe (such as Web sites that are on your organization's intranet or that come from established companies in whom you have confidence). When you add a Web site to the Trusted Sites zone, you believe that files you download or that you run from the Web site will not damage your computer or data. By default, there are no Web sites that are assigned to the Trusted Sites zone, and the security level is set to Low. http://support.microsoft.com/kb/174360
send
light_mode
delete
Question #18
Your network has client computers that run Windows 7 Enterprise. You plan to deploy new administrative template policy settings by using custom ADMX files.
You create the custom ADMX files, and you save them on a network share. You start Group Policy Object Editor (GPO Editor). The custom ADMX files are not available in the Group Policy editing session. You need to ensure that the ADMX files are available to the GPO Editor. What should you do?
You create the custom ADMX files, and you save them on a network share. You start Group Policy Object Editor (GPO Editor). The custom ADMX files are not available in the Group Policy editing session. You need to ensure that the ADMX files are available to the GPO Editor. What should you do?
- ACopy the ADMX files to the % systemroot% \ inf folder on each Windows 7 computer, and then restart the GPO Editor.
- BSet the network share permissions to grant all Windows 7 users Read access for the share.
- CCopy the ADMX files to the %systemroot% \ system32 folder on each Windows 7 computer, and then restart the GPO Editor.
- DCopy the ADMX files to the central store, and then restart the GPO Editor.
Correct Answer:
D
http://support.microsoft.com/kb/929841
To take advantage of the benefits of .admx files, you must create a Central Store in the SYSVOL folder on a domain controller. The Central Store is a file location that is checked by the Group Policy tools. The Group Policy tools use any .admx files that are in the Central Store. The files that are in the Central Store are later replicated to all domain controllers in the domain.
D
http://support.microsoft.com/kb/929841
To take advantage of the benefits of .admx files, you must create a Central Store in the SYSVOL folder on a domain controller. The Central Store is a file location that is checked by the Group Policy tools. The Group Policy tools use any .admx files that are in the Central Store. The files that are in the Central Store are later replicated to all domain controllers in the domain.
send
light_mode
delete
Question #19
DRAG DROP -
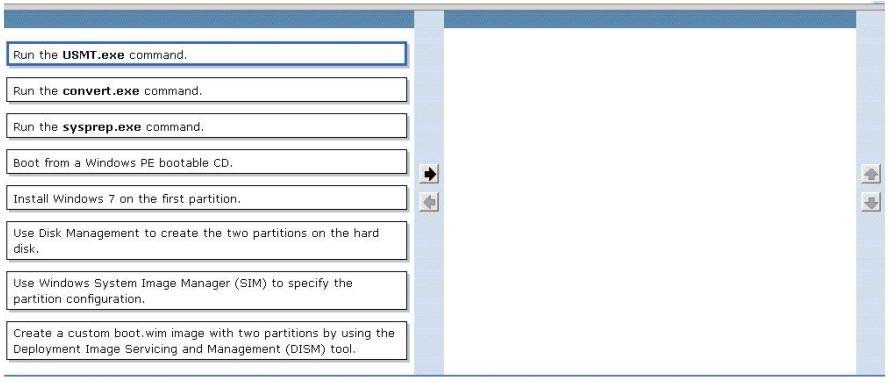
You are planning to deploy Windows 7 Enterprise to all of your company's client computers.
You have the following requirements:
"¢ Create two custom partitions on each client computer's hard disk, one for the operating system and the other for data.
"¢ Automatically create the partitions during Windows Setup.
You need to design an image that meets the requirements.
Which two actions should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order)
Select and Place:
You are planning to deploy Windows 7 Enterprise to all of your company's client computers.
You have the following requirements:
"¢ Create two custom partitions on each client computer's hard disk, one for the operating system and the other for data.
"¢ Automatically create the partitions during Windows Setup.
You need to design an image that meets the requirements.
Which two actions should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order)
Select and Place:

Correct Answer:
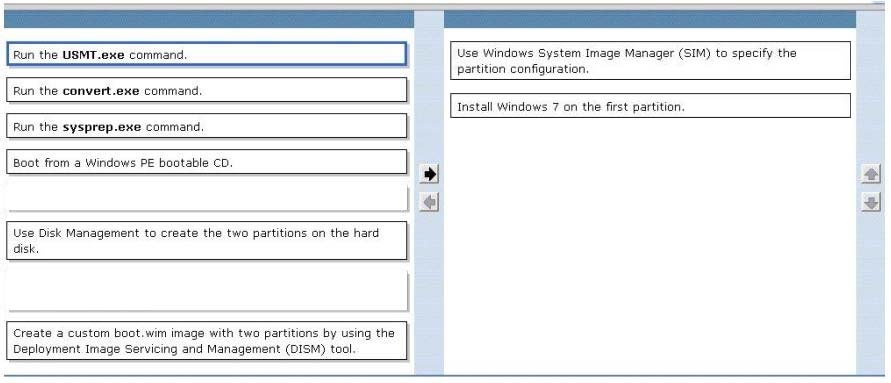
Windows System Image Manager create answer file
Using windows 7 setup DVD can create partition based on answer file.

Windows System Image Manager create answer file
Using windows 7 setup DVD can create partition based on answer file.
send
light_mode
delete
Question #20
DRAG DROP -
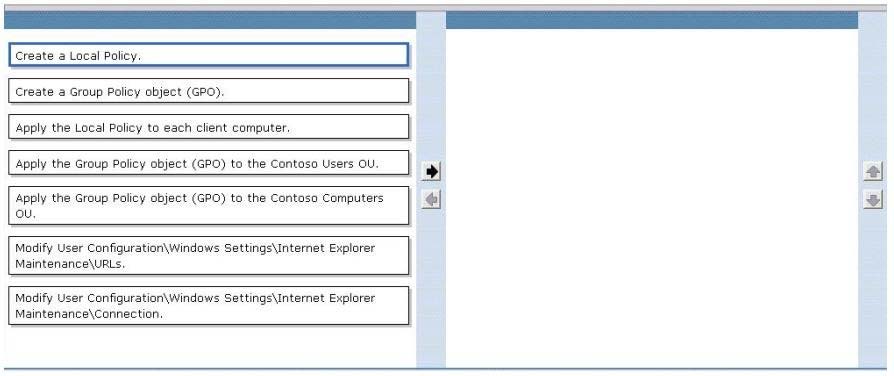
All client computers in an organization run Windows 7 and are joined to an Active Directory Domain Services (AD DS) domain. All user objects are stored in an
Organizational Unit (OU) named Contoso Users. All computer objects are stored in an OU named Contoso Computers.
You need to add a proxy server to the Microsoft Internet Explorer 9 configuration on all client computers by using the least administrative effort.
Which three actions should you perform? (To answer, move the appropriate action from the list of actions to the answer area and arrange them in the correct order.)
Select and Place:
All client computers in an organization run Windows 7 and are joined to an Active Directory Domain Services (AD DS) domain. All user objects are stored in an
Organizational Unit (OU) named Contoso Users. All computer objects are stored in an OU named Contoso Computers.
You need to add a proxy server to the Microsoft Internet Explorer 9 configuration on all client computers by using the least administrative effort.
Which three actions should you perform? (To answer, move the appropriate action from the list of actions to the answer area and arrange them in the correct order.)
Select and Place:

Correct Answer:
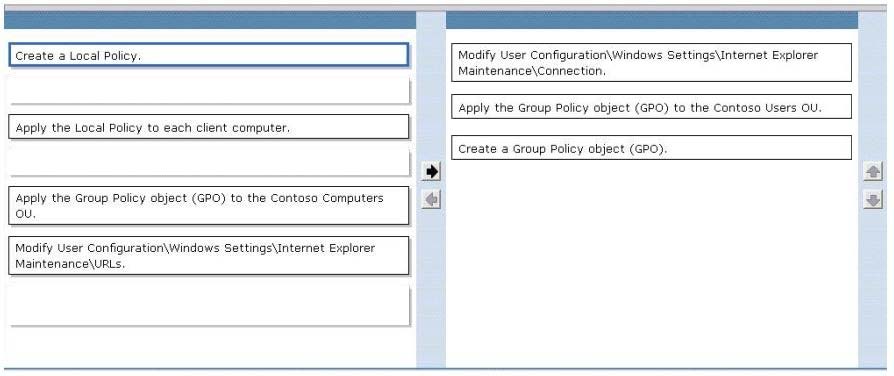
It should be create the GPO 1st, then modify it, then only apply it.
Original answer from smith is the following picture.
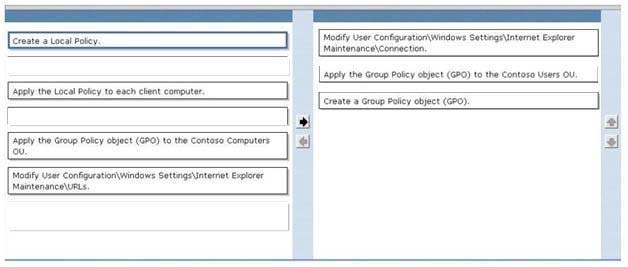

It should be create the GPO 1st, then modify it, then only apply it.
Original answer from smith is the following picture.

send
light_mode
delete
All Pages
