Microsoft 70-686 Exam Practice Questions (P. 3)
- Full Access (183 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #11
Your company has two Active Directory Domain Services (AD DS) domains, Domain1 and Domain2. A two-way trust relationship exists between the domains.
Users in both domains can log on to client computers in only their own domains. System logs on the domain controllers display the error message Clock skew too great when users in Domain1 attempt to log on to client computers in Domain2.
You need to ensure that users can log on to client computers in both domains.
What should you do?
Users in both domains can log on to client computers in only their own domains. System logs on the domain controllers display the error message Clock skew too great when users in Domain1 attempt to log on to client computers in Domain2.
You need to ensure that users can log on to client computers in both domains.
What should you do?
- ADecrease the Maximum tolerance for computer clock synchronization setting in the default Domain Group Policy object ( GPO ).
- BConfigure the primary domain controller (PDC) emulatorin each domain to synchronize its clock with the same external time source.
- CRun a startup script that includes Net Time /setsntp on all client computers.
- DRun a startup script that includes Net Time /querysntp on all client computers.
Correct Answer:
B
B
send
light_mode
delete
Question #12
Your company has an Active Directory Domain Services (AD DS) forest with a single domain named contoso.com. The design of the organizational units (OUs) and Group Policy objects (GPOs) is shown in the following diagram.
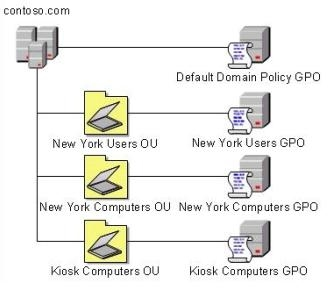
Multiple computer configuration settings and user configuration settings are defined in the Kiosk Computers GPO.
A security audit indicates that user configuration settings that are defined in the Kiosk Computers GPO are not applied when users log on to client computers that are in the Kiosk Computers OU.
You need to ensure that the user configuration settings are correctly applied.
What should you do?

Multiple computer configuration settings and user configuration settings are defined in the Kiosk Computers GPO.
A security audit indicates that user configuration settings that are defined in the Kiosk Computers GPO are not applied when users log on to client computers that are in the Kiosk Computers OU.
You need to ensure that the user configuration settings are correctly applied.
What should you do?
- AEnable loopback processing in Merge mode on the Default Domain Policy GPO.
- BDisable the user configuration settings on the Default Domain Policy GPO.
- CEnable loopback processing in Replace mode on the Kiosk Computers GPO.
- DDisable the user configuration settings on the New York Users GPO.
Correct Answer:
C
Refer to Planning and managing windows 7 desktop deployments and environment
Pg 10-92
C
Refer to Planning and managing windows 7 desktop deployments and environment
Pg 10-92
send
light_mode
delete
Question #13
You have a single Active Directory Domain Services (AD DS) site. All client computers run Windows 7. Users in the marketing department use a custom application.
You create a new Group Policy object (GPO) and link it to the site. Users in the marketing department then report that they are unable to use the custom application.
You need to ensure that all users in the marketing department are able to use the custom application. You need to ensure that all other users continue to receive the new GPO.
What should you do?
You create a new Group Policy object (GPO) and link it to the site. Users in the marketing department then report that they are unable to use the custom application.
You need to ensure that all users in the marketing department are able to use the custom application. You need to ensure that all other users continue to receive the new GPO.
What should you do?
- AAdd marketing users to a domain group. Use security filtering to grant the group the Allow-Read permission and the Allow-Apply Group Policy permission for the GPO.
- BMove marketing users to a dedicated organizational unit (OU). Apply the Block Inheritance setting to the OU.
- CAdd marketing users to a domain group. Use security filtering to grant the group the Allow-Read permission and the Deny-Apply Group Policy permission for the GPO.
- DMove marketing users to a dedicated organizational unit (OU). Apply the Block Inheritance setting to the domain.
Correct Answer:
C
C
send
light_mode
delete
Question #14
You use Group Policy to standardize Internet Explorer settings on Windows 7 client computers. Users occasionally change the Internet Explorer settings on individual client computers.
✑ The company wants to maintain a standard Internet Explorer configuration on all client computers.
✑ You need to ensure that the standard Internet Explorer configuration is in place each time users log on to client computers.
What should you do?
✑ The company wants to maintain a standard Internet Explorer configuration on all client computers.
✑ You need to ensure that the standard Internet Explorer configuration is in place each time users log on to client computers.
What should you do?
- AUse Group Policy to disable the Advanced tab of the Internet Explorer Properties dialog box.
- BUse the Group Policy Update utility to refresh Group Policy.
- CEnable Internet Explorer Maintenance Policy Processing in Group Policy.
- DEnable User Group Policy loopback processing mode.
Correct Answer:
C
nternet Explorer Maintenance policy processing
This policy affects all policies that use the Internet Explorer Maintenance component of Group Policy, such as those in Windows Settings\Internet Explorer
Maintenance. It overrides customized settings that the program implementing the Internet Explorer Maintenance policy set when it was installed.
If you enable this policy, you can use the check boxes provided to change the options.
Allow processing across a slow network connection updates the policies even when the update is being transmitted across a slow network connection, such as a telephone line. Updates across slow connections can cause significant delays.
Do not apply during periodic background processing prevents the system from updating affected policies in the background while the computer is in use.
Background updates can disrupt the user, cause a program to stop or operate abnormally, and, in rare cases, damage data.
Process even if the Group Policy objects have not changed updates and reapplies the policies even if the policies have not changed. Many policy implementations specify that they are updated only when changed.
However, you might want to update unchanged policies, such as reapplying a desired setting in case a user has changed it. http://technet.microsoft.com/en-us/library/cc978526.aspx
C
nternet Explorer Maintenance policy processing
This policy affects all policies that use the Internet Explorer Maintenance component of Group Policy, such as those in Windows Settings\Internet Explorer
Maintenance. It overrides customized settings that the program implementing the Internet Explorer Maintenance policy set when it was installed.
If you enable this policy, you can use the check boxes provided to change the options.
Allow processing across a slow network connection updates the policies even when the update is being transmitted across a slow network connection, such as a telephone line. Updates across slow connections can cause significant delays.
Do not apply during periodic background processing prevents the system from updating affected policies in the background while the computer is in use.
Background updates can disrupt the user, cause a program to stop or operate abnormally, and, in rare cases, damage data.
Process even if the Group Policy objects have not changed updates and reapplies the policies even if the policies have not changed. Many policy implementations specify that they are updated only when changed.
However, you might want to update unchanged policies, such as reapplying a desired setting in case a user has changed it. http://technet.microsoft.com/en-us/library/cc978526.aspx
send
light_mode
delete
Question #15
Your companys network includes client computers that run Windows 7.
You design a wireless network to use Extensible Authentication ProtocolCTransport Level Security (EAP-TLS). The Network Policy Server has a certificate installed.
Client computers are unable to connect to the wireless access points.
You need to enable client computers to connect to the wireless network.
What should you do?
You design a wireless network to use Extensible Authentication ProtocolCTransport Level Security (EAP-TLS). The Network Policy Server has a certificate installed.
Client computers are unable to connect to the wireless access points.
You need to enable client computers to connect to the wireless network.
What should you do?
- AInstall a certificate in the Trusted Root Certification Authorities certificate store.
- BConfigure client computers to use Protected Extensible Authentication ProtocolCTransport Layer Security (PEAP-TLS).
- CConfigure client computers to use Protected Extensible Authentication Protocol-Microsoft Challenge Handshake Authentication Protocol version 2 (PEAP-MS- CHAP v2).
- DInstall a certificate in the Third-Party Root Certification Authorities certificate store.
Correct Answer:
A
A
send
light_mode
delete
All Pages
