Microsoft 70-533 Exam Practice Questions (P. 4)
- Full Access (246 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #16
DRAG DROP -
You manage an Azure virtual machine (VM) named AppVM. The application hosted on AppVM continuously writes small files to disk. You disable caching for all disks that are attached to AppVM. Recently the usage of applications on AppVM has increased greatly.
You need to improve disk performance on AppVM.
Which Microsoft Azure Power Shell cmdlet should you use with each Power Shell command line? To answer, drag the appropriate Microsoft Azure Power Shell cmdlet to the correct location in the Power Shell code. Each Power Shell cmdlet may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
Select and Place:
You manage an Azure virtual machine (VM) named AppVM. The application hosted on AppVM continuously writes small files to disk. You disable caching for all disks that are attached to AppVM. Recently the usage of applications on AppVM has increased greatly.
You need to improve disk performance on AppVM.
Which Microsoft Azure Power Shell cmdlet should you use with each Power Shell command line? To answer, drag the appropriate Microsoft Azure Power Shell cmdlet to the correct location in the Power Shell code. Each Power Shell cmdlet may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
Select and Place:

Correct Answer:
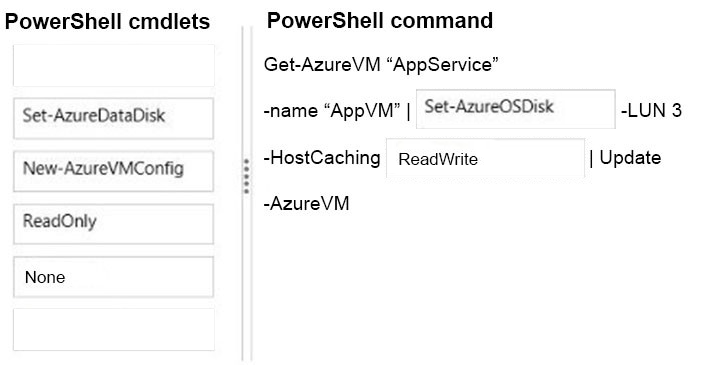
The question states that caching is disabled on all disks. No caching on the write-heavy data disk is the optimal configuration. However, for the OS disk, Read/
Write caching is the optimal configuration.

The question states that caching is disabled on all disks. No caching on the write-heavy data disk is the optimal configuration. However, for the OS disk, Read/
Write caching is the optimal configuration.
send
light_mode
delete
Question #17
DRAG DROP -
You administer a virtual machine (VM) that is deployed to Azure. The VM hosts a web service that is used by several applications.
You need to ensure that the VM sends a notification in the event that the average response time for the web service exceeds a pre-defined response time for an hour or more.
Which three steps should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:
You administer a virtual machine (VM) that is deployed to Azure. The VM hosts a web service that is used by several applications.
You need to ensure that the VM sends a notification in the event that the average response time for the web service exceeds a pre-defined response time for an hour or more.
Which three steps should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:

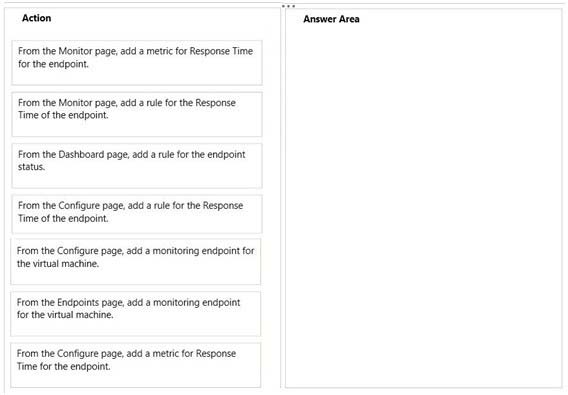
Correct Answer:
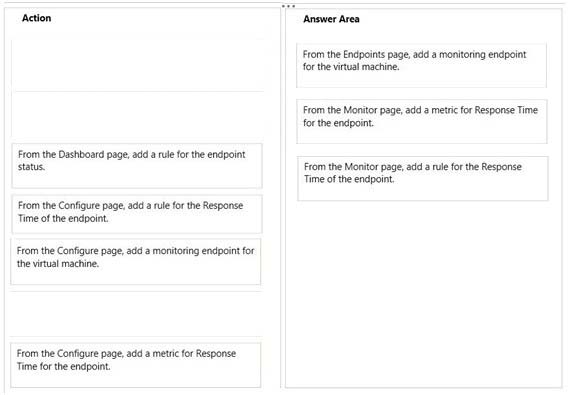
✑ From configure page, add a monitoring endpoint for the virtual machine
✑ From the monitor page, Add a metric for the Response Time for the end point
✑ From the Monitor page, add a rule for the response time of the end point.
References:
http://azure.microsoft.com/en-us/documentation/articles/web-sites-monitor/#webendpointstatus

✑ From configure page, add a monitoring endpoint for the virtual machine
✑ From the monitor page, Add a metric for the Response Time for the end point
✑ From the Monitor page, add a rule for the response time of the end point.
References:
http://azure.microsoft.com/en-us/documentation/articles/web-sites-monitor/#webendpointstatus
send
light_mode
delete
Question #18
DRAG DROP -
You administer an Azure Virtual Machine (VM) named CON-CL1. CON-CL1 is in a cloud service named ContosoService1.
You discover unauthorized traffic to CON-CL1. You need to:
✑ Create a rule to limit access to CON-CL1.
✑ Ensure that the new rule has the highest precedence.
Which Azure Power Shell cmdlets and values should you use? To answer, drag the appropriate cmdlet or value to the correct location in the Power Shell command. Each cmdlet or value may be used once, more than once, or not at all. You may need to drag the split bat between panes or scroll to view content.
Select and Place:
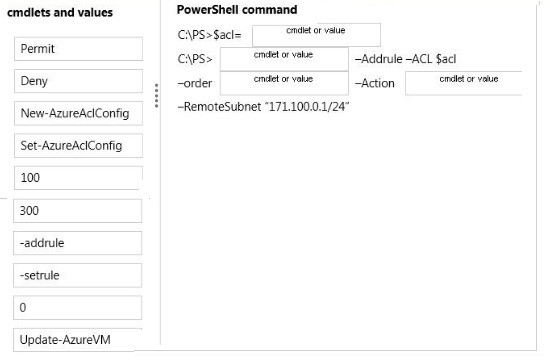
You administer an Azure Virtual Machine (VM) named CON-CL1. CON-CL1 is in a cloud service named ContosoService1.
You discover unauthorized traffic to CON-CL1. You need to:
✑ Create a rule to limit access to CON-CL1.
✑ Ensure that the new rule has the highest precedence.
Which Azure Power Shell cmdlets and values should you use? To answer, drag the appropriate cmdlet or value to the correct location in the Power Shell command. Each cmdlet or value may be used once, more than once, or not at all. You may need to drag the split bat between panes or scroll to view content.
Select and Place:

Correct Answer:
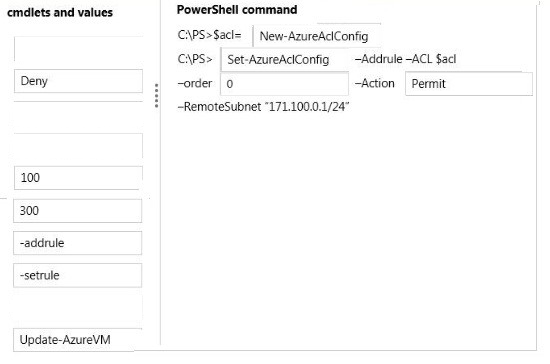
* Example 1
This example uses two commands:
The first command creates a new ACL object and stores it in a variable named $acl1.
The second command updates the ACL object with a rule that permits incoming network traffic only from remote subnet 10.0.0.0/8.
Windows PowerShell -
PS C:\> $acl1 = New-AzureAclConfigC:\PS> Set-AzureAclConfig –AddRule –ACL $acl1 –Order 100 –Action permit –RemoteSubnet "10.0.0.0/8" –
*Parameter: -Order<Int32>
Specifies the relative order in which this rule should be processed compared to the other rules applied to the ACL object. The lowest order takes precedence. 0 is allowed.
References:
http://msdn.microsoft.com/en-us/library/dn495192.aspx
http://blogs.technet.com/b/heyscriptingguy/archive/2013/08/31/weekend-scripter-creating-acls-for-windows-azure-endpoints-part-1-of-2.aspx

* Example 1
This example uses two commands:
The first command creates a new ACL object and stores it in a variable named $acl1.
The second command updates the ACL object with a rule that permits incoming network traffic only from remote subnet 10.0.0.0/8.
Windows PowerShell -
PS C:\> $acl1 = New-AzureAclConfigC:\PS> Set-AzureAclConfig –AddRule –ACL $acl1 –Order 100 –Action permit –RemoteSubnet "10.0.0.0/8" –
*Parameter: -Order<Int32>
Specifies the relative order in which this rule should be processed compared to the other rules applied to the ACL object. The lowest order takes precedence. 0 is allowed.
References:
http://msdn.microsoft.com/en-us/library/dn495192.aspx
http://blogs.technet.com/b/heyscriptingguy/archive/2013/08/31/weekend-scripter-creating-acls-for-windows-azure-endpoints-part-1-of-2.aspx
send
light_mode
delete
Question #19
HOTSPOT -
Your company network has two branch offices. Some employees work remotely, including at public locations. You manage an Azure environment that includes several virtual networks.
All users require access to the virtual networks.
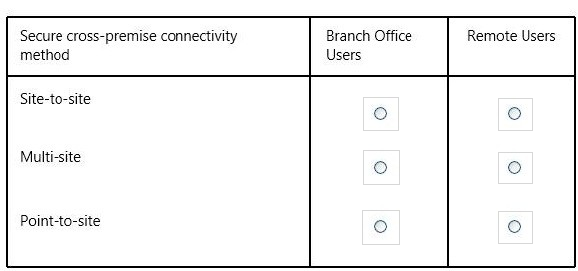
In the table below, identify which secure cross-premise connectivity option is needed for each type of user. Make only one selection in each column.
Hot Area:
Your company network has two branch offices. Some employees work remotely, including at public locations. You manage an Azure environment that includes several virtual networks.
All users require access to the virtual networks.
In the table below, identify which secure cross-premise connectivity option is needed for each type of user. Make only one selection in each column.
Hot Area:

Correct Answer:
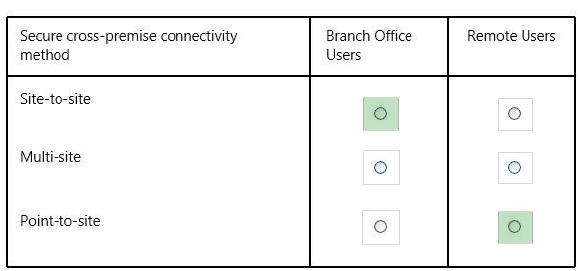
* A site-to-site VPN allows you to create a secure connection between your on-premises site and your virtual network.
* A point-to-site VPN also allows you to create a secure connection to your virtual network. In a point-to-site configuration, the connection is configured individually on each client computer that you want to connect to the virtual network.
* Use a point-to-site configuration when:
You want connect to your virtual network from a remote location. For example, connecting from a coffee shop.
You have a site-to-site connection, but have some clients that need to connect from a remote location.

* A site-to-site VPN allows you to create a secure connection between your on-premises site and your virtual network.
* A point-to-site VPN also allows you to create a secure connection to your virtual network. In a point-to-site configuration, the connection is configured individually on each client computer that you want to connect to the virtual network.
* Use a point-to-site configuration when:
You want connect to your virtual network from a remote location. For example, connecting from a coffee shop.
You have a site-to-site connection, but have some clients that need to connect from a remote location.
send
light_mode
delete
Question #20
HOTSPOT -
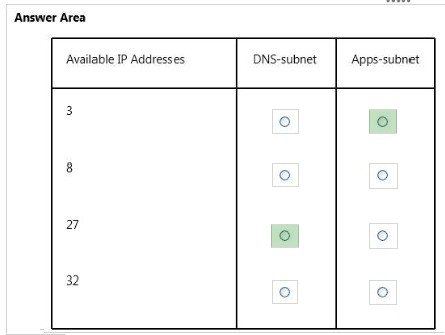
You create a virtual network named fabVNet01.
You design the virtual network to include two subnets, one named DNS-subnet and one named Apps-subnet, as shown in the exhibit. (Click the Exhibits button.)
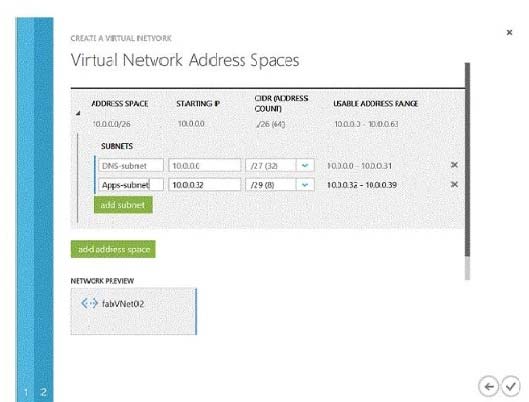
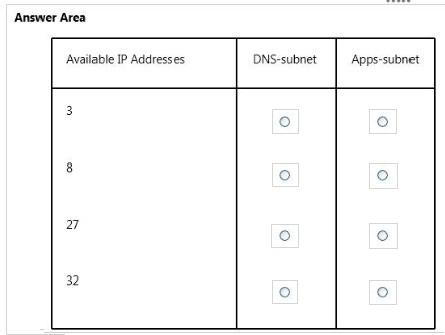
In the table below, identify the number of IP addresses that will be available for virtual machines (VMs) or cloud services in each subnet. Make only one selection in each column.
Hot Area:
You create a virtual network named fabVNet01.
You design the virtual network to include two subnets, one named DNS-subnet and one named Apps-subnet, as shown in the exhibit. (Click the Exhibits button.)

In the table below, identify the number of IP addresses that will be available for virtual machines (VMs) or cloud services in each subnet. Make only one selection in each column.
Hot Area:

send
light_mode
delete
All Pages