Microsoft 70-465 Exam Practice Questions (P. 5)
- Full Access (64 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #21
You have two databases named DB1 and DB2 that are located on the same server.
You plan to create a stored procedure named SProc1 in DB1.
SProc1 will query a table named Table2 in DB2.
You need to recommend a solution to ensure that SProc1 can access Table2 without granting users direct access to Table2.
What should you include in the recommendation?
More than one answer choice may achieve the goal. Select the BEST answer.
You plan to create a stored procedure named SProc1 in DB1.
SProc1 will query a table named Table2 in DB2.
You need to recommend a solution to ensure that SProc1 can access Table2 without granting users direct access to Table2.
What should you include in the recommendation?
More than one answer choice may achieve the goal. Select the BEST answer.
- AContained databases
- BApplication roles
- CCross-database ownership chaining
- DDigital certificates
Correct Answer:
B
An application role is a database principal that enables an application to run with its own, user-like permissions. You can use application roles to enable access to specific data to only those users who connect through a particular application. Unlike database roles, application roles contain no members and are inactive by default.
Reference:
Application Roles
B
An application role is a database principal that enables an application to run with its own, user-like permissions. You can use application roles to enable access to specific data to only those users who connect through a particular application. Unlike database roles, application roles contain no members and are inactive by default.
Reference:
Application Roles
send
light_mode
delete
Question #22
DRAG DROP -
You are designing an authentication strategy for a new server that has SQL Server 2014 installed. The strategy must meet the following business requirements:
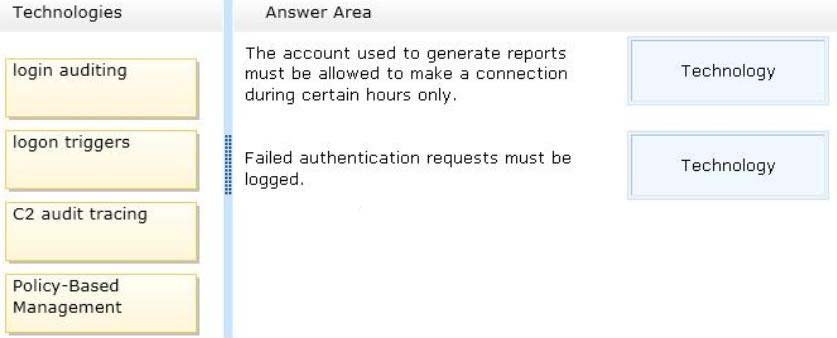
The account used to generate reports must be allowed to make a connection during certain hours only.
Failed authentication requests must be logged.
You need to recommend a technology that meets each business requirement. The solution must minimize the amount of events that are logged.
Which technologies should you recommend?
To answer, drag the appropriate solution to the correct business requirement in the answer area.
Select and Place:
You are designing an authentication strategy for a new server that has SQL Server 2014 installed. The strategy must meet the following business requirements:
The account used to generate reports must be allowed to make a connection during certain hours only.
Failed authentication requests must be logged.
You need to recommend a technology that meets each business requirement. The solution must minimize the amount of events that are logged.
Which technologies should you recommend?
To answer, drag the appropriate solution to the correct business requirement in the answer area.
Select and Place:

Correct Answer:
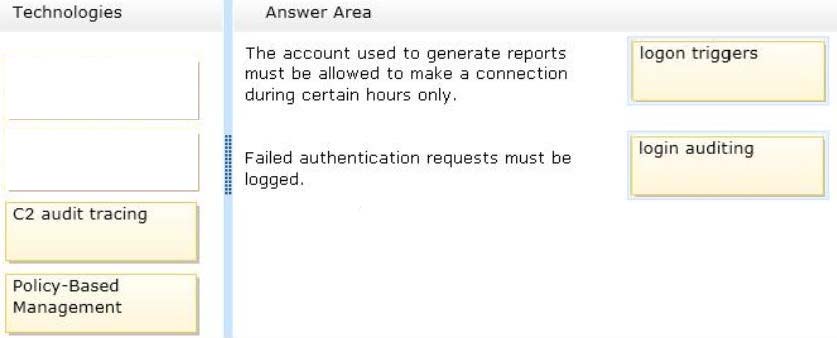
* Logon triggers fire stored procedures in response to a LOGON event. This event is raised when a user session is established with an instance of SQL Server.
Logon triggers fire after the authentication phase of logging in finishes, but before the user session is actually established.
You can use logon triggers to audit and control server sessions, such as by tracking login activity, restricting logins to SQL Server, or limiting the number of sessions for a specific login.
* Login auditing can be configured to write to the error log on the following events.
Failed logins -
Successful logins -
Both failed and successful logins
Incorrect:
* C2 audit mode can be configured through SQL Server Management Studio or with the c2 audit mode option in sp_configure. Selecting this option will configure the server to record both failed and successful attempts to access statements and objects.
References:
Logon Triggers -
Configure Login Auditing (SQL Server Management Studio)

* Logon triggers fire stored procedures in response to a LOGON event. This event is raised when a user session is established with an instance of SQL Server.
Logon triggers fire after the authentication phase of logging in finishes, but before the user session is actually established.
You can use logon triggers to audit and control server sessions, such as by tracking login activity, restricting logins to SQL Server, or limiting the number of sessions for a specific login.
* Login auditing can be configured to write to the error log on the following events.
Failed logins -
Successful logins -
Both failed and successful logins
Incorrect:
* C2 audit mode can be configured through SQL Server Management Studio or with the c2 audit mode option in sp_configure. Selecting this option will configure the server to record both failed and successful attempts to access statements and objects.
References:
Logon Triggers -
Configure Login Auditing (SQL Server Management Studio)
send
light_mode
delete
Question #23
You are creating a database that will store usernames and passwords for an application.
You need to recommend a solution to store the passwords in the database.
What should you recommend?
More than one answer choice may achieve the goal. Select the BEST answer.
You need to recommend a solution to store the passwords in the database.
What should you recommend?
More than one answer choice may achieve the goal. Select the BEST answer.
- AOne-way encryption
- BEncrypting File System (EFS)
- CTransparent Data Encryption (TDE)
- DReversible encryption
Correct Answer:
C
* Transparent Data Encryption (TDE) is a special case of encryption using a symmetric key. TDE encrypts an entire database using that symmetric key called the database encryption key. The database encryption key is protected by other keys or certificates which are protected either by the database master key or by an asymmetric key stored in an EKM module.
* SQL Server provides the following mechanisms for encryption:
Transact-SQL functions -
Asymmetric keys -
Symmetric keys -
Certificates -
Transparent Data Encryption -
Reference:
Transparent Data Encryption (TDE)
C
* Transparent Data Encryption (TDE) is a special case of encryption using a symmetric key. TDE encrypts an entire database using that symmetric key called the database encryption key. The database encryption key is protected by other keys or certificates which are protected either by the database master key or by an asymmetric key stored in an EKM module.
* SQL Server provides the following mechanisms for encryption:
Transact-SQL functions -
Asymmetric keys -
Symmetric keys -
Certificates -
Transparent Data Encryption -
Reference:
Transparent Data Encryption (TDE)
send
light_mode
delete
Question #24
QUESTION NO: 24 DRAG DROP -
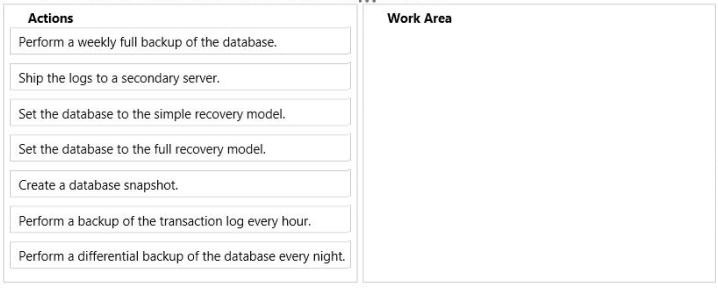
You need to recommend a backup process for data warehouse database.
The solution must meet the following requirements:
✑ Ensure that if a hardware failure occurs, you can bring the database online without losing more than 24 hours of transactions.
✑ Minimize the amount of administrative effort required to restore any lost data.
✑ Minimize the space used by transaction logs.
What should you include in the recommendation?
To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:
You need to recommend a backup process for data warehouse database.
The solution must meet the following requirements:
✑ Ensure that if a hardware failure occurs, you can bring the database online without losing more than 24 hours of transactions.
✑ Minimize the amount of administrative effort required to restore any lost data.
✑ Minimize the space used by transaction logs.
What should you include in the recommendation?
To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:

Correct Answer:
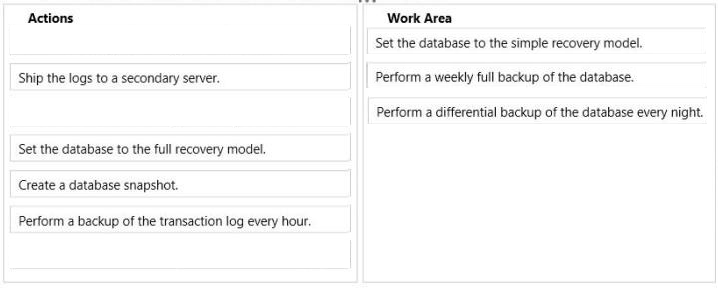
Note:
* Simple recovery model
No log backups.
* Full recovery model
Requires log backups -
Reference:
Recovery Models (SQL Server)
Full Database Backups (SQL Server)
Differential Backups (SQL Server)

Note:
* Simple recovery model
No log backups.
* Full recovery model
Requires log backups -
Reference:
Recovery Models (SQL Server)
Full Database Backups (SQL Server)
Differential Backups (SQL Server)
send
light_mode
delete
Question #25
DRAG DROP -
You plan to deploy a database to SQL Azure.
You must create two tables named Table 1 and Table 2 that will have the following specifications:
Table1 will contain a date column named Column1 that will contain a null value approximately 80 percent of the time.

✑ Table2 will contain a column named Column2 which is the product of two other columns in Table2.
Both Table1 and Table2 will contain over one million rows.
You need to recommend which options must be defined for the columns. The solution must minimize the time it takes to retrieve data from the tables.
Which options should you recommend?
To answer, drag the appropriate options to the correct column in the answer area.
Select and Place:
You plan to deploy a database to SQL Azure.
You must create two tables named Table 1 and Table 2 that will have the following specifications:
Table1 will contain a date column named Column1 that will contain a null value approximately 80 percent of the time.

✑ Table2 will contain a column named Column2 which is the product of two other columns in Table2.
Both Table1 and Table2 will contain over one million rows.
You need to recommend which options must be defined for the columns. The solution must minimize the time it takes to retrieve data from the tables.
Which options should you recommend?
To answer, drag the appropriate options to the correct column in the answer area.
Select and Place:
Correct Answer:
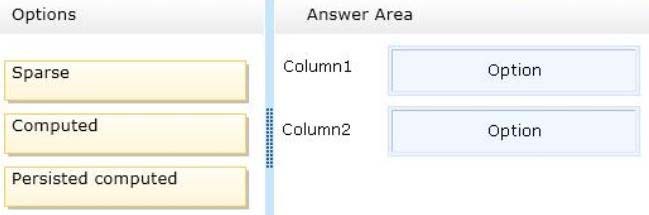
* Sparse columns are ordinary columns that have an optimized storage for null values. Sparse columns reduce the space requirements for null values at the cost of more overhead to retrieve nonnull values. Consider using sparse columns when the space saved is at least 20 percent to 40 percent.
* A Persisted column would be faster to retrieve.
* A computed column is computed from an expression that can use other columns in the same table. The expression can be a noncomputed column name, constant, function, and any combination of these connected by one or more operators.
Unless otherwise specified, computed columns are virtual columns that are not physically stored in the table. Their values are recalculated every time they are referenced in a query. The Database Engine uses the PERSISTED keyword in the CREATE TABLE and ALTER TABLE statements to physically store computed columns in the table. Their values are updated when any columns that are part of their calculation change.
References:
Use Sparse Columns -
Specify Computed Columns in a Table

* Sparse columns are ordinary columns that have an optimized storage for null values. Sparse columns reduce the space requirements for null values at the cost of more overhead to retrieve nonnull values. Consider using sparse columns when the space saved is at least 20 percent to 40 percent.
* A Persisted column would be faster to retrieve.
* A computed column is computed from an expression that can use other columns in the same table. The expression can be a noncomputed column name, constant, function, and any combination of these connected by one or more operators.
Unless otherwise specified, computed columns are virtual columns that are not physically stored in the table. Their values are recalculated every time they are referenced in a query. The Database Engine uses the PERSISTED keyword in the CREATE TABLE and ALTER TABLE statements to physically store computed columns in the table. Their values are updated when any columns that are part of their calculation change.
References:
Use Sparse Columns -
Specify Computed Columns in a Table
send
light_mode
delete
All Pages
